#firmwareprotection ผลการค้นหา
You’ve made it to the final level. Keeping your software and apps updated is one of the easiest ways to protect yourself online. Updates don’t just bring new features, they also patch vulnerabilities that attackers are eager to exploit. #KeeperSecurity…
Stay Safe Online Keeping your software up to date is one of the steps you can take to enhance your online safety.Regular updates fix security vulnerabilities that hackers could exploit. Protect your devices and privacy with reliable antivirus software. #CyberSecurity


Protecting systems isn’t about ticking boxes, it’s a mindset. The real firewall is vigilance. 💻🔐

Infineon’s PSOC Control C3 microcontrollers offer advanced Post-Quantum Cryptography for secure industrial embedded applications. #CNSA2.0 #embeddedsecurity #FirmwareProtection

Defend Against Ransomware 🛡️ Backup critical files regularly 🛡️ Use endpoint protection tools 🛡️ Block unauthorized apps 🛡️ Monitor for unusual file activity 🛡️ Educate teams on phishing threats #cybersecurity 

Essential Firmware Protection: Tactics to Secure Your Devices #FirmwareProtection #DeviceSecurity #SecureBoot #CyberSecurity #BootKitty #FirmwareUpdates #AccessControl #TechSafety #VulnerabilityManagement #ITSecurity
🛠 Take action to protect your critical systems before they’re corrupted! Dive into our infographic for actionable steps against malware threats. #infosec #securitytips



Bitdefender GravityZone PHASR prevents attackers from weaponizing trusted tools. And here’s why it's so crucial: When the overwhelming majority of serious cyberattacks use your own tools against you, detection isn’t enough. Learn more: 🔗 bitdefend.me/4kwceNF #Bitdefender…
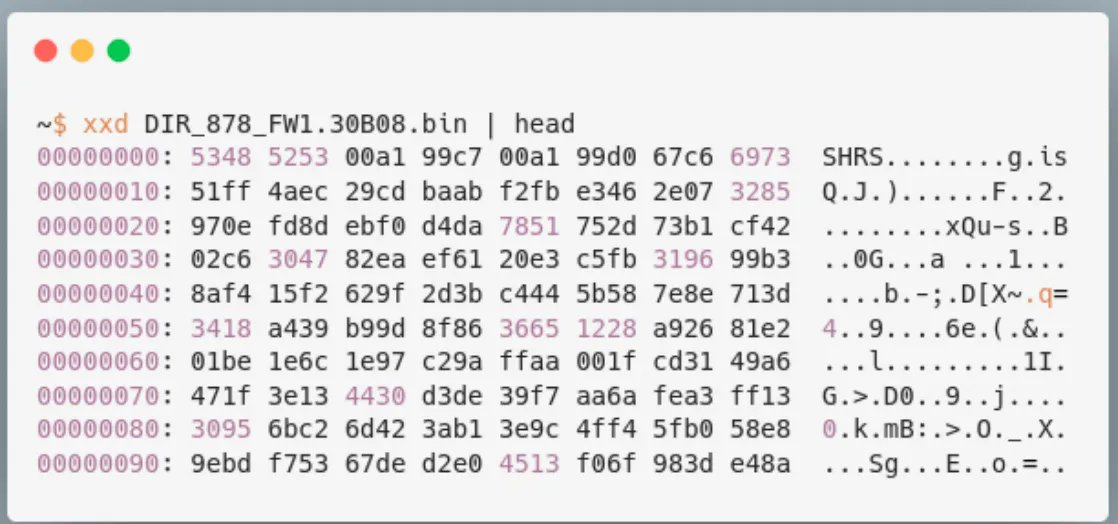
(1/2) A list of a few tools that can be useful for firmware unpacking, repacking and analysis binwalk: github.com/ReFirmLabs/bin… EMBA: github.com/e-m-b-a/emba unblob: github.com/onekey-sec/unb… #firmware



Any device that connects to the internet is vulnerable to risks. The best defense is to keep device security software, web browser and operating systems up to date. #SecureOurWorld by turning on auto-updates. #CybersecurityAwarenessMonth

