Oluwatobi Mustapha
@Techboy150
Cloud Detection Engineer (AWS) | Threat Detection & Incident Response | IAM & Serverless Monitoring | Security+ Certified 📧:[email protected]
The “Linux is immune to malware” myth needs to die. I’ve watched this narrative shift in real-time. Yes, Linux is more secure than most alternatives. But “more secure” doesn’t mean “safe by default” – especially not anymore. Here’s what changed: As you know, your…
AWS Went Dark If you were online this week, you probably noticed the internet had a bad day. Especially Snapchat and Fortnite users. A major AWS DNS outage in us-east-1 disrupted large parts of the web, from APIs to SaaS platforms, all because of a single point of failure that…
AI is changing the way we build and ship software. With that shift comes a new security reality many teams are not ready for: the AI attack surface. From my experience in cloud security, I have seen how quickly AI systems are deployed and how easily new risks are introduced. It…
A compromised system doesn’t mean the whole network is lost. It’s just one step in the chain. Prevention will never be perfect. Breaches will happen. What matters is how fast you see it, contain it, and limit the blast radius. If one device falling means everything is gone, the…
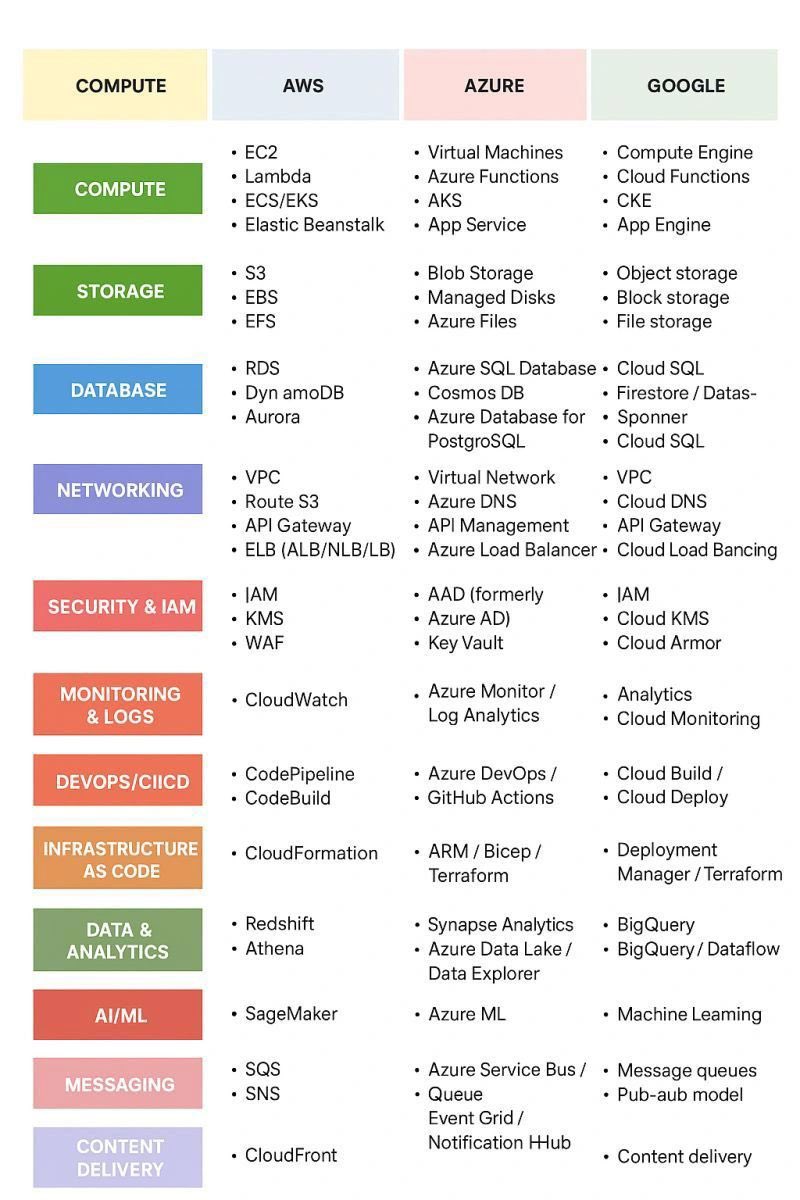
Cloud Services Showdown: AWS vs Azure vs Google Cloud Platform (GCP) 🌐
When most people study for AWS certifications, it looks like this: •Udemy for videos •Notion for notes •Quizlet for flashcards •probably tutorialsDojo for practice exams •YouTube and ChatGPT for more help I get it, I’ve done the same. But here’s the truth: it feels…
In the rush to deploy AI on cloud, teams forget: the models are smart, but the pipelines are blind. If you don’t monitor data access, your AI won’t just learn — it’ll leak.
Every time you see Action: * or Resource: * in an IAM policy, read it as “open invitation.” That’s how attackers escalate without anyone noticing. Least privilege isn’t theory, it’s survival.
IAM is discipline disguised as code. It’s not glamorous, but it decides who can touch what. Get it wrong once, and an attacker owns your environment. Get it right consistently, and you’ve built an invisible fortress.
To thrive in the cloud era, you need Linux. Most cloud servers, containers, and serverless functions run on it. Automate, secure, and scale faster if you know it.
Docker images from public registries = supply chain roulette. Attackers hide miners and backdoors in “useful” images. Rule 1: build from trusted base images, not random Docker Hub pulls.
Manual detection engineering doesn’t scale. Write detections like code: version them in Git, test in labs, deploy via CI/CD. That’s how you easily stay ahead of attackers.
AWS CloudTrail is not enough out of the box. Without S3 or Lambda Data Events, you will be blind to 70% of attacker actions. Turn them on.
I just went through this threat report by @wiz_io on the Shai-Hulud npm worm… and it’s wild. What actually happened is that attackers snuck bad code into npm packages. So if you installed one, it stole your secrets (tokens, API keys, cloud creds), leaked your repos, and even…

United States Trendy
- 1. #GivingTuesday 14.9K posts
- 2. The BIGGЕST 426K posts
- 3. #JUPITER 233K posts
- 4. #ALLOCATION 233K posts
- 5. #csm222 N/A
- 6. Lucario 14.1K posts
- 7. Costco 38.1K posts
- 8. #NXXT_NEWS N/A
- 9. Good Tuesday 39.1K posts
- 10. Susan Dell 2,339 posts
- 11. NextNRG Inc 1,235 posts
- 12. Michael and Susan 1,664 posts
- 13. Taco Tuesday 13.5K posts
- 14. Trump Accounts 7,656 posts
- 15. Hoss Cartwright N/A
- 16. King Von 1,097 posts
- 17. Dart 43K posts
- 18. Isack 14.6K posts
- 19. Project M 22.2K posts
- 20. Kanata 29.4K posts
Something went wrong.
Something went wrong.