#react2shell 搜索结果
WordPress people worrying about React UIs in plugins/themes etc the React vuln hits React Server Components & Next.js, not typical client side React. Most WP plugins only use React in wp-admin, so they aren’t exposed to that attack vector. #react2shell
Active exploitation of React2Shell flaw lands it on CISA KEV list, linked to Cloudflare outage. Apache Tika RCE, Oracle zero-day breach at Barts Health NHS, rising LockBit activity, and Agentic Wiper hitting Google Drive. #React2Shell #UK #DataBreach ift.tt/R8l73Q5
"Vercel paid 50k to one researcher so far" to my opinion its a trap to reward one and fix the rest of varitants of all the bypasses as Duplicate don't be foolish enough This reward is for someone for some reasons You know what I mean!!! #React2Shell
Multiple China-linked #hackers began exploiting the #React2Shell #vulnerability (CVE-2025-55182) affecting React and Next.js just hours after the max-severity issue was disclosed. #CyberSecurity #InfoSec ift.tt/LCoEzin

The recent #React2Shell vulnerability is a reminder that even mature ecosystems can expose serious risks when server-side rendering is involved. If you're using React Server Components or frameworks like Next.js, update immediately and review your server boundaries.
You've probably heard about the #React2Shell vulnerability. That's a security problem in the React's flight protocol. That's the protocol responsible for making React server components work. Here's a nice article by @rauchg about how it actually works - linkedin.com/pulse/react2sh……
🚨 CRITICAL: React2Shell (CVE-2025-55182) - CVSS 10.0 Pre-auth RCE affecting React 19.x & Next.js 15.x/16.x ⚠️ Active exploitation detected ⚠️ CISA KEV listed ⚠️ Default configs vulnerable techgines.com/post/is-your-r… #React2Shell #CyberSecurity

cve.org/CVERecord?id=C… 옛처럼 프론트단에서 ui 처리하고 서버단에서 처리하고 하는 시대는 지났어요. 요즘에 와서는 프론트가 사실상 미니 런타임 서버처럼 굴러가는게 기본값인데 예쁜 화면만 알면 안되는 시대에 들어온거 같아요. 프론트 분들 화이팅입니다.... #React2Shell
🚨 CVE-2025-55182, also known as React2Shell, is a critical unauthenticated remote code execution (RCE) vulnerability affecting React Server Components versions 19.0.0 through 19.2.0 and some Next.js versions. #CVE2025 #React2Shell
최악의 해킹 위협이라 할 수 있었던 #log4j RCE 취약점도 12월 6일~9일 사이... 이번 #React2Shell 해킹도 비슷한 시점... 크리스마스까지 모두 대응을 할 수 있을지...
React2Shell 해킹 위협 쇼단 검색 서비스 기준으로 한국 서비스 1만 2천개정도 노출 상태. AWS 클라우드 위에 동작하는게 50%정도네요. 회사 IP가 포함되어 있다면 관심 가지시길.. 주말 끝나면 헬게이트 열릴수 있으니.. #shodan #React2Shell shodan.io/search?query=V…


🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


just tested this in-memory backdoor via #React2Shell, this is crazy. github.com/Malayke/Next.j… I don't have time to set up a honeypot right now, but I'm pretty sure it would catch these kind of requests within minutes. :)

#React2Shell via FOFA. Chile: 4,503 results ( 1,649 unique IP )



🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


React2Shell is under live attack from China linked groups and unpatched servers are wide open. jenisystems.com/react2shell-ac… #React2Shell #CyberAlert #ServerSecurity
CVE-2025-55182 (React2Shell)、認証不要のRCEでCISAのKEV登録。React/Next.js利用環境で即実戦悪用、クラウドの約40%が影響との分析。パッチ適用とWAF導入が急務。#React2Shell #CVE202555182 #WebSecurity thehackernews.com/2025/12/critic…
React2Shell (CVE-2025-55182) の脆弱性で、77,000超の公開IPが影響。既に30超の組織が侵害され、PowerShell → Cobalt Strike によるバックドア設置が確認。React/Next.js 利用者は即時アップデートとWAF適用を。#React2Shell #RCE #WebSecurity bleepingcomputer.com/news/security/…
try this WAF bypass trick for rsc&&next.js CVE-2025-55182 All fields can use utf16le charset #React2Shell