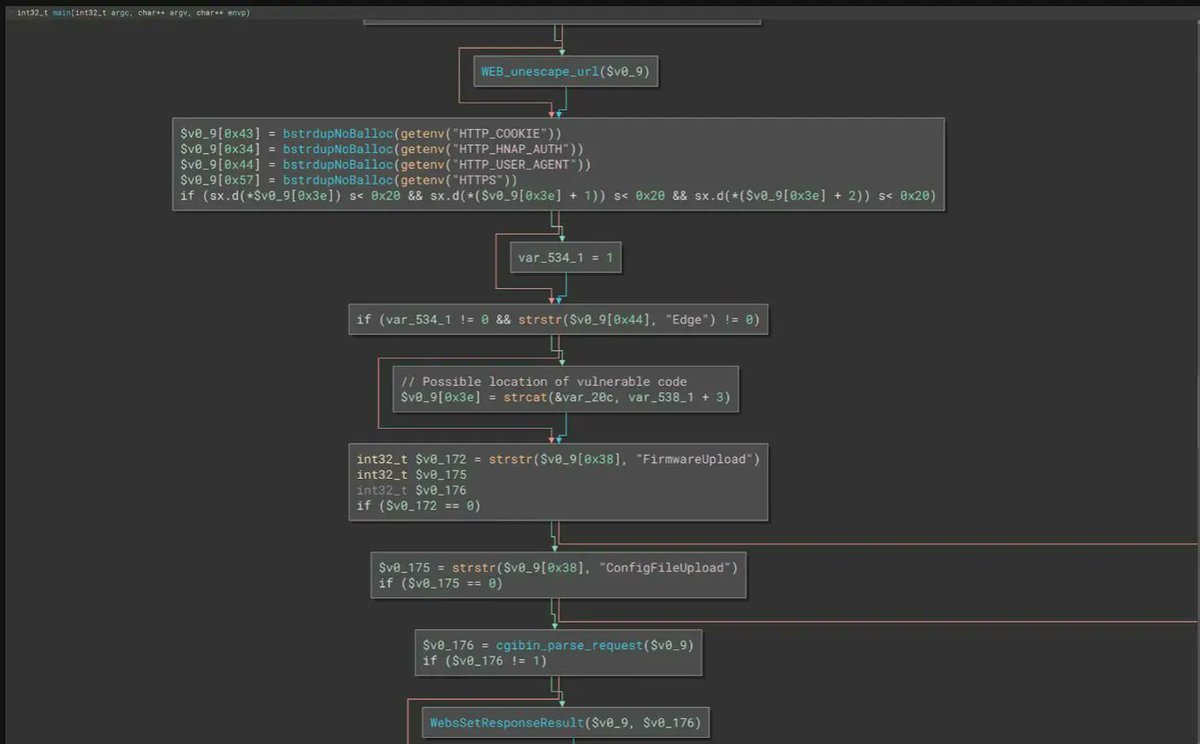
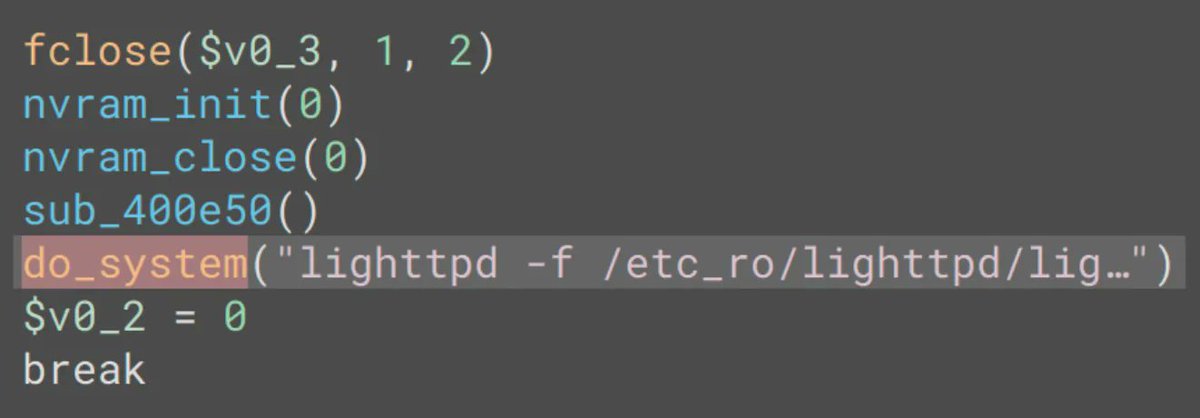
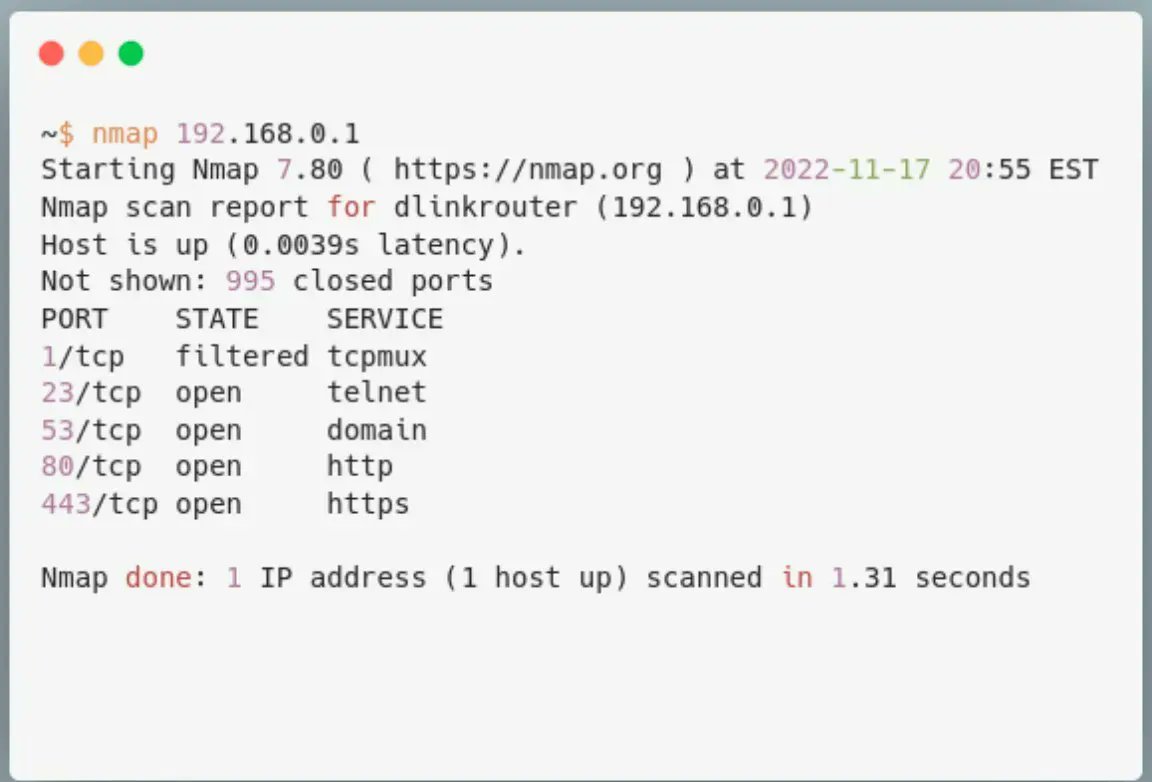
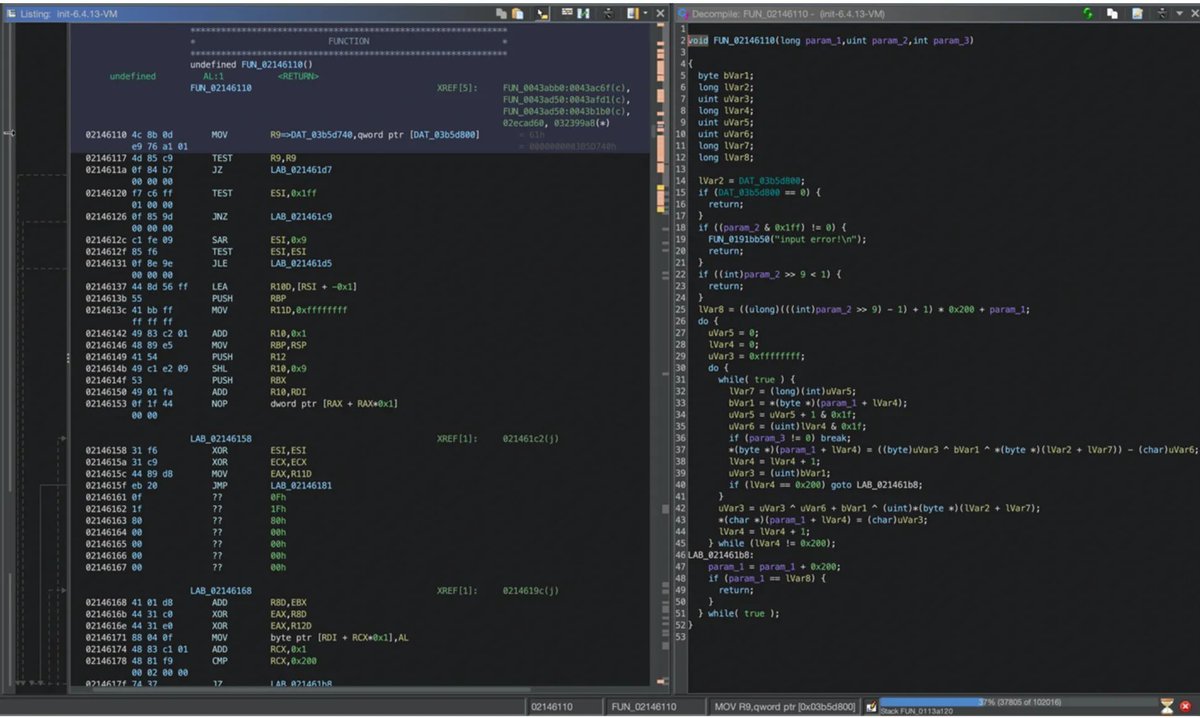
How to start with security analysis of embedded device firmwares (debugging and emulation) (With examples using D-Link routers and CVE-2022-1262) Excellent blog post by @GreyNoiseIO