#exploitdev результаты поиска
This should be the final set of labs published publicly. That's all folks for now... #RE #Offsec #ExploitDev #SoftwareExploitation exploitation.ashemery.com



I’m happy to announce that I passed OSED from @offsectraining 😍😍 I just got the email and man IT FELT SO GOOD #CyberSecurity #exploitdev

Hand-crafted ROP chain 🛠️! Had limited gadgets, so I used an IAT entry for HeapAlloc and calculated the VirtualAllocStub RVA offset. Got creative without ASLR and possibly should've used a read primitive. Details in the gist! #ROP #ExploitDev #osed gist.githubusercontent.com/snowcra5h/a7c1…

Bypassing PIE with partial overwrite? 🔥 Instead of guessing full addresses, just overwrite specific bytes to align with predictable offsets. Precision > brute force. A reminder that security evolves, and so must we. 🛡️ #CyberSecurity #ExploitDev #ReverseEngineering


New article alert : ek0msUSB medium.com/@ekoms1/ek0msu… #hacker #greyhat #exploitdev #commandandcontrol #payloads




Pwning LLaMA.cpp RPC Server #LLAMACpp #RPCServer #ExploitDev #CTF pwner.gg/2024/10/03/lla…
🚨 Released a full SEH exploit chain for DeepFreeze 8! With custom shellcode and ROP chain. Software was fully reversed, and an SEH vuln discovered studying for the #OSED 💪Blog write-up coming soon.🔍github.com/snowcra5h/Faro… #CyberSecurity #ExploitDev
If you're exploiting a driver offering R/W access to physical memory on Win11 24H2, you can leverage this simple trick to circumvent kernel address leak restrictions and retrieve the kernel base address :p xacone.github.io/kaslr_leak_24h… #exploitdev #driverexploitation
Happy New Year 2025! #infosec #CyberSec #ExploitDev #Hacker #Bug #bugbountyhunter #vulnerabilityResearcher #ReverseEngineering #Binex

Important note to those new to this account. The course below is completely FREE. I know someone (maybe more) has ripped the videos & probably now the labs & is selling them on @udemy. Please do not pay for this course, it is FREE! #ExploitDev #Offsec exploitation.ashemery.com
موضوع برنامه ی Off By One Security این هفته "A Practical Look at Windows Kernel Mode Shadow Stacks and the Secure Kernel!" هستش. این برنامه ساعت 23 به وقت ایران پخش میشه. اگه فرصت نکردید، برنامه ضبط میشه و بعدا هم از همون لینکها قابل دسترسه. #اکسپلویت #ExploitDev #windows
Join me on Friday, February 14th on the @offby1security stream with the amazing @33y0re (Connor McGarr) for a look at Windows Kernel Mode Shadow Stacks and the Secure Kernel! youtube.com/watch?v=T7qxs-…

ویدیوهای کنفرانس DistrictCon 2025 در #یوتیوب منتشر شد. کنفرانس @DistrictCon یک کنفرانس #امنیت_سایبری جامعه محور هستش که تمرکز اصلیش از #ExploitDev و #REV گرفته تا سیاست امنیت اطلاعات و ژئوپلیتیک هستش. فضاش یکمی دارکه ! youtube.com/@districtcon #کنفرانس #DistrictCon
Ma solution pour les exercices heap du #CTF Protostar github.com/devl00p/blog/b… #exploitdev #reverseengineering #vulndev
𝑪𝒊𝒂𝒐 𝑰𝒕𝒂𝒍𝒚, 𝑪𝒊𝒂𝒐 𝑹𝒐𝒎𝒂! 𝑹𝒆𝒂𝒅𝒚 𝒇𝒐𝒓 𝑪𝒐𝒓𝒆𝒍𝒂𝒏? Sign up for our Expert-level stack class: bit.ly/corelan-traini… #corelan #stack #exploitdev #windows11
💻 Go-exploit A Go-based exploit framework for creating compact, portable, and uniform exploits, with minimal dependencies and cross-compilation capabilities By VulnCheck's @Junior_Baines et al #infosec #exploitdev github.com/vulncheck-oss/…
Interested in Software Exploitation? This course is for you and will take you from knowing nothing, to understanding how exploits work and how to write them... I hope it will be useful to someone out there! #Offsec #Cybersecurity #ExploitDev #Debugging youtube.com/watch?v=5GGyFb…

