#modiloader search results
Threat actor turns a Cabinet (CAB) file into the Loader. It dropped #ModiLoader (aka #DBatLoader) and ultimately deployed Agent Tesla. NEOMS_EOI_FORM.cmd (yep this is CAB file) SHA256: a631e4304cf932de1129cc660fd648125226cfee4059321b4e2048c38b2f9357 Rules & IOCs in🧵 #malware

Dropping a #Yara rule for a new variant of #DBatLoader/#ModiLoader in the wild: github.com/d4rksystem/Yar… #100DaysOfYara

ISC Diary: @malware_traffic saw #GuLoader or #ModiLoader/#DBatLoader style traffic for #RemcosRAT i5c.us/d29990

ISC Diary: @malware_traffic reviews a malspam-based #ModiLoader infection for #RemcosRAT i5c.us/d29896

"Pre_Procurement Verification (Mog Energy)_Ref_TR0029388827772_10_27_2022" malspam mail -> sharepoint URL -> password protected 7z -> 3 #modiloader -> #AveMaria executables C2: pentester0.accesscam[.org Bazaar: bazaar.abuse.ch/browse/tag/pen… check comments for #modiloader opendir



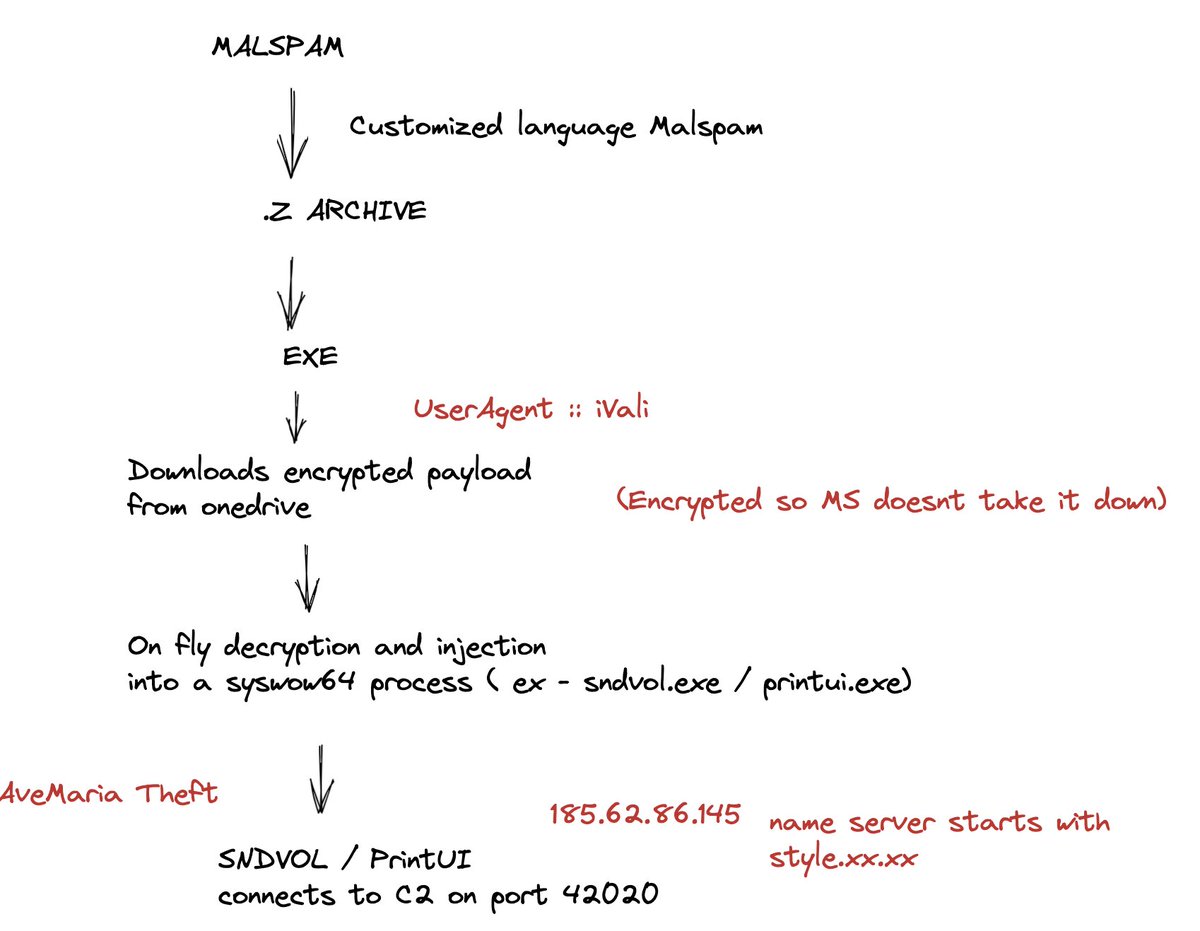
#Modiloader / #Dbatloader The .z archive leads to exe, which uses lVali UserAgent to download encrypted file from Onedrive ( so MS doesn't take it down ). Post decryption its injected in legit MS process like sndvol to do the C2 comms on 42020 port. bazaar.abuse.ch/sample/4473b5d…

