cyberprotocol
@cyberprotocol1
The Oompa Loompa of cybersecurity
North Korea's State-Sponsored APTs Organize & Align: informatech.co/3RSP499 by Elizabeth Montalbano
Check out my guest write-up on the MaliciousGroup blog. If you're interested in C, inline assembly, and return address spoofing, this is the writeup you're looking for. @deadvolvo blog.malicious.group/inline-assembl…
North Korean looking MQ-9 vs USAF MQ-9 Question: who/how shared the design plans?

OSINT TIP #176 🛰️ SatIntel is an OSINT tool for Satellites. Extract satellite telemetry, receive orbital predictions & parse TLEs 🔭, made with Golang! github.com/ANG13T/SatIntel Article: medium.com/@angelinatsubo… Creator: @AngelinaTsuboi 👏👏 #OSINT #infosec #geoint #satellite

🔥 Big update! Nanodump now supports the PPLMedic exploit! meaning you can dump LSASS on an up-to-date system with PPL enabled 😃 github.com/fortra/nanodump
Awesome @TrustedSec #Sysmon videos by @Carlos_Perez Part 1 youtu.be/kESndPO5Fig Part 2 youtu.be/MlGc44dfFBg Part 3 youtu.be/2JHjRR2Wt4g Part 4 youtu.be/VKVSedPGDgY Part 5 youtu.be/KBsEAaZFcyI Part 6 youtu.be/46-alN2_vlo Part 7 youtu.be/cN714yh7UF4…

youtube.com
YouTube
Learning Sysmon - File Create Time (Video 7)
Modular Incident Response Plan

PowerShell has a list of suspicious keywords. If found in a script block an automatic 4104 event will be generated regardless of logging policy :) (True for both PWSH 5/7) Look for EID 4104 with Level 3 (Warning) Full List: gist.github.com/nasbench/50cd0…


That's a pretty interesting @VirusTotal graph by abvcti_brs #3CX #3CXpocalypse virustotal.com/graph/g84bdefb…


Need a full AD lab with 20 windows servers +Kali+win logging+sysmon+splunk to test attack techniques and review the resulting telemetry ? Attack Range has your covered in ~30m ⌨️python attack_range.py build Config🔗gist.github.com/mvelazc0/77013… Attack Range 🔗 github.com/splunk/attack_…

UPDATED POSTER | #FOR585: #SmartphoneForensics - Includes new artifacts in iOS15/16 and Android 12 -Most relevant #MobileForensics Resources -Free scripts and helpful utilities DOWNLOAD NOW 👉sans.org/u/1o5b @HeatherMahalik @mattiaep @domenicacrognal #DFIR

Hive Ransomware’s Tor Infrastructure justice.gov/opa/pr/us-depa…




The photo of the U.S. Air Force's new stealth aircraft is on the left, taken at night, with stars in the background. We can use them to find the exact location of the jet (thread)
Unveiled today, the B-21 Raider will be a dual-capable, penetrating-strike stealth bomber capable of delivering both conventional and nuclear munitions. The B-21 will form the backbone of the future Air Force bomber force consisting of B-21s and B-52s.(U.S. Air Force photo)


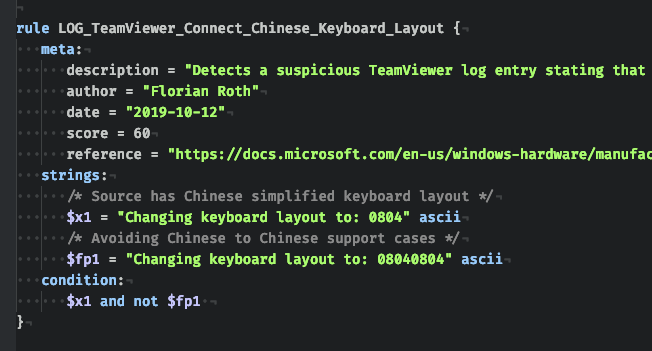
RT because a @thor_scanner user just recently noticed matches with YARA rules for RU keyboard layouts in his environment and contained the threat It’s useful forensic evidence #DFIR
It seems that #TeamViewer logs contain info on the keyboard layouts of both source & target system This can be used for some nifty YARA or Sigma rules like: - Alert on Chinese (e.g. APT41) remote keyboard layouts but exclude CN to CN support sessions


Over the last couple of years, me and my team have covered a lot about #Linux #DFIR. Lots of system and GUI artifacts has been covered and can be found here: github.com/ashemery/Linux…
Policía holandesa consigue recuperar 155 claves de descifrado del ransomware Deadbolt (QNAP y Asustor) para que sus víctimas puedan recuperar sus archivos de forma gratuita deadbolt.responders.nu

This is not a late "April Fool." This is real. I've been waiting months to say it. Now it's public. @Microsoft is embedding @Zeekurity into @Windows. This brings #networksecuritymonitoring to a potential billion+ endpoints. Hear Microsoft's take, Thu-Fri: zeek.org/zeekweek2022/
🧵We are excited to share that @Zeekurity is now a component of @Microsoft @Windows ! An incredible development that truly establishes Zeek as the de facto standard for #networkevidence: corelight.com/company/zeek-n… 1/4
Yamato Security's Ultimate Windows Event Log Configuration Guide For DFIR And Threat Hunting (especially for sigma users) github.com/Yamato-Securit… & github.com/Yamato-Securit…




United States Trends
- 1. Veterans Day 429K posts
- 2. Woody 18.1K posts
- 3. Tangle and Whisper 4,796 posts
- 4. Jeezy 1,754 posts
- 5. State of Play 32.5K posts
- 6. Toy Story 5 24.6K posts
- 7. Errtime N/A
- 8. #ShootingStar N/A
- 9. Luka 86.2K posts
- 10. AiAi 12.7K posts
- 11. NiGHTS 58.6K posts
- 12. Gambit 49.4K posts
- 13. Nico 149K posts
- 14. Wanda 32.7K posts
- 15. #SonicRacingCrossWorlds 3,214 posts
- 16. Tish 7,061 posts
- 17. Antifa 210K posts
- 18. SBMM 1,951 posts
- 19. Nightreign DLC 16K posts
- 20. Marvel Tokon 3,205 posts
Something went wrong.
Something went wrong.