greynoise.io/blog/debugging… #cybersecurity #embedded
🛡 Keep your software ecosystem healthy. Update operating systems, apps, and firmware promptly — and remove what you no longer use. Old, unpatched software is a favourite entry point for attackers. #CyberSecurity #InfoSec
Great blog post by @GreyNoiseIO on how to start with security analysis of embedded device firmwares (debugging and emulation) With examples using D-Link routers and CVE-2022-1262 greynoise.io/blog/debugging… #cybersecurity
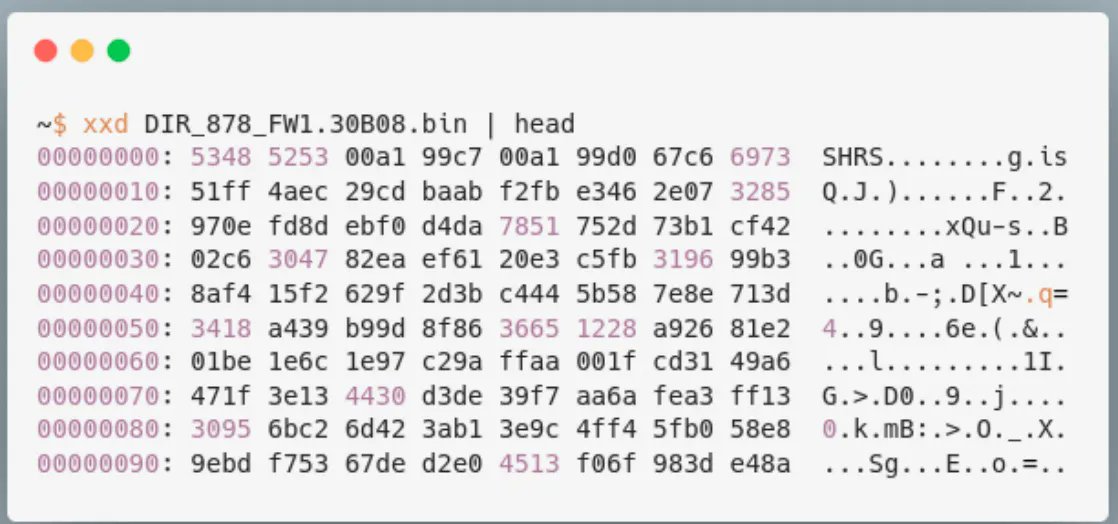
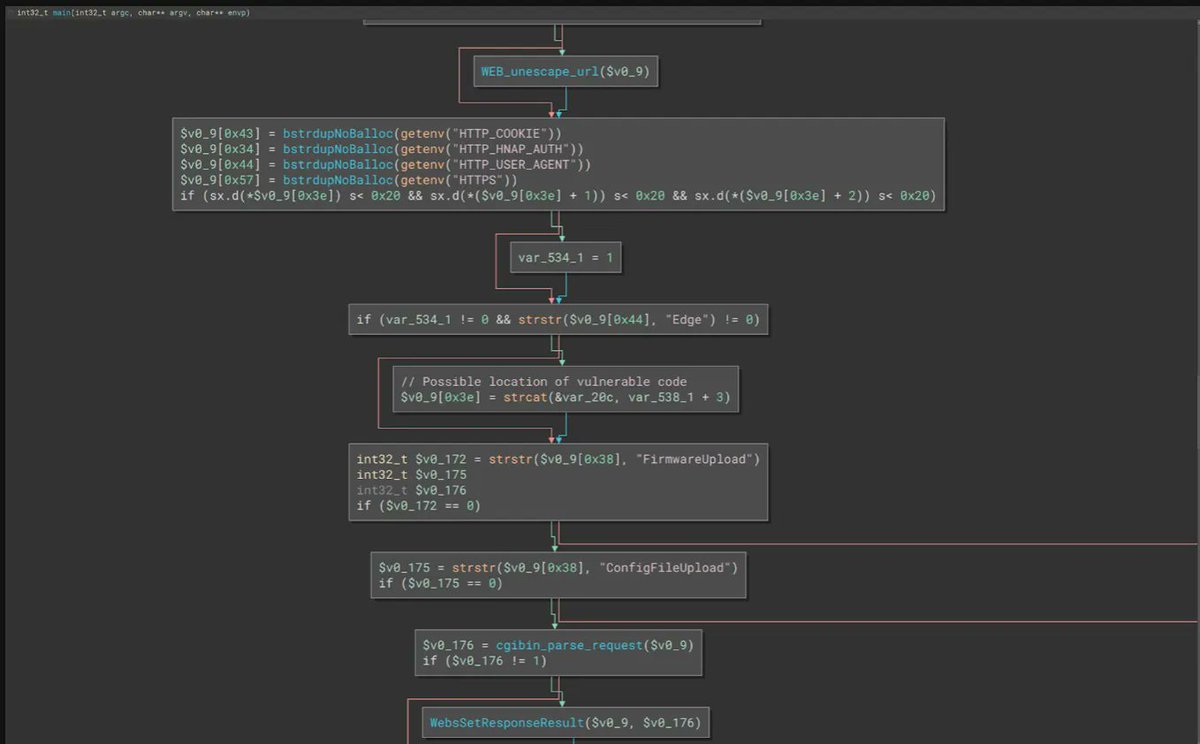
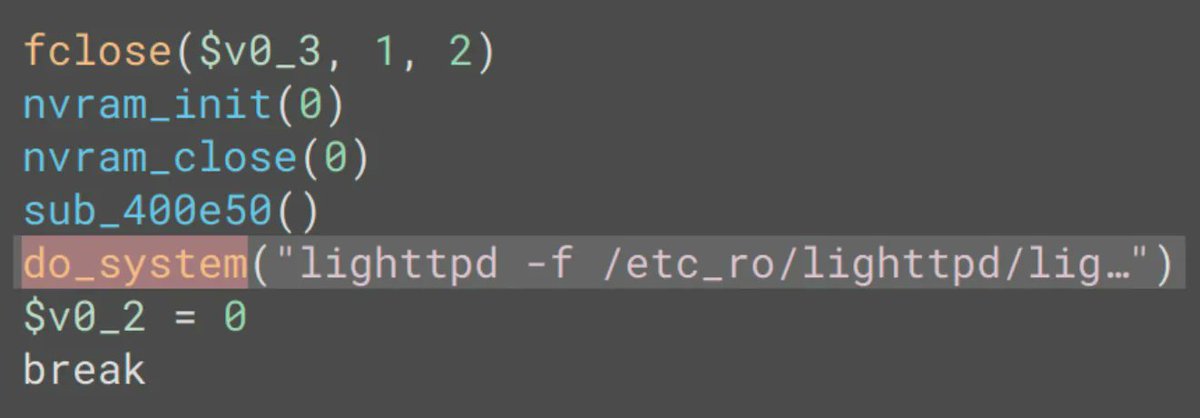
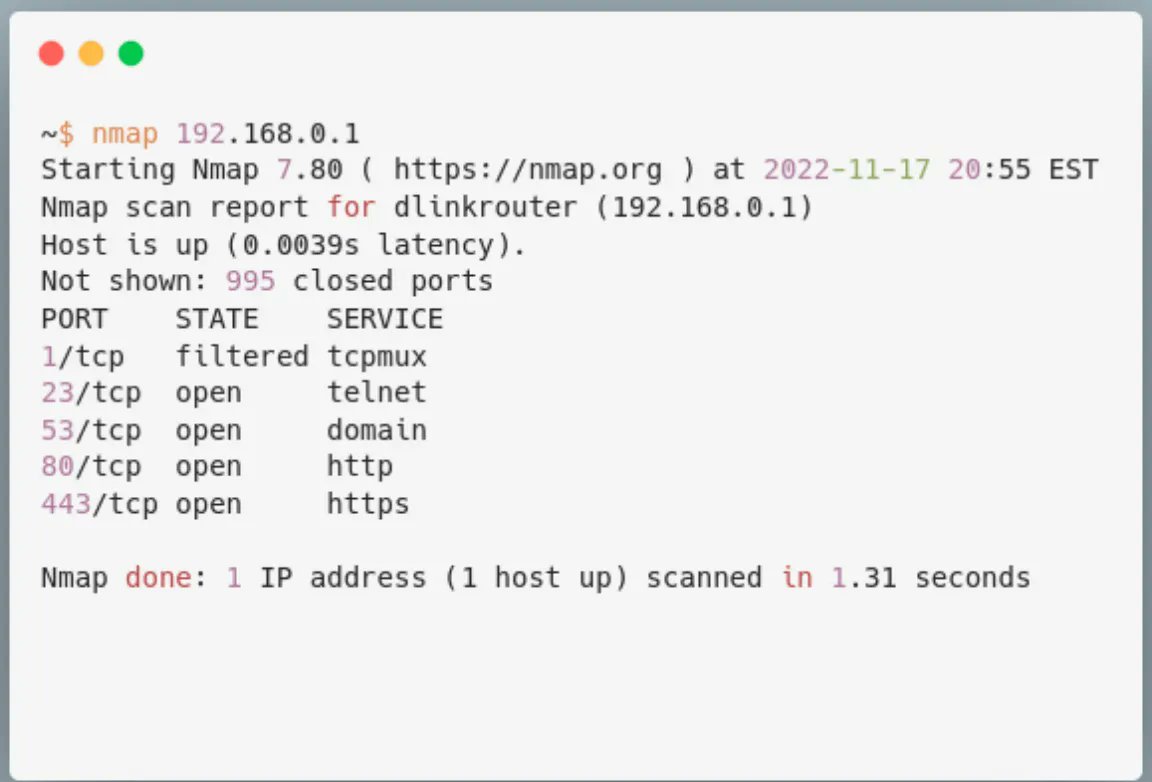
