#javasecurity نتائج البحث
Is your Java app truly secure? Java is secure by design, but real protection depends on how you code, configure & deploy. See key Java security best practices, common risks & how to secure your pipelines 👇 ➡️ xygeni.io/blog/java-secu… #JavaSecurity #AppSec #DevSecOps #Xygeni

🚨 CRITICAL: Hutool <5.8.4 lets attackers exploit QLExpressEngine for possible RCE—Java apps at risk! Audit & upgrade ASAP. Finance, health, gov sectors especially alert. Details: radar.offseq.com/threat/cve-202… #OffSeq #RCE #JavaSecurity

1.2 billion vulnerable Java dependencies are downloaded every month by open source consumers. Shockingly, 96% of these risky downloads could have been avoided. #JavaSecurity #OpenSource #Cybersecurity #softwaresecuritysoftware

🔐 Master real-world security skills! Join #NareshIT’s FREE 2-day workshop: Breaking & Fixing Java Login – SQL Injection vs Secure Coding by Mr. Kishan on 22–23 Nov, 2 PM IST. Register Link: t.ly/FWSBFJL-22N #JavaSecurity #SecureCoding #SQLInjection #CyberAwareness

A critical vulnerability, Log4Shell, exposed Apache Log4j for remote code execution. Discovered in 2021, attackers can exploit it via JNDI strings. This flaw impacts many Java applications. ⚠️ #JavaSecurity #Log4j #USA link: ift.tt/RwgtNhm

🔒 Prevent security flaws before they happen — SpotBugs can catch risky code patterns early. #JavaSecurity
Apache Parquet flaw in Java tool lets attackers run code via crafted files, putting big data apps using Hadoop and Spark at critical risk. #CyberSecurity #BigData #JavaSecurity

J is for Java Security: Keep your Java applications secure and up-to-date with ExtremeVPN. Stay protected from Java-related vulnerabilities and ensure the safety of your digital assets. #JavaSecurity #ExtremeVPN #CyberSecurity #JavaApps #OnlineSafety #DataProtection

Are your Java applications prepared for cyber threats? Explore strategies like continuous monitoring, secure dependency management, and runtime controls to fortify your code. 🚀🔒 #CyberSecurity #JavaDev #JavaSecurity #SoftwareDevelopment elinext.com/blog/java-secu…

🚨 CRITICAL: HubSpot jinjava <2.8.1 flaw enables remote code execution via unsafe deserialization! Java app users at risk—patch now. 🔒 Details: radar.offseq.com/threat/cve-202… #OffSeq #CVE202559340 #JavaSecurity

🔐 Java 25 (LTS) adds a new KDF API (JEP 510)! KDFs = algorithms that safely derive new keys from an existing secret. ✅ HKDF built in ✅ Secure key material generation ✅ Prepares Java for post-quantum crypto 🌐 #Java25 #JEP510 #JavaSecurity #Cryptography #PostQuantum

MergeBase simplifies the generation of SBOM for your Java applications. Discover the power of SBOMs in enhancing your Java security. Gain insights and take action to protect your applications and valuable assets. Get a free SBOM here: hubs.ly/Q01X3qXq0 #sbom #javasecurity
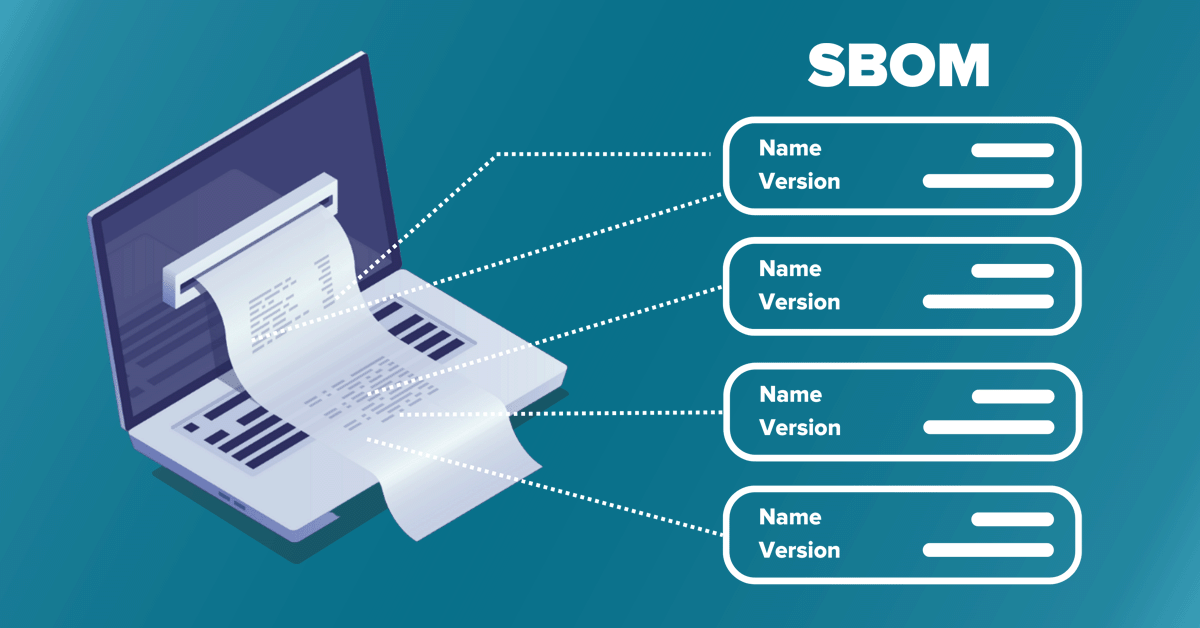
Building applications with third-party libraries in Java accelerates development but exposes you to vulnerabilities. We've compiled a list of the most critical Java CVEs, considering risk levels. Check the full list here: hubs.ly/Q01X3wxG0 #JavaSecurity #Cybersecurity

