makarov
@JacoubRob
toujours derrière ton pare-feu.
You might like
One thing I like do do when auditing is picking a state variable alone and focusing on it. Sometimes moving the focus away from the main flows but focusing just on how each var is updated everywhere makes bugs more obvious / increases the understanding of the codebase faster.
Our Balancer retro is live. The ecosystem has evolved & rounding issues are more critical than ever. Here are recommendations for preventing rounding issues and other important lessons from this incident: blog.trailofbits.com/2025/11/07/bal…
Since the Balancer hack on Monday, we've been working around the clock to help the Balancer team understand the bug and its implications. We've verified the bug's cause and have independently verified that the exploit does not work on Balancer V3. Once the dust settles, we plan…
“If debugging is the process of removing software bugs, then programming must be the process of putting them in.” E Dijkstra
Most JWT vulnerabilities go unnoticed as they're notoriously tricky to test for 😬 Yet, when present, they can allow for account takeovers, SQL injections and in-app privilege escalations 🤠 In our latest article, we break down every common JWT attack vector with practical…

Oh look, BAC made #1 🤣 If you ask 10 people to stand in a line and count each other, they will count off: 1.. 2... 3... 4.... NOT 52b25168-d784-4b3d-97ff-70841b39e8e9... be30ae3d-aa22-4cbc-8ecb-a172dffa066a..... We will have IDORs as long as we have humans making code.
This is still the way I recommend most people start in Web3 Security: 1. Get blockchain/smart contract basics 2. Do shadow audits 3. Analyse mistakes 4. Read similar reports/issues 5. After 1-2 month start in contests 6. Audit 80% / Study 20% 7. Repeat it type(uint256.max) times
The demon at the end of my bed every night.

I saw a post claiming it was simply access control bypass via user-provided input. unbelievable I remember hunting on this codebase back at the very beginning. part of me decidedly put it in the bucket of projects "too OG to contain bugs" which everyone looking at it must have…
I'm mad that I didn't catch the issue. I'm also mad that no whitehat or auditor did either. It's one of the pillars of DeFi, and they had a respectable bounty. We have no excuses. Sad day. The bug will probably be something trivial once understood. I still got much to learn.
New cool updates in audit-rewards.xyz Now there are Contest tabs + per-issue hide feature. You can either track multiple contests or multiple reward scenarios, all at once. You can dup, rename, delete/add a new tab. suggestions by @s4muraii77 🫡

It’s extra scary when a protocol with a long track history is attacked. Waiting to see the post mortem so we can figure out how to improve industry best practices to stay safer…
The article you've all been waiting for, finally! 🦄 Uniswap V4 Hooks Security Deep Dive 🦄 ✨ Epic @DevDacian style heuristic-based deep dive ✨ 26 categories & 126 examples of real bugs in the wild ✨ Learnings from 7 @areta_io @UniswapFND subsidized @CyfrinAudits Link 👇

Mastering Ethereum 2nd edition is officially out. How can you read it? - Online for free: in the next few days/weeks we will publish it on github/x and probably other venues - Kindle: you can buy it on amazon - Paperback: you can buy it on amazon - Online not for free (doesn't…
I probably have the biggest announcement of my career to make. Me, @crypto_ita2, and @idrocortisone are going to write "Mastering Ethereum: Second Edition." It is an honor for us to have the opportunity to update the masterpiece of @aantonop and @gavofyork. This is the biggest…


Shoutout to those building their own future: - No rich parents - No connections - No help - No excuses Just hard work, consistency, commitment, and focus.
The hardest part of bug bounty isn't finding vulnerabilities. It's dealing with: - Programs that ghost you - $100 "critical" payouts - Months of waiting Mental strength > technical skills.
I just built a custom action to let you test for race conditions with a single click! No tab groups required, and it uses the cutting edge single-packet attack under the hood.

1/6 Tired of manually testing every parameter hoping to find an XSS? Yeah us too. It's time-consuming, repetitive, and let's be honest, not the most exciting part of the job. So we built a Burp Suite extension @onetestfr to automate the entire process (Caido coming soon).

