#cryptographicalgorithms zoekresultaten
Are you ready to challenge your skills and become a crypto pro? Dive into the secrets behind the codes that keep the digital world safe. From cracking ciphers to mastering quantum-resistant algorithms. hackersarise.thinkific.com/courses/interm… @three_cube @_aircorridor

Hihi my face when I realized I need to understand a billion cryptographic algorithms to fully understand public and private keys. RIPEMD who? SHA256 what? Elliptic curve you say?

■CertiK Quiz Answers Threshold Cryptography IV: Multiplicative-to-Additive (MtA) Protocol and Paillier Encryption Scheme skynet.certik.com/quest/threshol…




Hi Frens 🫶 Check This @cysic_xyz Alpha's 👇 Bundle multiple micro-proofs via aggregation/recursion to reduce gas and on-chain clutter. Playbook: batch for small, recursion for big.

The global #bitcoin network calculates ~430,000,000,000,000,000,000 algorithms every second protecting the blockchain.
Longer thread on how Cipher Protocol will protect you ⬇️ Recent campaigns use[d] malicious SVGs as the first step in an elaborate, multi-stage infection chain. SVGs act as HTML carriers to push victims into downloading a passworded ZIP that contains CHM/HTA/EXE payloads. The…
![orithellama's tweet image. Longer thread on how Cipher Protocol will protect you ⬇️
Recent campaigns use[d] malicious SVGs as the first step in an elaborate, multi-stage infection chain. SVGs act as HTML carriers to push victims into downloading a passworded ZIP that contains CHM/HTA/EXE payloads.
The…](https://pbs.twimg.com/media/G4ldzI1XEAA6I0l.jpg)
![orithellama's tweet image. Longer thread on how Cipher Protocol will protect you ⬇️
Recent campaigns use[d] malicious SVGs as the first step in an elaborate, multi-stage infection chain. SVGs act as HTML carriers to push victims into downloading a passworded ZIP that contains CHM/HTA/EXE payloads.
The…](https://pbs.twimg.com/media/G4leLEsXwAAqQ-2.jpg)
Day 55 of #100DaysOfCode (#Web3) - travelling, somehow found few hours to study - Explored asymmetric encryption in depth - Studied common algorithms: RSA, ECC, and EdDSA - Learned how elliptic curves work and why they’re used in cryptography #Web3 #Blockchain #Crypto…
What makes Cysic special is its ability to turn complex cryptography into something easy to use. Developers do not need to understand the heavy math or manage large servers to generate proofs. They can connect to the @cysic_xyz network and request the computation they need,…

Crypto Basics! | Layer 1 101s Time for another Crypto Basics! This time its all about Layer 1’s, the backbone of the Crypto Market. What do you want to learn about next in the Crypto world?

Excellent introduction to cryptography concepts for beginners (credits @sergioprado) Part 1: sergioprado.blog/introduction-t… Part 2: sergioprado.blog/a-hands-on-app… Part 3: sergioprado.blog/asymmetric-key… #cryptography #infosec #cybersecurity



" The most appropriate and secure cryptographic methods for the Post-#Quantum #Cryptography (#PQC) era center on the new quantum-resistant algorithms that have been standardized by National Institute of Standards and Technology (NIST), while still leveraging established symmetric…

