#securityvulnerabilities نتائج البحث
Jai shri Ram 🙏 got Bounty $$$ Thanks lord Krishna for this ! #BugBounty #SecurityVulnerabilities #InfoSec #CyberSecurity #EthicalHacking #BugHunting #WhiteHat #server #unblock #WebSecurity #HackerCommunity #CyberAware
#DigitalTransformation Brings #SecurityVulnerabilities, Canon Research Says - MSSP Alert bit.ly/2MxHik8

Episode 3 of The @ActiveState Podcast is out! In this episode, Nicole Schwartz and Martin Drohmann dive into the challenges of managing #SecurityVulnerabilities while meeting development deadlines. Watch the full episode: bit.ly/3VVUHVD
#Jenkins released a new version that fixes multiple #SecurityVulnerabilities. Update now bitn.am/2JCHo3T

HOW TO TRAIN YOUR #Ghidra 🐉 a complex collection of #sourcecode with many third-party dependencies that are known to contain #securityvulnerabilities.👉 kas.pr/4kvx #cybersecuritytraining #ittraining #infosec #reverseengineering
#AI systems can be leveraged to insert hard-to-detect #SecurityVulnerabilities into computer chip designs, enabling even those with limited expertise to create sophisticated hardware attacks. @NYUTandon doi.org/g9576h techxplore.com/news/2025-10-a…
Understanding the human factor of #digitalsafety techradar.com/pro/understand… @TechRadarPro #securityvulnerabilities

#SecurityVulnerabilities – a zero-day exploit had been discovered in #log4j, a popular #Java logging library. All the library’s versions between 2.0 and 2.14.1 included are affected. Find out more on #InfoQ: bit.ly/31Ldtpz @olimpiupop #SoftwareArchitecture #DevOps

Insufficient logging and monitoring can slow down breach detection and worsen the impact of #SecurityVulnerabilities! ⚠️ Make sure you follow security logging standards, like #OWASP Logging Cheat Sheet guidelines, and enforce separate, restricted access controls. You can use…

MS-LLTD, MDNS, and ICMPv6 represent three commonly employed #networkprotocols, carrying potential #securityvulnerabilities that might not have caught your attention. Check out our #PenteraLabs research to learn more about the business risk they pose: okt.to/nm4UED
The Indian Computer Emergency Response Team (CERT-In) issued a critical advisory on August 2, warning of severe #securityvulnerabilities in various #Apple products. Read more: bit.ly/3yyGmFy

Severe weather events cause disruptions that could lead to #SecurityVulnerabilities. @barracuda's @GregArnette shares tips on protecting #data in the age of #ClimateChange, via @ITProToday @karendschwartz: ow.ly/8qtD30oLbYb #Cybersecurity #BCDR

Congrats to @Dooflin5 + Jesse Victors for having their research accepted to @thotcon 2023! Their selection demonstrates the high level of expertise our #SecurityEngineers have and places them among the best for identifying + solving even the most unique #securityvulnerabilities.

#Log4shell was one of the most critical #SecurityVulnerabilities of the current history. Read the #InfoQ Q&A with Arshan Dabirsiaghi and learn how #ContrastSecurity took an alternative approach to fix the issues: bit.ly/34Xbr6Y @olimpiupop #Java #DependencyManagement

Software companies typically provide #softwareupdates for 3 reasons: to add new features, fix known bugs, and #upgradesecurity. Always update to the latest version of your software to protect yourself from new or existing #securityvulnerabilities. 💻 #cybercrime #datasecurity

#SecurityVulnerabilities - A new vulnerability in the CRI-O container runtime used by many #Kubernetes installations allows a malicious user to gain root access to the host. The vulnerability was fixed by the CRI-O project: bit.ly/3uI3Bat @talonx #InfoQ #Containers

Qodana’s intuitive interface makes team onboarding easier! You can use the sunburst diagram to filter, identify, and address issues directly in your IDE. Try it now: jb.gg/vtt82l #CodeQuality #SecurityVulnerabilities #QodanaCloud
Thanks everybody who came to the Talented x White Hat Hackers -event on Wednesday! If you couldn't join us, you can watch Lea Viljanen & Antti Ollila's presentations here: bit.ly/2P4S6ba #securityvulnerabilities #hacking #BugBounty #whitehathackers #CTF #Cyberlympics

33 vulnerabilities found in embedded open source networking stacks @Forescout #Amnesia33 #SecurityVulnerabilities #IoT #TCPIP #Authentication #EmbeddedSoftware tinyurl.com/y3pncwg9

Jai shri Ram 🙏 got Bounty $$$ Thanks lord Krishna for this ! #BugBounty #SecurityVulnerabilities #InfoSec #CyberSecurity #EthicalHacking #BugHunting #WhiteHat #server #unblock #WebSecurity #HackerCommunity #CyberAware

#Jenkins released a new version that fixes multiple #SecurityVulnerabilities. Update now bitn.am/2JCHo3T

#DigitalTransformation Brings #SecurityVulnerabilities, Canon Research Says - MSSP Alert bit.ly/2MxHik8

