#secretssecurity search results
Shift your #secretssecurity left by: 🔍 Adopting proactive #secretsscanning ❗ Automatically prioritizing high-risk exposed secrets ✅ Using environment variables Ready to learn more? Explore how Prisma Cloud can help keep your secrets safe and sound: bit.ly/3MGRFyJ
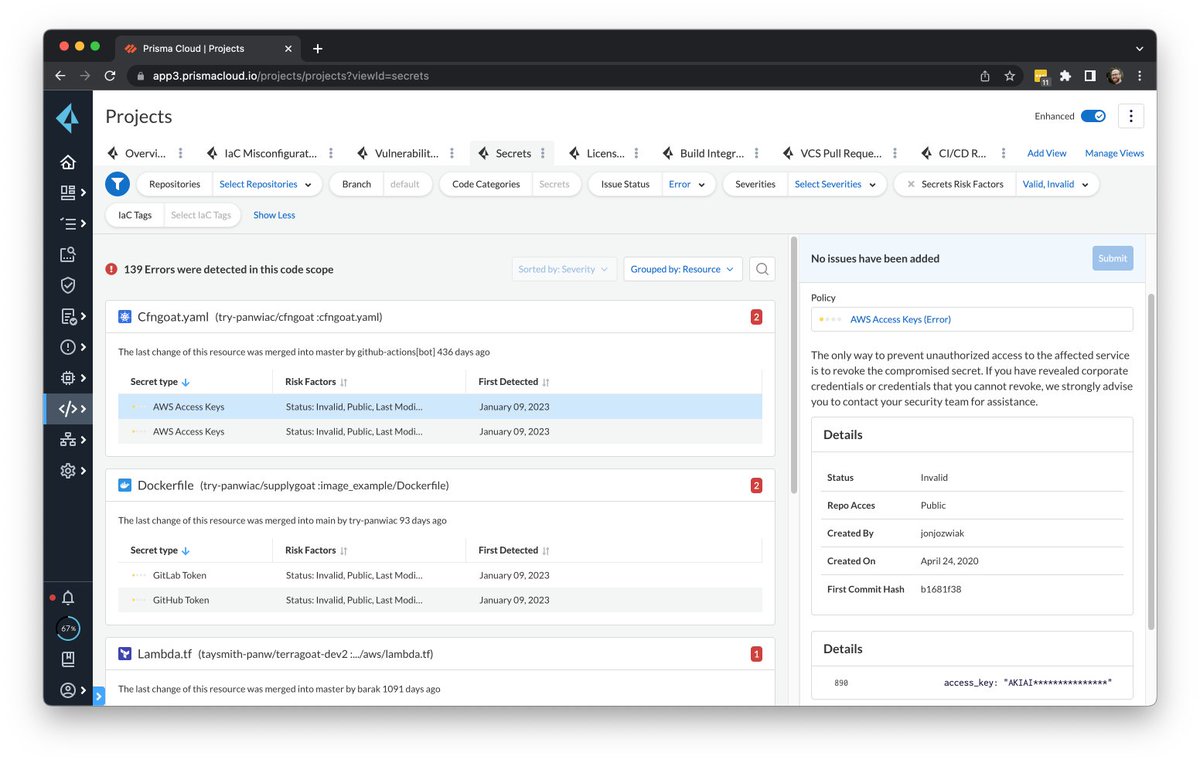
5/9 🔍 Continuous Visibility is Key! You can't secure what you can't see. #Monitor all assets for secrets to prevent breaches at the source. #SecretsSecurity #VisibilityMatters
Do you know how to keep your secrets secure wherever they are? 🤔 Learn how to adopt a full-stack, multidimensional approach to #secretssecurity with our 30-minute on-demand demo: bit.ly/3Ro2Fmh
The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian, on Tuesday, September 16th at 12 PM ET. . portal.h-isac.org/s/community-ev… #healthcare #nonHumanIdentity #secretsSecurity #threatIntelligence

It's all fun & games until you realize the average organization has 500+ secrets scattered across their cloud services... #SecretsSecurity #SecretsManagement

TODAY AT 12 PM ET! The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian. portal.h-isac.org/s/community-ev… #nonHumanIdentity #secretsSecurity #threatIntelligence

Will we see you at @ISMG_News Fraud, Security & Risk Management Summit in New York? Our all-star team of Itzik Alvas, Craig Clark, Steve Johnson, and Nirit Ickeson will be there to chat all things #SecretsManagement & #SecretsSecurity See you there!

