#lokibot search results
🔥An email related to VN spreads #LokiBot ✉️hash:88b508f0e10b580ca93c71938b3b6eb97b39a3f3b5cc50b6e8ce855d4bdd3709 IOCs: ☠️103[.]140.251.225 🌐http://eyecos[.]ga/kung/gate.php
![kienbigmummy's tweet image. 🔥An email related to VN spreads #LokiBot
✉️hash:88b508f0e10b580ca93c71938b3b6eb97b39a3f3b5cc50b6e8ce855d4bdd3709
IOCs:
☠️103[.]140.251.225
🌐http://eyecos[.]ga/kung/gate.php](https://pbs.twimg.com/media/FpdxhURaUAAFFjC.jpg)
🛑 'Loki Bot' Listing — CVV Shop Sells Android Loki Bot A CVV marketplace is advertising an advanced Android stealer (card grabber, SMS/USSD intercept, screen locker, contacts & app harvesting, and...). Handle with extreme caution — for #Malware analysts #LokiBot #CyberCrime

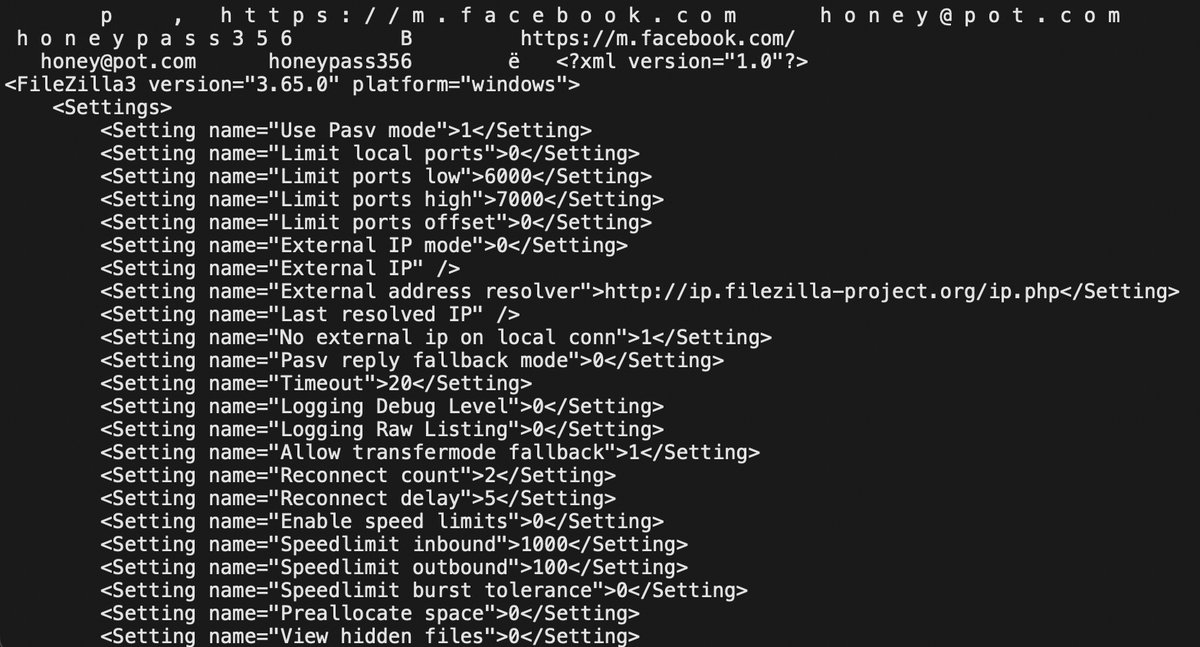
A simple and rarely seen example of extracting data stolen by a #lokibot, not that it's a big deal, but it might come in handy for someone💁♀️

