#binaryninja kết quả tìm kiếm
Sneak peek preview at new #BinaryNinja visualization tool utilizing #KaitaiStruct declarative power to explore inner structures of intricate binary formats. Hurray to more vis tools and integrations!
Closing out the #Pwn2Own 2018 blog series with with the details behind our sandbox-to-root privilege escalation (CVE-2018-4193). Write a less-shady exploit, and we'll give you a free #BinaryNinja Commercial License! blog.ret2.io/2018/08/28/pwn…
The new version of my #BinaryNinja plugin Obfuscation Analysis (v1.2) adds recursive function inlining in the decompiler. It collapses call-heavy code into a single function; analysis, constant propagation, DCE and other analyses work across boundaries. github.com/mrphrazer/obfu…
Just built a prototype for #BinaryNinja to deobfuscate MBAs within the decompiler. Simplified expressions are attached as comments. It will be released soon, stay tuned!

Why would we use genetic algorithms to construct an assembler??? Check out the latest #BinaryNinja blog post! binary.ninja/2018/06/19/fas…
New #BinaryNinja plugin: ReverserAI. It uses local large language models (LLMs) to derive semantically meaningful function names from decompiler output, demonstrating the potential of local LLMs to support reverse engineering on consumer hardware. Link: github.com/mrphrazer/reve…
Continuing with #BinaryNinja posters. This time - function. SSA form will be covered in different poster. Enjoy.

New #BinaryNinja vis tool based on #KaitaiStruct looks better and better ;) It supports all 129 formats available at formats.kaitai.io
I wrote a blog post on the automation of tedious reverse engineering tasks. We use string decryption in malware as an example. synthesis.to/2021/06/30/aut… We script #BinaryNinja to clean up the decompilation of the Mirai botnet. Try it yourself: github.com/mrphrazer/mira…
Closed source @Solana programs used to be safe. We’ve changed that. Learn how to hack Solana programs with our open-source #BinaryNinja plugin 👇 osec.io/blog/tutorials…

#BinaryNinja team spotted their icon in my laptop dock - nothing escapes your eyes: my daily RE companion 🥷

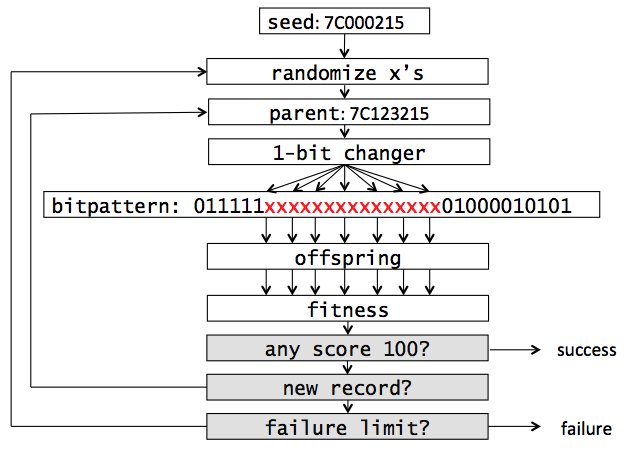
New version of my #binaryninja plugin to detect interesting code in binaries. I've added a new heuristic to detect simple XOR decryption loops. It can identify string decryption routines, code decryption stubs and cryptographic implementations. Code: github.com/mrphrazer/obfu…

New major release of my #BinaryNinja plugin obfuscation_detection: Additional to code detection heuristics to explore unknown binaries, it now also includes analysis helpers such as entropy computation to detect packed/encrypted code & data. Code: github.com/mrphrazer/obfu…

New blog post and updated #binaryninja plugin: "Statistical Analysis to Detect Uncommon Code" We use statistics to identify obfuscation in an #Anticheat, a mobile DRM, a #Windows kernel module & malware. Link: synthesis.to/2023/01/26/unc… Code: github.com/mrphrazer/obfu…