Severe weather events cause disruptions that could lead to #SecurityVulnerabilities. @barracuda's @GregArnette shares tips on protecting #data in the age of #ClimateChange, via @ITProToday @karendschwartz: ow.ly/8qtD30oLbYb #Cybersecurity #BCDR

🌟 Meet Sahil Bugade, a passionate cybersecurity enthusiast from MIT ADT University! 🚀 Recently, he made history by entering NASA's Hall of Fame for uncovering a security vulnerability in their digital assets. 🛡️ #CybersecurityHero #NASA #SecurityVulnerabilities #MITADT

#SmartHomes #SecurityNews #SecurityVulnerabilities #CyberAttack #CyberSecurityUpdates #CyberSecurityEvent #CyberSecurityReport #CyberSecurity #Infosec #TCSP #TheCyberSecurityPlace

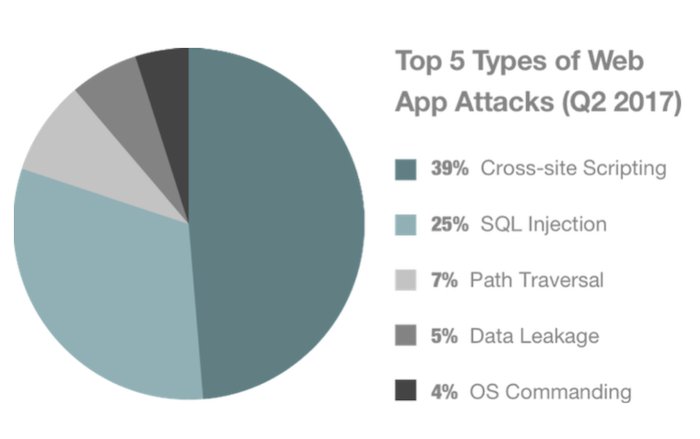
How to correct #SecurityVulnerabilities in #WebApplications? @RStyleLab shares some useful tips for businesses buff.ly/2HEELlc #WebDevelopment #WebApps #WebAppSecurity #CyberSecurity #CrossSiteScripting #SQLinjection #OpenSource via @clutch_co
33 vulnerabilities found in embedded open source networking stacks @Forescout #Amnesia33 #SecurityVulnerabilities #IoT #TCPIP #Authentication #EmbeddedSoftware tinyurl.com/y3pncwg9

Know how #MachineLearning is being used to handle #securityvulnerabilities by @farwa_sajjad96 via @datamadesimple bigdata-madesimple.com/machine-learni… #artificialintelligence #AI #ML #Cybersecurity #Security #technology #mistralsolutions

Common Python Security Problems - websystemer.no/common-python-… #programming #python #securityvulnerabilities

Understanding the human factor of #digitalsafety techradar.com/pro/understand… @TechRadarPro #securityvulnerabilities

Is your company ready to face #cyberattacks? Komodo Consulting helps you identify #securityvulnerabilities in your application before hackers do. bit.ly/3tJCixt #datasecurity #cyberattacks #quotes

“Found means fixed,” says @github's @_mph4 of the transformation unfolding with #AIAgents able to identify and fix software development #SecurityVulnerabilities in real-time. Watch Hanley, #OutshiftByCisco's @vijoy, and @VentureBeat's @LouisColumbus. 🎦 cs.co/6012m8CKm

Systemic Racism Is a Cybersecurity Threat on.cfr.org/3fzsdZw #CyberSecurity #SecurityVulnerabilities #AppsUnify

Insufficient logging and monitoring can slow down breach detection and worsen the impact of #SecurityVulnerabilities! ⚠️ Make sure you follow security logging standards, like #OWASP Logging Cheat Sheet guidelines, and enforce separate, restricted access controls. You can use…

If you are using this plugin, we strongly recommend that you update to the latest version immediately to protect your site. Stay safe and secure online! #WordPress #OnlineCourses #SecurityVulnerabilities #ProtectYourSite

#SecurityVulnerabilities – a zero-day exploit had been discovered in #log4j, a popular #Java logging library. All the library’s versions between 2.0 and 2.14.1 included are affected. Find out more on #InfoQ: bit.ly/31Ldtpz @olimpiupop #SoftwareArchitecture #DevOps

Something went wrong.
Something went wrong.
United States Trends
- 1. #GivingTuesday 20.6K posts
- 2. #twitchrecap 4,643 posts
- 3. Costco 45.4K posts
- 4. #AppleMusicReplay 6,980 posts
- 5. Jared Curtis 1,663 posts
- 6. Susan Dell 4,798 posts
- 7. #csm222 5,093 posts
- 8. #DragRace 1,966 posts
- 9. Lucario 21.5K posts
- 10. NextNRG Inc. 2,357 posts
- 11. RIP Larry N/A
- 12. King Von 1,452 posts
- 13. Michael and Susan 3,229 posts
- 14. Trump Accounts 11.2K posts
- 15. Carton 29K posts
- 16. BT and Sal N/A
- 17. WFAN N/A
- 18. Tiki 2,771 posts
- 19. Georgia to Vanderbilt 1,382 posts
- 20. Pentagon 77.6K posts