#awssecuritytips search results
I just published Keeping Your AWS Cloud Safe: How to Defend Your Cloud Project from Cyber Threats medium.com/trendfingers/k… #AWSSecurityTips #SecureAWS #CloudSecurityBestPractices #AWSBestPractices #HackingPrevention
medium.com
Keeping Your AWS Cloud Safe: How to Defend Your Cloud Project from Cyber Threats
In today’s digital world, cloud computing has become essential to business operations. Amazon Web Services (AWS) is a widely used cloud…
73% of orgs don't have a privileged security account. If you wouldn't let a 5th grader grade his own test paper, why would you let the account that writes the code also be in charge of its integrity? Source: bit.ly/2NPSRlK #awssecuritytips #cloudsecurity #cloud #aws
73% of orgs don't have a privileged security account. If you wouldn't let your students grade their individual test papers, why would you give your developers full access to the audit logs? Source: bit.ly/2NPSRlK #awssecuritytips #cloudsecurity #cloud #aws
101 AWS Security Tips & Quotes, Part 3: Best Practices for Using Security Groups in AWS more tips subscribe: bit.ly/2lm0vZ4 aws training contact: +91 98850 22027 #awssecuritytips #amazonwebservices #cloudcomputing securityboulevard.com/2018/07/101-aw…
New post by @coosuke AWS Security Fundamentals with AWS BuilderCards Security Expansion Pack dev.to/aws-builders/a… #aws #awsbuildercards #security