Nice series introducing cryptography concepts for beginners (credits @sergioprado) Part 1: sergioprado.blog/introduction-t… Part 2: sergioprado.blog/a-hands-on-app… Part 3: sergioprado.blog/asymmetric-key… #cryptography
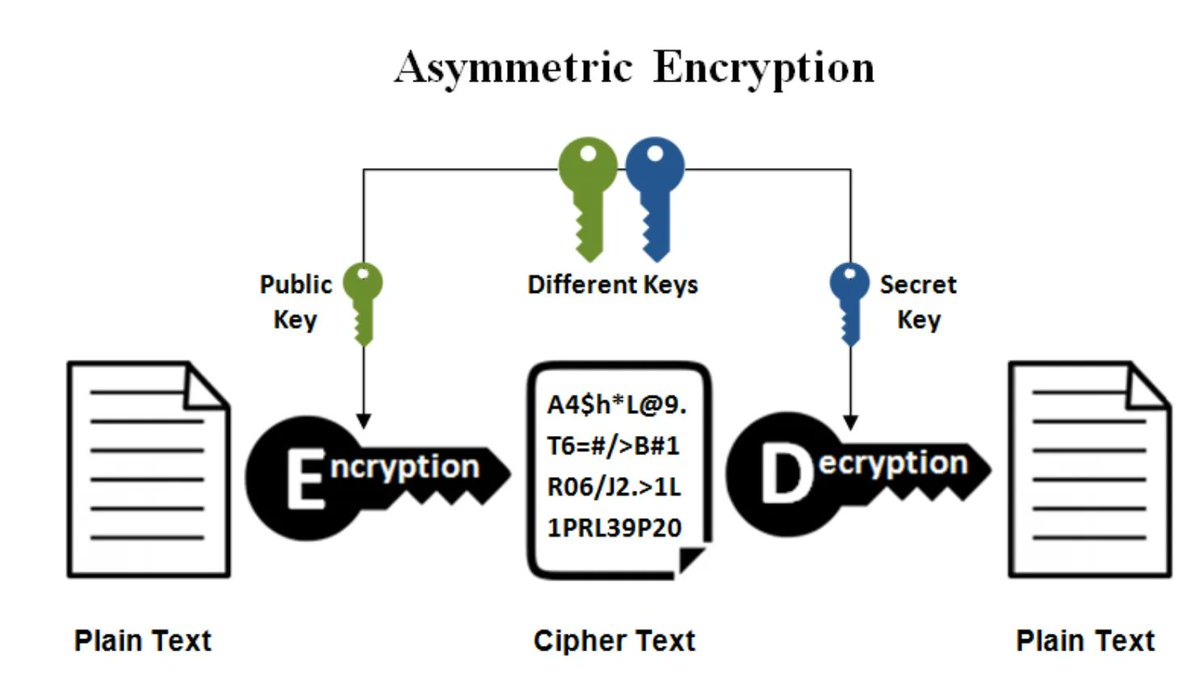
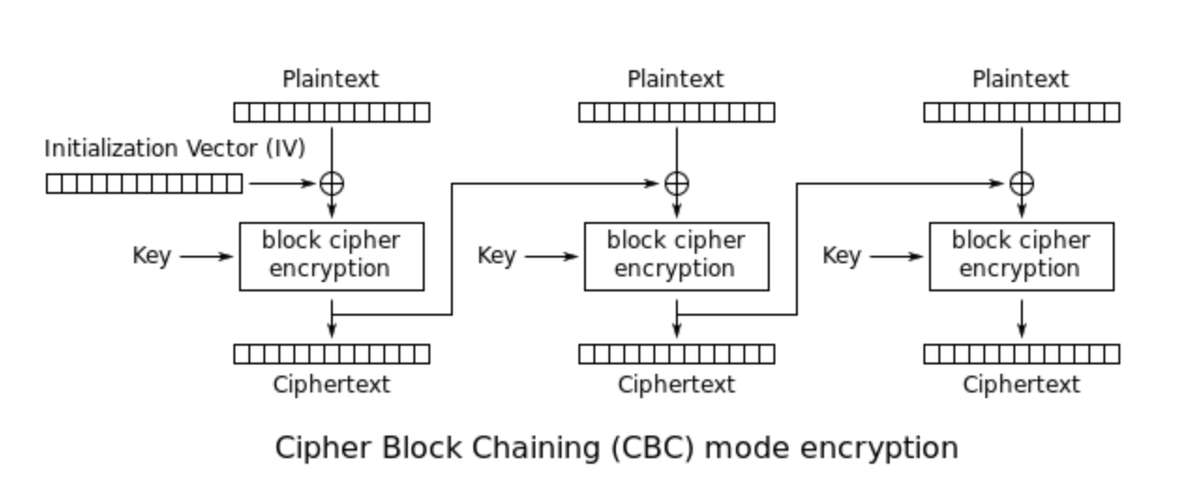
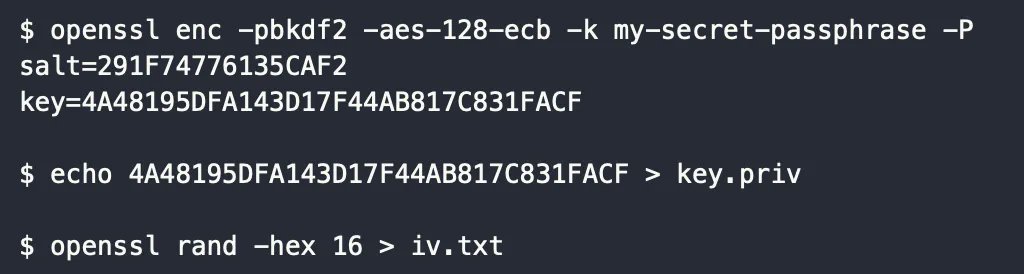
Claude Code Can Debug Low Level Cryptography words.filippo.io/claude-debuggi…
So let's discuss SSL encryption algorithms for the moment. If you are using Chrome, you've got a choice between AES, Triple-DES, and ChaCha20. This pic shows the list that Chrome sends to web servers saying which algorithms it'll support.

