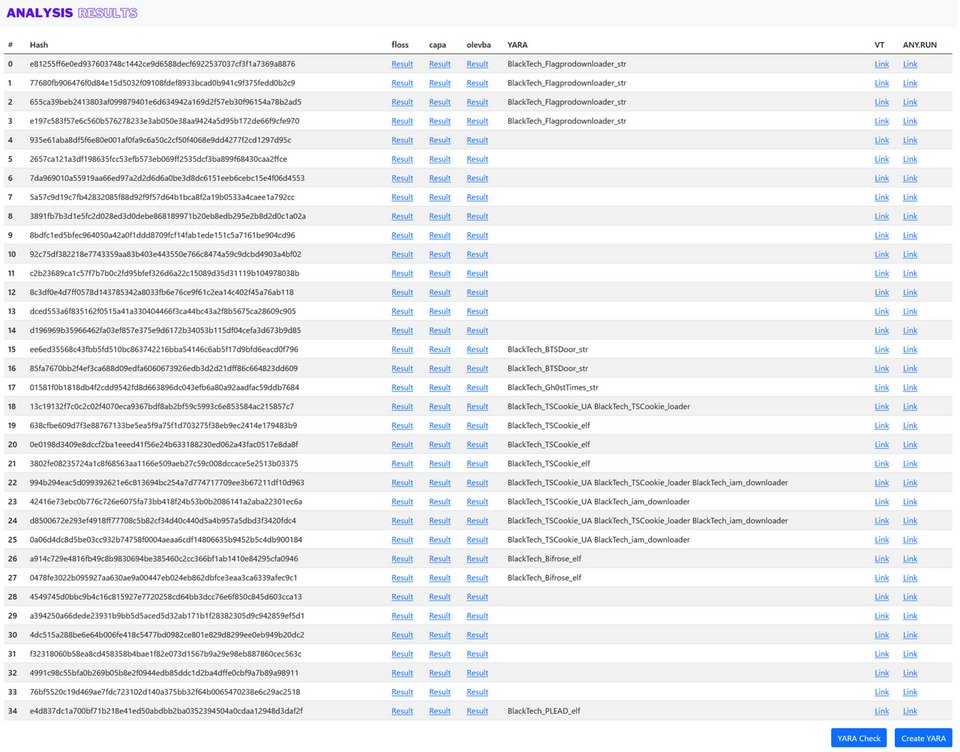
#malwareanalysis search results
It’s finally here! 📦 Just received my own printed copies of MAoS – Malware Analysis on Steroids 🔥 There’s nothing like holding your work after months of writing, research, and late-night debugging. Get your copy here👉amazon.com/dp/B0FQDGZGZW #CyberSecurity #MalwareAnalysis…


We’re excited to welcome Anmol Maurya, Staff Malware Reverse Engineer @ Palo Alto Networks, as he reveals how attackers leverage Go’s portability to target Mac & Linux—and why multi-OS defenses matter. #CyberSecurity #MalwareAnalysis #Infosec #ThreatResearch

RL ❤️ #YARArules! We've been writing them for years. Watch below to see how RL Spectra Analyze makes YARA seamless & powerful for the #SOC. #MalwareAnalysis
The PolySwarm ecosystem runs on a diverse set of independent engines, each with its own approach to detecting and classifying threats. Different perspectives. Shared intelligence. Better protection. #CyberSecurity #ThreatIntelligence #MalwareAnalysis #PolySwarm
Example: IDA + DIE — Decode XOR data directly in DIE’s data convertor. A fast workflow for efficient malware analysis. #MalwareAnalysis #XOR #ReverseEngineering #DIE #IDA
🚀 #x33fcon 2025 Onsite Workshop! 🚀 Join @xoreipeip to master software reverse-engineering with Unicorn Engine! Learn to dynamically execute and analyze code to crack encryption and obfuscation in binaries using Python and Ghidra. Perfect for #malwareanalysis,…

