Programm.r
@thatCoding_Yogi
Software Developer | DevOps Engineer | Cyber Security Engineer.
You might like
🔎 𝗢𝗦𝗜𝗡𝗧-𝗦𝗔𝗡 Herramienta desarrollada por investigadores rusos para realizar OSINT (Open Source Intelligence). Compatible con Kali Linux 🐉 y Parrot OS 🦜. - En este repositorio encuentras la versión gratuita, aunque también existe una opción premium que puedes…

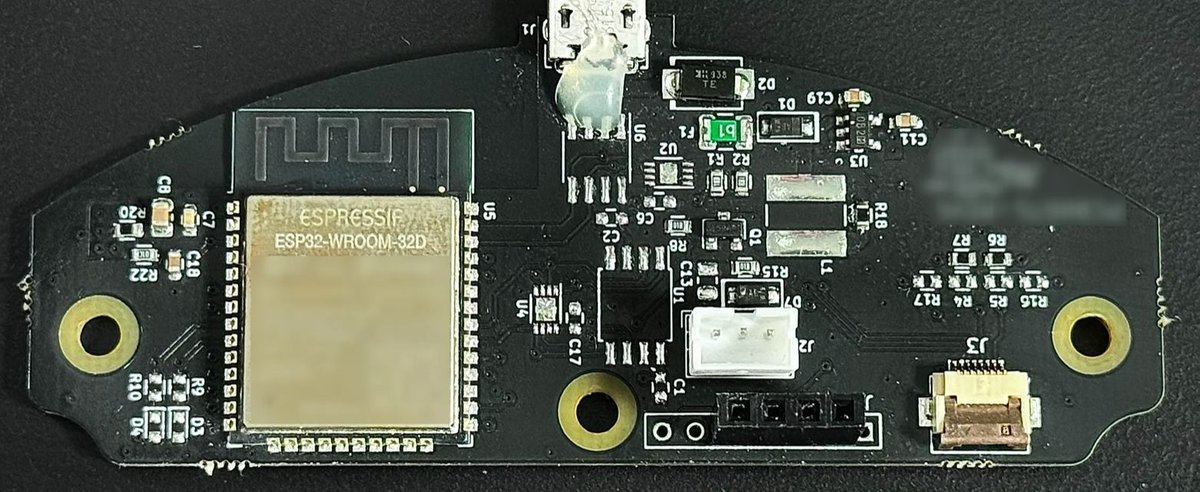
Reverse engineering and security analysis of an ESP32 based IoT device jmswrnr.com/blog/hacking-a… Great blog post by @jmswrnr #esp32 #cybersecurity

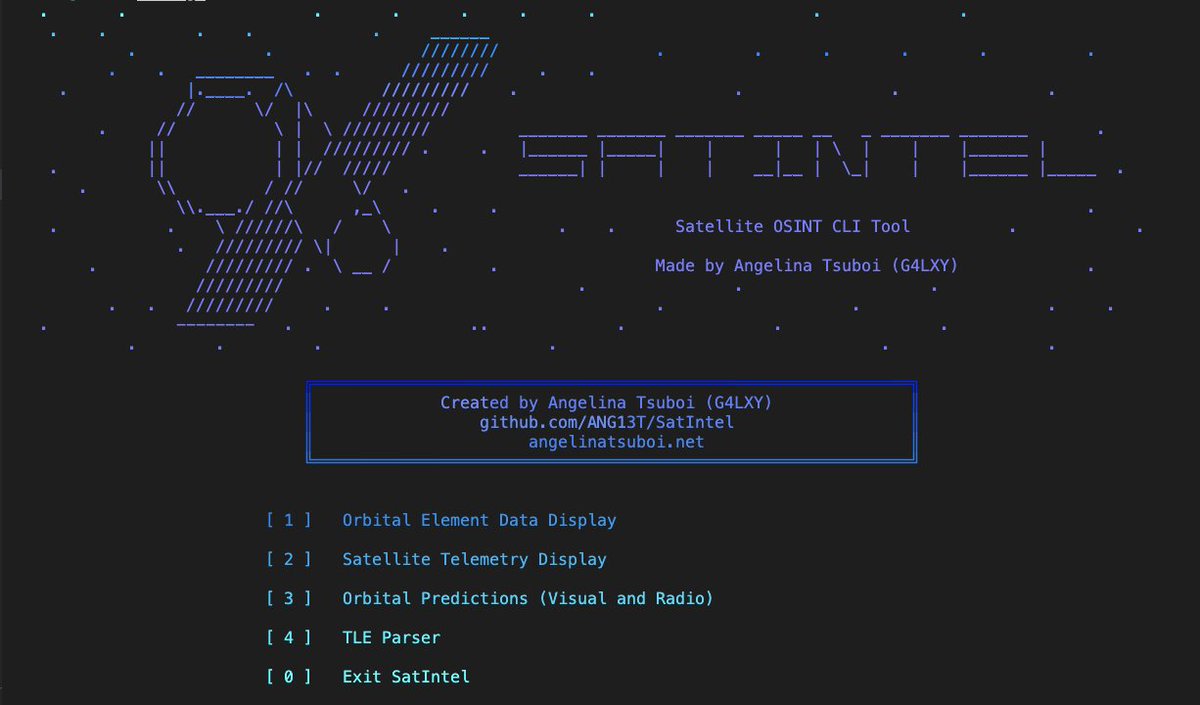
SatIntel: An OSINT tool for satellite reconnaissance made with Golang. The tool can extract satellite telemetry, receive orbital predictions, and parse TLEs. GitHub: github.com/ANG13T/SatIntel Features: • Satellite Catalog Retrieval from NORAD ID or Selection Menu • Display…
Sherlock: Hunt down social media accounts by username across social networks📝 🔗github.com/sherlock-proje…