(1/18) Cryptography Basics: Polynomial Encoding Humans think in words and ideas, machines think in numbers and math; the translation of words into numbers is core to basic computing. Want to learn about the powers we have in this process? Let's start with Lagrange Polynomials.

Check out the new algo website and test the algo out yourself! This is passive and trades for you automatically… Check out the new website and try it out here: tradegy.net/algo

This article will provide a detailed guide to RFID cryptographic algorithms to help you understand the security challenges in RFID technology and how to improve data security. rfidlabel.com/rfid-cryptogra… #rfid #cryptographicalgorithms
Cybersecurity is incomplete without #CryptographicAlgorithms to sustain and amplify cyber resilience. This read focuses on the strategic role of Cryptography in leveraging robust security for your organization. Explore the read here: shorturl.at/iZ3TS #Cryptography

🔥 Read our Paper 📚 Analysis of Cryptographic Algorithms to Improve Cybersecurity in the Industrial Electrical Sector 🔗 mdpi.com/2076-3417/14/7… 👨🔬 by Francisco Alonso et al. #cybersecurity #cryptographicalgorithms
Can Google's Willow Quantum Chip Compromise Bitcoin Security and Cryptocurrency's Future? market-news24.com/crypto/can-goo… #Bitcoinsecurity #cryptocurrencyrisks #cryptographicalgorithms #GoogleWillowchip #quantumcomputing #quantumresistantsolutions #SundarPichai

Microchip Technology introduced the PIC64HX microprocessor family, specifically designed to meet the needs of intelligent edge applications. #cryptographicalgorithms #IntelligentEdgeDesigns #MicrochipTechnology

STMicroelectronics' FIPS 140-3 certified STSAFE-TPM modules provide cryptographic protection for PCs, servers, IoT, and automotive systems. #Automotive #cryptographicalgorithms #FIPS1403

Bitcoin to Stablecoins: An Overview of Cryptocurrency Categories tinyurl.com/ym6u6h3y #Bitcoin #Stablecoins #CryptographicAlgorithms #Ethereum #Litecoin #AI #AINews #AnalyticsInsight #AnalyticsInsightMagazine

Quantum Computing and Its Implications for Cybersecurity tinyurl.com/rfmur64f #Quantumcomputing #CryptographicAlgorithms #QuantumAttacks #Postquantumcryptography #Cybersecurity #AINews #AnalyticsInsight #AnalyticsInsightMagazine

A massive advantage of Bitcoin is its #security - Unlike traditional currencies, Bitcoin transactions are secured using #CryptographicAlgorithms that make it virtually impossible to counterfeit. This makes Bitcoin a more secure form of money, less susceptible to fraud and theft.

