#spoofingattack resultados de búsqueda
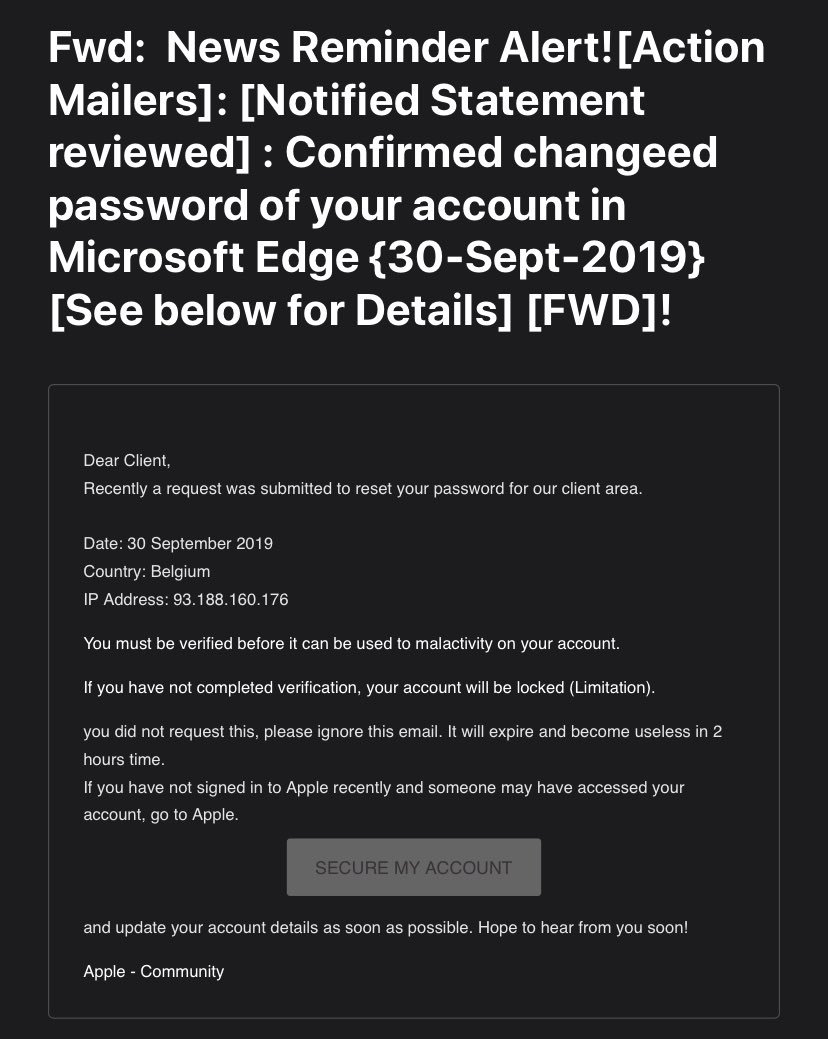
Apple always keeps my security safe or maybe it's not Apple? #SpoofingAttack #Malware #iOSsecurity #Apple
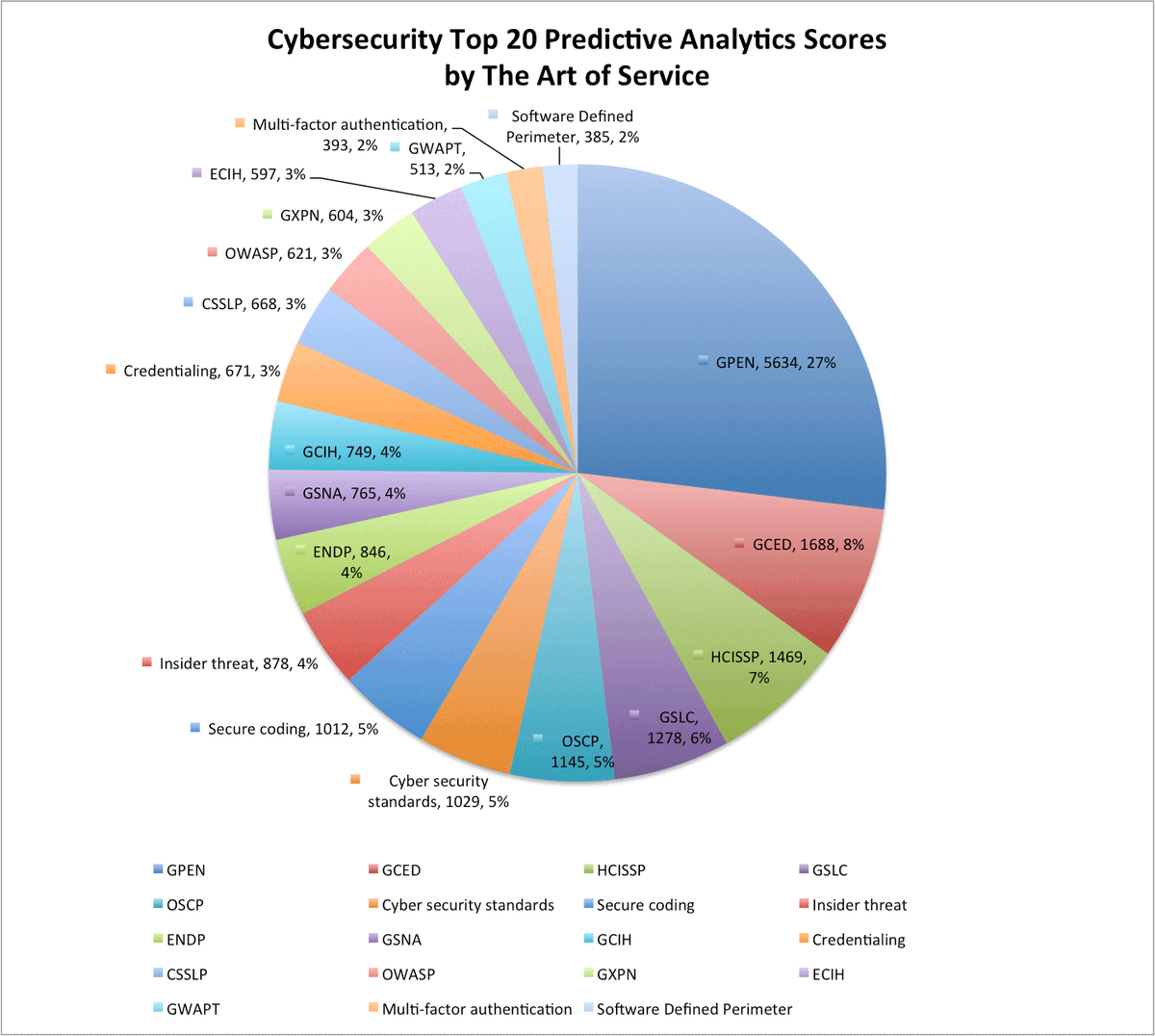