Security Researcher walks into a bar. Orders a beer. Orders 0 beers. Orders 999999999 beers. Orders a lizard. Orders -1 beers. Orders a sfdeljknesv.
Want to know how to exploit HTTP headers? From basic to advanced techniques, our guide to HTTP header hacks gives you invaluable knowledge for securing bug bounties 💸 👉 yeswehack.com/learn-bug-boun… #YesWeRHackers #BugBounty #BugBountyTips
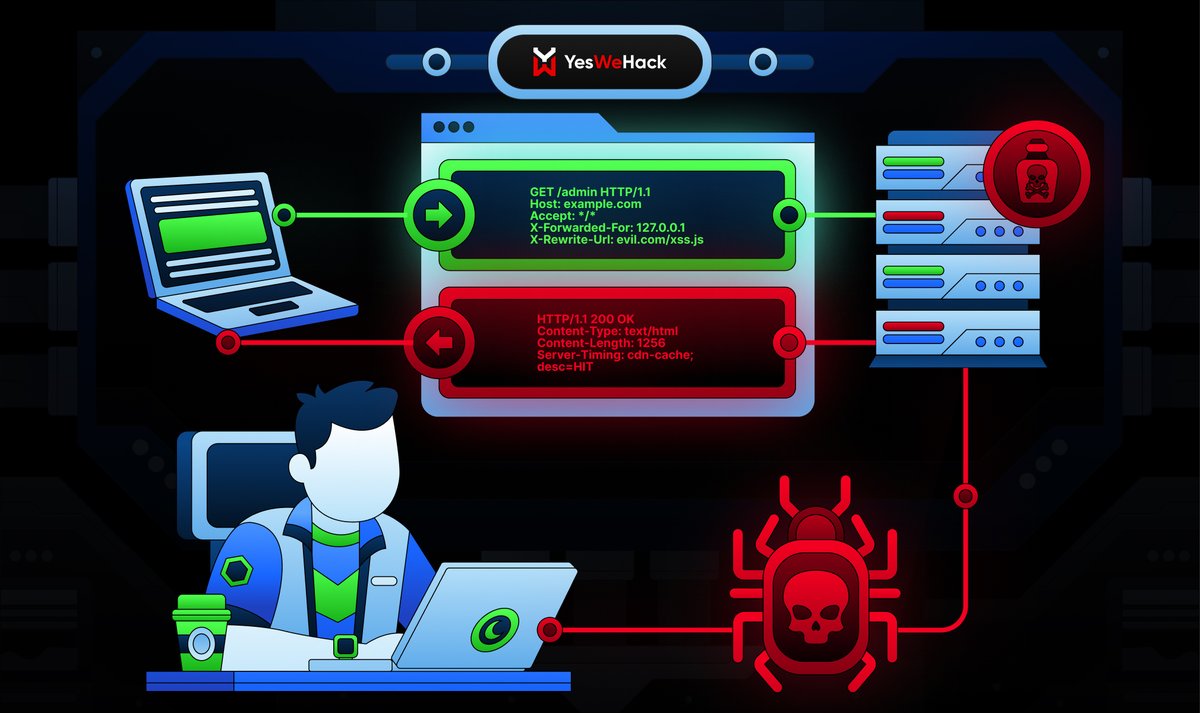
🔌 Introducing the Burp Suite MCP Server extension Join us this Tuesday at 4pm BST (11am EDT) to see how you can leverage MCP for powerful AI integrations with Burp Suite. Live demo + Q&A with the devs. Join the PortSwigger Discord to attend 👉 bit.ly/4jwJDHt

United States Trends
- 1. #DWTS 42.4K posts
- 2. Northern Lights 16K posts
- 3. Justin Edwards 1,096 posts
- 4. Andy 58.6K posts
- 5. #Aurora 3,558 posts
- 6. Elaine 45.7K posts
- 7. Robert 97.6K posts
- 8. #RHOSLC 5,038 posts
- 9. Dylan 30.4K posts
- 10. #WWENXT 13.4K posts
- 11. Louisville 11.1K posts
- 12. Whitney 8,465 posts
- 13. Alix 8,954 posts
- 14. Kentucky 21.5K posts
- 15. Kam Williams N/A
- 16. Xochitl 3,340 posts
- 17. Lowe 11.1K posts
- 18. #DancingWithTheStars 1,013 posts
- 19. Carrie Ann 1,697 posts
- 20. Meredith 3,441 posts
Something went wrong.
Something went wrong.