Deep dive into CyberGate RAT! 🔬 We unpack this notorious Delphi malware, detail its process injection, persistence, and C2 communication Don't miss the full technical breakdown! Read the analysis: blog.cyber5w.com/cybergate-malw… #C5W #MalwareAnalysis #CyberGate #RAT #DFIR #InfoSec…

Revisited my malware analysis project using FLARE VM and upgraded it with a custom YARA rule to hunt AgentTesla variants. Proud of how it turned out. Shoutout to @ireteeh and @Cyblackorg for this opportunity 🙂 #MalwareAnalysis #YARARules #Cybersecurity #ThreatHunting #FLAREVM

🔥 A week after release and thank God, MAoS – Malware Analysis on Steroids is officially a #1 Best Seller on Amazon! Get your copy today: amazon.com/gp/aw/d/B0FQDL… #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware


Hello! I just dropped a new article about an old but very up-to-date subject. Please let me know if you find anything incorrect or not well-explained. moval0x1.github.io/posts/the-peb-… #malwareanalysis #reverseengineering #malcat #x64dbg #pebwalk #shellcode
moval0x1.github.io
The PEB Walk Anatomy
Practical Techniques for Shellcode & Reversing
🔍 A DLL isn’t a standalone file — it has no main function like an EXE. That’s why we need tools like WinDbg + SOS to uncover where execution really begins. In this week’s drop, we show you how. youtu.be/MsijfXAu3rA?si… #ReverseEngineering #dotnet #MalwareAnalysis #HackDef #dll
Malware hides behind layers of obfuscation. Most analysts slow down there. We don’t. 👊⚡️ #NeZa reveals runtime behavior, API activity, and memory artifacts fast — and you learn to do it hands-on. Train like a real defender, not a spectator. #MalwareAnalysis #DFIR #BlueTeam
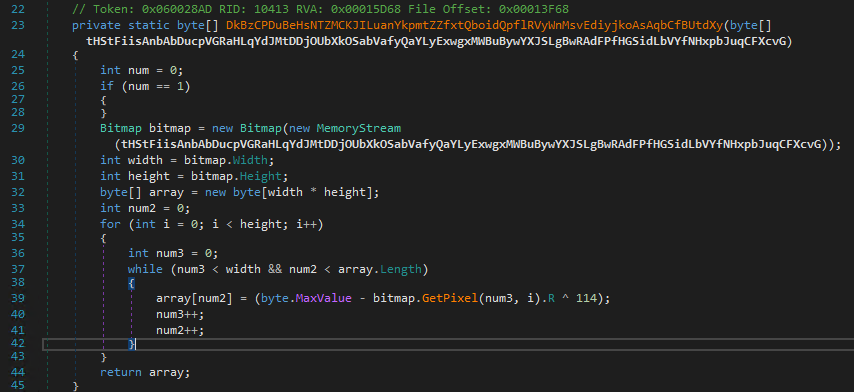
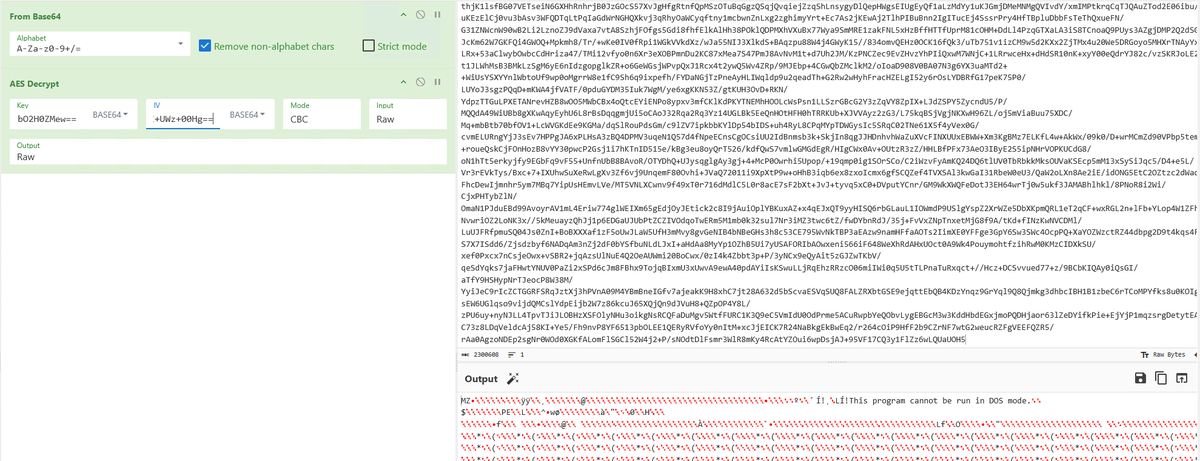
🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 github.com/ShadowOpCode/S… #LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence