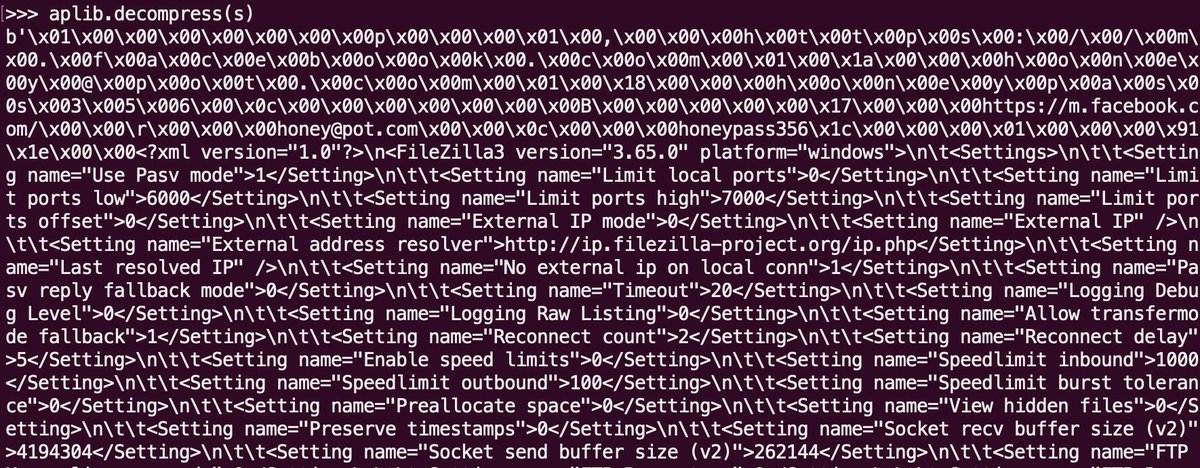
#LokiBot is one of the most enduring credential stealers. On ANYRUN, the first tag for LokiBot was applied on March 6, 2018, making it one of the first public submissions. 🟥 - The aPLib compression algorithm is used to compress the decoded exfiltrated data and credentials from…

