
JM
@SourceFrenchy
Dad, husband & Security dinosaur. Former @MatroxVideo, @Ubisoft, @Canary, @PdtPartners. 🫶Sec. Mgnt., IR, OffSec, Sec Eng. & National Security
Вам может понравиться
Thanks again for allowing me to present! Slides available at github.com/sourcefrenchy/…
This is a super useful example of what every org should be maintaining with their own internal service dependencies (on both other internal services/infra and 3rd-party infra).
I put together a service dependency diagram based on what has been mentioned in today's AWS outage, along with Monday's, and one from Nov 25, 2020 with color coding based on which outage mentioned the dependency.

Aardvark is a labor of love and mission for the whole team. We are super excited to bring it to you. Sign up for the beta immediately!!!
Now in private beta: Aardvark, an agent that finds and fixes security bugs using GPT-5. openai.com/index/introduc…

Lateral movement across server room? Steven Flores (@0xthirteen) of @SpecterOps describes a new fancy WMI class that can be used to move laterally between Windows server boxes. Also, mentions methods of extending this tactic to workstations. Post: specterops.io/blog/2025/09/1……

A penetration tester got root access to our Kubernetes cluster in 15 minutes. Here's what they exploited. The attack chain: - Found exposed Kubernetes dashboard (our bad) - Dashboard had view-only service account (we thought this was safe) - Service account could list secrets…
This is by far the best post on advanced Claude Code usage I've seen, tapping the power of hooks to context engineer and prevent slop. Only thing missing is that OP can use plugins (agents+hooks+commands+MCP) to distribute their amazing work! reddit.com/r/ClaudeAI/com…
Malware spreading via WhatsApp with multi-vector persistence & sophisticated C&C. Investigation shows the consistent use of Portuguese, which suggest the threat actor’s focus on Brazil. The most sophisticated aspect of the backdoor is its email-based C&C infrastructure. Rather…




We’re hiring offensive security researchers @Apple SEAR! We’re looking for skilled researchers across multiple security domains. Learn more and apply here: jobs.apple.com/en-us/details/… If you’re into low level systems like firmware, RTOS, coprocessors, embedded components, or…
NEW: exec at zero-day supplier pleads guilty to selling to buyer in Russia. FBI had warned elite supplier Trenchant about a potential leak in 2024... Appears that Peter Williams was leading the internal investigation & meeting with FBI even as he did deals. Wild. He's…




Here's my Wired story about his guilty plea and what prosecutors revealed in this morning's hearing: wired.com/story/peter-wi…
Raw NTFS parsing for SAM/SYSTEM/NTDS.dit access? github.com/kfallahi/Under… 400 lines Powershell - easy peasy ❤️🔥

🛠️ HikvisionExploiter HikvisionExploiter is a powerful and automated exploitation toolkit targeting unauthenticated endpoints on Hikvision IP cameras, particularly those running firmware version 3.1.3.150324. github.com/HexBuddy/Hikvi…

CVE-2025-55752 - exploit poc for the Apache Tomcat Rewrite Valve Relative Path Traversal, no RCE (for now) #pruva tried to fake it playing witht he rewrite, relaxing it a lot, but after some pass was able to reproduce. gist.github.com/N3mes1s/013061…


CVE-2025-55752 Apache Tomcat possible RCE if PUT is enabled 🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡🤡 This is like saying i can extract your data from db if sql query is enabled

GRU's Spy Airbnb: check out our latest video investigation into Unit 29155, and the "Czech" spy couple they used to help them plant explosives in weapons depots. youtu.be/tRqcJV0Z55c?si…

youtube.com
YouTube
Russia's Spy Hotel | Unit 29155 - Episode 5
Harvard professor literally dropped the best ML systems tutorial you’ll ever see