buff.ly/2bIBRrF #Cybersecurity #Spoofingattack #ISO55000 #blogpost #CallCenter #CIOs #predictplugs #CloudSt…
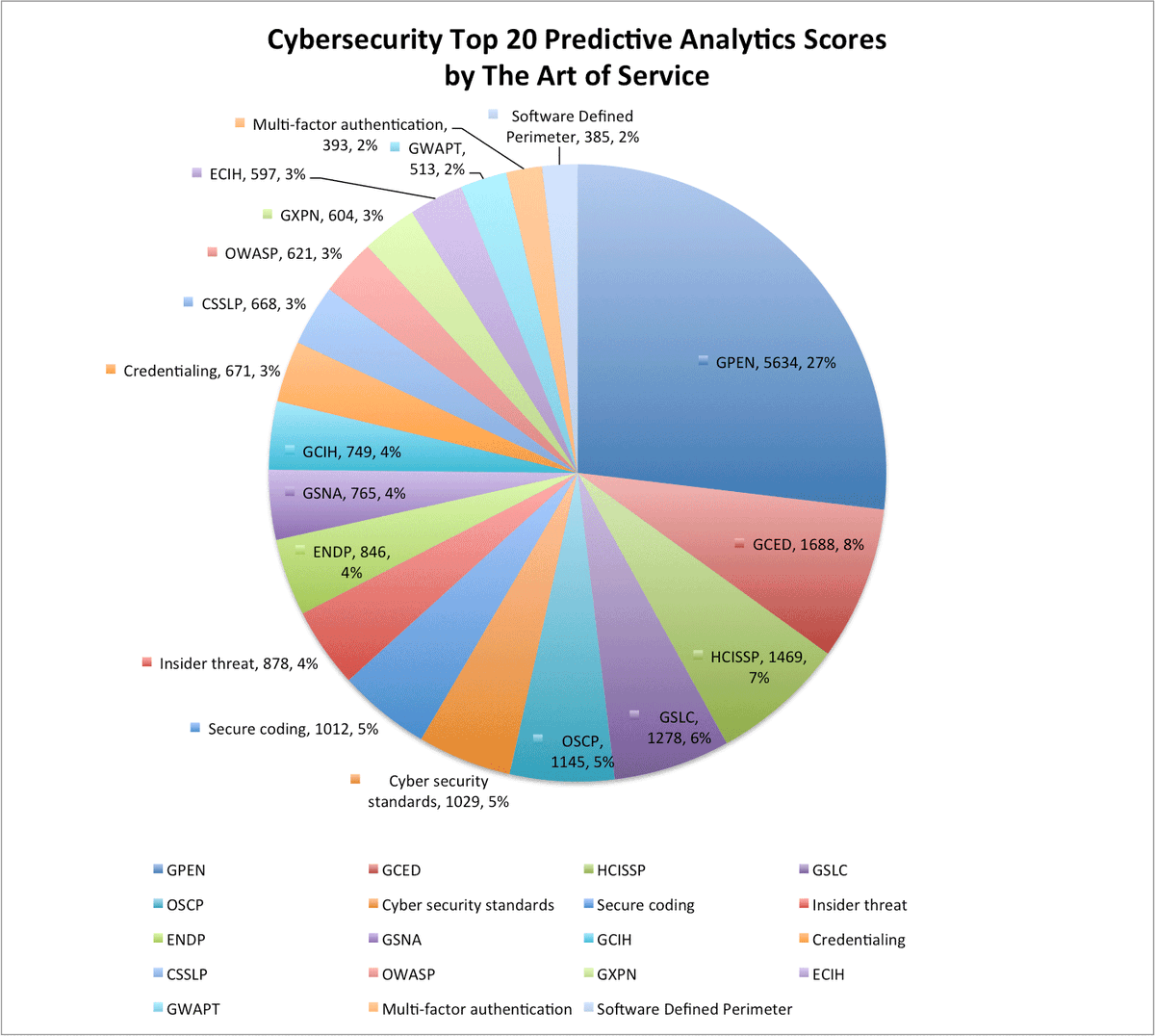
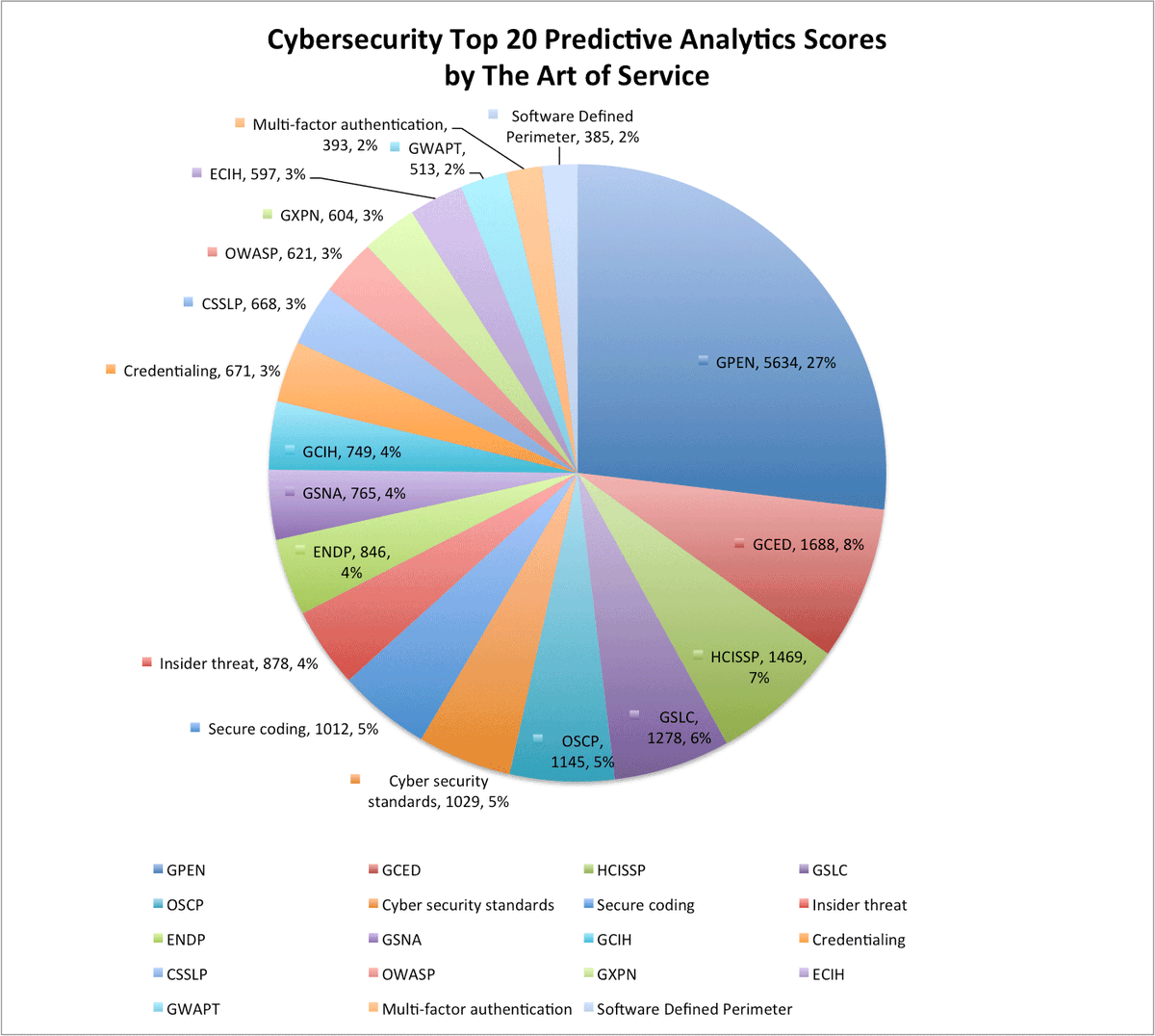
buff.ly/2bICd1k #Cybersecurity #Spoofingattack #ISO55000 #blogpost #CallCenter #CIOs #predictplugs #CloudSt…
Beware of spoofing attacks - cybercriminals disguise themselves as trusted sources to deceive you. #SpoofingAttack #CyberSecurity #StaySafeOnline