🔥 An email spreads #LokiBot ✉️hash: 55f21edd4d3d287b961b57d6215a809cc06fe00c8f649ed812522b8061276409 IOCs: 📄http://192[.]3.223.114/77.doc 👹http://192[.]3.223.114/477/vbc.exe 🌐http://sempersim[.]su/ha1/fre.php
![kienbigmummy's tweet image. 🔥 An email spreads #LokiBot
✉️hash: 55f21edd4d3d287b961b57d6215a809cc06fe00c8f649ed812522b8061276409
IOCs:
📄http://192[.]3.223.114/77.doc
👹http://192[.]3.223.114/477/vbc.exe
🌐http://sempersim[.]su/ha1/fre.php](https://pbs.twimg.com/media/FoWCLnhaUAAd_QL.jpg)
🔥An email spreads #LokiBot was submitted to VT from VN! ✉️hash: 5df9df2e1b4aeec1b8036c627dcaeffb049853d2f1c6bcf83109e541c36a46ac IOCs: 🐛http://195[.]133.40.108/explorer/.win32.exe 🌐http://sempersim[.]su/ha19/fre.php
![kienbigmummy's tweet image. 🔥An email spreads #LokiBot was submitted to VT from VN!
✉️hash: 5df9df2e1b4aeec1b8036c627dcaeffb049853d2f1c6bcf83109e541c36a46ac
IOCs:
🐛http://195[.]133.40.108/explorer/.win32.exe
🌐http://sempersim[.]su/ha19/fre.php](https://pbs.twimg.com/media/Fo_5BPcaMAAxi0h.png)
🔥An email sample related to VN spreads #Lokibot ✉️hash:cb87ec5825659ec1919ac6ffdec4b88e4336c0be420c726ceab1917689fdd161 IOCs: ☠️107[.]175.212.18 🌐http://185[.]246.220.60/shen/five/fre.php
![kienbigmummy's tweet image. 🔥An email sample related to VN spreads #Lokibot
✉️hash:cb87ec5825659ec1919ac6ffdec4b88e4336c0be420c726ceab1917689fdd161
IOCs:
☠️107[.]175.212.18
🌐http://185[.]246.220.60/shen/five/fre.php](https://pbs.twimg.com/media/FqYpbg3agAc46vC.png)
![kienbigmummy's tweet image. 🔥An email sample related to VN spreads #Lokibot
✉️hash:cb87ec5825659ec1919ac6ffdec4b88e4336c0be420c726ceab1917689fdd161
IOCs:
☠️107[.]175.212.18
🌐http://185[.]246.220.60/shen/five/fre.php](https://pbs.twimg.com/media/FqYp4pqakAAhJ_w.jpg)
🔥 An email sample spreads #LokiBot was submitted from VN! ✉️27011215dce27a21aaa6a08898f11672 🐛93ed842119d52c8104eba8c1d3cbfe8e IOCs: 🌐http://161[.]35.102.56/~nikol/?p=314875839320
![kienbigmummy's tweet image. 🔥 An email sample spreads #LokiBot was submitted from VN!
✉️27011215dce27a21aaa6a08898f11672
🐛93ed842119d52c8104eba8c1d3cbfe8e
IOCs:
🌐http://161[.]35.102.56/~nikol/?p=314875839320](https://pbs.twimg.com/media/Fx7TPpnaQAEydr6.png)
![kienbigmummy's tweet image. 🔥 An email sample spreads #LokiBot was submitted from VN!
✉️27011215dce27a21aaa6a08898f11672
🐛93ed842119d52c8104eba8c1d3cbfe8e
IOCs:
🌐http://161[.]35.102.56/~nikol/?p=314875839320](https://pbs.twimg.com/media/Fx7TUSmaIAA0urF.jpg)
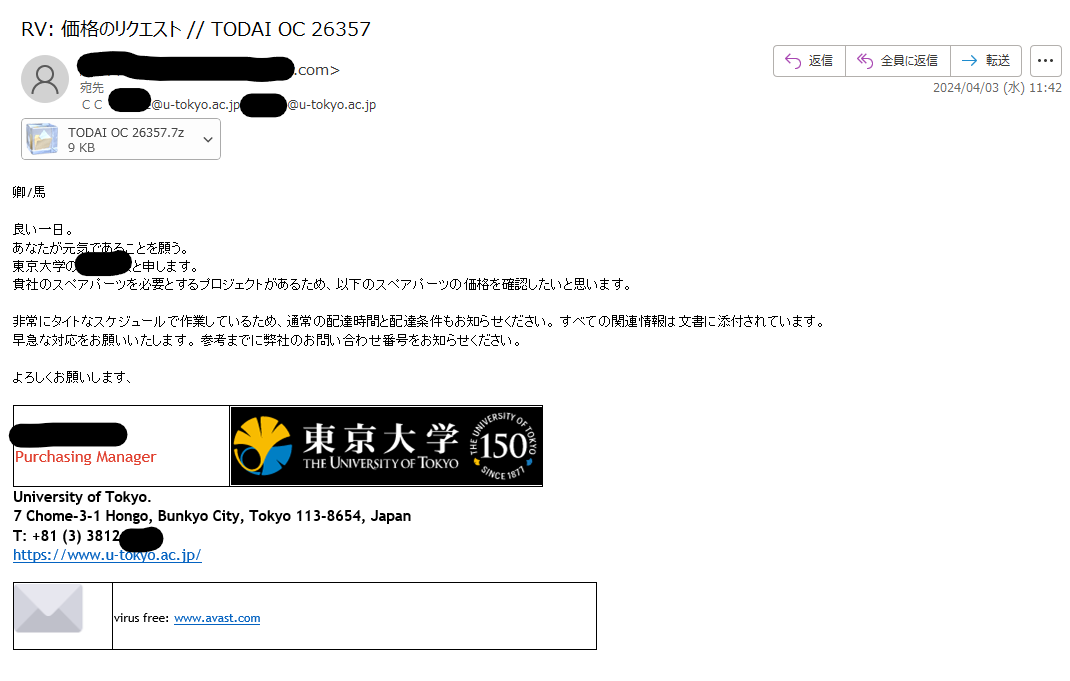
日本語マルウェアメールの接到を確認しています。 #malspam in Japanese #guloader #Lokibot 件名 : RV: 価格のリクエスト // TODAI OC 26357 File name : TODAI OC 26357.7z MD5 : 92b88a1994ff2642ef9f74d419843b6e Payload ffrom :…
🇻🇳 From Positive Hack Talks in Hanoi: @kienbigmummy on using IDA AppCall to deobfuscate malware! Learn how to: 1⃣ Recover hidden WinAPI names (e.g., #LokiBot) 2⃣ Extract strings & C&C addresses (e.g., #Emotet) Applicable to your samples! The slides 👉 static.ptsecurity.com/events/empower…