A new approach to static analysis with AI that turns days of research into hours. No MCP or live IDA required. Using GPT-5, we completely cracked XLoader v8, one of the most challenging malware families to analyze. #XLoader #MalwareAnalysis #AI research.checkpoint.com/2025/generativ…
CyberProof researchers have analyzed the Maverick banking Trojan, revealing its similarities to the Coyote malware, both targeting Brazilian users via WhatsApp and employing multi-stage attacks with .NET frameworks. #CyberSecurity #MalwareAnalysis cyberproof.com/blog/maverick-…
🚨 New variant spotted: Matanbuchus 3.0 — a rebuilt malware loader advertised on underground forums. Features DNS/HTTPS C2, in-memory execution, reverse shell, morphing builds & multitenant panel. Price: $10K–$15K/month. Active threat. #CyberThreat #Infosec #MalwareAnalysis

🌱🕵️♀️ Every great hacker story starts with curiosity — the urge to ask “how does this work?” Join @_sudhackar at #NullconGoa2026 to advance that spark into a skill, learning through the complexities of #reverseengineering and #malwareanalysis. Know More: nullcon.net/goa-2026/train…

🌐 Two months ago, we uncovered APT Sidewinder’s use of Netlify and Pages[.]dev hosting platforms to deploy phishing portals that impersonated government and defense agencies throughout South Asia. ⬇️ hunt.io/blog/apt-sidew… #MalwareAnalysis #SecurityResearch
🆕 New Research Published in Journal of Cybersecurity and Privacy 🛡️ Integrated Analysis of Malicious Software: Static + Dynamic Perspectives 📖 Read the full paper: mdpi.com/2624-800X/5/4/… #MalwareAnalysis #NetworkSecurity #IntrusionDetection #StaticAnalysis
💀 Top 18 Malware Analysis Tools Every Cybersecurity Enthusiast Must Know ⚡ #CyberSecurity #HackingTools #MalwareAnalysis

CyberProof researchers have analyzed the Maverick banking Trojan, revealing its similarities to the Coyote malware, both targeting Brazilian users via WhatsApp and employing multi-stage attacks with .NET frameworks. #CyberSecurity #MalwareAnalysis cyberproof.com/blog/maverick-…
The PolySwarm ecosystem runs on a diverse set of independent engines, each with its own approach to detecting and classifying threats. Different perspectives. Shared intelligence. Better protection. #CyberSecurity #ThreatIntelligence #MalwareAnalysis #PolySwarm
In questo articolo, scritto per la rivista 8Bit Security, con cui collaboro, esploro le fasi fondamentali dell’analisi dinamica di un malware ELF. blog.8bitsecurity.com/2025/11/10/ana… #reverseengineering #malwareanalysis #elf

Completed my Emotet Maldoc Analysis lab✨ Used CyberChef to decode a malicious PowerShell script, extracted hidden URLs, and analyzed suspicious VBA macros with oletools. This was honestly my favorite lab so far. I really enjoyed every part! #CyberSecurity #MalwareAnalysis




🚨 Why it matters: Deleting malware too soon can erase valuable forensic evidence 🛡️ Action: Use MalwareDecoder.com to decode and analyze malicious payloads before removal #MalwareAnalysis #Quttera #CyberForensics