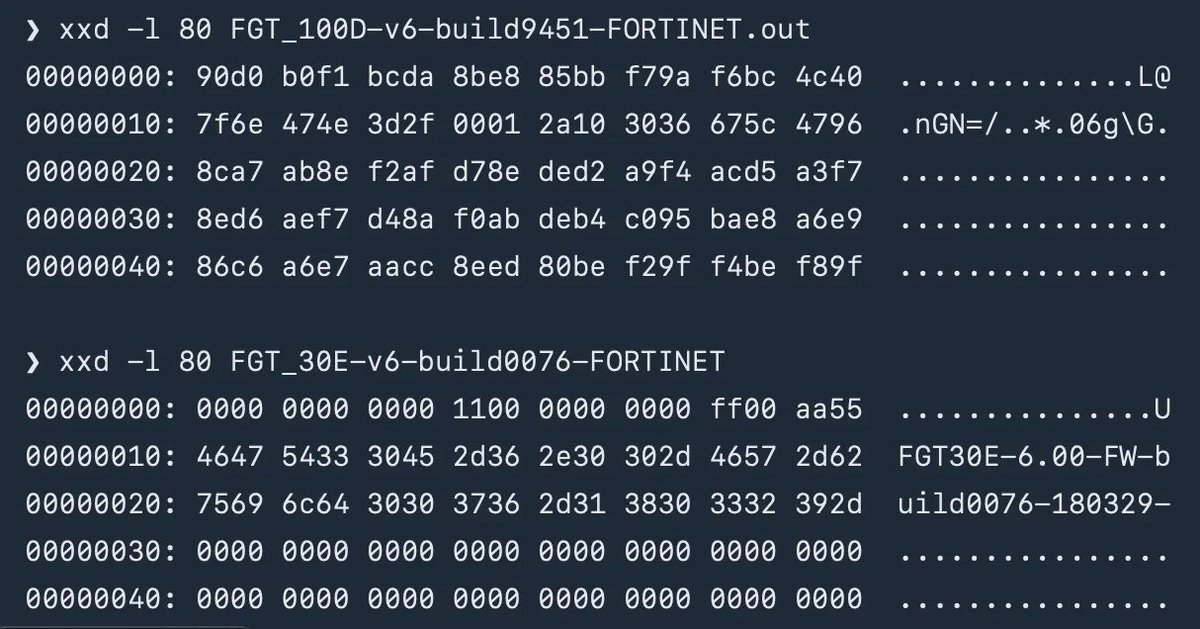
Reverse engineering and breaking bare metal firmware encryption in FortiGate firewalls. bishopfox.com/blog/breaking-… Credits Jon Williams (@bishopfox) #Fortinet #cybersecurity
🎃 Don’t let unpatched devices haunt your designs. The EU Cyber Resilience Act requires secure updates—our TrustMANAGER platform helps you stay compliant and protected. 