Andrea Naspi
@andreanaspi
Msc Cybersecurity at @SapienzaRoma | Threat Hunting | Malware Analyst @nozominetworks
You might like
I'd like to share a project I've been working recently related to the #Bumblebee #loader. This #Python script allows you to quickly extract the C&C server configuration from the #Bumblebee process through PE-Sieve by @hasherezade github.com/AndreaNaspi/un… @cluster25_io
Our latest post has just gone live! In this one, we're looking at using Capstone Disassembler, Unicorn Emulation Framework, and Python to defeat encrypted stack strings within a Conti ransomware sample 0ffset.net/reverse-engine…
#Patchwork #Spyder v3 downloader delivering #Remcos RAT Campaign reference: mp.weixin.qq.com/s?__biz=MzI2MD…
As P2PInfect raises #cybersecurity concerns, our Labs team identified a strain of #P2Pinfect that targets a new #IoT architecture – ARM. Read this blog to learn about recent P2PInfect worm operations & behavior, and the implications for digital #security: ow.ly/7C9E50QrH7C

Today, the pro-Palestinian hacker group "Islamic Cyber Team Indonesian" claims to have hacked the #FBI. Two compressed archives, referring to FBI data, totaling about 7GB were shared on their telegram channel. In the message, numerous pro Palestinian collectives have been quoted



Good news for #obfuscator/#packer researchers, the complete #VMProtect (v3.5.1) source code has just been leaked! 🔥 e41e4c6048abddeb5f3652bfb5036927f3e49b4a02b558d72839c9ebcf2c7e98 First submission: 2023-12-07 08:38:30 UTC

#GoTitan #botnet samples available on VT, have a good hunt! 9f639212aa8f31b4bf45adb9a8008502 e32a5b9c58c3e40d2246b7774cb4fb33

Fortinet researchers detail the Apache ActiveMQ CVE-2023-46604 exploitation and provide insights into the malware associated with these recent attacks, such as the newly discovered Golang-based botnet named GoTitan and a .NET program called PrCtrl Rat. fortinet.com/blog/threat-re…

Yesterday, the pro-Rus hacker group #XakNet Team claims to have "hacked #NATO." They shared an Excel containing personal information about natoschool students (elearning.natoschool.nato.int). In addition, they shared a series of accounts on the said platform. Screenshots:




#Honeypots are essential tools for threat hunting, primarily used to lure #cyberattackers. They can also help warn that an intrusion attempt is happening, and improve our understanding of #threats. Learn how to set up & use an #IoT #honeypot: ow.ly/E2t050QcBti

OK, this morning I'm doing to go cruising with #Censys ############################ You all have very specific custom config ############################# "Very Secure FTP Daemon" HTML Fingerprint HTML Title: "404 That's an Error" 8.130.12.120 47.251.45.4 86.57.172.226…


Tried hunting for DarkGate servers ? Try using this search term on Censys. -> (Autoit3.exe) and services.service_name=`DARKGATE` Censys: 10 results #darkgate #threathunting #malware #threatintelligence #threatintel