🔍 At @defcon 32's AppSec Village, we tackled secrets security! 🕵️♂️ Discover insights on spotting and managing hidden credentials from our interactive sessions. Read the full recap from @McDwayne: s.gitguardian.com/066 #DEFCON32 #AppSec #SecretsSecurity
blog.gitguardian.com
DEF CON 32: What We Learned About Secrets Security at AppSec Village
At DEF CON 32's AppSec Village, we explored secrets security challenges, answered common questions, and shared how to detect and handle hidden credentials effectively.
Do you know how to keep your secrets secure wherever they are? Learn how to adopt a full-stack, multidimensional approach to #secretssecurity with Prisma Cloud's 30-minute on-demand #demo. sprou.tt/1tz3NsvoAXF
🚨 Hackers use Crackhash to turn leaked hashes into real passwords—fast. 💥 Common leaks: .env files, CI logs, Git commits Learn how to stop them: xygeni.io/blog/how-attac… #PasswordCracking #DevSecOps #SecretsSecurity #Crackhash #Xygeni #AppSec #CI_CD
xygeni.io
How Attackers Use Crackshash for Password Cracking (And How to Stop Them)
Learn how attackers use Crackhash for password cracking. Prevent breaches by understanding hash cracking techniques & securing your pipeline!
Developers use secrets to access services they need to build #cloudnativeapps at speed! 🏎️ But when secrets get hardcoded in #sourcecode, they can fall into the wrong hands. Join our deep dive to learn how Prisma Cloud's #SecretsSecurity module can help: bit.ly/3GAMfC5

7/20 🔑 Secrets Management: Never hardcode secrets in Dockerfiles or environment variables. Use Docker Secrets or external tools like HashiCorp Vault for secret management. #SecretsSecurity
Shift your #secretssecurity left by: - Adopting proactive #secretsscanning - Automatically prioritizing high-risk exposed secrets - Using environment variables Ready to learn more? Explore how #PrismaCloud can help keep your secrets safe and sound sprou.tt/1bG2uygmfJ4
paloaltonetworks.com
Shift Left Secrets Security: How to Prioritize Secrets Risks
Exposed credentials in your repositories can lead to unauthorized network access. Learn how to detect and remediate your exposed secrets with Checkov.
Heading to @IANS_Security in Chicago next week? Entro's team will be there to talk about, you guessed it, Non-human identities and secrets security See you there! #IANS #SecretsManagement #SecretsSecurity

Entro Secures $6 Million in Seed Funding #SaaS #SecretsSecurity and #Management solution #cybersecurity #seedround for its secrets security platform #funding #Entro thesaasnews.com/news/entro-sec…
Do you know how to keep your secrets secure wherever they are? Learn how to adopt a full-stack, multidimensional approach to #secretssecurity with Prisma Cloud's 30-minute on-demand demo sprou.tt/1tz3NsvoAXF
🎙️Podcast Highlight: Connection strings, API keys, vaults, access tokens. On average, there are about 30 secrets for every engineer in a large enterprise. Learn from Itzik Alvas (@entrosecurity ) why keeping these secrets safe is paramount.buff.ly/46mfwMR #SecretsSecurity
Shift your #secretssecurity left by: - Adopting proactive #secretsscanning - Automatically prioritizing high-risk exposed secrets - Using environment variables Ready to learn more? Explore how #PrismaCloud can help keep your secrets safe and sound sprou.tt/1bG2uygmfJ4
paloaltonetworks.com
Shift Left Secrets Security: How to Prioritize Secrets Risks
Exposed credentials in your repositories can lead to unauthorized network access. Learn how to detect and remediate your exposed secrets with Checkov.
In our new blog, we cover the #SecretsSecurity misconfigurations you MUST avoid. From what they are, to the OWASP Top 10, and preventing & remediating issues, it shines a light on steps companies can take to secure their digital keys. hubs.la/Q02lW9Lg0 #CyberSecurity

Do you know how to keep your secrets secure wherever they are? Learn how to adopt a full-stack, multidimensional approach to #secretssecurity with #Prisma Cloud's 30-minute on-demand demo. sprou.tt/1tz3NsvoAXF
TODAY AT 12 PM ET! The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian. portal.h-isac.org/s/community-ev… #nonHumanIdentity #secretsSecurity #threatIntelligence

The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian, on Tuesday, September 16th at 12 PM ET. . portal.h-isac.org/s/community-ev… #healthcare #nonHumanIdentity #secretsSecurity #threatIntelligence