🔥New #maldoc spreads #LokiBot was submitted to VT from VN 🇻🇳! 📃hash:6be525d464e45656332ec814975fbced53acfc8ff7ba0e165f2c66c85df47e20 ☠️IOCs: 👹http://23[.]227.196.204/Newfold/ansi.exe 💀23[.]227.196.204 🌐http://sempersim[.]su/a14/fre.php
![kienbigmummy's tweet image. 🔥New #maldoc spreads #LokiBot was submitted to VT from VN 🇻🇳!
📃hash:6be525d464e45656332ec814975fbced53acfc8ff7ba0e165f2c66c85df47e20
☠️IOCs:
👹http://23[.]227.196.204/Newfold/ansi.exe
💀23[.]227.196.204
🌐http://sempersim[.]su/a14/fre.php](https://pbs.twimg.com/media/GAa7JcsaMAADYu3.jpg)
🔥Maldoc sample spreads #LokiBot was submitted to VT from VN!! 📄hash:e1d6c159c4e0b5d404d763846914c1b33b26591fd4100da3235335889f6a9407 IOCs: 👹http://103[.]167.92.45/kung/GG18.exe 🌐http://171[.]22.30.164/kung/five/fre.php
![kienbigmummy's tweet image. 🔥Maldoc sample spreads #LokiBot was submitted to VT from VN!!
📄hash:e1d6c159c4e0b5d404d763846914c1b33b26591fd4100da3235335889f6a9407
IOCs:
👹http://103[.]167.92.45/kung/GG18.exe
🌐http://171[.]22.30.164/kung/five/fre.php](https://pbs.twimg.com/media/FrF0vZIaQAAocH5.png)
![kienbigmummy's tweet image. 🔥Maldoc sample spreads #LokiBot was submitted to VT from VN!!
📄hash:e1d6c159c4e0b5d404d763846914c1b33b26591fd4100da3235335889f6a9407
IOCs:
👹http://103[.]167.92.45/kung/GG18.exe
🌐http://171[.]22.30.164/kung/five/fre.php](https://pbs.twimg.com/media/FrF1V0EaQAEERne.jpg)


🚨#Opendir #Malware 🚨 🧵1/2 hxxp://198.46.178.229/55433/ ⚠️#Lokibot #Stealer winiti.exe➡️MD5:33f3dc03864d8d5cce813683d49ad2dd 📡5 C2: hxxp://overclockingmachines.info/bally/fre.php hxxp://kbfvzoboss.bid/alien/fre.php hxxp://alphastand.trade/alien/fre.php

#LOKIBOT Alert: A #Malicious Domain Identified 🚨 Domain: sodiumlaurethsulfatedesyroyer[.]com 🛑 Flagged by 13/96 security vendors as malicious. 💻 What is Lokibot? A sophisticated banking trojan targeting Windows: Steals login credentials, financial info & sensitive data.…
![cyberfeeddigest's tweet image. #LOKIBOT Alert: A #Malicious Domain Identified
🚨 Domain: sodiumlaurethsulfatedesyroyer[.]com
🛑 Flagged by 13/96 security vendors as malicious.
💻 What is Lokibot?
A sophisticated banking trojan targeting Windows:
Steals login credentials, financial info & sensitive data.…](https://pbs.twimg.com/media/Gd8nxVeWMAA2PeO.jpg)
#lokibot #c2 hxxp://ghcopz.shop/BISH/PWS/PvqDq929BSx_A_D_M1n_a.php malware coming from the previous c2: dddotx[.]shop cc: @ViriBack
![banthisguy9349's tweet image. #lokibot #c2
hxxp://ghcopz.shop/BISH/PWS/PvqDq929BSx_A_D_M1n_a.php
malware coming from the previous c2: dddotx[.]shop
cc: @ViriBack](https://pbs.twimg.com/media/GeHuF0RWwAA5pZd.jpg)
From a suspicious spike to a malicious ISO file, we track a #LokiBot infection. Our evaluation includes coverage of the tools we used and the data that resulted from this email campaign. bit.ly/3Yi2uec

