You might like
We're so relieved to see Germany reaffirm its opposition to the dangerous Chat Control proposal--the one that would mandate mass scanning of communications. Germany's long been a solid champion of privacy, and the news that it was considering backing mass surveillance was…
📣 Germany is close to reversing its principled opposition to mass surveillance & private message scanning, & backing the Chat Control bill. This could end private —& Signal—in the EU. Time is short and they're counting on obscurity: please let German politicians know how…
We are alarmed by reports that Germany is on the verge of a catastrophic about-face, reversing its longstanding and principled opposition to the EU’s Chat Control proposal which, if passed, could spell the end of the right to privacy in Europe. signal.org/blog/pdfs/germ…
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
Today we unveil BadSuccessor - a new no-fix Active Directory privilege escalation technique. We will explore the recently introduced dMSA feature, and show how it enables turning a very common, seemingly benign permission, into a full domain take over. akamai.com/blog/security-…
#RustPack Version 1.2.0 is now released for our customers. The biggest change was to add full DInvoke support for all payloads. The import table now won't show the Windows APIs being used anymore, instead by default random non malicious imports are added in here to make payloads…
New blog from me on using CLR customizations to improve the OPSEC of your .NET execution harness. This includes a novel AMSI bypass that I identified in 2023. By taking control of CLR assembly loads, we can load assemblies from memory with no AMSI scan. securityintelligence.com/x-force/being-…
Few BloodHound python updates: LDAP channel binding is now supported with Kerberos auth (native) or with NTLM (custom ldap3 version). Furthermore, the BH CE collector now has its own pypi package and command. You can have both on the same system with pipx. github.com/dirkjanm/Blood…
18 hacking books. Name your price. Our Hacking 2024 @humble bundle is now LIVE. Support @ACLU & @EFF while leveling up your security game. #CyberMonday humblebundle.com/books/hacking-…

Yesterday I finally finished part II of my anti rootkit evasion series, where I showcase some detections for driver "stomping", attack flawed implementations of my anti-rootkit, hide system threads via the PspCidTable and detect that as well. Enjoy! eversinc33.com/posts/anti-ant…
eversinc33.com
(Anti-)Anti-Rootkit Techniques - Part II: Stomped Drivers and Hidden Threads
Detectin driver 'stomping' and hiding system threads by manipulating the PspCidTable.
CVE-2024-39825 and CVE-2024-39818: High-Risk Zoom Flaws Require Urgent Updates securityonline.info/cve-2024-39825…
This year it happened. What started as a spare time hobby and fun project became a commercial product for the Offensive Security community. I founded a company, @MSecOps . And this company will sell a Packer to Red Teams or Pentesters. (1/x) 🔥
🔥 Introducing RustPack 🔥 . RustPack is an evasive Packer/Loader, that is capable of bypassing common AV/EDR vendors. It accepts user-provided known malicious input payloads, such as shellcode, C# assemblies or portable executables (PE). Those inputs are encrypted, and…

Tomorrow 1 pm ECT I’ll do a stream about stable DLL Sideloading for persistence 🙌 twitch.tv/s3cur3th1sshlt
One year ago, @T00uF and I did a talk at @_leHACK_ about DPAPI and #DonPAPI. Well, we've completely rewritten it to add a lot of new features. DonPAPI 2.0 available now 🚀 ▶️github.com/login-securite…
Who's ever received one of these "pentest" reports?

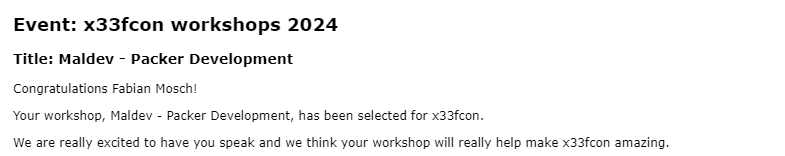
Join us for "Maldev - Packer Development" with @ShitSecure and @eversinc33. Learn to build your own packer and evade AV/EDR detections. Perfect for intermediate-level participants. Register now: x33fcon.com/#!conference.m… Full workshop details: x33fcon.com/#!w/FabianMosc… #x33fcon…

Looks like @ShitSecure and me are giving a workshop at @x33fcon this year👀We will be talking about packer development and help you to build your own packer for dropping malware in protected environments. Be there or be square🟥
Yeeah! 🔥🔥🔥🔥 Looks like @eversinc33 and I will give a Maldev Workshop at @x33fcon 2024! 😎Looking forward for that but also for this conference in general 🥰 Pirate Ship, we are ready 🏴☠️🦜
I'll spontaneously go live within the next hour to build some AI powered Packer Malware starting by 0: twitch.tv/S3cur3Th1sshlt Let's see how far we can get in 1-2 hours when using AI.
New blogpost and small tool release: Wrote a naive anti-rootkit driver that detects mapped drivers, and talk about some bypasses for those detections in part I of my new (anti-)-anti-rootkit series. More research on rootkit evasion coming soon : ) eversinc33.com/posts/anti-ant…
I'm pumped to announce the release of Misconfiguration Manager, a knowledge base and how-to for both offensive and defensive SCCM attack path management, that @subat0mik, @garrfoster, and I have been working on! Check it out and let us know what you think! posts.specterops.io/misconfigurati…
Some Windows Event IDs and how they help defenders. #ThreatHunting #DFIR
United States Trends
- 1. Pond 243K posts
- 2. Daboll 37.3K posts
- 3. Veterans Day 22.6K posts
- 4. Jimmy Olsen 3,279 posts
- 5. Go Birds 13.3K posts
- 6. McRib 1,634 posts
- 7. Downshift N/A
- 8. #OTGala8 121K posts
- 9. Schoen 19.4K posts
- 10. Akira 27.5K posts
- 11. Zendaya 10.4K posts
- 12. Biker 4,070 posts
- 13. American Vandal 1,871 posts
- 14. #FlyEaglesFly 5,943 posts
- 15. Gorilla Grodd 1,781 posts
- 16. Mecole Hardman N/A
- 17. Nene Leakes N/A
- 18. Hanoi Jane 1,475 posts
- 19. Johnny Carson 1,043 posts
- 20. #EmmettJohnson N/A
You might like
-
 woshub - Windows OS Hub
woshub - Windows OS Hub
@woshub -
 Diego Capriotti
Diego Capriotti
@naksyn -
 Fabre Pierre-jean
Fabre Pierre-jean
@FabrePierrejean -
 TruBluFan / @[email protected]
TruBluFan / @[email protected]
@TheTruBluFan -
 Michael 🆘
Michael 🆘
@matonis -
 Jannis Grunewald
Jannis Grunewald
@HerrGrunewald -
 Ilan Kalendarov
Ilan Kalendarov
@IKalendarov -
 смех
смех
@0x6D6172636F -
 Zach Stein
Zach Stein
@synzack21 -
 Tushar
Tushar
@0xdeadpool -
 hybr
hybr
@hybr10 -
 Magpie
Magpie
@malwaremagpie -
 TIGER❤️🅰️ST SP🅰️CE
TIGER❤️🅰️ST SP🅰️CE
@tigeryu2001 -
 I🇺🇸
I🇺🇸
@Ian313f -
 Paul Moriarty
Paul Moriarty
@pmoriarty
Something went wrong.
Something went wrong.