Old tools can't win new fights. This course updates your analytic tradecraft, focusing on countering modern malware and state-sponsored disinformation campaigns with structured, repeatable methods. #MalwareAnalysis #Tradecraft #InfoWar cyberinteltrainingcenter.com/p/featured
Automating C2 collection from packed and unpacked variants of TinyLoader with Qiling medium.com/@Krknsec/emula… #MalwareAnalysis #ReverseEngineering #Qiling #Infosec #Cybersecurity #ThreatIntel

New release of PEHint v0.4.0 This version brings PEHint closer to being the go-to educational and research-grade PE visualization tool — bridging theory, analysis, and automation. github.com/moval0x1/PEHint #pehint #malwareanalysis #reverseengineering
Intro to Malware Analysis on @TryHackMe shifted my threat analysis approach! Understanding static and dynamic techniques was truly eye-opening. File headers, hash analysis, evasion detection, and forensic tools felt incredibly powerful. #MalwareAnalysis #ThreatHunting #SOC

Check Point Research used ChatGPT + exported IDA data and MCP to accelerate static reverse engineering of XLoader 8.0, extracting runtime keys and uncovering hidden C2 domains in hours instead of days. #xloader #malwareanalysis #ChatGPT research.checkpoint.com/2025/generativ…
🔍 Web Malware Scan Results Website: pointnthink.fr Security Verdict: LOW RISK Full analysis & details: scanmalware.com/scan/17f0d0a3-… #DevSecOps #Ransomware #MalwareAnalysis
scanmalware.com
Security Scan: Untitled
✅ Low Risk - https://www.pointnthink.fr/en/attack-on-titan-an-endless-cycle-of-hatred/
Binary Reverse Engineering vs Binary exploitation #reverseengineering #binaryexploitation #malwareanalysis #vulnerabilityresearch #espincorp e-spincorp.com/reverse-engine…

Enhance your malware analysis skills with Mandiant Academy's Basic Static and Dynamic Analysis course! 🛠️🔍 #MalwareAnalysis #ThreatHunting #DigitalForensics #Cybersecurity cloud.google.com/blog/products/…
Example: IDA + DIE — Decode XOR data directly in DIE’s data convertor. A fast workflow for efficient malware analysis. #MalwareAnalysis #XOR #ReverseEngineering #DIE #IDA
Black Friday sales have started! Link: training.dfirdiva.com/current-discou… Having a sale? Submit it here: training.dfirdiva.com/submit-a-sale-… or tag me in a post about the sale. #DFIR #IncidentResponse #MalwareAnalysis #OSINT #Cybersecurity

If this has piqued your interest, head over to our article to read more ➡️ hunt.io/blog/tinyloade… #ThreatHunting #TinyLoader #MalwareAnalysis #SecurityResearch
🚀 Two months ago, we uncovered the operation behind the malware loader known as #TinyLoader, which was found distributing crypto-theft tools across a global infrastructure. hunt.io/blog/tinyloade… #MalwareAnalysis #SecurityResearch
🛡 Malware has nowhere to hide. Atomesus AI analyzes malicious files, identifies hidden behavior & stops attacks instantly. #AtomesusAI #MalwareAnalysis #CyberDefense #AIShield #SecureTech

It’s finally here! 📦 Just received my own printed copies of MAoS – Malware Analysis on Steroids 🔥 There’s nothing like holding your work after months of writing, research, and late-night debugging. Get your copy here👉amazon.com/dp/B0FQDGZGZW #CyberSecurity #MalwareAnalysis…


🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥 Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg. We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses. [1/24] 🖊️ #Malwareanalysis #Ghidra
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gG0vaUAAkrE4.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gOFMbIAA2_rv.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gVA0bMAAeWzo.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0hjgObwAAyIRM.png)
CyberChef Tips - Creating and Accessing Variables #CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis. [1/2] #malware #malwareanalysis
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTCaMAECV1x.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTabwAAd1RG.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTNa4AAkCq3.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQR2bEAAPiZM.png)
Revisited my malware analysis project using FLARE VM and upgraded it with a custom YARA rule to hunt AgentTesla variants. Proud of how it turned out. Shoutout to @ireteeh and @Cyblackorg for this opportunity 🙂 #MalwareAnalysis #YARARules #Cybersecurity #ThreatHunting #FLAREVM

We’re excited to welcome Anmol Maurya, Staff Malware Reverse Engineer @ Palo Alto Networks, as he reveals how attackers leverage Go’s portability to target Mac & Linux—and why multi-OS defenses matter. #CyberSecurity #MalwareAnalysis #Infosec #ThreatResearch

In one of the #MalwareAnalysis communities I’m in, we were talking about Go malware. Someone mentioned CAPA as a good tool. I have to say, it’s really helpful for finding the 50kb of interesting code buried inside a 5mb Go binary 😎What other tools do you use?

🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 github.com/ShadowOpCode/S… #LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence




FLARE floss applied to all unpacked+dumped samples in Malpedia Nice project by Daniel Plohmann (@push_pnx) Blog post: danielplohmann.github.io/blog/2024/03/0… Github repo: github.com/malpedia/malpe… #malwareanalysis #infosec


🚀 #x33fcon 2025 Onsite Workshop! 🚀 Join @xoreipeip to master software reverse-engineering with Unicorn Engine! Learn to dynamically execute and analyze code to crack encryption and obfuscation in binaries using Python and Ghidra. Perfect for #malwareanalysis,…

🚨 New variant spotted: Matanbuchus 3.0 — a rebuilt malware loader advertised on underground forums. Features DNS/HTTPS C2, in-memory execution, reverse shell, morphing builds & multitenant panel. Price: $10K–$15K/month. Active threat. #CyberThreat #Infosec #MalwareAnalysis