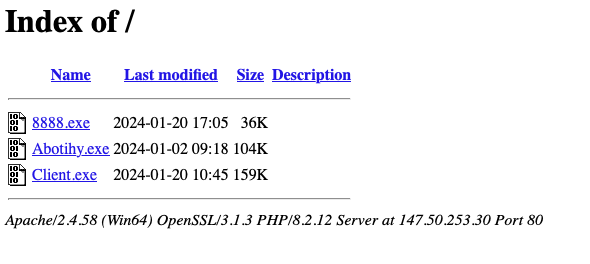
🔓#opendir 147.50.253[.30 🔑Abotihy.exe - #PHEMEDRONE 🔗C2: 💬/bot5358754228:AAE42HAGW1bzIPxU7iVRC_96iDuHcwSjjVo/sendMessage?chat_id=5556872222 🖥️8888.exe - #MODILOADER -> 147.50.253[.30:8888 -> Process.exe 🖥️Client.exe - #NJRAT -> 147.50.253[.30:6522 -> WindowsServices.exe
🚨 Suspicious IP #opendir: 209.126.87[.92:8888 🌐 Domain: premiere-coal-tonight-procedure.trycloudflare[.com 🔗 File chain: iz.exe - #modiloader #remcos 🔽 onedrive[.live.com/download?resid=F4D24344D7B13420%21110&authkey=!AL5-vxbOzO8Bd8E 🔽 255_Sraomttecbk 📝 1/2

📂#modiloader opendir: https://aljassimaluminium[.com/xerror/images/deleted/webcloudserverimagesteautodeletegroupscloudapi/ contains a password protected archive + a lot of shellcodes

Recently, I have been investigating a malware loader which is ModiLoader. This loader is delivered through the Malspam services to lure end users to execute malicious code. blog.vincss.net/2020/09/re016-… #VinCSS #ModiLoader #MalwareAnalysis #Z2A



