
x86byte
@x86byte
iOS & Windows Vulnerability Researcher & Exploit Developer — Reverse engineer, Obfuscation & De-Obfuscation Practitioner & Compilers Backend 👾🥤
LLMs still hallucinate, so the practical goal is to keep every answer tied to verifiable evidence. This survey maps the field and adds a clear taxonomy of metrics, a rollup of proven fixes, and guidance on retrieval‑augmented generation, called RAG, and domain tuning. It frames…

[Apple] Memory Integrity Enforcement: A complete vision for memory safety in Apple devices - Apple Security Research security.apple.com/blog/memory-in…
![secharvesterx's tweet image. [Apple] Memory Integrity Enforcement: A complete vision for memory safety in Apple devices - Apple Security Research
security.apple.com/blog/memory-in…](https://pbs.twimg.com/media/G0cX25iWIAAi9vI.jpg)
We’re excited to launch LLZK, an open-source intermediate representation (IR) for zero-knowledge circuits. Think LLVM, but for ZK. Built by @VeridiseInc and supported with a grant from the @ethereumfndn, LLZK is now live on GitHub. Thread 🧵 1/4
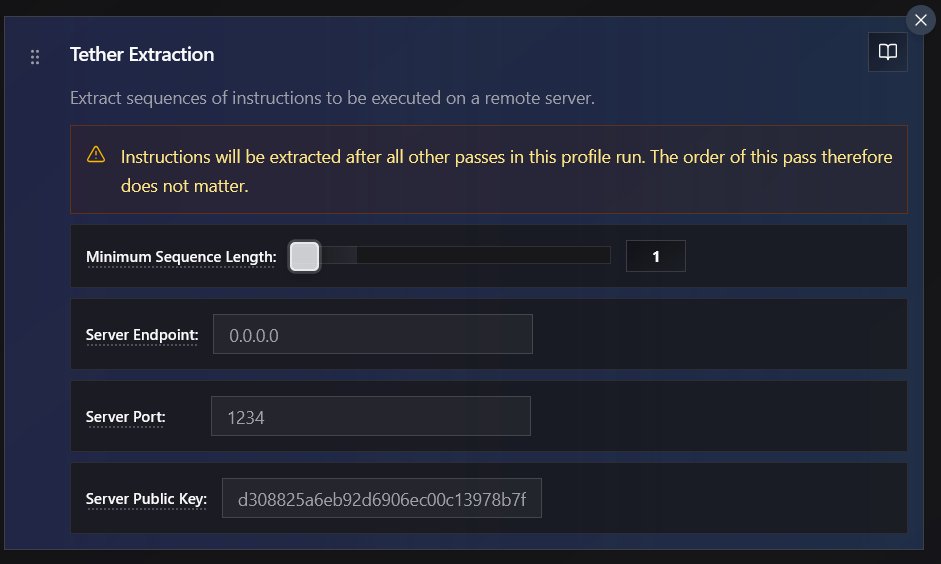
We have recently released a small side project called "Tether" which explores post-compilation extraction of instructions for exclusive server execution. github.com/codedefender-i…
yet another MBA paper: asmMBA: Robust Virtualization Obfuscation with Assembly-Based Mixed Boolean-Arithmetic (dl.acm.org/doi/pdf/10.114…) unfortuntely, neither the Loki-Blast nor the asmMBA code seems to be available
❗️ We discovered a bug in Microsoft's driver compliance checks which are used to determine if "Memory Integrity" can be enabled on a system. ❌The function "vsbapi!HvciIsDriverImage" is comparing an RVA against the raw file size. learn.microsoft.com/en-us/answers/…


🚀 CodeDefender SDK now supports source-level macros! Obfuscate functions in Rust/C/C++ by tagging them with your pre-defined obfuscation profile. 🦀 #[codedefender("Profile1")] 💻 CODEDEFENDER("Profile1", ...) Docs + examples 👉 github.com/codedefender-i… #infosec #rustlang…
![BackEngineerLab's tweet image. 🚀 CodeDefender SDK now supports source-level macros!
Obfuscate functions in Rust/C/C++ by tagging them with your pre-defined obfuscation profile.
🦀 #[codedefender("Profile1")]
💻 CODEDEFENDER("Profile1", ...)
Docs + examples 👉 github.com/codedefender-i…
#infosec #rustlang…](https://pbs.twimg.com/media/GviPpReakAYoNKy.png)
🧰 CodeDefender API and CLI are live Protect binaries from the terminal or Rust SDK Upload → Analyze → Obfuscate → Download YAML configs give full control over passes, symbols, and transform logic 🔗 github.com/codedefender-i… 📔 docs.codedefender.io/features/api