🔍 #Opendir Alert! 📂 Target: ⚠️ hxxps://m[.]bureaux[.]fr/ 📄 Sample Files: Advanced IP Scanner.exe AnyDesk.exe AnyDesk.apk ⚡ Repository contains .apk & .exe files. Handle with caution! 🛡️ 🎯 Potential resource for malware analysts. #CyberSecurity #MalwareAnalysis…
![cyberfeeddigest's tweet image. 🔍 #Opendir Alert!
📂 Target:
⚠️ hxxps://m[.]bureaux[.]fr/
📄 Sample Files:
Advanced IP Scanner.exe
AnyDesk.exe
AnyDesk.apk
⚡ Repository contains .apk & .exe files. Handle with caution! 🛡️
🎯 Potential resource for malware analysts.
#CyberSecurity #MalwareAnalysis…](https://pbs.twimg.com/media/GhhcEuqWoAAUj9f.jpg)
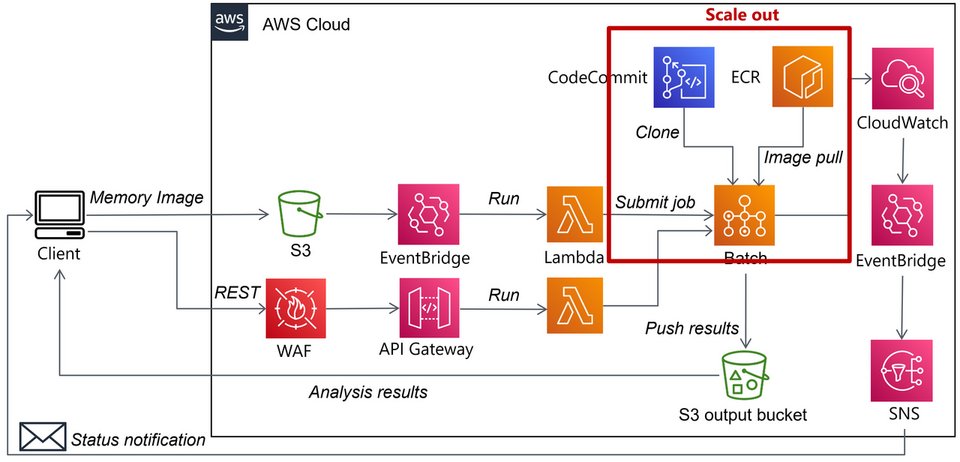
Automating Malware Analysis Operations (MAOps) blogs.jpcert.or.jp/en/2023/01/clo… #Pentesting #MalwareAnalysis #CyberSecurity #Infosec
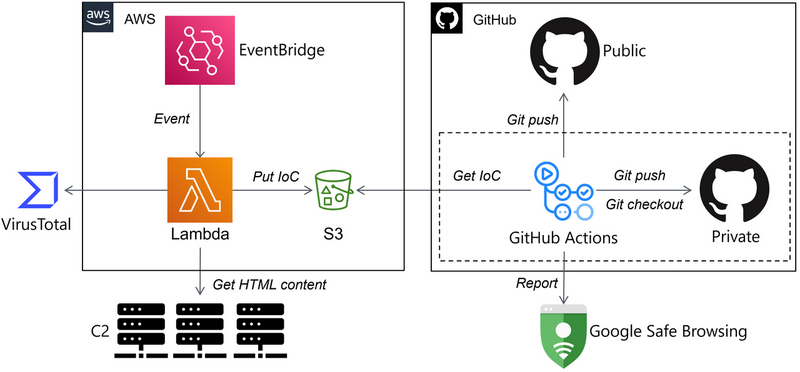
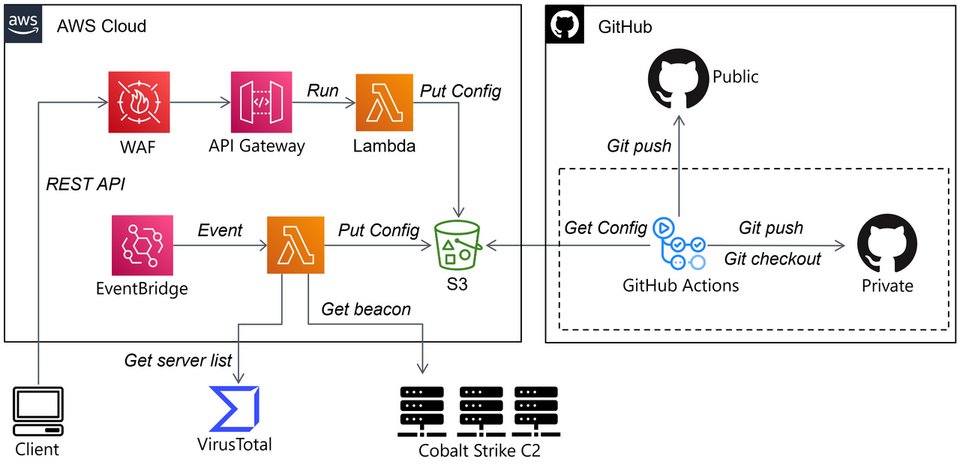
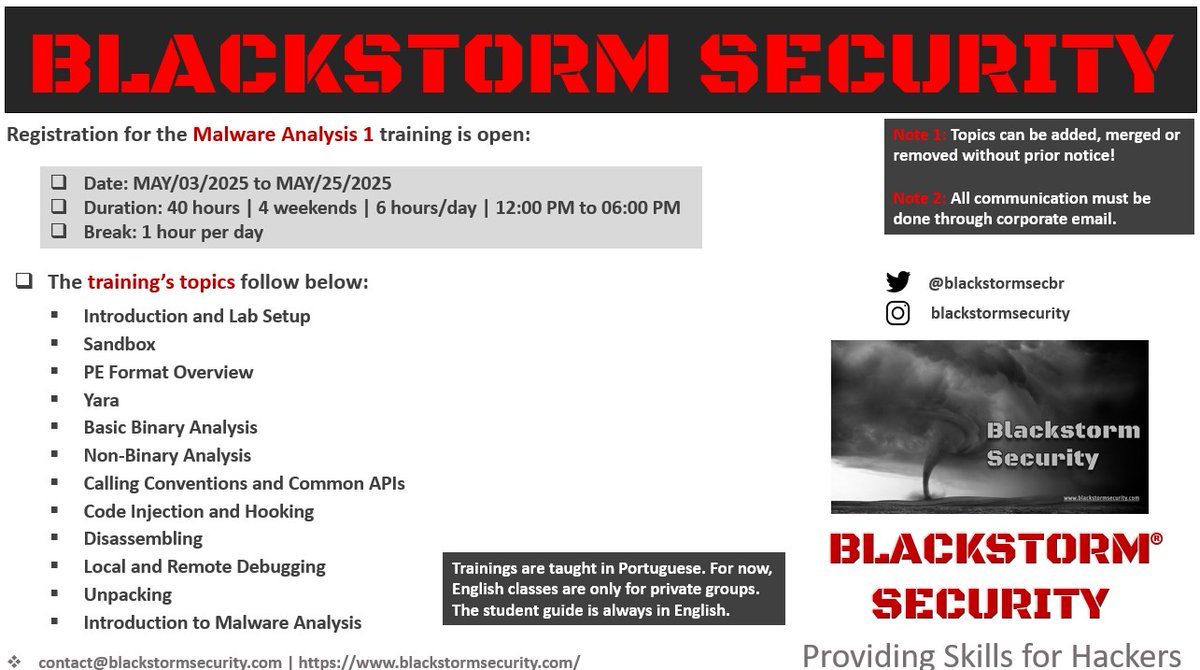
(PT_BR) O treinamento de MALWARE ANALYSIS 1 está com a próxima turma CONFIRMADO para 03/MAIO/2025. Informações adicionais podem ser obtidas no website da Blackstorm Security. #malwareanalysis #informationsecurity #malware #cybersecurity #threathunting #blueteam
📱MasterFred malware uses hidden overlays, permissions, and JavaScript interfaces to steal sensitive data. Get the full analysis here: 8ksec.io/mobile-malware… 🚀For a deeper understanding of mobile malware techniques, explore our course: academy.8ksec.io/course/offensi… #MalwareAnalysis…