#lokibot #malware targetting german citizens with the following domains: kwk-identificatie[.]ir, deutsche-registrierung[.]ir, deutsche-aktivierung[.]ir other domains: sempersim[.]su, cfgd[.]in, bfdlcloud[.]lol c2's :103.215.221.168 | 104.237.252.65 @Gi7w0rm @DeutscheBank
![banthisguy9349's tweet image. #lokibot #malware targetting german citizens with the following domains:
kwk-identificatie[.]ir, deutsche-registrierung[.]ir, deutsche-aktivierung[.]ir
other domains: sempersim[.]su, cfgd[.]in, bfdlcloud[.]lol
c2's :103.215.221.168 | 104.237.252.65
@Gi7w0rm @DeutscheBank](https://pbs.twimg.com/media/GBns454XwAAwMqr.jpg)
2022年の最終週にインフォスティーラー(情報窃取型マルウェア)の #LokiBot のアクティビティ急増が確認されました。この事例からサンプルを解析し、窃取対象となるアプリケーションや窃取されるデータの種類、同マルウェアの主な機能を含むIoCを共有します。 bit.ly/3SO3DJv

🚨 New C2 Detected! 🔗 18[.]239[.]83[.]83 ℹ️ ASN: AS16509 ℹ️ ASN Organization: Amazon.com, Inc. 📍 Country: NL 📍 City: Amsterdam 📅 2025-10-24T17:48:23 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🚨 New C2 Detected! 🔗 18[.]66[.]147[.]8 ℹ️ ASN: AS16509 ℹ️ ASN Organization: Amazon.com, Inc. 📍 Country: DE 📍 City: Mörfelden-Walldorf 📅 2025-10-24T18:08:27 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🚨 New C2 Detected! 🔗 3[.]170[.]19[.]103 ℹ️ ASN: AS16509 ℹ️ ASN Organization: Amazon.com, Inc. 📍 Country: US 📍 City: South Riding 📅 2025-10-23T17:36:14 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🚨 New C2 Detected! 🔗 54[.]208[.]125[.]145 ℹ️ ASN: AS14618 ℹ️ ASN Organization: Amazon.com, Inc. 📍 Country: US 📍 City: Ashburn 📅 2025-10-22T17:09:39 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🚨 New C2 Detected! 🔗 37[.]9[.]111[.]142 ℹ️ ASN: AS13238 ℹ️ ASN Organization: YANDEX LLC 📍 Country: RU 📍 City: Moscow 📅 2025-10-20T18:43:40 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🚨 New C2 Detected! 🔗 61[.]160[.]192[.]98 ℹ️ ASN: AS140293 ℹ️ ASN Organization: CHINATELECOM Jiangsu province Changzhou 5G network 📍 Country: CN 📍 City: Nanjing 📅 2025-10-19T16:15:07 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🚨 New C2 Detected! 🔗 18[.]159[.]18[.]235 ℹ️ ASN: AS16509 ℹ️ ASN Organization: Amazon.com, Inc. 📍 Country: DE 📍 City: Frankfurt am Main 📅 2025-10-19T17:54:22 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🟠#LokiBot se desarrolló en 2015 para robar información de diversas aplicaciones. A pesar de su antigüedad, este malware sigue siendo bastante popular entre los ciberdelincuentes. #QintegraNews #ciberseguridad @Medium medium.com/@anyrun/lokibo…
🚨 New C2 Detected! 🔗 18[.]66[.]112[.]94 ℹ️ ASN: AS16509 ℹ️ ASN Organization: Amazon.com, Inc. 📍 Country: DE 📍 City: Mörfelden-Walldorf 📅 2025-10-17T17:31:58 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🚨 New C2 Detected! 🔗 185[.]111[.]111[.]155 ℹ️ ASN: AS212238 ℹ️ ASN Organization: Datacamp Limited 📍 Country: DE 📍 City: Frankfurt am Main 📅 2025-10-17T17:44:52 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🚨 New C2 Detected! 🔗 31[.]31[.]197[.]13 ℹ️ ASN: AS197695 ℹ️ ASN Organization: "Domain names registrar REG.RU", Ltd 📍 Country: RU 📍 City: Moscow 📅 2025-10-15T18:10:18 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🛑 'Loki Bot' Listing — CVV Shop Sells Android Loki Bot A CVV marketplace is advertising an advanced Android stealer (card grabber, SMS/USSD intercept, screen locker, contacts & app harvesting, and...). Handle with extreme caution — for #Malware analysts #LokiBot #CyberCrime