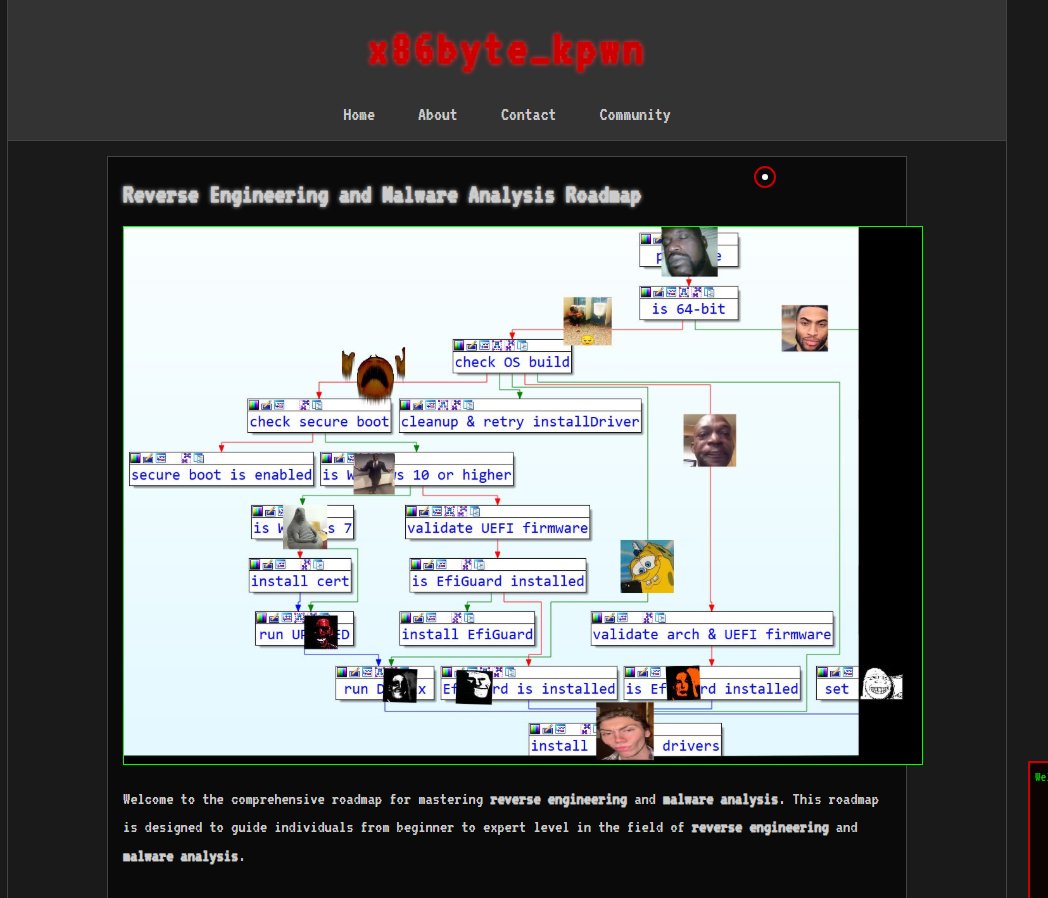
RE-MA Roadmap Repository Update The RE-MA Roadmap (github.com/x86byte/RE-MA-…) has been updated with new resources. Check it out to explore more materials for mastering reverse engineering and malware analysis! links : - - x86byte.github.io/x86byte_kpwn/a…
- #VMProtect 2 - Detailed Analysis of the Virtual Machine Architecture (blog.back.engineering/17/05/2021/) - #VMProtect 2 - Part Two, Complete Static Analysis (blog.back.engineering/21/06/2021/) #reverseengineering #virtualisation #Obfuscation

occasionally I'd get people asking me "how'd you know what this function is/does by just glancing at it?" it's just years of looking at the same thing over and over again

John Carmack Then: Doom programmer Now: Doomslayer


What has BELabs been up to ⁉️ Check out these new SSE based obfuscations. 🫣 We have completely rewritten our compiler from the ground up to pave the way for ARM support. ✅ This has allowed us to make the world's strongest bin2bin obfuscation framework even stronger.💪 The…

Stealth syscalls (@darkrelaylabs), VM introspection (@memn0ps), Marebackup LPE (@itm4n), Azure Arc C2 (@ZephrFish), and more! blog.badsectorlabs.com/last-week-in-s…
United States Trends
- 1. Good Wednesday 25.4K posts
- 2. #wednesdaymotivation 3,696 posts
- 3. Hump Day 11K posts
- 4. #hazbinhotelseason2 41.5K posts
- 5. PancakeSwap BNB Chain 2,273 posts
- 6. Jameis 1,679 posts
- 7. #Wednesdayvibe 1,937 posts
- 8. ADOR 62K posts
- 9. Happy Hump 6,855 posts
- 10. #ENGLOTxHOWEAWARDS25 615K posts
- 11. Northern Lights 52.5K posts
- 12. USDT 109K posts
- 13. #HazbinHotelSpoilers 4,914 posts
- 14. Hanni 17.7K posts
- 15. StandX 2,568 posts
- 16. Jack Schlossberg 2,538 posts
- 17. Antarctica 8,287 posts
- 18. MIND-BLOWING 32.7K posts
- 19. Wike 259K posts
- 20. H-1B 47.1K posts
Something went wrong.
Something went wrong.
































































