From compliance to containers—secure your AWS stack with: ✅ NIST, PCI DSS, GDPR ✅ Serverless & IoT protection ✅ Multi-cloud & hybrid strategies Built for cloud pros & security enthusiasts. 🛡️ #CloudSecurity #AWS #DevSecOps #CyberResilience 🔗 ow.ly/VQ7H50X6qT6

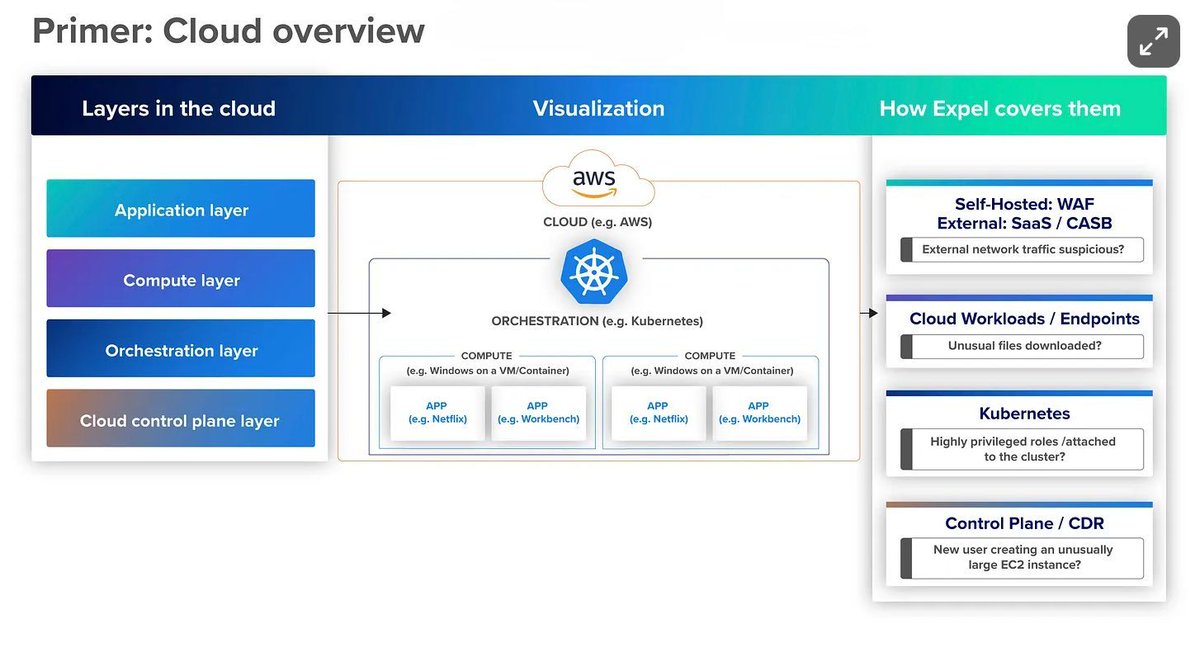
🧭 Building a Cloud Security Roadmap: Tools by Layer and When You Need Them (Part 1) By Ethan Chen If you’re overwhelmed by the sprawling cloud security tool landscape, Ethan Chen’s guide brings clarity with structure. This article breaks down cloud security tooling by control…
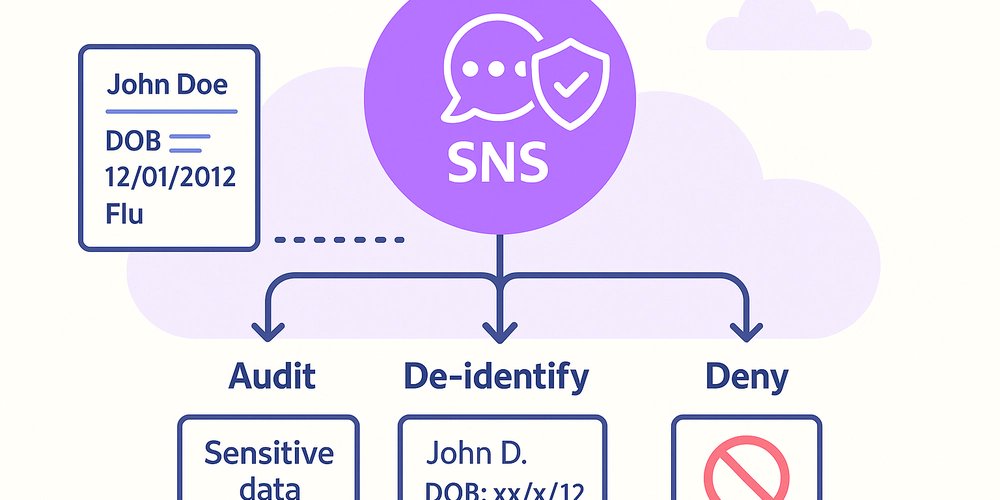
New post by vikasbanage. How to Use Amazon SNS Data Protection Policies to Prevent Sensitive Data Leakage dev.to/aws-builders/h… #aws #data #privacy #security
As cloud security threats continue to evolve, it's essential for cybersecurity professionals and threat hunters to stay vigilant. From misconfigured #IAM roles to lateral movement via Azure Active Directory (#AAD) attacks, the risks are real. Let's dive into the top cloud…
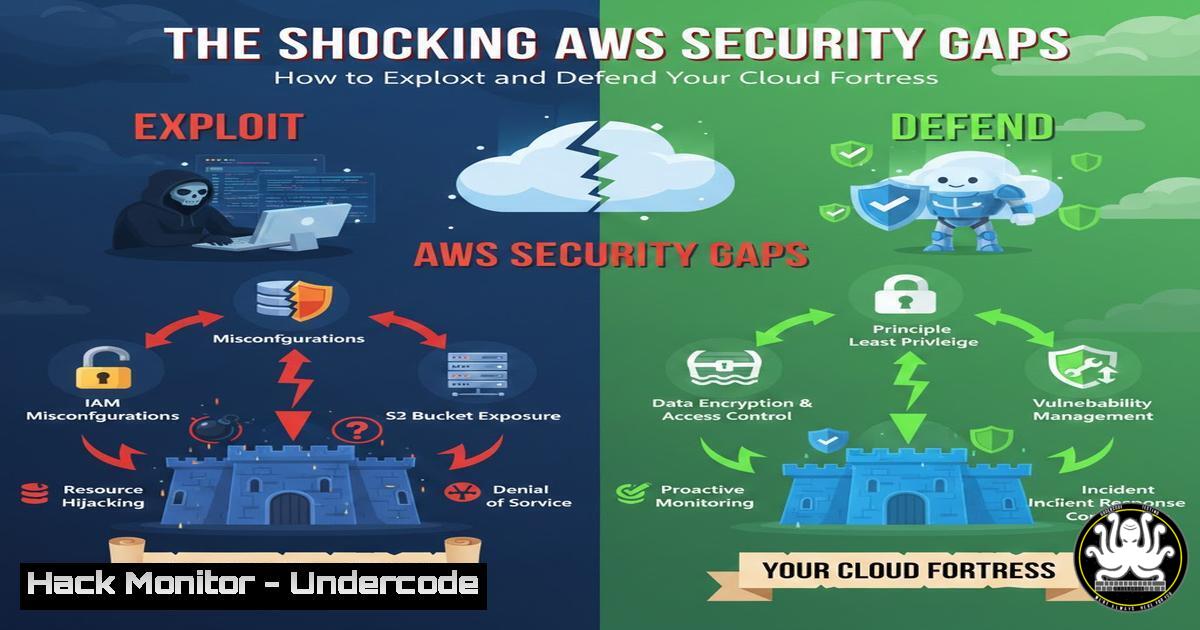
🚨 The Shocking #AWS Security Gaps Nobody Told You About: How to Exploit and Defend Your Cloud Fortress undercodetesting.com/the-shocking-a… Educational Purposes!