🦇 Learn more: mchp.us/48LM7zv. #CyberResilience #IoTSecurity
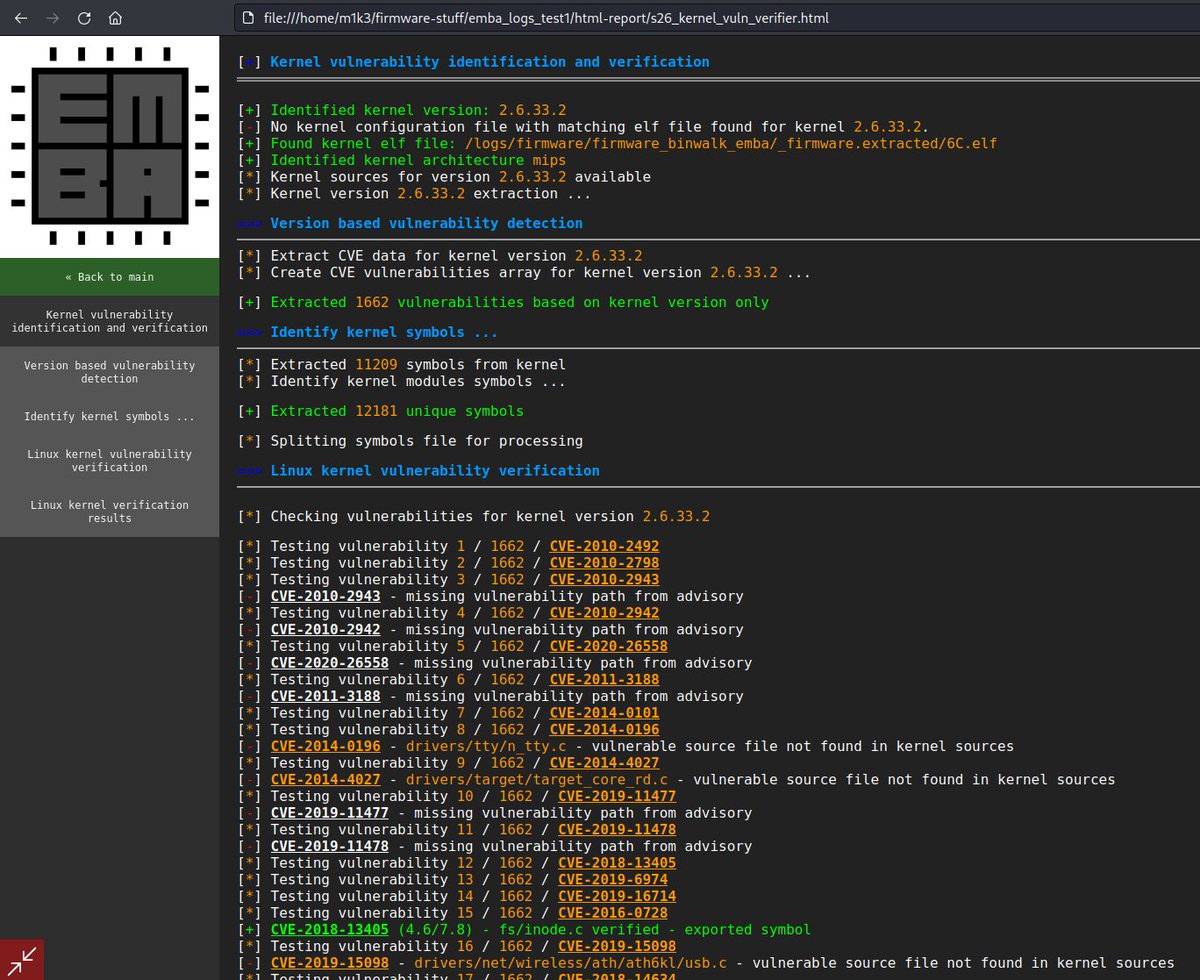
You are also bored from searching thousands of kernel CVEs for a matching vulnerability with exploit code during firmware analysis? Check the new EMBA feature for kernel CVE verification. Let's improve IoT pentesting

