facundo Mz
@0xfmz
Malware Researcher at ESET 🙂
You might like
I will presenting at #JSAC2025 this afternoon at 15:20 about PlushDaemon. Come say hello!👋
Join #ESETresearch at #JSAC2025! Facundo Munoz will talk about China-aligned PlushDaemon APT compromising the supply chain of a 🇰🇷 South Korean VPN. In 2024, several users downloaded a trojanized NSIS installer from the official website of a South Korean VPN company. 1/3

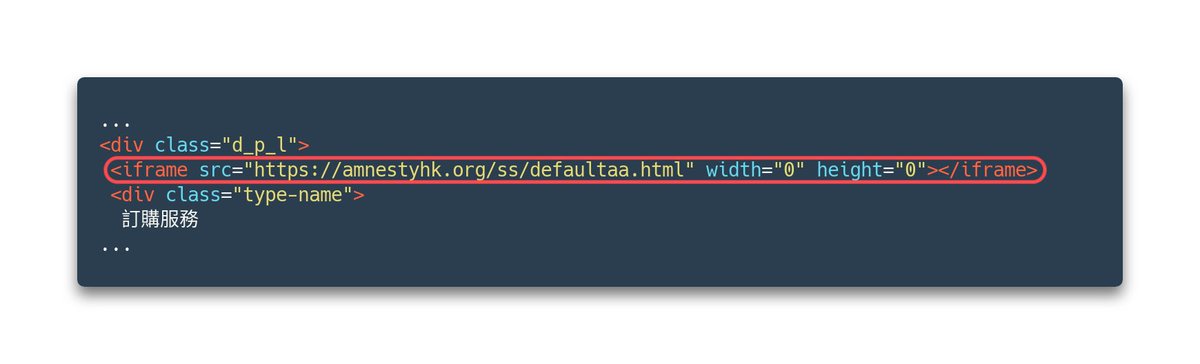
What a fcking disgrace 🤬
The @ukrcancongress wrote a breakdown of the Canadian organizations like @CMF_FMC who are helping to fund and distribute this disgusting piece of propaganda disguised as a documentary They listed their contact info too. ucc.ca/2024/09/06/why…
We are looking for a strategic threat intel analyst to join @ESETresearch. Interested in cyber-espionage and geopolitics? Apply! ca.linkedin.com/jobs/view/anal…
linkedin.com
1,000+ Intelligence Officer jobs in United States (31 new)
Today’s top 1,000+ Intelligence Officer jobs in United States. Leverage your professional network, and get hired. New Intelligence Officer jobs added daily.
My man @juanandres_gs is not happy. “Is there hope? No” said Nicole from Intezer. Is this time for panic? I think yes.

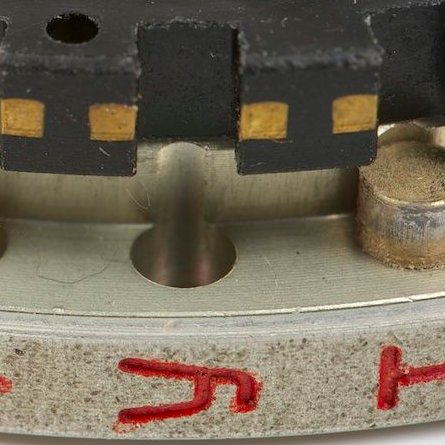
NSPX30's installer component ⬇️
Sample is now on VT! 🚩Hash: f7eb86f60458ea8888b8df86dd4baf93 🎯Actor name: Blackwood 🔹Comment: ESET analysis of a sophisticated implant named #NSPX30 used by the #Blackwood China-aligned threat actor 🌐URL: welivesecurity.com/en/eset-resear… 🔎OnVT: virustotal.com/gui/file/796d0…
I'm glad that so many colleagues have found this research interesting, and I even got to shake hands with Franki Li who authored the 1st report on PWood in 2011. Grateful to @marc_etienne_, Anh, and our master detection engineer who helped me with research! 🙌🏻
#ESETresearch has discovered a China-aligned APT group, which we named #Blackwood, that leverages adversary-in-the-middle (AitM) to deliver the NSPX30 implant via software updates. NSPX30 is a sophisticated implant evolving since at least 2005. @0xfmz welivesecurity.com/en/eset-resear… 1/6
Today I will be presenting our #Blackwood (and a bit more) research at #jsac2024, if you see me around come say hello!