You have to admire the effort behind this #SpoofingAttack, typical signs of urgency and the promise of a return..😳 it seems like the Royal family have come along way, now using #BTC rather than the £ 🤣 #Hacking #Phishing

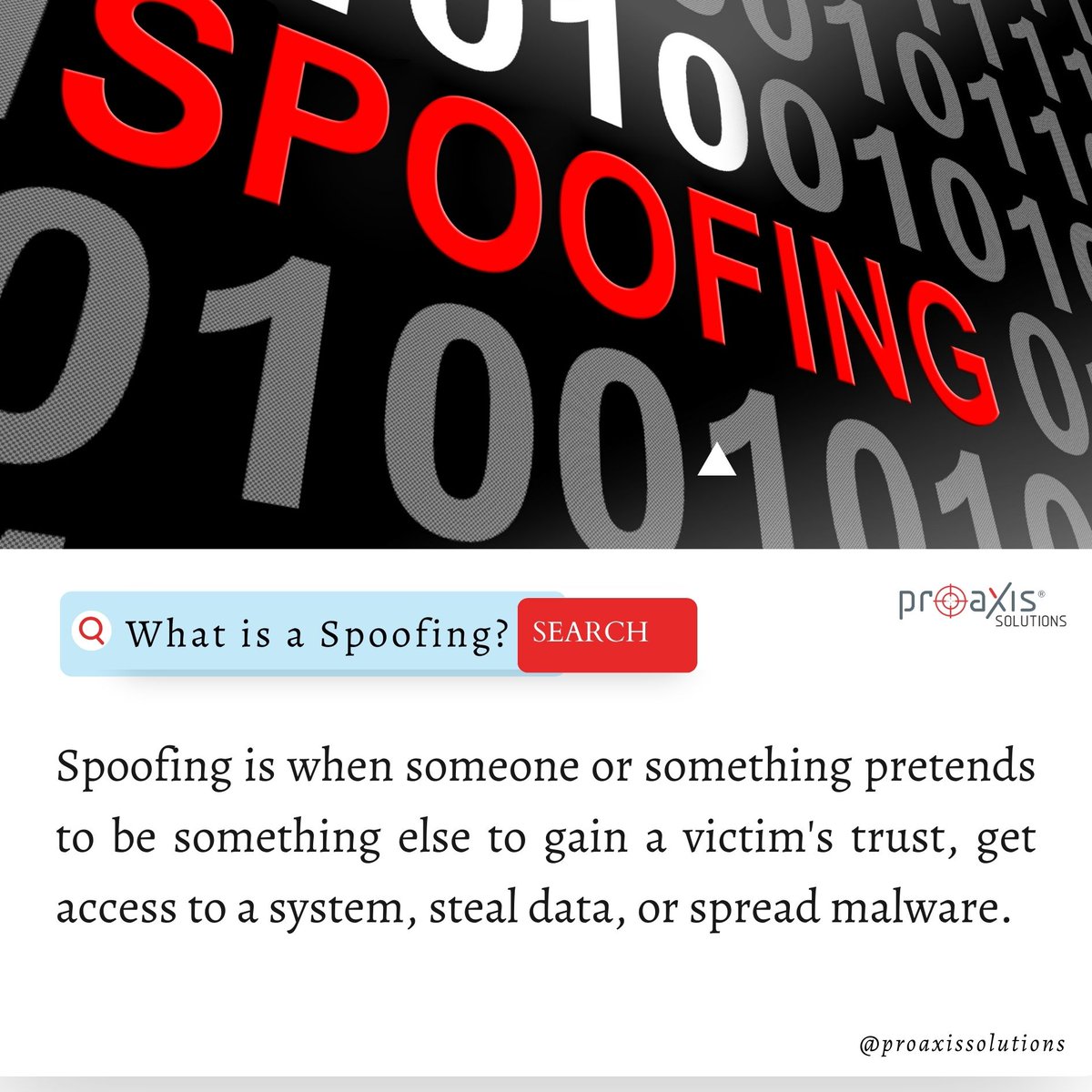
Have you heard of spoofing? Spoofing is when someone or something pretends to be something else to gain a victim's trust, get access to a system, steal data, or spread malware. #spoofing #spoofingattack #hackers #staysafeonline #cybersecuritymatters #proaxissolutions
If you think the size of your company is relevant to attackers who target domains for spoofing, you might be mistaken. Attackers target domains that don't have adequate security measures like #DMARC in place. #spoofingattack #smallbusiness #emailsecurity #dmarc #powerdmarc