The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian on Tuesday, September 16th at 12 PM ET. portal.h-isac.org/s/community-ev… #nonHumanIdentity #secretsSecurity #threatIntelligence

The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian on Tuesday, September 16th at 12 PM ET. portal.h-isac.org/s/community-ev… #nonHumanIdentity #secretsSecurity #threatIntelligence

The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian , on Tuesday, September 16th at 12 PM ET. portal.h-isac.org/s/community-ev… #secretsSecurity #threatIntelligence

🚨 Hackers use Crackhash to turn leaked hashes into real passwords—fast. 💥 Common leaks: .env files, CI logs, Git commits Learn how to stop them: xygeni.io/blog/how-attac… #PasswordCracking #DevSecOps #SecretsSecurity #Crackhash #Xygeni #AppSec #CI_CD
xygeni.io
How Attackers Use Crackshash for Password Cracking (And How to Stop Them)
Learn how attackers use Crackhash for password cracking. Prevent breaches by understanding hash cracking techniques & securing your pipeline!
5/9 🔍 Continuous Visibility is Key! You can't secure what you can't see. #Monitor all assets for secrets to prevent breaches at the source. #SecretsSecurity #VisibilityMatters
🔍 At @defcon 32's AppSec Village, we tackled secrets security! 🕵️♂️ Discover insights on spotting and managing hidden credentials from our interactive sessions. Read the full recap from @McDwayne: s.gitguardian.com/066 #DEFCON32 #AppSec #SecretsSecurity
blog.gitguardian.com
DEF CON 32: What We Learned About Secrets Security at AppSec Village
At DEF CON 32's AppSec Village, we explored secrets security challenges, answered common questions, and shared how to detect and handle hidden credentials effectively.
Machine identities are crucial for communication between systems and require a strategic security plan. CyberArk's research highlights the urgency of addressing this issue. Read more: rpb.li/3PR #SecretsSecurity #MachineIdentities #CyberSecurity
As automation grows, securing #nonhumanidentities like machines and applications is crucial. Discover how we're helping to safeguard your digital infrastructure in this insightful @Forbes article: hubs.la/Q02CZ8kK0 #secretssecurity #cybersecurity
Protecting non-human identities is key to business security. But achieving this remains a BIG challenge. This eBook covers: ✅Choosing a non-human identity management solution ✅Building a security framework ✅A #SecretsSecurity checklist Check it out: hubs.la/Q02sycF50

Heading to @IANS_Security in Chicago next week? Entro's team will be there to talk about, you guessed it, Non-human identities and secrets security See you there! #IANS #SecretsManagement #SecretsSecurity

To get a grip on #SecretsSecurity misconfigurations, it's key to know where vulnerabilities arise. This often has to do with how secrets are managed, how APIs play along, and how credentials are handled. Let's dive into some typical slip-ups 👇 hubs.la/Q02mcrsF0
In our new blog, we cover the #SecretsSecurity misconfigurations you MUST avoid. From what they are, to the OWASP Top 10, and preventing & remediating issues, it shines a light on steps companies can take to secure their digital keys. hubs.la/Q02lW9Lg0 #CyberSecurity

Don't risk upsetting Kurt Angle 🤼♂️ Dive into our #SecretsSecurity glossary and learn how to take control of your secrets now: hubs.la/Q02ljxQL0 #CyberSecurity
Did you know that, according to @Avast, “90% of advertised exploits on dark marketplaces sell for less than $10”? Vaults and scanners enough? Think again. Learn about the risks of dark web leakage and how to counter them: hubs.ly/Q02jtC6s0 #CyberSecurity #SecretsSecurity

2023 saw a lot of #CyberSecurity leaks... But which one's which caught the headlines? 🤔 Check out this video see some of 2023's major "on no's...", then get the full story behind each breach and the lessons that can be learned from them:hubs.la/Q02jhSMn0 #SecretsSecurity
It's all fun & games until you realize the average organization has 500+ secrets scattered across their cloud services... #SecretsSecurity #SecretsManagement

Will we see you at @ISMG_News Fraud, Security & Risk Management Summit in New York? Our all-star team of Itzik Alvas, Craig Clark, Steve Johnson, and Nirit Ickeson will be there to chat all things #SecretsManagement & #SecretsSecurity See you there!