DIY cybersecurity for IoT sounds good—until it’s not. Learn why custom stacks are hard to scale, expensive to maintain, and how platform-based solutions offer a better path forward. #EdgeAI #IoTSecurity #FirmwareProtection #CRA #NIS2 @thistlesec electronicsmedia.info/2025/09/02/cyb…
electronicsmedia.info
Cybersecurity for IoT devices: How to avoid the risk and cost of implementing a DIY solution
Cybersecurity for IoT devices: Learn why building your own IoT cybersecurity stack can be risky, costly, and hard to scale—and how platform-based solutions offer faster, safer alternatives.
Infineon’s PSOC Control C3 microcontrollers offer advanced Post-Quantum Cryptography for secure industrial embedded applications. #CNSA2.0 #embeddedsecurity #FirmwareProtection

🔐 Seamless security for embedded systems. Emproof Nyx integrates protection directly into your firmware with no source code changes and no disruption. 🔗 emproof.com/architecture-i… #EmbeddedSecurity #FirmwareProtection #BinarySecurity

Missed a webinar or event? Catch full replays and highlights on our YouTube channel, covering embedded security, reverse engineering, and more. 📺 Subscribe: youtube.com/channel/UC8zEy… #EmbeddedSecurity #FirmwareProtection #ReverseEngineering #TechWebinars
Security that works in theory isn’t enough it needs to perform in real-world embedded environments. Emproof’s architecture supports secure integration from MCUs to full SoCs. 🔗 emproof.com/architecture-i… #EmbeddedSecurity #FirmwareProtection #IoTSecurity #MicrocontrollerSecurity
emproof.com
Architecture and Integration - Emproof
Compatible by design Emproof Nyx is built for the real-world complexity of embedded systems: from microcontrollers running bare-metal programs or real-time operating systems, to high-performance […]
Essential Firmware Protection: Tactics to Secure Your Devices #FirmwareProtection #DeviceSecurity #SecureBoot #CyberSecurity #BootKitty #FirmwareUpdates #AccessControl #TechSafety #VulnerabilityManagement #ITSecurity
7/13 macOS Sequoia 15.2 patches IOMobileFrameBuffer issue, stopping potential code execution in DCP firmware. #MacOSSecurity #FirmwareProtection 🌐
Binarly @binarly_io Raises $3.6 Million in Seed Round #SaaS #AI #FirmwareProtection #cybersecurity #seedround to secure the #firmware supply chain #funding thesaasnews.com/news/binarly-r…
You spent a lot of time, energy and money developing your firmware. Now, here are some "don'ts" when you are protecting it from vulnerabilities. bit.ly/3dNeejE #security #firmwareprotection #firmware
You spent a lot of time, energy and money developing your firmware. Now, here are some "don'ts" when you are protecting it from vulnerabilities. bit.ly/3dNeejE #security #firmwareprotection #firmware
You spent a lot of time, energy and money developing your firmware. Now, here are some "don'ts" when you are protecting it from vulnerabilities. bit.ly/3dNeejE #security #firmwareprotection #firmware
You spent a lot of time, energy and money developing your firmware. Now, here are some "don'ts" when you are protecting it from vulnerabilities. bit.ly/3dNeejE #security #firmwareprotection #firmware
Before you ship your firmware, stop and check our list of 5 Don'ts When Protecting Your Firmware. You will be glad you did bit.ly/3dNeejE #security #firmwareprotection #firmware
Infineon’s PSOC Control C3 microcontrollers offer advanced Post-Quantum Cryptography for secure industrial embedded applications. #CNSA2.0 #embeddedsecurity #FirmwareProtection