Domain spoofing can be detrimental to your organization's reputation and can drastically impact your email deliverability rates. Know how safe you are against them, run the test today: powerdmarc.com #domainspoofing #spoofingattack #domainsecurity #dmarc #powerdmarc
Today we discuss about "Spoofing" Spoofing is an illegal strategy where cybercriminals act as trusted sources to gain access to users’ confidential info for monetary purposes or to spread malware. #SpoofingAttack #IdentityTheft #IPSpoofing #ttb #EmailSpoofing #Phishing #ttb

Russia denies role in Israeli airport GPS jamming - BBC News #Spoofingattack #Instrumentlandingsystem skyrl.co/x7PACE

🕵️♂️ Ever heard of ARP Spoofing or IP Spoofing? 🤔 These attacks can compromise your data! Learn the latest techniques and how to defend against them in our new video! 🔍💡 #InfoSec #SpoofingAttack #TechTutorial #CyberAwareness #Hacker101 #KaliLinux ⬇️ youtube.com/watch?v=r_Hcca…

LIVE Cybersecurity Training Moment! Watch as @amiablesteve from Elite Comp Tech demonstrates Man-in-the-Middle attack using spoofing with a Student 📷Stay aware. Stay protected. #CyberSecurity #MITM #SpoofingAttack #EliteCompTech #CyberSecurityTraining #HackerTactics
Halloween And Spoofing Scams: How Real-Time Verification Helps bit.ly/39ousyD #SpoofingAttack #DigitalScam #SpoofingScams #IdentityTheft #RealTimeVerification #DigitalKYC #IdentityVerification #BiometricAuthentication

Our latest work examines the security implications of so-called privacy preserving #synthetic data. We show how to balance the inherent trade-offs for voice signals using a new tandem framework,🧵 #voicecloning #spoofingattack #adversarialexample

