nop
@thenopcode
professional binary breaker | Red Teamer @ MTD | BSODs are my daily routine
You might like
Around one month ago I started my OSED journey. If you want to get into binexp as well, feel free to check out my OSED GitHub repository containing lots of resources & practice binaries: github.com/nop-tech/OSED/
„Generative AI in the Crosshairs - Angriffe auf KI & LLMs“ - @thenopcode hat einen interessanten Talk im Rahmen der heutigen #AlmatoDevCon gehalten! 😎

Back to reality after another amazing edition of @offensive_con Thank you to everyone that made this conference and the parties as great as usual and see you again next time!

#SAFACon2025 is over. This edition was even more special than we could’ve imagined. Thank you all for coming, your wonderful energy and smiles are truly unforgettable. Already missing more time together 🤗 @SAFATeamGmbH



This concludes my first #0x41con and #SAFAcon Thank you very much @xerub & @justandrijana for those outstanding conferences and great talks! And also a big thank you to all the people who made the events so incredible 😄

/me sighs I said we were declining more giveaways, but I've made an exception and I've accepted 1 more. After this addition, NO MORE GIVEAWAYS will be accepted. Okay? New giveaway added to queue (this isn't the official giveaway yet, please don't spam the comment section) Our…
Releasing full 2+hr video of my browser exploitation workshop from VXCON 2024: youtube.com/live/b9OhamkAY… In which I show what goes inside the mind of a skilled hacker while exploiting a highly non-trivial vulnerability in v8, from zero to exploit concept. Especially this workflow…

youtube.com
YouTube
VXCON 2024 Workshop | Alisa Esage - Browser Exploitation Workshop
🚀 The Flare-On Challenge is officially wrapped up! This year, we had 5,324 participants, but only 275 made it to the finish line! Check out our blog post for the solutions, winner stats, and a shoutout to our challenge authors! bit.ly/4fvzfh8

Today I learned there's a Yahoo Finance article talking about me: finance.yahoo.com/news/guided-ha…
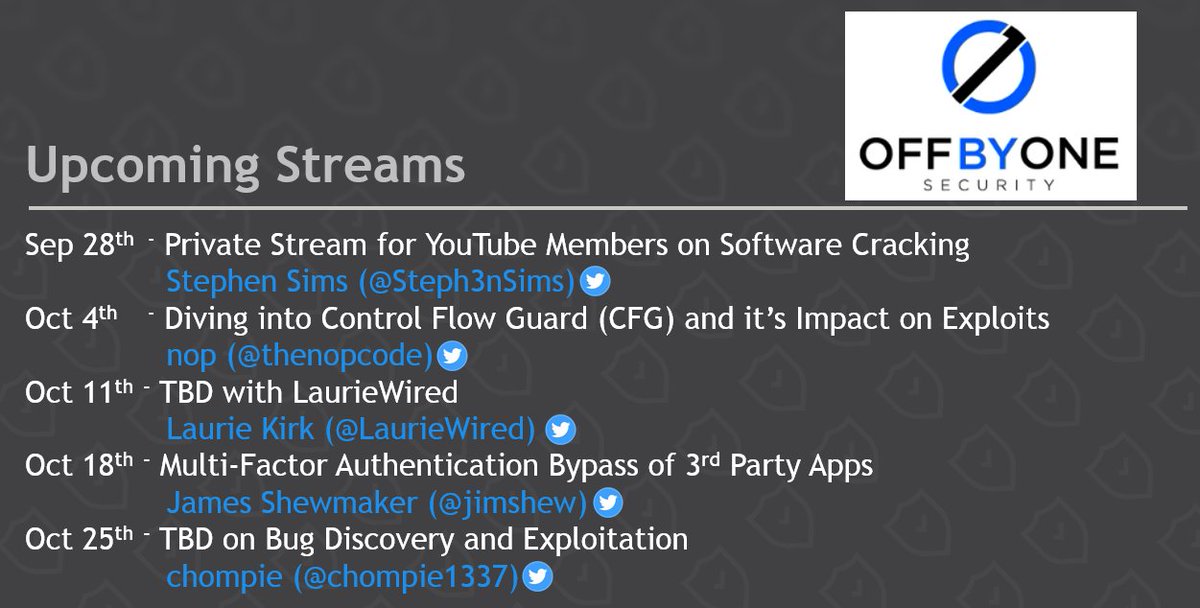
Join me and @Steph3nSims for the next Off By One Security stream!
Join me this Friday (4-Oct) at 11AM PT for the next Off By One Security stream with guest @thenopcode for a stream on the impact the Control Flow Guard (CFG) mitigation has on Windows Exploits! youtube.com/watch?v=A-vtsq… discord.gg/offbyonesecuri… @offby1security

Upcoming Off By One Security Streams! More details coming soon. Tomorrow, I'm doing a private stream for YouTube members on Software Cracking via Discord. @offby1security discord.gg/offbyonesecuri… youtube.com/@OffByOneSecur…
Created a blog post explaining physical memory primitives, how they can be exploited and how we can abuse the address translation mechanism to access any memory on a system as well as inject code into any process. 0dr3f.github.io/Demystifying_P…
0dr3f.github.io
Demystifying Physical Memory Primitive Exploitation on Windows
In this blog post, we dive in the world of physical memory primitives and how the right primitives can be abused to access process memory as well as inject code, all without opening handles.
#flareon11 game board is now open for early registration. Go claim your username. See you in two days! flare-on11.ctfd.io
#flareon11 is starting soon, get your tools ready! And by tools of course I mean get your own randomized FLARE bingo card webapp you can fill in as you go bashing your head against the wall solving all the challenges. 👉 washi.dev/bingo.html

United States Trends
- 1. Northern Lights 44.6K posts
- 2. #Aurora 9,361 posts
- 3. #DWTS 52.9K posts
- 4. #RHOSLC 7,116 posts
- 5. Carmilla 1,863 posts
- 6. AI-driven Web3 N/A
- 7. Sabonis 6,207 posts
- 8. H-1B 34.4K posts
- 9. Justin Edwards 2,448 posts
- 10. #GoAvsGo 1,563 posts
- 11. Gonzaga 2,966 posts
- 12. #MakeOffer 9,064 posts
- 13. Louisville 18K posts
- 14. Creighton 2,300 posts
- 15. Eubanks N/A
- 16. MIND-BLOWING 36.1K posts
- 17. Jamal Murray N/A
- 18. Andy 59.5K posts
- 19. Cleto 2,518 posts
- 20. Oweh 2,120 posts
You might like
-
 MalDev Academy
MalDev Academy
@MalDevAcademy -
 MDSec
MDSec
@MDSecLabs -
 Interrupt Labs
Interrupt Labs
@InterruptLabs -
 Ido Veltzman
Ido Veltzman
@Idov31 -
 Alexandre Borges
Alexandre Borges
@ale_sp_brazil -
 Reverse Engineering and More
Reverse Engineering and More
@re_and_more -
 seal
seal
@seal9055 -
 /r/netsec
/r/netsec
@_r_netsec -
 Stephen Sims
Stephen Sims
@Steph3nSims -
 NULL
NULL
@NUL0x4C -
 Connor McGarr
Connor McGarr
@33y0re -
 waldoirc
waldoirc
@waldoirc -
 d1rkmtr
d1rkmtr
@d1rkmtr -
 zhassulan zhussupov
zhassulan zhussupov
@cocomelonckz -
 Hex-Rays SA
Hex-Rays SA
@HexRaysSA
Something went wrong.
Something went wrong.