🚨 New C2 Detected! 🔗 92[.]113[.]16[.]213 ℹ️ ASN: AS47583 ℹ️ ASN Organization: Hostinger International Limited 📍 Country: DE 📍 City: Frankfurt am Main 📅 2025-10-05T17:40:10 ℹ️ Type: #cnc - #c2 ℹ️ Family: #LokiBot #ThreatIntelligence #IoCs #Malware
🛑 'Loki Bot' Listing — CVV Shop Sells Android Loki Bot A CVV marketplace is advertising an advanced Android stealer (card grabber, SMS/USSD intercept, screen locker, contacts & app harvesting, and...). Handle with extreme caution — for #Malware analysts #LokiBot #CyberCrime

🔥An email related to VN spreads #LokiBot ✉️hash:88b508f0e10b580ca93c71938b3b6eb97b39a3f3b5cc50b6e8ce855d4bdd3709 IOCs: ☠️103[.]140.251.225 🌐http://eyecos[.]ga/kung/gate.php
![kienbigmummy's tweet image. 🔥An email related to VN spreads #LokiBot
✉️hash:88b508f0e10b580ca93c71938b3b6eb97b39a3f3b5cc50b6e8ce855d4bdd3709
IOCs:
☠️103[.]140.251.225
🌐http://eyecos[.]ga/kung/gate.php](https://pbs.twimg.com/media/FpdxhURaUAAFFjC.jpg)
A simple and rarely seen example of extracting data stolen by a #lokibot, not that it's a big deal, but it might come in handy for someone💁♀️


#LokiBot is one of the most enduring credential stealers. On ANYRUN, the first tag for LokiBot was applied on March 6, 2018, making it one of the first public submissions. 🟥 - The aPLib compression algorithm is used to compress the decoded exfiltrated data and credentials from…


🇻🇳 From Positive Hack Talks in Hanoi: @kienbigmummy on using IDA AppCall to deobfuscate malware! Learn how to: 1⃣ Recover hidden WinAPI names (e.g., #LokiBot) 2⃣ Extract strings & C&C addresses (e.g., #Emotet) Applicable to your samples! The slides 👉 static.ptsecurity.com/events/empower…



🚨#Opendir #Malware 🚨 🧵1/2 hxxp://198.46.178.229/55433/ ⚠️#Lokibot #Stealer winiti.exe➡️MD5:33f3dc03864d8d5cce813683d49ad2dd 📡5 C2: hxxp://overclockingmachines.info/bally/fre.php hxxp://kbfvzoboss.bid/alien/fre.php hxxp://alphastand.trade/alien/fre.php