It’s very common for us to see offensive tooling enable SeDebugPrivilege so that they may bypass certain OS checks. However, what does this mean? Which OS checks are skipped? I dove into this and decided to write a blog on it. Check it out! bit.ly/3trYxdg
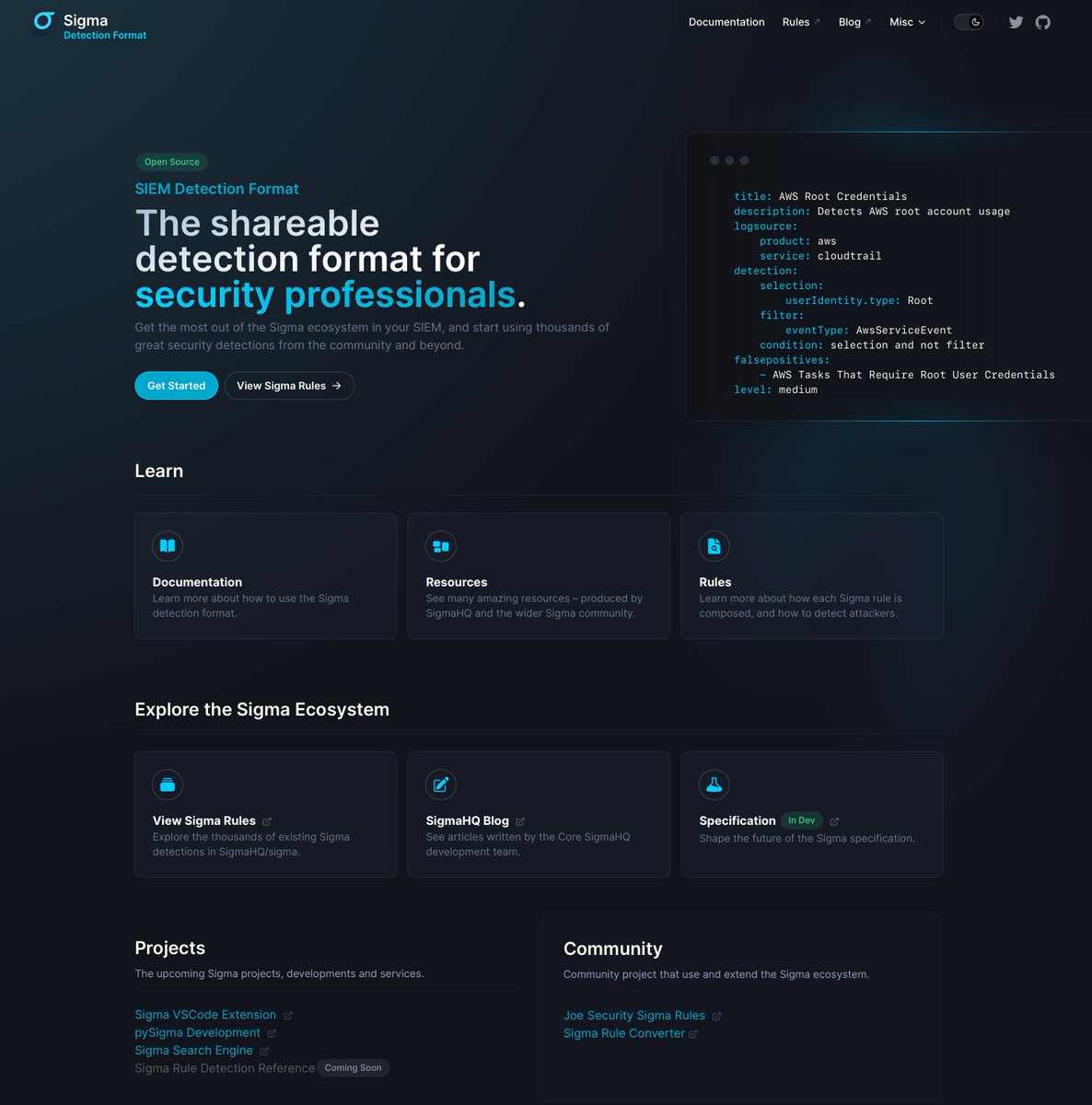
We're pleased to announce the launch of our new website Access resources, documentation, and community projects to enhance your experience with the Sigma Rule Standard Special thx to @sifex for the hard work! Blog: medium.com/sigma-hq/intro… Explore now: sigmahq.io


#APT #Saaiwc #DarkPink #CVE-2023-38831 Keputusan Permohonan Mendapatkan Perkhidmatan Penceramah Luar Untuk Program Anjuran Kementerian Pertahanan\.zip ac28e93dbf337e8d1cc14a3e7352f061 fefe7fb2072d755b0bfdf74aa7c9013e Final payload is #TelePowerBot


United States Trends
- 1. #FinallyOverIt 4,170 posts
- 2. Justin Fields 9,823 posts
- 3. Summer Walker 14.2K posts
- 4. 5sos 20.2K posts
- 5. Jets 68.1K posts
- 6. #criticalrolespoilers 3,580 posts
- 7. Patriots 149K posts
- 8. Drake Maye 20.6K posts
- 9. Jalen Johnson 7,724 posts
- 10. 1-800 Heartbreak 1,111 posts
- 11. Judge 199K posts
- 12. Go Girl 25K posts
- 13. Henderson 22.2K posts
- 14. AD Mitchell 2,398 posts
- 15. Wale 32.5K posts
- 16. #everythingisalot N/A
- 17. Santana 14.2K posts
- 18. Disc 2 N/A
- 19. Pats 14.5K posts
- 20. Rainbet 2,627 posts
Something went wrong.
Something went wrong.