3/5 Validate and sanitize all incoming data, including user input and payload parameters. Use libraries like OWASP ESAPI to help you identify and mitigate common vulnerabilities. Remember, a little validation goes a long way!
How To Combat AI-Enhanced Social Engineering Attacks via @AWNetworks #Cybersecurity arcticwolf.com/resources/blog…
1/ Learn attack vectors first OWASP Top 10 shows the most common vulnerabilities. Build security into architecture, not after deployment. Prevention > reaction.
> Trusted Advisor & Self-help resources Whether you pay for support or not, AWS gives you powerful self-help tools: > Trusted Advisor checks 5 categories: Cost Optimisation, Performance, Security, Fault Tolerance, Service Limits. Basic users get limited checks;…
Strengthen your cloud security with the practices that matter most. From identity controls to encryption and continuous monitoring, @awscloud gives enterprises the foundation to stay secure while scaling with confidence.



New post by Vimal Paliwal. Stop Malware at the Door: Automated S3 File Scanning with AWS GuardDuty dev.to/aws-builders/s… #aws #guardduty #lambda #security
Attackers are moving beyond on-prem systems and now using AWS’s own encryption and key management features to lock organizations out of their cloud data. networkworld.com/article/409448…
This is a very good read and a good upgrade. I think “aws login” is more secure than “aws configure”.
Verify internal access to critical AWS resources with new IAM Access Analyzer capabilities aws.amazon.com/blogs/aws/veri… #aws #cloudcomputing #cloud #devops #azure #technology #python #awscloud #cybersecurity #amazonwebservices
AWS has published new guidelines for authorized network scanning to help customers safely test and monitor their AWS environments via Stephen Goodman on Amazon Web Services (AWS) aws.amazon.com/blogs/security… #aws #awscloud #Security #NetworkSecurity #CloudSecurity
Referencing Synapxe's HealthX-AWS Co-Innovation Lab, Amazon Web Services (AWS)' Elsie Tan says that AWS offers over 300 cloud security tools and enables a highly resilient infrastructure with multiple Availability Zones.🩺 buff.ly/Ghd4InF @awscloud

The best approach I know of for reducing the risk here is to make sure that any credentials that are visible to coding agents - like AWS keys - are tied to non-production accounts with strict spending limits That way if the credentials are stolen the blast radius is limited
From compliance to containers—secure your AWS stack with: ✅ NIST, PCI DSS, GDPR ✅ Serverless & IoT protection ✅ Multi-cloud & hybrid strategies Built for cloud pros & security enthusiasts. 🛡️ #CloudSecurity #AWS #DevSecOps #CyberResilience 🔗 ow.ly/VQ7H50X6qT6

Something went wrong.
Something went wrong.
United States Trends
- 1. #ALLOCATION 226K posts
- 2. #JUPITER 226K posts
- 3. The BIGGЕST 467K posts
- 4. #GMMTVxTPDA2025 601K posts
- 5. #GivingTuesday 9,052 posts
- 6. Good Tuesday 28.9K posts
- 7. rUSD N/A
- 8. Kanata 24.6K posts
- 9. #AreYouSure2 54.2K posts
- 10. JOSSGAWIN AT TPDA2025 88K posts
- 11. JIMMYSEA TPDA AWARD 2025 64.4K posts
- 12. Snow Day 7,744 posts
- 13. Dart 39.4K posts
- 14. Costco 29.6K posts
- 15. Pentagon 57K posts
- 16. Bron 26.8K posts
- 17. Penny 23.4K posts
- 18. Hololive 16.5K posts
- 19. Dillon Brooks 8,271 posts
- 20. Matt Van Epps 62.1K posts