🔥 An email spreads #LokiBot ✉️hash: 55f21edd4d3d287b961b57d6215a809cc06fe00c8f649ed812522b8061276409 IOCs: 📄http://192[.]3.223.114/77.doc 👹http://192[.]3.223.114/477/vbc.exe 🌐http://sempersim[.]su/ha1/fre.php
![kienbigmummy's tweet image. 🔥 An email spreads #LokiBot
✉️hash: 55f21edd4d3d287b961b57d6215a809cc06fe00c8f649ed812522b8061276409
IOCs:
📄http://192[.]3.223.114/77.doc
👹http://192[.]3.223.114/477/vbc.exe
🌐http://sempersim[.]su/ha1/fre.php](https://pbs.twimg.com/media/FoWCLnhaUAAd_QL.jpg)
![v0lundr_'s tweet image. #opendir on 23.227.196.204 spreading #Lokibot and reaching out to good old sempersim[.]su](https://pbs.twimg.com/media/GAP66xHWsAADrQA.png)
#C2, #Malware #Lokibot hxxp://werdotx[.]shop/Devil/PWS/PvqDq929BSx_A_D_M1n_a.php hxxps://trvtest[.]click/RF/PWS/PvqDq929BSx_A_D_M1n_a.php cc:@500mk500, @HuntIO, @ViriBack, @drb_ra, @hasherezade,@ReversingLabs, @JAMESWT_MHT,@Arkbird_SOLG,@0xor0ne,@ESETresearch,@0x6rss ,…
![cyberfeeddigest's tweet image. #C2, #Malware #Lokibot
hxxp://werdotx[.]shop/Devil/PWS/PvqDq929BSx_A_D_M1n_a.php
hxxps://trvtest[.]click/RF/PWS/PvqDq929BSx_A_D_M1n_a.php
cc:@500mk500, @HuntIO,
@ViriBack, @drb_ra, @hasherezade,@ReversingLabs, @JAMESWT_MHT,@Arkbird_SOLG,@0xor0ne,@ESETresearch,@0x6rss ,…](https://pbs.twimg.com/media/GYRAiMZWEAAtPKP.jpg)
C2 panel of #Lokibot #Stealer #Malware detected: hxxps://touxzw[.]ir/sweetwhore/five/PvqDq929BSx_A_D_M1n_a.php cc:@abuse_ch #cybersecurity #malware #Lockibot #Stealer
![cyberfeeddigest's tweet image. C2 panel of #Lokibot #Stealer #Malware detected: hxxps://touxzw[.]ir/sweetwhore/five/PvqDq929BSx_A_D_M1n_a.php
cc:@abuse_ch
#cybersecurity #malware #Lockibot #Stealer](https://pbs.twimg.com/media/GXQQVn7XoAAmmRl.jpg)
🚨#Opendir #Malware🚨 hxxp://66.63.187.231/35/ ⚠️#Lokibot ☣️TU-35.exe ➡️4dea06ea49de777e6458e274d7bd5dae 📡http://94.156.177.41/maxzi/five/fre.php 📡hxxp://kbfvzoboss.bid/alien/fre.php 📡hxxp://alphastand.trade/alien/fre.php 📡hxxp://alphastand.win/alien/fre.php

🔥 An email sample spreads #LokiBot was submitted from VN! ✉️27011215dce27a21aaa6a08898f11672 🐛93ed842119d52c8104eba8c1d3cbfe8e IOCs: 🌐http://161[.]35.102.56/~nikol/?p=314875839320
![kienbigmummy's tweet image. 🔥 An email sample spreads #LokiBot was submitted from VN!
✉️27011215dce27a21aaa6a08898f11672
🐛93ed842119d52c8104eba8c1d3cbfe8e
IOCs:
🌐http://161[.]35.102.56/~nikol/?p=314875839320](https://pbs.twimg.com/media/Fx7TPpnaQAEydr6.png)
![kienbigmummy's tweet image. 🔥 An email sample spreads #LokiBot was submitted from VN!
✉️27011215dce27a21aaa6a08898f11672
🐛93ed842119d52c8104eba8c1d3cbfe8e
IOCs:
🌐http://161[.]35.102.56/~nikol/?p=314875839320](https://pbs.twimg.com/media/Fx7TUSmaIAA0urF.jpg)
Threat actor TA2540 continued its high-volume email activity in November, with campaign message volumes as high as six figures in some cases. While the group has recently favored #AgentTesla, multiple campaigns featured #LokiBot #malware. @ThreatInsight 💡