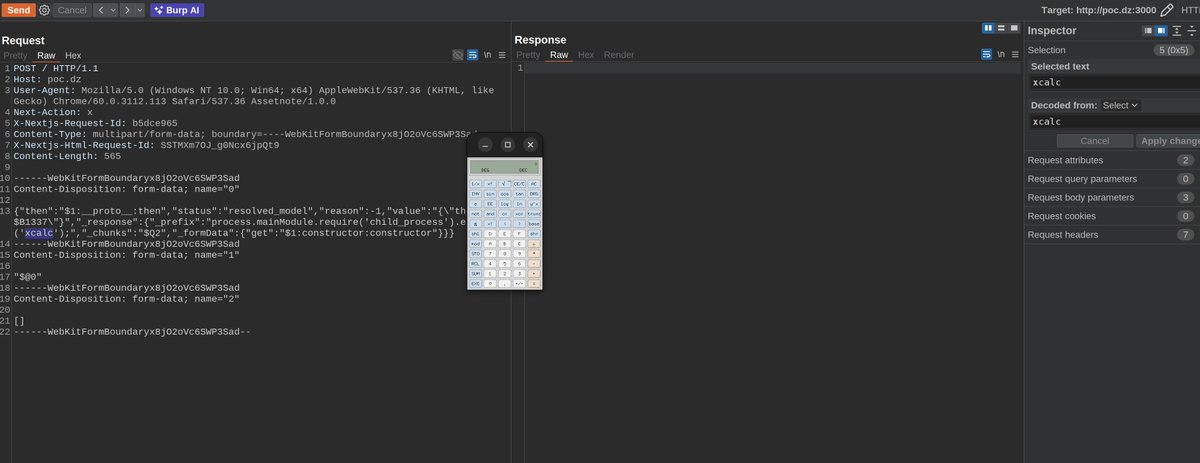
You can now scan for #react2shell in @Burp_Suite. To enable, install the Extensibility Helper bapp, go to the bambda tab and search for react2shell. Shout-out to @assetnote for sharing a reliable detection technique!

Yay, i got my first RCE! #BugBounty #InfoSec #React2Shell

This is the best scanner for the CVE-2025-55182 Try it out !🫡 github.com/zack0x01/CVE-2… #Hacking #CyberSecurity #ethicalhacking
from greynoise.io/blog/cve-2025-… child processes spawning.... 2nd wave... ecrime boyz with their coinminers and stagers #react2shell

Built a vulnerable React/Next.js lab for testing the #React2Shell bugs (CVE-2025-55182 & CVE-2025-66478). Everything ships in Docker containers.. use it 4fun github.com/jctommasi/reac…

Detecting #React2Shell (CVE-2025-55182), Safe probe for Flight parser error with Curl and without harmful execution. Indicators of vulnerability: ✅ Response Code = 500 ✅ Word "digest" appears in response body #React2Shell #CVE202555182 #BugBounty

just tested this in-memory backdoor via #React2Shell, this is crazy. github.com/Malayke/Next.j… I don't have time to set up a honeypot right now, but I'm pretty sure it would catch these kind of requests within minutes. :)

🚨 Censys on #React2Shell (CVE-2025-55182): We observe ~2.15M exposed web services running Next.js or other RSC-based frameworks—mostly in the U.S. and China. Not all are vulnerable, but active exploitation is underway. Patch now. 👉 Full advisory: hubs.ly/Q03X5QFV0