#opendir #trojan #modiloader hxxp://103.230.121.]50 - 1.exe - Trojan - Build.exe - Moldiloader - Crypted.Exe - Trojan - main.exe - Trojan - server.exe - Trojan
![RacWatchin8872's tweet image. #opendir #trojan #modiloader
hxxp://103.230.121.]50
- 1.exe - Trojan
- Build.exe - Moldiloader
- Crypted.Exe - Trojan
- main.exe - Trojan
- server.exe - Trojan](https://pbs.twimg.com/media/GPJ-O7QWkAAW1NW.png)
![RacWatchin8872's tweet image. #opendir #trojan #modiloader
hxxp://103.230.121.]50
- 1.exe - Trojan
- Build.exe - Moldiloader
- Crypted.Exe - Trojan
- main.exe - Trojan
- server.exe - Trojan](https://pbs.twimg.com/media/GPJ-O7KWoAA1Ngg.png)
![RacWatchin8872's tweet image. #opendir #trojan #modiloader
hxxp://103.230.121.]50
- 1.exe - Trojan
- Build.exe - Moldiloader
- Crypted.Exe - Trojan
- main.exe - Trojan
- server.exe - Trojan](https://pbs.twimg.com/media/GPJ-O7LXIAARSYz.jpg)
![RacWatchin8872's tweet image. #opendir #trojan #modiloader
hxxp://103.230.121.]50
- 1.exe - Trojan
- Build.exe - Moldiloader
- Crypted.Exe - Trojan
- main.exe - Trojan
- server.exe - Trojan](https://pbs.twimg.com/media/GPJ-O7WXAAAN35X.png)
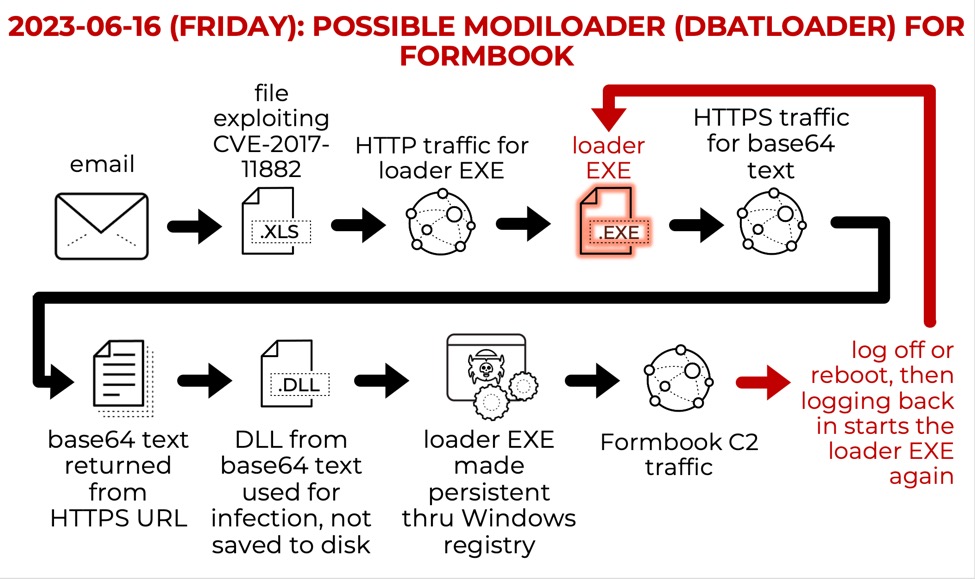
"RE : URGENT QOUTATION" spam email spread #modiloader > #FormBook Rar bazaar.abuse.ch/sample/d34adda… Exe @0xToxin bazaar.abuse.ch/sample/e26db42… >> bazaar.abuse.ch/sample/35e4a45… C2 www.futurelightiq.]com/b5sf/
![JAMESWT_WT's tweet image. "RE : URGENT QOUTATION" spam email
spread #modiloader > #FormBook
Rar
bazaar.abuse.ch/sample/d34adda…
Exe @0xToxin
bazaar.abuse.ch/sample/e26db42…
>>
bazaar.abuse.ch/sample/35e4a45…
C2
www.futurelightiq.]com/b5sf/](https://pbs.twimg.com/media/FbY3LcyWYAEqcvy.jpg)
![JAMESWT_WT's tweet image. "RE : URGENT QOUTATION" spam email
spread #modiloader > #FormBook
Rar
bazaar.abuse.ch/sample/d34adda…
Exe @0xToxin
bazaar.abuse.ch/sample/e26db42…
>>
bazaar.abuse.ch/sample/35e4a45…
C2
www.futurelightiq.]com/b5sf/](https://pbs.twimg.com/media/FbY3jHjXEAE5zf9.jpg)
![JAMESWT_WT's tweet image. "RE : URGENT QOUTATION" spam email
spread #modiloader > #FormBook
Rar
bazaar.abuse.ch/sample/d34adda…
Exe @0xToxin
bazaar.abuse.ch/sample/e26db42…
>>
bazaar.abuse.ch/sample/35e4a45…
C2
www.futurelightiq.]com/b5sf/](https://pbs.twimg.com/media/FbY4wnNXkAMFLhj.jpg)
🚨#Opendir #Malware 🚨 ⚠️#ModiLoader ☣️audiodg.exe➡️bbf710c83246092a538128620853d4fd 📡C2:hxxps://maan2u.com/doc/233_Qzzgbhhaaml ℹ️ C:\\Users\\Public\\pha.pif -WindowStyle hidden -Command Add-MpPreference -ExclusionExtension '.exe','bat','.pif'

