
Ahmed ElDeeb
@elldeeboo2
Cyber Security Engineer
คุณอาจชื่นชอบ
Work on a program for 9 months , The result is a good understanding of the site, despite the number of 9,000 vulnerabilities reported I am still able to report critical reports happy hunting $$$$$ 🔥



SQLi Automation by @coffinxp7 tool Automation script github.com/freelancermija… #sqli #BugBounty
🎩🎩Search engines for osint🎩🎩 leak.sx scylla.sh intelx.io 4iq.com leaked.site hashes.org leakcheck.io vigilante.pw leakcheck.net weleakinfo.to…
من الحاجات اللي كنت مهتم بيها مؤخرا هي Dark Web OSINT و ازاي اقدر ادور علي المعلومة علي الDark Web او اتأكد من صحتها او مصدرها , فالثريد ده هشارك معاكوا شوية معلومات لذيذة عن الموضوع و فالاخر هحط مصادر لو حد حابب يتعمق فالموضوع ده

Account takeover techniques

Cloudflare XSS bypass : ">%20<img src=o onerror=alert``>// github.com/Edr4/XSS-Bypas…

ثغرة Deeplink من الثغرات ال Android الذيذه جدا وده رايت اب انا كتبتها حالل فيها تلات apps vulnerable لثغرة deeplink وفيها شرح للثغره علي قد كده link writeup: medium.com/@Sisi0x/androi… وكمان سايبلك لكن تحميل apps علشان تطبق عليهم ان شآء الله
1 install waymore tool waymore.py -i domain -mode U And send all the results to burp 2 start bing and google dorking on the same proxy browser to get all the results to burp 3 install GAP extension and then send the target to GAP there’s lot to do, this start
من فتره للتانيه بحاول ادخل اهانت على h1 , BC كنوع من التغيير . ولكن كل مره اخد فيها N/A او Duplicate بشكل غير طبيعى . ارجع تانى اهانت ف الاماكن بتاعتى المتعود عليها . سؤال هنا مهم ! هل منطقى اخد duplicate على Report اتعمل من سنه كامله ؟

Embed A Malicious Executable in a Normal PDF or EXE : medium.com/@sam.rothlisbe…
Automating SSRF using Autorepeater In the window of Auto-Repeater, we can specify some regex to find urls. 👉 https?:\/\/(www\.)?[-a-zA-Z0–9@:%._\+~#=]{1,256}\.[a-zA-Z0–9()]{1,6}\b([-a-zA-Z0–9()@:%_\+.~#?&//=]*) By:@akaclandestine #bugbountytips #BugBounty
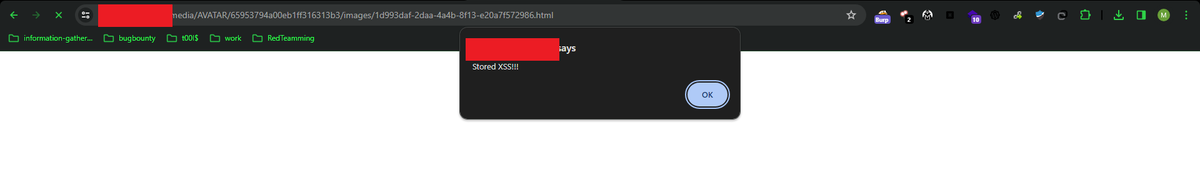
Tip for Stored XSS Bypass on Profile Uploader: +add magic number (jpg , jpeg) +bypass file extention Protection #BugBounty #bugbountytips #bugbountytip #Pentesting

“How I got RCE on 403 admin.redacted.org” by Shivpratapsingh medium.com/@shivpratapsin…

When you are hunting for blind XSS. Go to forget password and add admin@company .com and add your blind XSS payload on the header. Easy way and it will logged on admin log, if he checked his account you will exploit his account. #bugbountytips

United States เทรนด์
- 1. Dodgers 640K posts
- 2. #WorldSeries 311K posts
- 3. Yamamoto 196K posts
- 4. Blue Jays 143K posts
- 5. Will Smith 46.6K posts
- 6. Miguel Rojas 39.8K posts
- 7. Kershaw 30.5K posts
- 8. Yankees 15K posts
- 9. Baseball 157K posts
- 10. Dave Roberts 12.3K posts
- 11. Kendrick 16.4K posts
- 12. Vladdy 21.3K posts
- 13. Ohtani 83.5K posts
- 14. #Worlds2025 26.5K posts
- 15. Jeff Hoffman 3,508 posts
- 16. Auburn 14.2K posts
- 17. Nike 34.9K posts
- 18. Cubs 7,453 posts
- 19. Phillies 3,464 posts
- 20. Miggy 8,129 posts
คุณอาจชื่นชอบ
-
 Abdelhy khaled🦅
Abdelhy khaled🦅
@cysky0x1 -
 Abdelrhman Amin🇵🇸
Abdelrhman Amin🇵🇸
@0xUchihamrx -
 Marwan Elsayyad
Marwan Elsayyad
@0xMalWan -
 Hagar Yousef
Hagar Yousef
@alien0x_ -
 Mohamed Mater🇵🇸
Mohamed Mater🇵🇸
@micro0x00 -
 Abdelrhman Allam 🇵🇸
Abdelrhman Allam 🇵🇸
@sl4x0 -
 Rahmat Qurishi
Rahmat Qurishi
@RahmatQurishi -
 ᴀʙᴅᴇʟʀʜᴍᴀɴ ᴢᴀʏᴇᴅ
ᴀʙᴅᴇʟʀʜᴍᴀɴ ᴢᴀʏᴇᴅ
@aufzayed -
 Sir. Zeus
Sir. Zeus
@Eyhuss1 -
 Vulnera 🇪🇬
Vulnera 🇪🇬
@0xvulnera -
 /usr/bin/fares
/usr/bin/fares
@SirBagoza -
 Ahmed Rabeaa Mosaa
Ahmed Rabeaa Mosaa
@AhmedMosaa18 -
 Ahmed Gad
Ahmed Gad
@0xGAD -
 Mohamed reda ameen
Mohamed reda ameen
@AlQa3Qa3M0x0101 -
 Naeem Ahmed Sayed 🇧🇩
Naeem Ahmed Sayed 🇧🇩
@0xNaeem
Something went wrong.
Something went wrong.




























































































































