Moving from Slack to Discord. You're welcome to join, hang out, contribute to the community. Be nice. discord.gg/DjfR5ntXrb #corelancommunity #corelantraining #exploitdev #safeplace
discord.com
Join the Corelan Discord Server!
Check out the Corelan community on Discord - hang out with 301 other members and enjoy free voice and text chat.
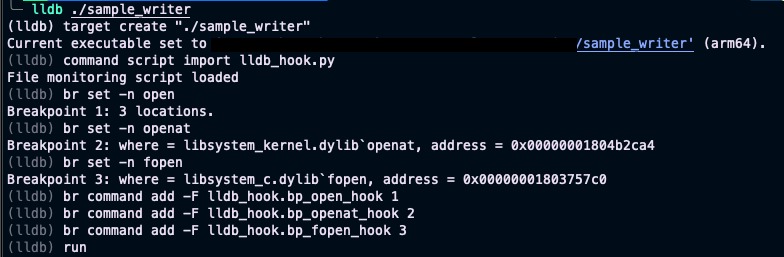
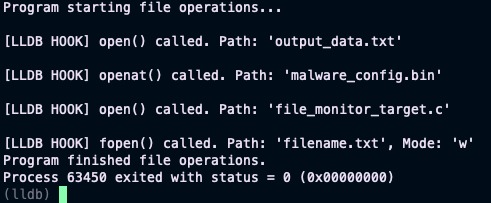
Tip #2: Level up your security analysis! 🚀 Use #lldb & Python 🐍 to dynamically monitor every file a program opens (open/openat/fopen). Crucial for #MalwareAnalysis & #ExploitDev to uncover file system interactions. See what that binary really touches! 💻📂 #CyberSecurity

⚠️ Afraid of public classes? 🔒 Corelan Academy = private, intense, small-group exploit dev training 2–8 ppl • one-on-one access • flexible timing • competitive pricing • Stack & Heap DM or reply interested #corelan #exploitdev #training #heap #stack #corelanacademy
⚠️ Afraid of public classes? 🔒 Corelan Academy = private, intense, small-group exploit dev training 2–8 ppl • one-on-one access • flexible timing • competitive pricing • Stack & Heap DM or reply interested #corelan #exploitdev #training #heap #stack #corelanacademy
New article alert : ek0msUSB medium.com/@ekoms1/ek0msu… #hacker #greyhat #exploitdev #commandandcontrol #payloads




New whitepaper: Polymorphic shellcode bypasses on modern architectures—evasion techniques, detection gaps, and practical defenses. Read: github.com/MottaSec/White… #SecurityResearch #ExploitDev #BlueTeam
CVE-2025-52915 assigned - my first vulnerability!🥳 A classic BYOVD case: kernel driver with unrestricted process termination. Vendor coordination turned out more challenging than the exploit itself. Technical write-up: blacksnufkin.github.io/posts/BYOVD-CV… #ExploitDev #CVE #BYOVD #RedTeam
Privilege escalation isn't always about the shell. Kernel memory leaks can offer direct paths to root access. Details: versprite.com/blog/the-shell… #PrivilegeEscalation #LinuxSecurity #ExploitDev
NEW: Digital Demonology Grimoire - A dark exploration into buffer overflow exploitation & shellcode analysis Perfect reading for👹 github.com/h3xorc1sm/digi… #DEFCON #ExploitDev #Shellcode #BufferOverflow #InfoSec #HackTheGibson
"Those who gaze into the assembler, take care that the assembler does not gaze also into them." The silicon souls whisper their secrets... github.com/h3xorc1sm/digi… #DEFCON #ExploitDev #DigitalDemonology
We dissect a DFG compiler bug we discovered in Safari/WebKit. This post covers root cause, impact, and technical analysis: blog.exodusintel.com/2025/08/04/oop… #WebKit #VulnerabilityResearch #ExploitDev #Safari #CyberSecurity #ExodusIntel
🔔 Reminder: Zürich, Corelan Stack is coming Oct 7–10, 2025 ✅ No nonsense, No BS ✅ Just real-world exploit dev skills 🎟️ eventcreate.com/e/sigs-corelan… 💛 RT appreciated! #corelan #win11 #exploitdev
Something went wrong.
Something went wrong.
United States Trends
- 1. #UFC323 118K posts
- 2. Indiana 103K posts
- 3. Merab 40.8K posts
- 4. Mendoza 40.1K posts
- 5. Roach 29.7K posts
- 6. Ohio State 62.3K posts
- 7. Petr Yan 23.1K posts
- 8. Pantoja 33.7K posts
- 9. Bama 85.4K posts
- 10. Joshua Van 9,753 posts
- 11. Heisman 18.8K posts
- 12. Curt Cignetti 10.5K posts
- 13. Manny Diaz 2,814 posts
- 14. Miami 307K posts
- 15. #iufb 8,426 posts
- 16. The ACC 36.7K posts
- 17. Tulane 18.1K posts
- 18. Virginia 46.2K posts
- 19. Sayin 87.3K posts
- 20. Fielding 8,644 posts