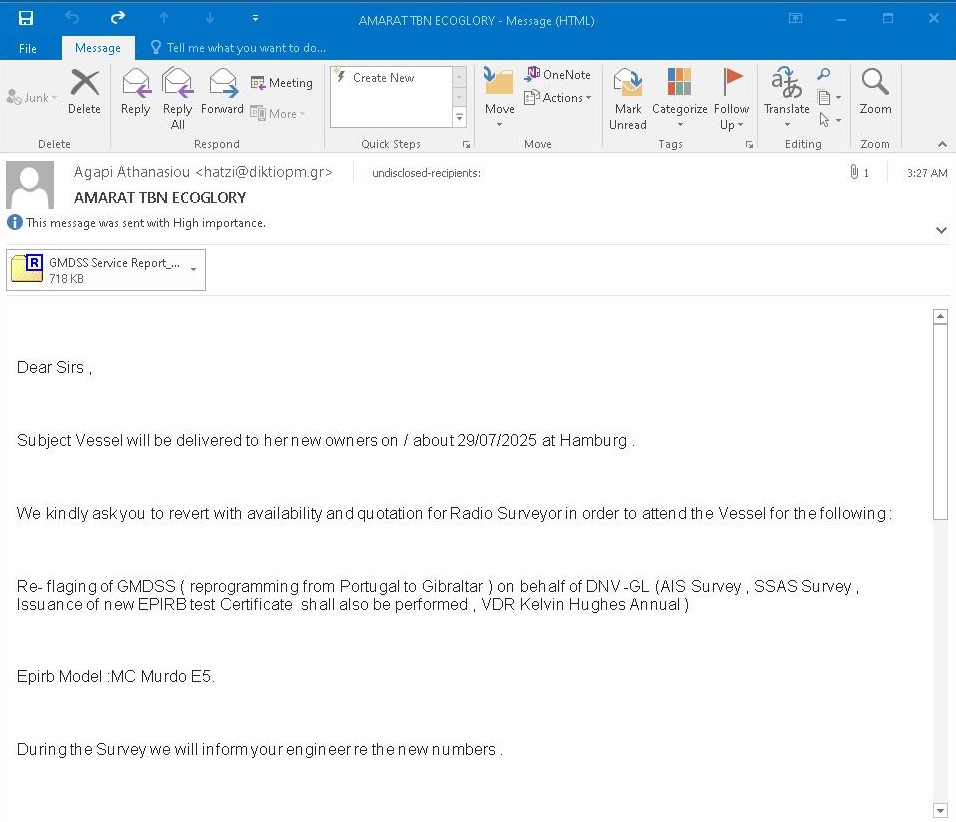
Global Maritime and Safety System users targeted with this one especially in Greece, Germany and UK: 'GMDSS Service Report_xlsx.rar' Looks like #ModiLoader @abuse_ch bazaar.abuse.ch/sample/4c27d80…
🇮🇹 Campagna #Remcos tramite #Modiloader 🎯 Italia ⚔️ TTP: ZIP > JS > PIF 🦠 #IoC👇 🔗 t.me/certagid/841 (Telegram)

32ba1ee78874a80a23a0d09427d52af6 05ef4ca659965c1d3faa58077b0f9943 #FormBook #ModiLoader #DBatLoader


