Alex_
@Alex_ctf_
🇫🇷 CTF Player for @idekCTF (Web/Forensic) | ECSC Team France 2023 | Bug Bounty Hunter
You might like
I found out that you can use "ftp::" to convert a limited Dom Clobering situation into a full CSPT. Then, while talking about it with @LooseSecurity, he found that we can also use "https::" This can be used to prevent URL parsing of href, allowing us to hit other endpoints

Made a writeup on a critical CVSS 10.0 vulnerability I've recently found. Check it out, maybe you'll manage to make into a full config independent RCE. blog.z3r.ru/posts/spring-c…
Just published my first blog post "Cache Deception + CSPT: Turning Non Impactful Findings into Account Takeover" You can read the full write-up here: zere.es/posts/cache-de…
Here’s the source code of our #AIxCC winning team @TeamAtlanta24, enjoy! github.com/Team-Atlanta/a… More things TBA
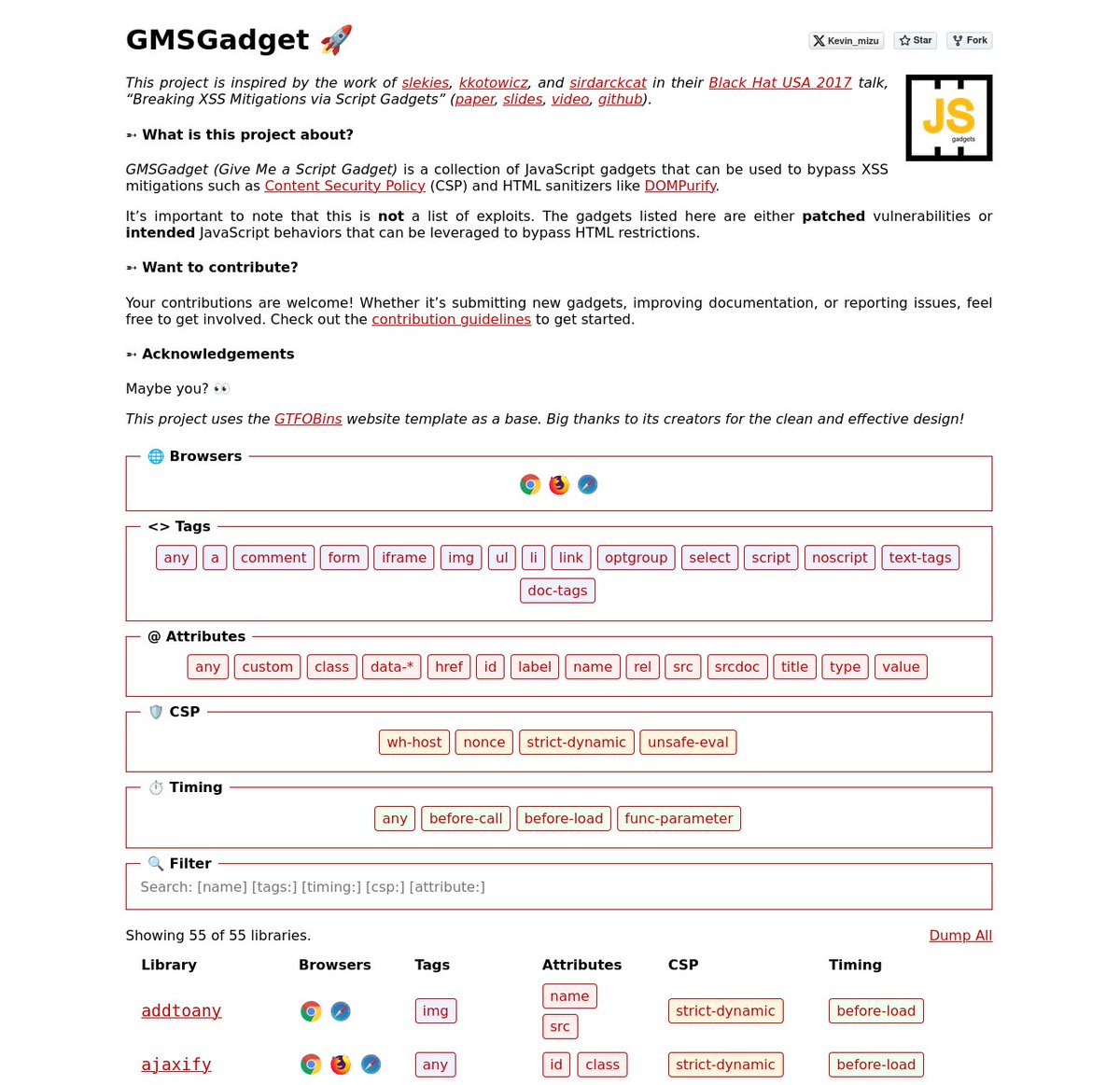
I'm happy to release a script gadgets wiki inspired by the work of @slekies, @kkotowicz, and @sirdarckcat in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4
Just pushed a new frontend for my site, and a new post! This one's about an tricky file write vulnerability on Windows in OBS. By crafting an image with very specific pixels, we can plant a backdoor on your PC all from an attacker's site by misconfiguring: jorianwoltjer.com/blog/p/researc…
New blog post with @infosec_au: We found a vulnerability in Subaru where an attacker, with just a license plate, could retrieve the full location history, unlock, and start vehicles remotely. The issue was reported and patched. Full post here: samcurry.net/hacking-subaru
I'm thrilled to finally share my research on HTML parsing and DOMPurify at @GreHack 2024 📜 The research article is available here: mizu.re/post/exploring… The slides are available here: slides.com/kevin-mizu/gre… 1/3