Delhi Airport ATC Glitch : फ्लाइट्स के GPS सिस्टम से छेड़छाड़ की साजिश किसने की? #DelhiAirport #CyberAttack #SpoofingAttack #GPSSpoofing @journoanjalii @PratyushSinghKr
📷 Warning: Spoofing Attacks on ADFS Login Pages 📷 Hackers are targeting Microsoft ADFS login pages with sophisticated spoofing attacks. Protect your business with robust security measures! 📷 Learn more: bbg-mn.com/2476/16/07 #SpoofingAttack #ADFS #Cybersecurity
Having a well-developed security posture is essential to any business. Organizations should not assume the security of their customers' data and instead must take proactive steps to ensure it throughout the development process. #cybersecurity #cyraacs #spoofingattack

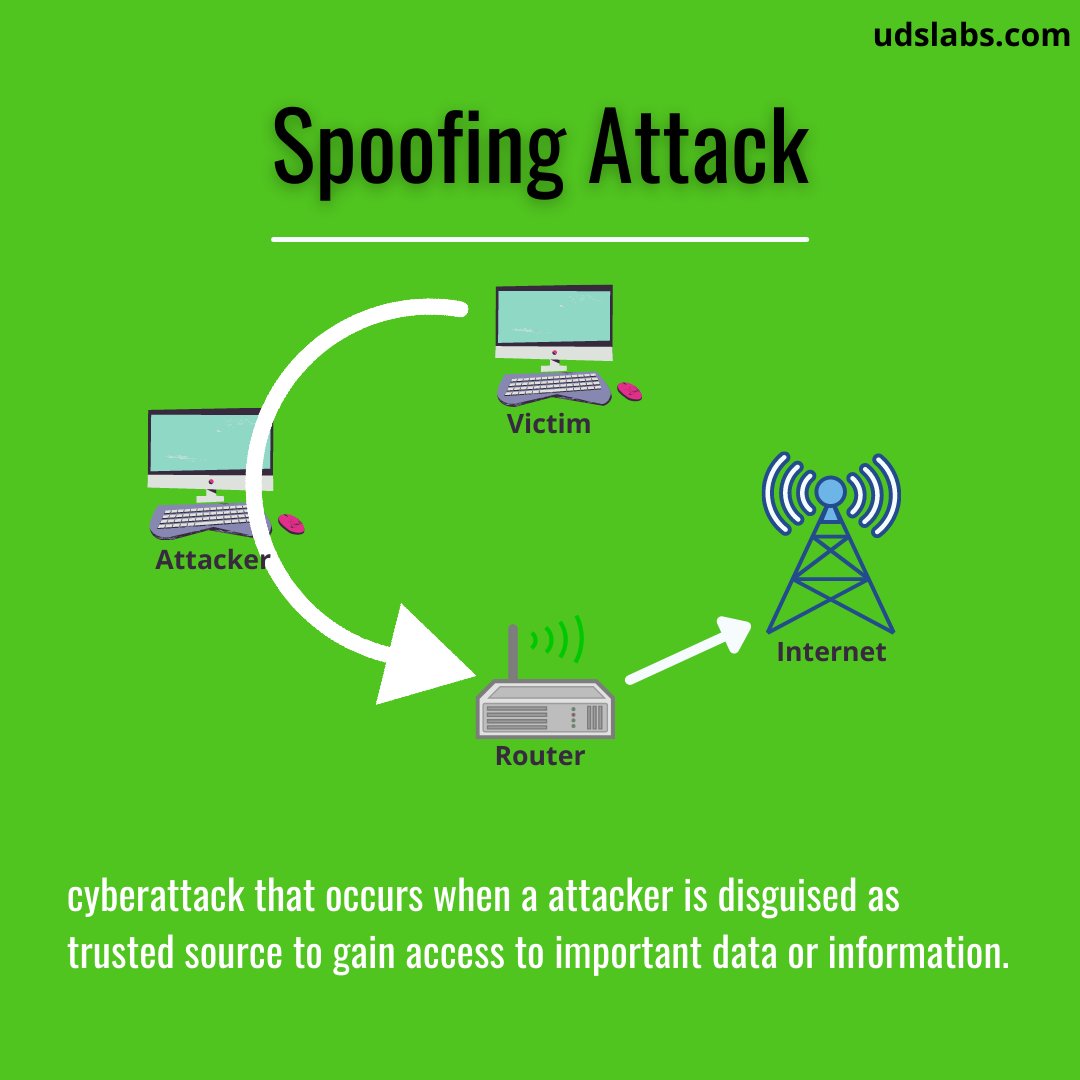
Cyber-Attack that occurs when attacker is disguised as a trusted source to gain access to important data or information. Spoofing can be through websites, emails, phone calls, texts, IP addresses and servers. #spoofingAttack #CyberAttack #cybersecurityawareness #Cybersecurity
Delhi Airport ATC Glitch : फ्लाइट्स के GPS सिस्टम से छेड़छाड़ की साजिश किसने की? #DelhiAirport #CyberAttack #SpoofingAttack #GPSSpoofing @journoanjalii @PratyushSinghKr
LIVE Cybersecurity Training Moment! Watch as @amiablesteve from Elite Comp Tech demonstrates Man-in-the-Middle attack using spoofing with a Student 📷Stay aware. Stay protected. #CyberSecurity #MITM #SpoofingAttack #EliteCompTech #CyberSecurityTraining #HackerTactics
Understanding spoofing attacks and enforcing strong security protocols are essential to avoiding them and protecting your data and business. #cybersecurity #spoofingattack #itmanagedservices nuvodia.com/spoofing-attac…
📷 Warning: Spoofing Attacks on ADFS Login Pages 📷 Hackers are targeting Microsoft ADFS login pages with sophisticated spoofing attacks. Protect your business with robust security measures! 📷 Learn more: bbg-mn.com/2476/16/07 #SpoofingAttack #ADFS #Cybersecurity
🕵️♂️ Ever heard of ARP Spoofing or IP Spoofing? 🤔 These attacks can compromise your data! Learn the latest techniques and how to defend against them in our new video! 🔍💡 #InfoSec #SpoofingAttack #TechTutorial #CyberAwareness #Hacker101 #KaliLinux ⬇️ youtube.com/watch?v=r_Hcca…