Carl Sagan's brilliant answer to a question regarding the Existence of God.
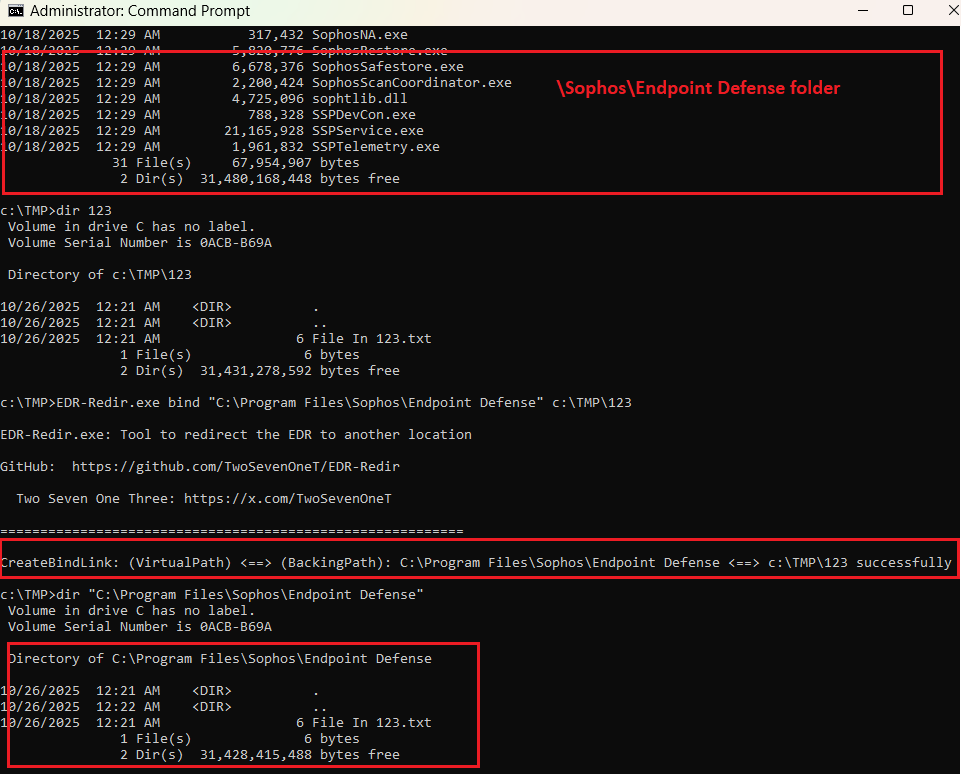
EDR-Redir: You can break EDRs/Antivirus from user mode with bind link and cloud minifilter. Because your payload deserves privacy. #antimalware #itsecurity #redteam

China releases 'UBIOS' standard to replace UEFI — Huawei-backed BIOS firmware replacement charges China's domestic computing goals tomshardware.com/software/china…
🚨CVE-2025-59287 PoC: gist.github.com/hawktrace/76b3… Blog: hawktrace.com/blog/CVE-2025-… Microsoft: learn.microsoft.com/en-us/windows/… Windows Server 2025 (KB5070881) Windows Server, version 23H2 (KB5070879) Windows Server 2022 (KB5070884) Windows Server 2019 (KB5070883) Windows Server 2016…
🚨CVE-2025-59287: Deserialization of untrusted data in Windows Server Update Service allows an unauthorized attacker to execute code over a network. CVSS: 9.8 Microsoft releases out-of-band (OOB) urgent fix for actively exploited WSUS vulnerability: helpnetsecurity.com/2025/10/24/wsu…
New drop from the Three Buddy Problem: Apple’s iOS forensics freeze, WhatsApp zero-click, China outs NSA securityconversations.com/episode/apples…

Never judge a book by its cover - or a website by its default IIS page! 😄 Default IIS page → Sql Injection 🔥 Want the full writeup? Follow me & stay tuned! 👇 mugh33ra.medium.com #BugBounty #SQLinjection #WebSecurity #hackerone #idor #sqlinjection #bugbountytip #xss


Reports indicate that the F5 BIG-IP source code leak is linked to state-sponsored campaigns utilizing the BRICKSTORM backdoor, highlighting ongoing cybersecurity threats. #Cybersecurity #F5BIGIP #BRICKSTORM resecurity.com/blog/article/f…
United States Тренды
- 1. Drake London 6,064 posts
- 2. Packers 38.4K posts
- 3. Colts 31.6K posts
- 4. Steelers 46.6K posts
- 5. FanDuel 36.8K posts
- 6. Falcons 25.7K posts
- 7. Bengals 32.7K posts
- 8. Daniel Jones 5,927 posts
- 9. Lions 53.7K posts
- 10. Jordan Love 7,746 posts
- 11. Bears 49.7K posts
- 12. Panthers 28.7K posts
- 13. Vikings 32.6K posts
- 14. Tee Higgins 4,487 posts
- 15. Parker Romo 1,012 posts
- 16. Caleb Williams 4,372 posts
- 17. #HereWeGo 4,969 posts
- 18. #Skol 3,205 posts
- 19. Matt LaFleur 1,822 posts
- 20. #NYGiants 3,700 posts
Вам может понравиться
-
 Alexandre Borges
Alexandre Borges
@ale_sp_brazil -
 DirectoryRanger
DirectoryRanger
@DirectoryRanger -
 Silas Cutler (p1nk)
Silas Cutler (p1nk)
@silascutler -
 🇺🇦 Joe Gray aka JOSINT 🇺🇦
🇺🇦 Joe Gray aka JOSINT 🇺🇦
@C_3PJoe -
 Richard Greenberg
Richard Greenberg
@RAGreenberg -
 Ethical Hacker
Ethical Hacker
@offethhacker -
 Spencer Walden
Spencer Walden
@__Masq__ -
 maldevel ☣
maldevel ☣
@maldevel -
 MrBill // wardrive every day //
MrBill // wardrive every day //
@SecureThisNow -
 JC
JC
@JC_SoCal -
 Securityblog
Securityblog
@Securityblog -
 Warren Mercer
Warren Mercer
@SecurityBeard -
 cryptopotato
cryptopotato
@cryptoishard -
 prakash kamalakannan
prakash kamalakannan
@sn0wli0n -
 Michael Farnum
Michael Farnum
@m1a1vet
Something went wrong.
Something went wrong.




































































































































