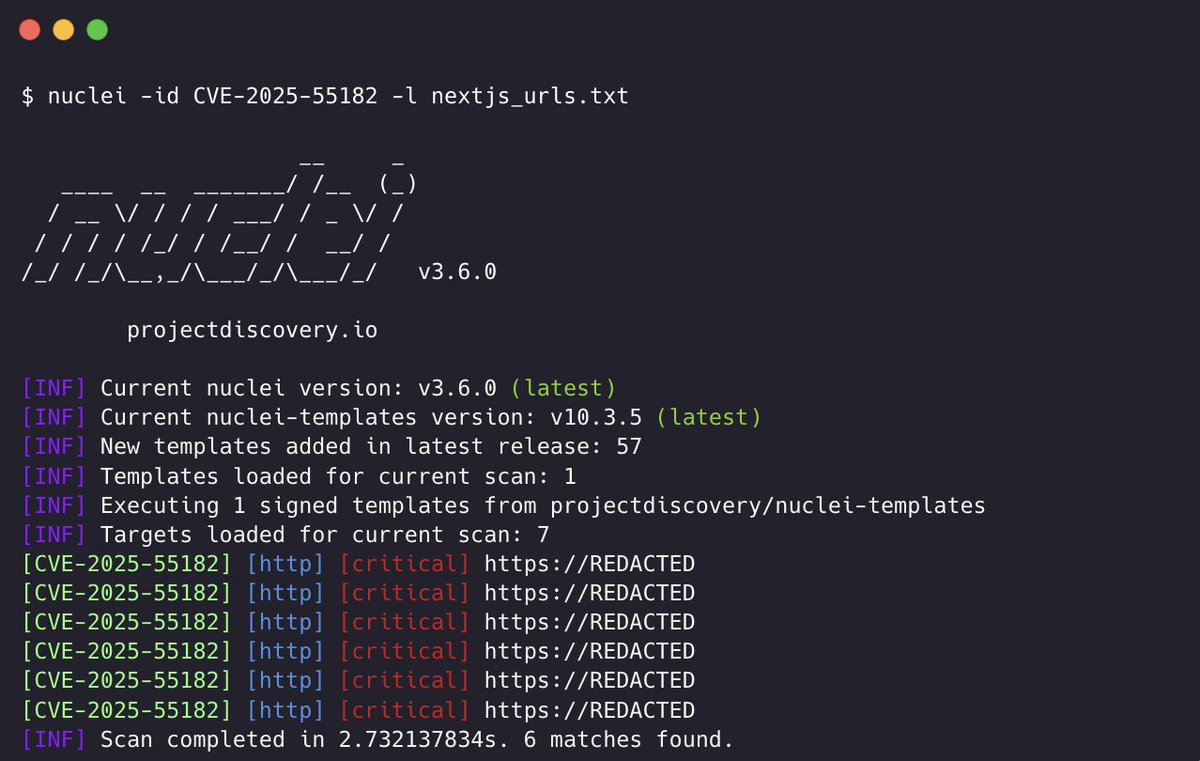
Scanning for CVE-2025-55182 using @pdnuclei 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell
#React2Shell via FOFA. Chile: 4,503 results ( 1,649 unique IP )



🚩 #React2Shell 🌐📡 → Censys (+270K assets): services.http.response.headers: (key: `Vary` and value.headers: `RSC, Next-Router-State-Tree`) → Shodan (+380K assets): "Vary: RSC, Next-Router-State-Tree"


Something went wrong.
Something went wrong.
United States Trends
- 1. #UFC323 124K posts
- 2. Indiana 105K posts
- 3. Merab 44.8K posts
- 4. Roach 29.5K posts
- 5. Petr Yan 26.2K posts
- 6. Ohio State 63.8K posts
- 7. Mendoza 41.4K posts
- 8. Pantoja 35K posts
- 9. Bama 86.8K posts
- 10. Joshua Van 10.7K posts
- 11. Heisman 19.3K posts
- 12. Curt Cignetti 11.5K posts
- 13. Miami 320K posts
- 14. Manny Diaz 2,929 posts
- 15. #iufb 8,661 posts
- 16. The ACC 37.5K posts
- 17. Tulane 18.2K posts
- 18. $HAVE 4,368 posts
- 19. TOP CALL 8,445 posts
- 20. Virginia 45.1K posts