Quote of the Day zcu.io/Xi4x #CryptographicAlgorithms #Cryptographic #QuantumComputing #Crypto #DataEncryption #AI #AINews #AnalyticsInsight #AnalyticsInsightMagazine
Quantum Computing and Its Implications for Cybersecurity tinyurl.com/rfmur64f #Quantumcomputing #CryptographicAlgorithms #QuantumAttacks #Postquantumcryptography #Cybersecurity #AINews #AnalyticsInsight #AnalyticsInsightMagazine

Bitcoin to Stablecoins: An Overview of Cryptocurrency Categories tinyurl.com/ym6u6h3y #Bitcoin #Stablecoins #CryptographicAlgorithms #Ethereum #Litecoin #AI #AINews #AnalyticsInsight #AnalyticsInsightMagazine

STMicroelectronics' FIPS 140-3 certified STSAFE-TPM modules provide cryptographic protection for PCs, servers, IoT, and automotive systems. #Automotive #cryptographicalgorithms #FIPS1403

Microchip Technology introduced the PIC64HX microprocessor family, specifically designed to meet the needs of intelligent edge applications. #cryptographicalgorithms #IntelligentEdgeDesigns #MicrochipTechnology

A massive advantage of Bitcoin is its #security - Unlike traditional currencies, Bitcoin transactions are secured using #CryptographicAlgorithms that make it virtually impossible to counterfeit. This makes Bitcoin a more secure form of money, less susceptible to fraud and theft.

Only Cryptographic Algorithms Can Stop Quantum Computers from Data Stealing bit.ly/3wy6onk #CryptographicAlgorithms #QuantumComputers #DataStealing #DataProtection #QuantumComputing #Cryptyographic #Cybercriminals #AI #AINews #AnalyticsInsight #AnalyticsInsightMagazine

Can Google's Willow Quantum Chip Compromise Bitcoin Security and Cryptocurrency's Future? market-news24.com/crypto/can-goo… #Bitcoinsecurity #cryptocurrencyrisks #cryptographicalgorithms #GoogleWillowchip #quantumcomputing #quantumresistantsolutions #SundarPichai

🔥 Read our Paper 📚 Analysis of Cryptographic Algorithms to Improve Cybersecurity in the Industrial Electrical Sector 🔗 mdpi.com/2076-3417/14/7… 👨🔬 by Francisco Alonso et al. #cybersecurity #cryptographicalgorithms

What Is Cryptography? Cryptography allows digitals assets to be transacted and verified without the need for a trusted third party. news.bitchain.link/2021/08/what-i… #Cryptography #Crypto #CryptographicAlgorithms #Encryption #Blockchain #cryptocurrencies #BitchainBIC #BitchainCrypto

Cybersecurity is incomplete without #CryptographicAlgorithms to sustain and amplify cyber resilience. This read focuses on the strategic role of Cryptography in leveraging robust security for your organization. Explore the read here: shorturl.at/iZ3TS #Cryptography

Abu Dhabi's Cryptography Research Centre has built the UAE's first national and sovereign #CryptoLibrary. In our Sept/Oct issue we find out about the work they're doing: ow.ly/2Oy350GrT6M @TIIuae #CryptographicAlgorithms #CyberSecurity

Only Cryptographic Algorithms Can Stop Quantum Computers from Data Stealing bit.ly/38wkvBK #CryptographicAlgorithms #QuantumComputers #DataStealing #DataProtection #QuantumComputing #Cryptographic #Data #Crypto #Cybercriminals #GlobalTechMarket #WDC #WorldDataCongress
Something went wrong.
Something went wrong.
United States Trends
- 1. #SNME 58.9K posts
- 2. Ohtani 53.1K posts
- 3. Bo Bichette 13.8K posts
- 4. Shohei 38.9K posts
- 5. #UFCVegas110 12.3K posts
- 6. Blue Jays 68.6K posts
- 7. Dave Roberts 5,263 posts
- 8. Georgia 49.3K posts
- 9. CM Punk 14.7K posts
- 10. Scherzer 12.2K posts
- 11. Game 7 3,819 posts
- 12. Mason Thomas N/A
- 13. #AEWCollision 5,789 posts
- 14. Drew 121K posts
- 15. Underwood 3,139 posts
- 16. Jey Uso 7,796 posts
- 17. Lagway 4,112 posts
- 18. Jade Cargill 18.8K posts
- 19. Springer 11.4K posts
- 20. Max Gilbert N/A