[4/4] drop url: 176.65.144[.23/ff/kkinng.txt sha256: 954b611a8e8163b42691ec83d4ff0077ef6f80505a434d03e04c9ae19494ea13 bazaar.abuse.ch/browse/tag/176…
ModiLoader (DBatLoader) is a stealthy malware acting as a first-stage entry point for bigger cyberattacks on businesses. Read below to learn more! #cts #ctstechnologysolutions #modiloader #dbatloader #cybersecurity #soc #siem #pentesting #edr cts-tex.com/2025/05/20/mod…
cts-tex.com
9 Ways To Combat The Cybersecurity Threat: ModiLoader (DBatLoader) - CTS Technology Solutions...
Protect your business from ModiLoader (DBatLoader), a stealthy malware loader. Learn how it works, the risks, and essential prevention strategies
#ModiLoader #Malware #Attacking #Windows Users to #Steal #Login #Credentials. bit.ly/4j5fzSx #CyberAttack #Cybersecurity
cybersecuritynews.com
ModiLoader Malware Attacking Windows Users to Steal Login Credentials
ModiLoader (aka DBatLoader) targets Windows users via crafted phishing, posing a major threat to individuals.
Same #ModiLoader with another domain @abuse_ch bazaar.abuse.ch/sample/9d96854… Conn: mack-concord(.)hr @_operations6_
Looks like a low detected #ModiLoader 'TESLIMAT FISI.cmd' @abuse_ch bazaar.abuse.ch/sample/32816da… Drops this bazaar.abuse.ch/sample/676122e… Domain: link(.)storjshare(.)io

Looks like a low detected #ModiLoader 'TESLIMAT FISI.cmd' @abuse_ch bazaar.abuse.ch/sample/32816da… Drops this bazaar.abuse.ch/sample/676122e… Domain: link(.)storjshare(.)io

AhnLab warns of a new tactic using CAB header batch files to distribute ModiLoader malware via phishing emails, cleverly bypassing email security. Stay vigilant! 🔒🦠 #ModiLoader #Phishing #India link: ift.tt/U45Ki8c

🚨 AhnLab warns of ModiLoader (DBatLoader) malware exploiting CAB file headers to bypass email security. Delivered via purchase orders, this threat executes malicious commands. Stay vigilant! 🛡️ #ModiLoader #MalwareAlert #India #ThreatResearch link: ift.tt/x3KX1pr

Threat actor turns a Cabinet (CAB) file into the Loader. It dropped #ModiLoader (aka #DBatLoader) and ultimately deployed Agent Tesla. NEOMS_EOI_FORM.cmd (yep this is CAB file) SHA256: a631e4304cf932de1129cc660fd648125226cfee4059321b4e2048c38b2f9357 Rules & IOCs in🧵 #malware

🚨#Opendir #Malware 🚨 ⚠️#ModiLoader ☣️audiodg.exe➡️bbf710c83246092a538128620853d4fd 📡C2:hxxps://maan2u.com/doc/233_Qzzgbhhaaml ℹ️ C:\\Users\\Public\\pha.pif -WindowStyle hidden -Command Add-MpPreference -ExclusionExtension '.exe','bat','.pif'

The overall number of Rescoms samples delivered via AceCryptor nonetheless declined by 75%. It seems that the delivery method of Rescoms in the region has switched to #ModiLoader. We registered several notable ModiLoader phishing campaigns in May, see welivesecurity.com/en/eset-resear…. 4/6
"instead, in all nine campaigns, #attackers used #ModiLoader (aka #DBatLoader) as the preferred delivery tool of choice. The final payload to be delivered and launched on the compromised machines varied" welivesecurity.com/en/eset-resear…
🚨 New Video! Are you safe from the latest phishing attacks? Discover how ModiLoader is targeting Polish SMBs and how to protect your business. #CybersecurityNews #PhishingAlert #ModiLoader #PolishSMBs #Malware #BusinessProtection #CyberAttack #news youtu.be/QDtpD6Ypczs
youtube.com
YouTube
Phishing Epidemic: How ModiLoader is Targeting Polish SMBs – What You...
#ThreatProtection #ModiLoader #malware campaign targeting Small and Medium-Sized Business (#SMB) in #Poland, read more about Symantec's protection: broadcom.com/support/securi…
ISC Diary: @malware_traffic reviews a malspam-based #ModiLoader infection for #RemcosRAT i5c.us/d29896