🔐 Seamless security for embedded systems. Emproof Nyx integrates protection directly into your firmware with no source code changes and no disruption. 🔗 emproof.com/architecture-i… #EmbeddedSecurity #FirmwareProtection #BinarySecurity

Before you ship your firmware, stop and check our list of 5 Don'ts When Protecting Your Firmware. You will be glad you did bit.ly/2SXXSup #security #firmwareprotection #firmware

You spent a lot of time, energy, and money developing your firmware. Now, here are some "don'ts" when you are protecting it from vulnerabilities. bit.ly/2SXXSup #security #firmwareprotection #firmware

You spent a lot of time, energy and money developing your firmware. Now, here are some "don'ts" when you are protecting it from vulnerabilities. bit.ly/2SXXSup #security #firmwareprotection #firmware

Before you ship your firmware, stop and check our list of 5 Don'ts When Protecting Your Firmware. You will be glad you did bit.ly/2SXXSup #security #firmwareprotection #firmware

Something went wrong.
Something went wrong.
United States Trends
- 1. #SNME 72.3K posts
- 2. #WorldSeries 136K posts
- 3. Ohtani 58.7K posts
- 4. Bo Bichette 22.4K posts
- 5. Gimenez 14.2K posts
- 6. Blue Jays 78.1K posts
- 7. Jesse Love 2,903 posts
- 8. Mateer 2,428 posts
- 9. Jordan Marshall 1,210 posts
- 10. Hugh Freeze 1,377 posts
- 11. Max Scherzer 12.4K posts
- 12. Shohei 41.3K posts
- 13. Zilisch 4,393 posts
- 14. Wrobleski 6,460 posts
- 15. CM Punk 24.5K posts
- 16. #UFCVegas110 14.6K posts
- 17. Purdue 4,109 posts
- 18. Sellers 9,458 posts
- 19. Springer 13.9K posts
- 20. #AEWCollision 9,160 posts

