Beware of spoofing attacks - cybercriminals disguise themselves as trusted sources to deceive you. #SpoofingAttack #CyberSecurity #StaySafeOnline

Today we discuss about "Spoofing" Spoofing is an illegal strategy where cybercriminals act as trusted sources to gain access to users’ confidential info for monetary purposes or to spread malware. #SpoofingAttack #IdentityTheft #IPSpoofing #ttb #EmailSpoofing #Phishing #ttb

What's security terminology? | What's a Spoofing Attack? | Types of Traffic Listen now: podcasters.spotify.com/pod/show/infos… #security #cybersecurity #spoofingattack #learntorise #infosectrain #cyberattacks

What's security terminology? | What's a Spoofing Attack? | Types of Traffic Listen Now - podcasters.spotify.com/pod/show/infos… #securityterminology #spoofingattack #infosectrain #learntorise
What's security terminology? | What's a Spoofing Attack? | Types of Traffic listen now - podcasters.spotify.com/pod/show/infos… #securityterminology #spoofingattack #traffic #learntorise
Have you heard of spoofing? Spoofing is when someone or something pretends to be something else to gain a victim's trust, get access to a system, steal data, or spread malware. #spoofing #spoofingattack #hackers #staysafeonline #cybersecuritymatters #proaxissolutions

…this crypto ads used a key successful name in @Twitter to get my attention and details… since then I am receiving a volume of spoofy calls…that spooky ! and annoying.. #soliloquy #SpoofingAttack
DNS spoofing is an attack tactic commonly used to defraud companies. DNS has never been secure in and of itself since it was designed in the 1980s encouraging bad actors to exploit the problem over time. Read more: powerdmarc.com/what-is-dns-sp… #dnsspoofing #spoofingattack #powerdmarc
#SPOOFINGATTACK. Spoofing is a type of market manipulation attack. Market manipulation tricks are seen in almost all financial markets and of course the #crypto market. But what exactly is spoofing? In the spoofing attack, a fake buy or sell order is submitted in order


buff.ly/2bIBRrF #Cybersecurity #Spoofingattack #ISO55000 #blogpost #CallCenter #CIOs #predictplugs #CloudSt…

Apple always keeps my security safe or maybe it's not Apple? #SpoofingAttack #Malware #iOSsecurity #Apple