I'm happy to announce I will be presenting at #JSAC2024 our latest work at ESET research, titled: NSPX30: a sophisticated AitM-enabled implant evolving since 2005 You can read more about it here: jsac.jpcert.or.jp/timetable.html
#ESETResearch discovered a previously unknown #Belarus-aligned cyberespionage group that we named #MoustachedBouncer. Active since 2014, they are spying on EU, African and Asian diplomats stationed in 🇧🇾 🇧🇾 1/5 welivesecurity.com/en/eset-resear…
🚨🚨➡️ NEW REPORT OUT > Imagine if someone read everything you type online. Our new report- “Please do not make it public”, analyzes Tencent's #Sogou Input Method, the most popular input app in #China has serious vulnerabilities in the encryption system. citizenlab.ca/?p=79791&previ…
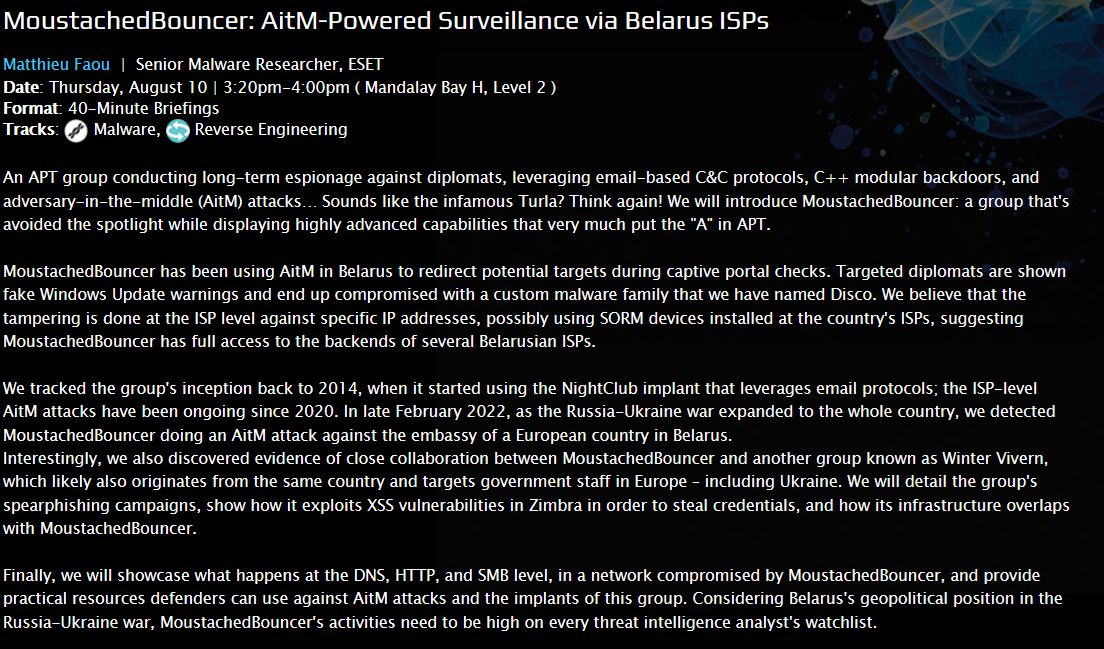
#ESETresearch will present at Black Hat USA 2023. On August 10th, @matthieu_faou will talk about #MoustachedBouncer: AitM-Powered Surveillance via Belarus ISPs 🇧🇾 #BHUSA #BlackHat Stay tuned!
Our research on Tick APT group is out! 👇
#ESETResearch discovered an attack by APT group Tick against a data-loss prevention (DLP) company in East Asia and found a previously unreported tool used by the group. welivesecurity.com/2023/03/14/slo… @0xfmz 1/6
The exploit for Safari is quite complex and massive. I really wanted to understand exactly what the vulnerability was and how it was mitigated, so I dived into the world of browser exploits for a few days and tried to explain how leaking object addresses was possible.
#ESETresearch uncovers new Mac malware DazzleSpy, delivered using watering hole on a pro-democracy Hong Kong radio station website. Payload was launched as root without user interaction, using exploits for Safari and macOS. @marc_etienne_ @cherepanov74 welivesecurity.com/2022/01/25/wat… 1/7
United States Trends
- 1. Northern Lights 42.1K posts
- 2. #Aurora 8,780 posts
- 3. #DWTS 52.1K posts
- 4. #RHOSLC 6,852 posts
- 5. Justin Edwards 2,341 posts
- 6. Sabonis 6,147 posts
- 7. Louisville 17.9K posts
- 8. #GoAvsGo 1,544 posts
- 9. Creighton 2,236 posts
- 10. #OlandriaxHarpersBazaar 5,569 posts
- 11. H-1B 32K posts
- 12. Eubanks N/A
- 13. Gonzaga 2,913 posts
- 14. Andy 60.5K posts
- 15. Lowe 12.7K posts
- 16. Jamal Murray N/A
- 17. Schroder N/A
- 18. JT Toppin N/A
- 19. Oweh 2,105 posts
- 20. Zags N/A
You might like
-
 Johann Aydinbas
Johann Aydinbas
@jaydinbas -
 Silas Cutler (p1nk)
Silas Cutler (p1nk)
@silascutler -
 Dan Perez
Dan Perez
@MrDanPerez -
 Adrien B
Adrien B
@Int2e_ -
 Chuong Dong
Chuong Dong
@cPeterr -
 J. A. Guerrero-Saade
J. A. Guerrero-Saade
@juanandres_gs -
 Blackstorm Security
Blackstorm Security
@blackstormsecbr -
 Rufus
Rufus
@rufusmbrown -
 Jean-Ian Boutin
Jean-Ian Boutin
@jiboutin -
 Aleksandar Milenkoski
Aleksandar Milenkoski
@milenkowski -
 NexusFuzzy 💩
NexusFuzzy 💩
@NexusFuzzy -
 Robert Lipovsky
Robert Lipovsky
@Robert_Lipovsky -
 Anton Cherepanov
Anton Cherepanov
@cherepanov74 -
 __mat__
__mat__
@matthieu_faou -
 The Banshee Queen👑
The Banshee Queen👑
@cyberoverdrive
Something went wrong.
Something went wrong.