Spring Cloud Gateway: CVE-2025-41253 Summary A SpEL injection flaw in Spring Cloud Gateway can leak sensitive environment variables. All users should review configs and patch ASAP. For more details, read ZeroPath's blog on this vuln. #AppSec #InfoSec #JavaSecurity…
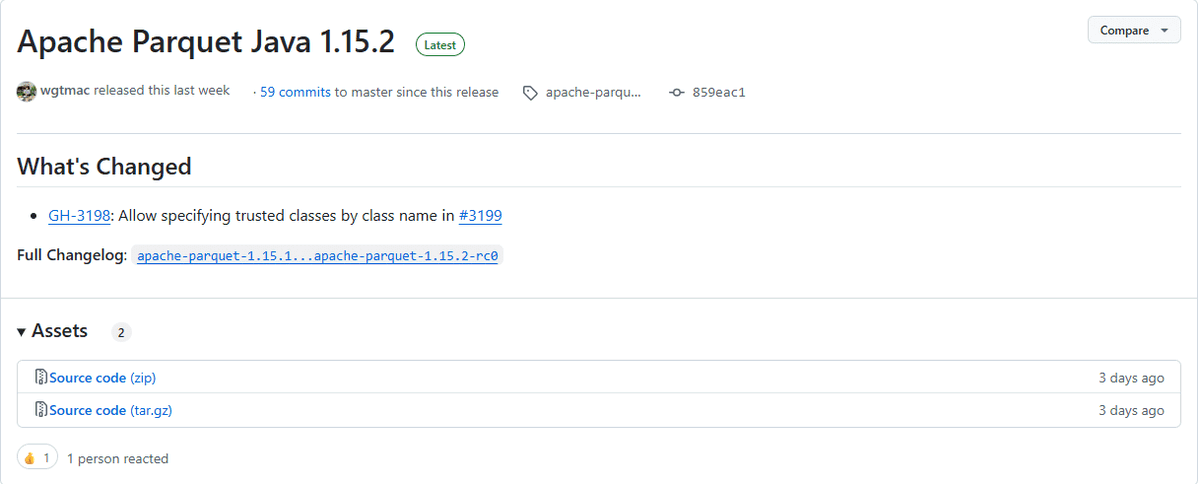
A serious vulnerability (CVE-2025-46762) in Apache Parquet Java allows remote code execution via insecure parquet-avro module schema parsing. All versions up to 1.15.1 are affected. Upgrade to 1.15.2. ⚠️ #JavaSecurity #DataBreach #USA link: ift.tt/OcZ1rBb
NetSPI Security Consultant Mayuri Bochare has published an insightful deep-dive on securing Java Spring applications through code review. 👉 Read the full article: ow.ly/IWfx50WnoVy #proactivesecurity #JavaSecurity #SecureCodeReview

Unlocking security flaws in web apps can lead to $50K in bug bounties! Java's URL handling & Spring Boot actuators reveal critical vulnerabilities. 💰🔍 #BugBounty #JavaSecurity #USA link: ift.tt/ydgCp0V
🚨 A critical RCE vulnerability (CVE-2025-24813) in Apache Tomcat is being exploited in the wild. Attackers can gain control with a single PUT API request! Affected versions include 9.0.98. #ApacheTomcat #JavaSecurity #USA link: ift.tt/GjoBUDz

⚠️ Your Java app may be fast — but unseen security gaps can turn it into a ticking time bomb. Protect your code. Protect your users. 🔐⚡ #JavaSecurity #CyberSecurity #JavaDev #AppSec #SecureCoding #AIDevelopment #DevOps #InfoSec #PrinceMonga

🔐 Modern Java Security — Built for Trust Java’s latest updates strengthen application security with: ✔ TLS 1.3 for faster, safer communication ✔ Improved key management ✔ Enhanced SecureRandom for stronger encryption Secure, reliable, future-ready Java. #Java #JavaSecurity