Have you heard of spoofing? Spoofing is when someone or something pretends to be something else to gain a victim's trust, get access to a system, steal data, or spread malware. #spoofing #spoofingattack #hackers #staysafeonline #cybersecuritymatters #proaxissolutions

buff.ly/2bICd1k #Cybersecurity #Spoofingattack #ISO55000 #blogpost #CallCenter #CIOs #predictplugs #CloudSt…

Beware of spoofing attacks - cybercriminals disguise themselves as trusted sources to deceive you. #SpoofingAttack #CyberSecurity #StaySafeOnline

Halloween And Spoofing Scams: How Real-Time Verification Helps bit.ly/39ousyD #SpoofingAttack #DigitalScam #SpoofingScams #IdentityTheft #RealTimeVerification #DigitalKYC #IdentityVerification #BiometricAuthentication

If you think the size of your company is relevant to attackers who target domains for spoofing, you might be mistaken. Attackers target domains that don't have adequate security measures like #DMARC in place. #spoofingattack #smallbusiness #emailsecurity #dmarc #powerdmarc

You have to admire the effort behind this #SpoofingAttack, typical signs of urgency and the promise of a return..😳 it seems like the Royal family have come along way, now using #BTC rather than the £ 🤣 #Hacking #Phishing

Domain spoofing can be detrimental to your organization's reputation and can drastically impact your email deliverability rates. Know how safe you are against them, run the test today: powerdmarc.com #domainspoofing #spoofingattack #domainsecurity #dmarc #powerdmarc

🕵️♂️ Ever heard of ARP Spoofing or IP Spoofing? 🤔 These attacks can compromise your data! Learn the latest techniques and how to defend against them in our new video! 🔍💡 #InfoSec #SpoofingAttack #TechTutorial #CyberAwareness #Hacker101 #KaliLinux ⬇️ youtube.com/watch?v=r_Hcca…

Today we discuss about "Spoofing" Spoofing is an illegal strategy where cybercriminals act as trusted sources to gain access to users’ confidential info for monetary purposes or to spread malware. #SpoofingAttack #IdentityTheft #IPSpoofing #ttb #EmailSpoofing #Phishing #ttb

Russia denies role in Israeli airport GPS jamming - BBC News #Spoofingattack #Instrumentlandingsystem skyrl.co/x7PACE

buff.ly/2bIBNrI #Cybersecurity #Spoofingattack #ISO55000 #blogpost #CallCenter #CIOs #predictplugs #CloudSt…
Our latest work examines the security implications of so-called privacy preserving #synthetic data. We show how to balance the inherent trade-offs for voice signals using a new tandem framework,🧵 #voicecloning #spoofingattack #adversarialexample

buff.ly/2bICmSJ #Cybersecurity #Spoofingattack #ISO55000 #blogpost #CallCenter #CIOs #predictplugs #CloudSt…
Cyber-Attack that occurs when attacker is disguised as a trusted source to gain access to important data or information. Spoofing can be through websites, emails, phone calls, texts, IP addresses and servers. #spoofingAttack #CyberAttack #cybersecurityawareness #Cybersecurity

buff.ly/2bICUHV #Cybersecurity #Spoofingattack #ISO55000 #blogpost #CallCenter #CIOs #predictplugs #CloudSt…
What's security terminology? | What's a Spoofing Attack? | Types of Traffic Listen now: podcasters.spotify.com/pod/show/infos… #security #cybersecurity #spoofingattack #learntorise #infosectrain #cyberattacks

Something went wrong.
Something went wrong.
United States Trends
- 1. Kanata 13.1K posts
- 2. Lakers 49.5K posts
- 3. Dillon Brooks 7,162 posts
- 4. Bron 25K posts
- 5. Giants 85.9K posts
- 6. #WWERaw 72K posts
- 7. Patriots 132K posts
- 8. Dart 36.4K posts
- 9. Suns 19.3K posts
- 10. #AvatarFireAndAsh 3,119 posts
- 11. Collin Gillespie 2,078 posts
- 12. Drake Maye 24.5K posts
- 13. Hololive 13.7K posts
- 14. STEAK 10.5K posts
- 15. Ryan Nembhard 4,337 posts
- 16. James Cameron 4,792 posts
- 17. Diaz 33.8K posts
- 18. Devin Williams 7,781 posts
- 19. Pats 16.3K posts
- 20. Devin Booker 2,661 posts