Why I use Mosh over SSH when traveling 👇 SSH dies on flaky networks. Mosh doesn’t. You can switch networks, go offline briefly, and still maintain a live session. Built for travel, trusted by remote developers, and essential for all you digital nomads.
Llama.cpp exploitation (heap buffer overflow) retr0.blog/blog/llama-rpc… #cybersecurity #llama


dnstwist: A domain name permutation engine for detecting homograph phishing attacks, typo squatting, and brand impersonation GitHub: github.com/elceef/dnstwist

Email2Phonenumber: A OSINT tool to obtain a target's phone number just by having their email address GitHub: github.com/martinvigo/ema…


A recent #malware bypassed almost every public sandbox and antivirus, except Threat.Zone, and even evaded EDR/XDR in real-world incidents. Many banks, ISPs, and organizations were impacted. #ThreatIntelligence #onpatrol4malware malwation.com/blog/technical…
⚔️ ADVANCED CHAIN: Web Vuln ➝ RCE ➝ PrivEsc ➝ Root ➝ Persist ⸻ 🔍 STAGE 1 — Recon and Target Selection # Discover live hosts naabu -host scope.txt -p 80,443,8080,8000 | httpx -silent -title -tech -web-server -status-code -ports > alive.txt # Enumerate files/paths cat…

🛡️ cf-hero – Technical Overview cf-hero is an open-source CLI tool that reveals the real IP addresses of websites hidden behind Cloudflare’s reverse proxy protection. GITHUB Link 🔗 ⤵️⤵️

Linux kernel rootkits: beginners introduction inferi.club/post/the-art-o… #Linux #infosec

Trojanized KeePass Used to Deploy Cobalt Strike and Steal Credentials securityonline.info/trojanized-kee…
Cloud Privilege Escalation Awesome Script Suite github.com/carlospolop/Cl…
GhostStrike: The Undetectable Red Team Weapon meterpreter.org/ghoststrike-th…
meterpreter.org
GhostStrike: The Undetectable Red Team Weapon
GhostStrike is an advanced cybersecurity tool designed for Red Team operations, featuring sophisticated techniques to evade detection
𝗠𝗮𝗹𝘄𝗮𝗿𝗲 𝗗𝗲𝘃𝗲𝗹𝗼𝗽𝗺𝗲𝗻𝘁, 𝗔𝗻𝗮𝗹𝘆𝘀𝗶𝘀 𝗮𝗻𝗱 𝗗𝗙𝗜𝗥 𝗦𝗲𝗿𝗶𝗲𝘀 👾 🔗 Parte 1: - azr43lkn1ght.github.io/Malware%20Deve… 🔗 Parte 2: - azr43lkn1ght.github.io/Malware%20Deve… 🔗 Parte 3: - azr43lkn1ght.github.io/Malware%20Deve… 🔗 Parte 4: - azr43lkn1ght.github.io/Malware%20Deve… #maldev
(Old) List of Awesome Red Teaming Resources github.com/yeyintminthuht…
pwnat: Breakthrough NAT Traversal Without Port Forwarding meterpreter.org/pwnat-breakthr…
meterpreter.org
pwnat: Breakthrough NAT Traversal Without Port Forwarding
pwnat is a tool that allows any client behind a NAT to communicate with a server behind a separate NAT with no port forwarding
Fragtunnel: The Undetectable TCP Tunneling Tool for Bypassing Next Generation Firewalls meterpreter.org/fragtunnel-the…
meterpreter.org
Fragtunnel: The Undetectable TCP Tunneling Tool for Bypassing Next Generation Firewalls
Fragtunnel is a PoC TCP tunneling tool that exploits the design flaw that IDS/IPS engines and Next Generation Firewalls have
🚨Writing Exploits for IoT N-Days The amazing @_stigward has blessed our channel with another excellent video, this time exploiting a Zyxel NAS. 🥇Analyzing CVE-2023-35138 🥈Reversing the Firmware 🥉Developing the Exploit 👉youtube.com/watch?v=3Z7qXc…

United States Trends
- 1. Northern Lights 45.2K posts
- 2. #Aurora 9,531 posts
- 3. #DWTS 53.1K posts
- 4. Carmilla 2,085 posts
- 5. MIND-BLOWING 36.5K posts
- 6. #RHOSLC 7,187 posts
- 7. AI-driven Web3 N/A
- 8. H-1B 35.1K posts
- 9. Justin Edwards 2,471 posts
- 10. #GoAvsGo 1,566 posts
- 11. Sabonis 6,235 posts
- 12. #MakeOffer 9,226 posts
- 13. Louisville 18.1K posts
- 14. Creighton 2,323 posts
- 15. Eubanks N/A
- 16. Andy 60.2K posts
- 17. Gonzaga 3,004 posts
- 18. Cleto 2,581 posts
- 19. Zach Lavine 2,659 posts
- 20. H1-B 4,109 posts
Something went wrong.
Something went wrong.