ISC Diary: @malware_traffic saw #GuLoader or #ModiLoader/#DBatLoader style traffic for #RemcosRAT i5c.us/d29990

Dropping a #Yara rule for a new variant of #DBatLoader/#ModiLoader in the wild: github.com/d4rksystem/Yar… #100DaysOfYara

"Pre_Procurement Verification (Mog Energy)_Ref_TR0029388827772_10_27_2022" malspam mail -> sharepoint URL -> password protected 7z -> 3 #modiloader -> #AveMaria executables C2: pentester0.accesscam[.org Bazaar: bazaar.abuse.ch/browse/tag/pen… check comments for #modiloader opendir



#Modiloader / #Dbatloader The .z archive leads to exe, which uses lVali UserAgent to download encrypted file from Onedrive ( so MS doesn't take it down ). Post decryption its injected in legit MS process like sndvol to do the C2 comms on 42020 port. bazaar.abuse.ch/sample/4473b5d…


Recently, I have been investigating a malware loader which is ModiLoader. This loader is delivered through the Malspam services to lure end users to execute malicious code. blog.vincss.net/2020/09/re016-… #VinCSS #ModiLoader #MalwareAnalysis #Z2A




"RE : URGENT QOUTATION" spam email spread #modiloader > #FormBook Rar bazaar.abuse.ch/sample/d34adda… Exe @0xToxin bazaar.abuse.ch/sample/e26db42… >> bazaar.abuse.ch/sample/35e4a45… C2 www.futurelightiq.]com/b5sf/
![JAMESWT_WT's tweet image. "RE : URGENT QOUTATION" spam email
spread #modiloader > #FormBook
Rar
bazaar.abuse.ch/sample/d34adda…
Exe @0xToxin
bazaar.abuse.ch/sample/e26db42…
>>
bazaar.abuse.ch/sample/35e4a45…
C2
www.futurelightiq.]com/b5sf/](https://pbs.twimg.com/media/FbY3LcyWYAEqcvy.jpg)
![JAMESWT_WT's tweet image. "RE : URGENT QOUTATION" spam email
spread #modiloader > #FormBook
Rar
bazaar.abuse.ch/sample/d34adda…
Exe @0xToxin
bazaar.abuse.ch/sample/e26db42…
>>
bazaar.abuse.ch/sample/35e4a45…
C2
www.futurelightiq.]com/b5sf/](https://pbs.twimg.com/media/FbY3jHjXEAE5zf9.jpg)
![JAMESWT_WT's tweet image. "RE : URGENT QOUTATION" spam email
spread #modiloader > #FormBook
Rar
bazaar.abuse.ch/sample/d34adda…
Exe @0xToxin
bazaar.abuse.ch/sample/e26db42…
>>
bazaar.abuse.ch/sample/35e4a45…
C2
www.futurelightiq.]com/b5sf/](https://pbs.twimg.com/media/FbY4wnNXkAMFLhj.jpg)
#opendir #trojan #modiloader hxxp://103.230.121.]50 - 1.exe - Trojan - Build.exe - Moldiloader - Crypted.Exe - Trojan - main.exe - Trojan - server.exe - Trojan
![RacWatchin8872's tweet image. #opendir #trojan #modiloader
hxxp://103.230.121.]50
- 1.exe - Trojan
- Build.exe - Moldiloader
- Crypted.Exe - Trojan
- main.exe - Trojan
- server.exe - Trojan](https://pbs.twimg.com/media/GPJ-O7QWkAAW1NW.png)
![RacWatchin8872's tweet image. #opendir #trojan #modiloader
hxxp://103.230.121.]50
- 1.exe - Trojan
- Build.exe - Moldiloader
- Crypted.Exe - Trojan
- main.exe - Trojan
- server.exe - Trojan](https://pbs.twimg.com/media/GPJ-O7KWoAA1Ngg.png)
![RacWatchin8872's tweet image. #opendir #trojan #modiloader
hxxp://103.230.121.]50
- 1.exe - Trojan
- Build.exe - Moldiloader
- Crypted.Exe - Trojan
- main.exe - Trojan
- server.exe - Trojan](https://pbs.twimg.com/media/GPJ-O7LXIAARSYz.jpg)
![RacWatchin8872's tweet image. #opendir #trojan #modiloader
hxxp://103.230.121.]50
- 1.exe - Trojan
- Build.exe - Moldiloader
- Crypted.Exe - Trojan
- main.exe - Trojan
- server.exe - Trojan](https://pbs.twimg.com/media/GPJ-O7WXAAAN35X.png)
#modiloader #signed "Umbor LLC" bazaar.abuse.ch/sample/4aba670… drop #vidar and other malware as #ParallaxRAT bazaar.abuse.ch/sample/9a5e8b3… bazaar.abuse.ch/sample/b2f7094… bazaar.abuse.ch/sample/d9d1a29… h/t @malwrhunterteam cc @Arkbird_SOLG @sugimu_sec @lazyactivist192 @Jan0fficial @verovaleros @VK_Intel