DOMLogger++ v1.0.6 is now out and available! It comes with some new features, but mostly fixes inconvenient bugs 🔥 More details can be found here 👇 github.com/kevin-mizu/dom… Btw, if you have issues trying the extension on labs, you should check this: github.com/kevin-mizu/dom…

ooh, this works on Chrome Canary :D <input type="hidden" oncontentvisibilityautostatechange="alert(/ChromeCanary/)" style="content-visibility:auto">
<p oncontentvisibilityautostatechange="alert(/FirefoxOnly/)" style="content-visibility:auto">
🔥 XSS on any website with missing charset information? 😳 Attackers may leverage the ISO-2022-JP character encoding to inject arbitrary JavaScript code into a website. Read more in our latest blog post: sonarsource.com/blog/encoding-… #appsec #security #vulnerability

🚨💰 Google VRP Reward Update 💰🚨 Good news, we are significantly increasing the reward amounts offered by the Google VRP! Look out for up to 5x higher payouts and a maximum reward of $151,515! Details here: bughunters.google.com/blog/540051395…
Our security researcher @hash_kitten found one of the most critical exploit chains in the history of @assetnote. Affecting 40k+ instances of ServiceNow, we could execute arbitrary code, access all data without authentication. You can read our blog here: assetnote.io/resources/rese…

My latest blog about my discovery for Evernote Client All-platform RCE via PDF.js font-injection to preload.js exposed ipcRenderer-BrokerBridge-boron.actions bypassing Electron's nodeIntegration | context-isolation; Enjoy reading! 0reg.dev/blog/evernote-…
Iconv, set the charset to RCE (part 2): @cfreal_ exploits direct iconv() calls to hack the PHP engine, and its most popular webmail, @Roundcube (CVE-2024-2961). ambionics.io/blog/iconv-cve…
Phishing with Progressive Web Apps: mrd0x.com/progressive-we… More fake URL bars :)

Thanks for everyone watching my keynote on WAF bypasses at Nahamcon. You can find my slides here: drive.google.com/file/d/1PwKdma…
XSS in PDF.js! I think this is going to cause some chaos both client-side and server-side... really nice finding by @CodeanIO codeanlabs.com/blog/research/…
United States Trends
- 1. Cynthia 70K posts
- 2. #WorldKindnessDay 10.1K posts
- 3. #GrabFoodMegaSalexหลิงออม 712K posts
- 4. Good Thursday 33.3K posts
- 5. Larry Brooks 1,369 posts
- 6. RIP Brooksie N/A
- 7. Taylor Fritz N/A
- 8. Rejoice in the Lord 2,643 posts
- 9. $MYNZ N/A
- 10. Happy Friday Eve N/A
- 11. #thursdayvibes 3,033 posts
- 12. Michael Burry 9,456 posts
- 13. #thursdaymotivation 2,178 posts
- 14. #SwiftDay N/A
- 15. Tommy James N/A
- 16. RIP Larry 1,262 posts
- 17. Bonhoeffer 1,010 posts
- 18. MEDICA 15.6K posts
- 19. THEATRE EFW2025 X CL 414K posts
- 20. Mollie 2,293 posts
Something went wrong.
Something went wrong.