🦠💻Explore Part 2 of our Windows Malware blog series on process injections: 8ksec.io/dissecting-win… 📈Ready to sharpen your skills? Browse our courses here: academy.8ksec.io/course/practic… #MalwareAnalysis #Windows #ReverseEngineering

Dive deep into the world of antivirus systems. Learn how static, dynamic, heuristic and unpacking engines work to detect malware. hackers-arise.net/2023/12/12/eva… #CyberSecurity #MalwareAnalysis @three_cube

🔥 A week after release and thank God, MAoS – Malware Analysis on Steroids is officially a #1 Best Seller on Amazon! Get your copy today: amazon.com/gp/aw/d/B0FQDL… #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware


Something went wrong.
Something went wrong.
United States Trends
- 1. #DWTS 28.3K posts
- 2. Northern Lights 9,848 posts
- 3. Elaine 54.7K posts
- 4. #RHOSLC 4,551 posts
- 5. Dylan 28.8K posts
- 6. #Aurora 2,583 posts
- 7. Robert 95.3K posts
- 8. Whitney 7,929 posts
- 9. #WWENXT 9,496 posts
- 10. Carrie Ann 1,479 posts
- 11. Louisville 10K posts
- 12. Meredith 3,291 posts
- 13. Alix 8,151 posts
- 14. Daniella 2,800 posts
- 15. Wake Forest 2,165 posts
- 16. Mikel Brown N/A
- 17. #DancingWithTheStars N/A
- 18. Woody 23.4K posts
- 19. Jeezy 3,627 posts
- 20. Kentucky 21.4K posts























