#ModiLoader #imgur #loader #signed "Smart Line Logistics" Sample bazaar.abuse.ch/sample/30ea297… analyze.intezer.com/analyses/b47f3… Url urlhaus.abuse.ch/url/878713/ h/t @malwrhunterteam cc @Arkbird_SOLG @sugimu_sec @Jan0fficial @verovaleros @VK_Intel @guelfoweb @JRoosen @arieitan @lazyactivist192

32ba1ee78874a80a23a0d09427d52af6 05ef4ca659965c1d3faa58077b0f9943 #FormBook #ModiLoader #DBatLoader


[4/4] drop url: 176.65.144[.23/ff/kkinng.txt sha256: 954b611a8e8163b42691ec83d4ff0077ef6f80505a434d03e04c9ae19494ea13 bazaar.abuse.ch/browse/tag/176…
🇮🇹 Campagna #Remcos tramite #Modiloader 🎯 Italia ⚔️ TTP: ZIP > JS > PIF 🦠 #IoC👇 🔗 t.me/certagid/841 (Telegram)

🚨 #Malspam Alert: Ongoing ModiLoader malspam campaign detected. The initial threat is hidden in a 7Zip archive with a sneaky CAB file, delivering #ModiLoader and initiating #RemcosRAT infection.

Something went wrong.
Something went wrong.
United States Trends
- 1. Justin Fields 3,652 posts
- 2. Henderson 13.5K posts
- 3. Judge 161K posts
- 4. Cal Raleigh 4,877 posts
- 5. Patriots 116K posts
- 6. AD Mitchell 1,267 posts
- 7. Purdue 7,044 posts
- 8. #911onABC 13K posts
- 9. Diggs 5,121 posts
- 10. Braden Smith N/A
- 11. AL MVP 13.5K posts
- 12. Pats 10.6K posts
- 13. #Jets 3,347 posts
- 14. #TNFonPrime 2,113 posts
- 15. Drake Maye 9,730 posts
- 16. RIP Beef N/A
- 17. Michael Clemons N/A
- 18. ALL RISE 11.2K posts
- 19. Shohei Ohtani 41.6K posts
- 20. Mack Hollins 2,042 posts





![skocherhan's tweet image. taqareer[.]tech
#modiloader #Remcos](https://pbs.twimg.com/media/GsEW3TZWwAAMKyc.png)



![skocherhan's tweet image. lightstone[.]ae
#modiloader @userlolxxl @AbuseAE](https://pbs.twimg.com/media/GsESMWTW8AAZ5b5.png)
![skocherhan's tweet image. www[.]32win[.]art
#ModiLoader](https://pbs.twimg.com/media/Gsp4kWPWIAAUAZt.jpg)