Is your Java app truly secure? Java is secure by design, but real protection depends on how you code, configure & deploy. See key Java security best practices, common risks & how to secure your pipelines 👇 ➡️ xygeni.io/blog/java-secu… #JavaSecurity #AppSec #DevSecOps #Xygeni

Phrack: Twenty years of Escaping the Java Sandbox (Ieu Eauvidoum & disk noise) exploit-db.com/papers/45517/ #Java #Sandbox #JavaSecurity #Phrack #ExploitDev #Infosec

Java security: sign without pin popup stackoverflow.com/questions/6652… #smartcard #java #javasecurity

🚨 CRITICAL: Hutool <5.8.4 lets attackers exploit QLExpressEngine for possible RCE—Java apps at risk! Audit & upgrade ASAP. Finance, health, gov sectors especially alert. Details: radar.offseq.com/threat/cve-202… #OffSeq #RCE #JavaSecurity

Offshore Java projects come with risks. ⚠️ Our checklist helps you avoid fraud & protect your business. 👉 Read the full blog! developers.dev/tech-talk/chec… #OffshoreDevelopment #JavaSecurity #SafeOutsourcing #developersdev

1.2 billion vulnerable Java dependencies are downloaded every month by open source consumers. Shockingly, 96% of these risky downloads could have been avoided. #JavaSecurity #OpenSource #Cybersecurity #softwaresecuritysoftware

A critical vulnerability, Log4Shell, exposed Apache Log4j for remote code execution. Discovered in 2021, attackers can exploit it via JNDI strings. This flaw impacts many Java applications. ⚠️ #JavaSecurity #Log4j #USA link: ift.tt/RwgtNhm

Modern Java is built for trust — security at its core. 🔐TLS 1.3 🎲Stronger SecureRandom 🗝️Better key management Secure by default. Enterprise ready. #Java #JavaSecurity #TLS13 #CyberSecurity #SecureCoding #JDK #EnterpriseSecurity #SoftwareDevelopment #BackendDevelopment #Tech

Deserialization exploits in @Java : why should I Care? Now on @foojayio - @snyksec @BrianVerm's informative #DevSecOps talk @DevoxxUK. Watch now: hubs.ly/Q01gSYv00 #JavaSecurity

Why copy/paste is a dangerous coding technique: buff.ly/2xjxXjH @TheRegister #StackOverflow #JavaSecurity #securecoding

🔒"Maximizing Security with JDK" with @laurspilca ! Dive into JDK's powerful security features, including encryption & digital signatures. Gain practical insights to enhance your #Java security skills. 🌟 #JavaSecurity #JDK #Encryption #DigitalSignatures


& our related guide by @BrianVerm & @rdebusscher ! #DevSecOps #DevOps #javasecurity payara.fish/resource/how-t…

🚨 CRITICAL: HubSpot jinjava <2.8.1 flaw enables remote code execution via unsafe deserialization! Java app users at risk—patch now. 🔒 Details: radar.offseq.com/threat/cve-202… #OffSeq #CVE202559340 #JavaSecurity

NetSPI Security Consultant Mayuri Bochare has published an insightful deep-dive on securing Java Spring applications through code review. 👉 Read the full article: ow.ly/IWfx50WnoVy #proactivesecurity #JavaSecurity #SecureCodeReview

🔐 Master real-world security skills! Join #NareshIT’s FREE 2-day workshop: Breaking & Fixing Java Login – SQL Injection vs Secure Coding by Mr. Kishan on 22–23 Nov, 2 PM IST. Register Link: t.ly/FWSBFJL-22N #JavaSecurity #SecureCoding #SQLInjection #CyberAwareness

#JavaSecurity #SpringBoot #BackendDevelopment #CyberSecurity #TechInnovation #SoftwareEngineering #CloudSecurity #ProgrammingTips 💡 Security is not a product, but a continuous process of improvement and adaptation! 🚀🔒


Something went wrong.
Something went wrong.
United States Trends
- 1. #UFC323 102K posts
- 2. Indiana 98.6K posts
- 3. Mendoza 38K posts
- 4. Ohio State 59.4K posts
- 5. Roach 28.9K posts
- 6. Merab 29.4K posts
- 7. Petr Yan 14.8K posts
- 8. Pantoja 31K posts
- 9. Bama 83.1K posts
- 10. Joshua Van 8,458 posts
- 11. Curt Cignetti 9,044 posts
- 12. Heisman 18K posts
- 13. Manny Diaz 2,578 posts
- 14. #iufb 7,999 posts
- 15. Miami 295K posts
- 16. The ACC 35K posts
- 17. Virginia 46.1K posts
- 18. James Madison 6,233 posts
- 19. James Madison 6,233 posts
- 20. #Big10Championship 2,087 posts


























