dougy
@R3dHash
Cyber Threat Intelligence | OSINT | Misinformation | Threat Hunting
You might like
We are excited that we were once again part in the coordinated international operation #OpEndgame 📣, taking action against the notorious information and credential stealer #Rhadamanthys 🕵️ We assisted in the takedown of threat actor infrastructure and share a full list of…

Possible new leak of internal Conti / Trickbot chats A valuable dataset of internal communications that appears to be missing from public leaks. Some conversations are dated 2019. Not previously published in Conti-Leaks; partially overlaps with Trick-Leaks, but in a different…
When you think there’s a new APT in town... Relax, it’s just our Red Team doing their thing (thanks to @Defte_ technique)😅 Want to improve your detections or challenge your team? Contact us!
⚠️ Our threat intel team just caught attackers using a clever new trick to bypass security tools: cache smuggling. Instead of downloading malware, they hide it in fake images that browsers automatically cache. Then PowerShell extracts and runs it—no web requests needed.

Proud to support our Law Enforcement partners in another successful cybercrime disruption: Operation SIMCARTEL Great work everyone involved 👏 europol.europa.eu/media-press/ne…


⚠️ Breach Notification from F5 Networks: “In August 2025, we learned a highly sophisticated nation-state threat actor maintained long-term, persistent access to, and downloaded files from, certain F5 systems.” my.f5.com/manage/s/artic…
Now you know why the China tab in the APT spreadsheet is the biggest one. You can only imagine the scale of damage their industrial espionage caused - and why some believe it’s far worse than anything ransomware groups ever did.
From software, equipment to materials, China is reconstructing an entire ecosystem inside the country

We are releasing details on BRICKSTORM malware activity, a China-based threat hitting US tech to potentially target downstream customers and hunt for data on vulnerabilities in products. This actor is stealthy, and we've provided a tool to hunt for them. cloud.google.com/blog/topics/th…
Following the @volatility parity release, VolWeb v3.15.0 is now available with some new features like Linux “Explore” support. Checkout the release note here: forensicxlab.com/blog/volweb-3-… Project: github.com/k1nd0ne/VolWeb #DFIR




CyberNews pushed the same fucking story last year. It's even written by the same author. You can't keep fear mongering people every time a Threat Actor assembles a data leak package


An indictment was unsealed yesterday charging four foreign nationals with operating botnet services that targeted thousands of wireless internet routers. The conspirators allegedly amassed more than $46 million from selling access to infected routers. justice.gov/usao-ndok/pr/b…

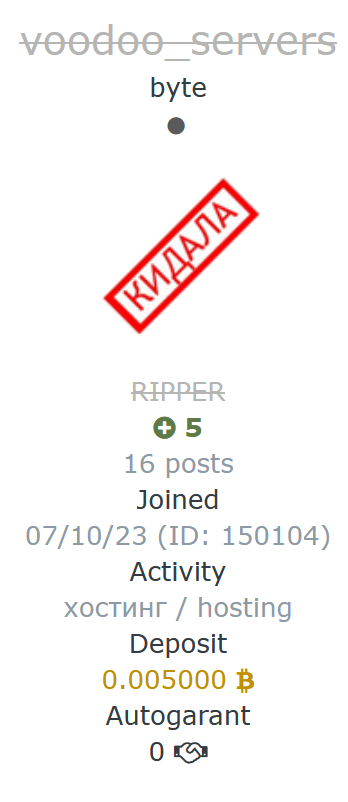
Bearhost (aka UNDERGROUND and recently VOODOO SERVERS), alledgelly the "biggest bulletproof hosting" has decided to do an exit scam after several years of service, leaving a "farewell note" in forums and shutting down servers suddenly with no further reasons @spamhaus @abuse_ch


🚨 A major blow to ransomware ops: Medialand, a core BPH linked to Yalishanda (LARVA-34), exposed. Used by BlackBasta & others. Likely same actors behind Feb 11 BlackBasta leak. This leak offers rare, high-value insight into cybercriminal infrastructure. #ThreatIntel

🚨 Ivanti Vulnerability (CVE-2025-22457) Actively Exploited Mandiant & Ivanti discovered active exploitation of a critical buffer overflow vulnerability in Ivanti Connect Secure VPN, leading to remote code execution. Patch now to secure your systems: bit.ly/4iTpKdD

🔎 [THREAD] – New analysis by Intrinsec Cyber Threat Intelligence on the latest operations by Russian-aligned intrusion sets #UAC0050 & #UAC0006📢 🔗 Our Report: intrinsec.com/wp-content/upl…
Our Indicators of Compromise blog post for CVE-2025-2825, an authentication bypass affecting #CrushFTP. horizon3.ai/attack-researc…
False positives happen - it’s just part of managing community-driven data! 🤷 But transparency is key, that's why we’ve rolled out a consolidated False Positive List... 🔍 Now you can identify false positives across our platforms via API, with CSV or JSON export options. Find…

🚨 Suspicious French-themed domains spotted in the Prospero OOO (RU) range! 🚨 A cluster of domains mimicking BNP Paribas, Ameli, La Poste, Netflix, and more—likely set up for fraud. Stay vigilant! 🕵️♂️ Examples: 15-bnpparibas[.]com 5-bnpparibas[.]com 8-bnpparibas[.]com…
We have received the following comment from Kaspersky which we would like to share with you ⤵️ "Kaspersky is aware of the public claim about the company's allegedly providing services to a "bulletproof" web hosting provider. Kaspersky denies these claims as the company does not…
United States Trends
- 1. #NXXT_Earnings N/A
- 2. #FanCashDropPromotion N/A
- 3. Good Friday 47.9K posts
- 4. Summer Walker 21.5K posts
- 5. #FridayVibes 3,955 posts
- 6. #GringosVenezuelaNoSeToca 1,342 posts
- 7. #FinallyOverIt 7,001 posts
- 8. Wale 36K posts
- 9. Happy Friyay 1,197 posts
- 10. Go Girl 25.9K posts
- 11. RED Friday 2,591 posts
- 12. Meek 6,222 posts
- 13. Saylor 30.7K posts
- 14. $BTC 120K posts
- 15. SONIC RACING 2,390 posts
- 16. Robbed You 4,704 posts
- 17. Bubba 8,901 posts
- 18. Monaleo 2,327 posts
- 19. For Christ 22.5K posts
- 20. 1-800 Heartbreak 1,876 posts
You might like
-
 Chris Duggan
Chris Duggan
@TLP_R3D -
 Will
Will
@BushidoToken -
 Shadow Chaser Group
Shadow Chaser Group
@ShadowChasing1 -
 𝕚𝕟𝕕𝕚𝕧𝕚𝕕𝕦𝕒𝕝 𝕓
𝕚𝕟𝕕𝕚𝕧𝕚𝕕𝕦𝕒𝕝 𝕓
@bumbl3r -
 Thomas Roccia 🤘
Thomas Roccia 🤘
@fr0gger_ -
 Chuong Dong
Chuong Dong
@cPeterr -
 3xp0rt
3xp0rt
@3xp0rtblog -
 Tommy M (TheAnalyst)
Tommy M (TheAnalyst)
@ffforward -
 Intel 471
Intel 471
@Intel471Inc -
 Tony Lambert
Tony Lambert
@ForensicITGuy -
 Dee
Dee
@ViriBack -
 Sekoia.io
Sekoia.io
@sekoia_io -
 Jiří Vinopal
Jiří Vinopal
@vinopaljiri -
 Kostas
Kostas
@Kostastsale -
 Tatyana Shishkova
Tatyana Shishkova
@sh1shk0va
Something went wrong.
Something went wrong.