🔥An email sample related to VN spreads #Lokibot ✉️hash:cb87ec5825659ec1919ac6ffdec4b88e4336c0be420c726ceab1917689fdd161 IOCs: ☠️107[.]175.212.18 🌐http://185[.]246.220.60/shen/five/fre.php
![kienbigmummy's tweet image. 🔥An email sample related to VN spreads #Lokibot
✉️hash:cb87ec5825659ec1919ac6ffdec4b88e4336c0be420c726ceab1917689fdd161
IOCs:
☠️107[.]175.212.18
🌐http://185[.]246.220.60/shen/five/fre.php](https://pbs.twimg.com/media/FqYpbg3agAc46vC.png)
![kienbigmummy's tweet image. 🔥An email sample related to VN spreads #Lokibot
✉️hash:cb87ec5825659ec1919ac6ffdec4b88e4336c0be420c726ceab1917689fdd161
IOCs:
☠️107[.]175.212.18
🌐http://185[.]246.220.60/shen/five/fre.php](https://pbs.twimg.com/media/FqYp4pqakAAhJ_w.jpg)
🔥An email spreads #LokiBot was submitted to VT from VN! ✉️hash: 5df9df2e1b4aeec1b8036c627dcaeffb049853d2f1c6bcf83109e541c36a46ac IOCs: 🐛http://195[.]133.40.108/explorer/.win32.exe 🌐http://sempersim[.]su/ha19/fre.php
![kienbigmummy's tweet image. 🔥An email spreads #LokiBot was submitted to VT from VN!
✉️hash: 5df9df2e1b4aeec1b8036c627dcaeffb049853d2f1c6bcf83109e541c36a46ac
IOCs:
🐛http://195[.]133.40.108/explorer/.win32.exe
🌐http://sempersim[.]su/ha19/fre.php](https://pbs.twimg.com/media/Fo_5BPcaMAAxi0h.png)
#lokibot #c2 hxxp://ghcopz.shop/BISH/PWS/PvqDq929BSx_A_D_M1n_a.php malware coming from the previous c2: dddotx[.]shop cc: @ViriBack
![banthisguy9349's tweet image. #lokibot #c2
hxxp://ghcopz.shop/BISH/PWS/PvqDq929BSx_A_D_M1n_a.php
malware coming from the previous c2: dddotx[.]shop
cc: @ViriBack](https://pbs.twimg.com/media/GeHuF0RWwAA5pZd.jpg)
日本語マルウェアメールの接到を確認しています。 #malspam in Japanese #guloader #Lokibot 件名 : RV: 価格のリクエスト // TODAI OC 26357 File name : TODAI OC 26357.7z MD5 : 92b88a1994ff2642ef9f74d419843b6e Payload ffrom :…

LokiBot, is an information stealer malware that harvests credentials from the most popular web browsers, FTP, email clients, and over a hundred applications installed on the infected machine. #LokiBot #stealer #malware #cybersecurity


Something went wrong.
Something went wrong.
United States Trends
- 1. #DWTS 28.3K posts
- 2. Northern Lights 9,848 posts
- 3. Elaine 54.7K posts
- 4. #RHOSLC 4,551 posts
- 5. Dylan 28.8K posts
- 6. #Aurora 2,583 posts
- 7. Robert 95.3K posts
- 8. Whitney 7,929 posts
- 9. #WWENXT 9,496 posts
- 10. Carrie Ann 1,479 posts
- 11. Louisville 10K posts
- 12. Meredith 3,291 posts
- 13. Alix 8,151 posts
- 14. Daniella 2,800 posts
- 15. Wake Forest 2,165 posts
- 16. Mikel Brown N/A
- 17. #DancingWithTheStars N/A
- 18. Woody 23.4K posts
- 19. Jeezy 3,627 posts
- 20. Kentucky 21.4K posts



























![v0lundr_'s tweet image. #opendir on 146.70.35[.]211 delivering #lokibot](https://pbs.twimg.com/media/GAAzgxZXUAA1_6i.png)