Ever felt like this in your IT environment? That 'This is fine' moment when everything seems to be falling apart? We've all been there. See how to make this a thing of the past: hubs.la/Q02gTDst0 #CyberSecurity #SecretsSecurity #SecretsManagement

The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian, on Tuesday, September 16th at 12 PM ET. . portal.h-isac.org/s/community-ev… #healthcare #nonHumanIdentity #secretsSecurity #threatIntelligence

TODAY AT 12 PM ET! The State of Secrets Sprawl in Healthcare webinar by Health-ISAC Navigator, @GitGuardian. portal.h-isac.org/s/community-ev… #nonHumanIdentity #secretsSecurity #threatIntelligence

Shift your #secretssecurity left by: 🔍 Adopting proactive #secretsscanning ❗ Automatically prioritizing high-risk exposed secrets ✅ Using environment variables Ready to learn more? Explore how Prisma Cloud can help keep your secrets safe and sound: bit.ly/3MGRFyJ

It's all fun & games until you realize the average organization has 500+ secrets scattered across their cloud services... #SecretsSecurity #SecretsManagement

Will we see you at @ISMG_News Fraud, Security & Risk Management Summit in New York? Our all-star team of Itzik Alvas, Craig Clark, Steve Johnson, and Nirit Ickeson will be there to chat all things #SecretsManagement & #SecretsSecurity See you there!

Do you know how to keep your secrets secure wherever they are? 🤔 Learn how to adopt a full-stack, multidimensional approach to #secretssecurity with our 30-minute on-demand demo: bit.ly/3Ro2Fmh

Heading to @IANS_Security in Chicago next week? Entro's team will be there to talk about, you guessed it, Non-human identities and secrets security See you there! #IANS #SecretsManagement #SecretsSecurity

Developers use secrets to access services they need to build #cloudnativeapps at speed! 🏎️ But when secrets get hardcoded in #sourcecode, they can fall into the wrong hands. Join our deep dive to learn how Prisma Cloud's #SecretsSecurity module can help: bit.ly/3GAMfC5

Did you know that, according to @Avast, “90% of advertised exploits on dark marketplaces sell for less than $10”? Vaults and scanners enough? Think again. Learn about the risks of dark web leakage and how to counter them: hubs.ly/Q02jtC6s0 #CyberSecurity #SecretsSecurity

Ever felt like this in your IT environment? That 'This is fine' moment when everything seems to be falling apart? We've all been there. See how to make this a thing of the past: hubs.la/Q02gTDst0 #CyberSecurity #SecretsSecurity #SecretsManagement

In our new blog, we cover the #SecretsSecurity misconfigurations you MUST avoid. From what they are, to the OWASP Top 10, and preventing & remediating issues, it shines a light on steps companies can take to secure their digital keys. hubs.la/Q02lW9Lg0 #CyberSecurity

Cybersecurity ROI isn't just financial, it's about safeguarding digital assets, and regular reassessment is crucial for tight security. A key question to ask: Is your #SecretsManagement impacting HR ROI? Read more here: hubs.ly/Q02dtdHX0 #SecretsSecurity

Ready to become a Guardian of the Secrets?💂🏻♂️ In this whitepaper, you'll learn: ✅How secrets are created and the different types ✅Real life use cases of #SecretsSecurity platforms ✅How secret security platforms affect #CloudSecurity Download it here: hubs.la/Q0295bsm0

Use of stolen or compromised credentials remains the most common cause of a data breach - as they are 1 of the top 3 attack vectors, and the most destructive ⚔️ Learn how you can protect your organizations secrets: hubs.la/Q027x22m0 #SecretsSecurity #SecretsManagement

Protecting non-human identities is key to business security. But achieving this remains a BIG challenge. This eBook covers: ✅Choosing a non-human identity management solution ✅Building a security framework ✅A #SecretsSecurity checklist Check it out: hubs.la/Q02sycF50

Something went wrong.
Something went wrong.
United States Trends
- 1. #GivingTuesday 14.8K posts
- 2. The BIGGЕST 426K posts
- 3. #JUPITER 233K posts
- 4. #ALLOCATION 233K posts
- 5. #csm222 N/A
- 6. Lucario 13.8K posts
- 7. Costco 38K posts
- 8. #NXXT_NEWS N/A
- 9. Good Tuesday 38.9K posts
- 10. NextNRG Inc 1,194 posts
- 11. Susan Dell 2,339 posts
- 12. Michael and Susan 1,616 posts
- 13. Taco Tuesday 13.4K posts
- 14. Trump Accounts 7,522 posts
- 15. Hoss Cartwright N/A
- 16. King Von 1,086 posts
- 17. Dart 42.9K posts
- 18. Project M 22.2K posts
- 19. Kanata 29.4K posts
- 20. Mainz Biomed N.V. N/A