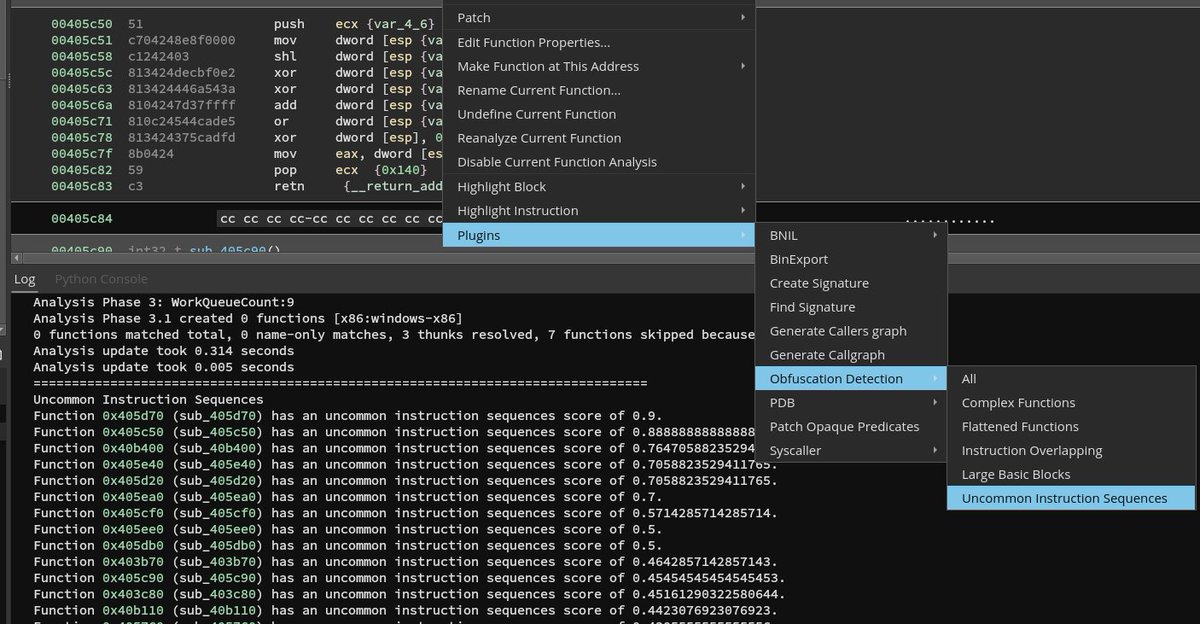
My #BinaryNinja plugin obfuscation_detection can now identify uncommon instruction sequences (such as MBAs or weird calculations) based on stochastic n-gram analysis. Right now the feature works for x86-64; an architecture-agnostic version follows soon. github.com/mrphrazer/obfu…
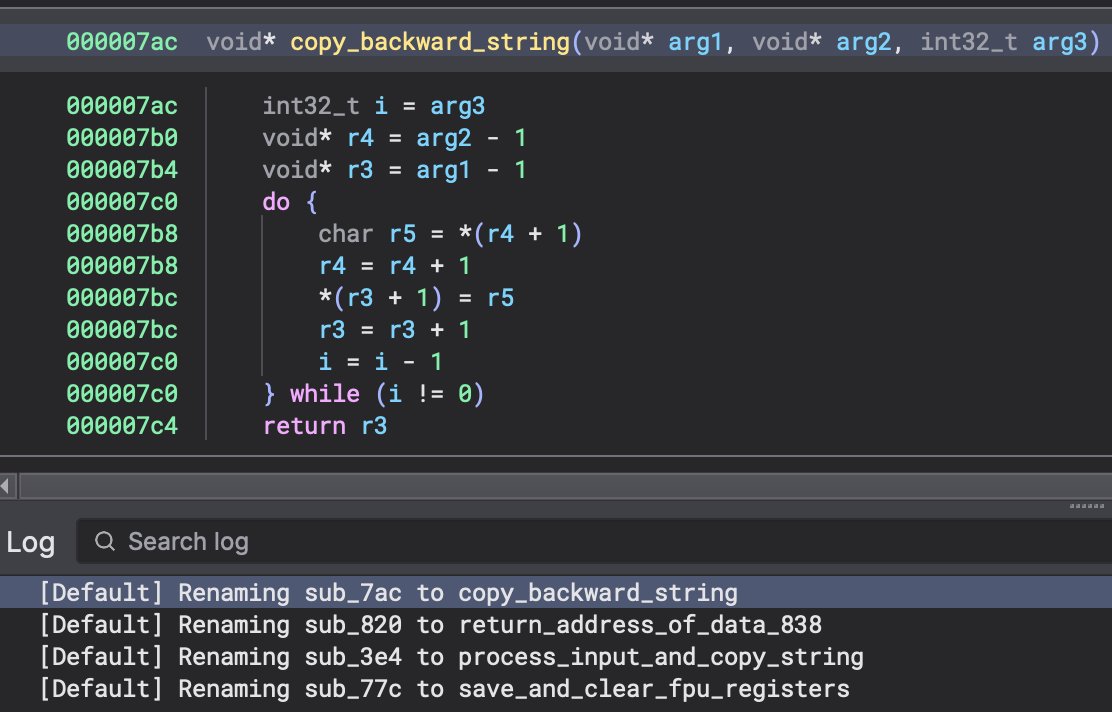
My new blog post introduces a heuristic based on call frequency to identify API functions in statically-linked executables & embedded firmware. It also detects API hashing routines in PlugX malware. Link: synthesis.to/2023/08/02/api… #binaryninja plugin: github.com/mrphrazer/obfu…

Have you seen all the features we've released for Binary Ninja? These are just a few of the many that we're excited to offer our users #BinaryNinja #reverseengineering

If you're writing/editing shellcode or work towards OSED course like me, this #BinaryNinja plug in should come in handy 👇 github.com/CX330Blake/She…
Static pointer tracking is tricky. Just shipped some improvements to my #BinaryNinja plugin #Mole: it now tracks array and struct members more precisely. An example on how Mole does this: github.com/cyber-defence-… Binja's multiple ILs make precise analysis so much more powerful!

📚🦠Zero2Auto - Custom Sample - Stage 1 The first stage of the provided sample offers some interesting features that are excellent for reinforcing the content learnt so far in this course. #zero2auto #BinaryNinja #pestudio medium.com/@0x747863/zero…
- ساختار داده های پیچیده رو شناسایی و بازسازی میکنه. - نمایش گرافیکی قابل پیکربندی داره. - از دیکامپایلرهای #IDAPro , #Ghidra و #BinaryNinja پشتیبانی میکنه. - قابل اجرا روی #Windows، #Linux، و #macOS هستش.
The recording of our (CC @nicolodev) talk "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" at @reconmtl is now online! Recording: youtube.com/watch?v=QxSGWk… Slides: synthesis.to/presentations/… #BinaryNinja Plugin: github.com/mrphrazer/obfu…
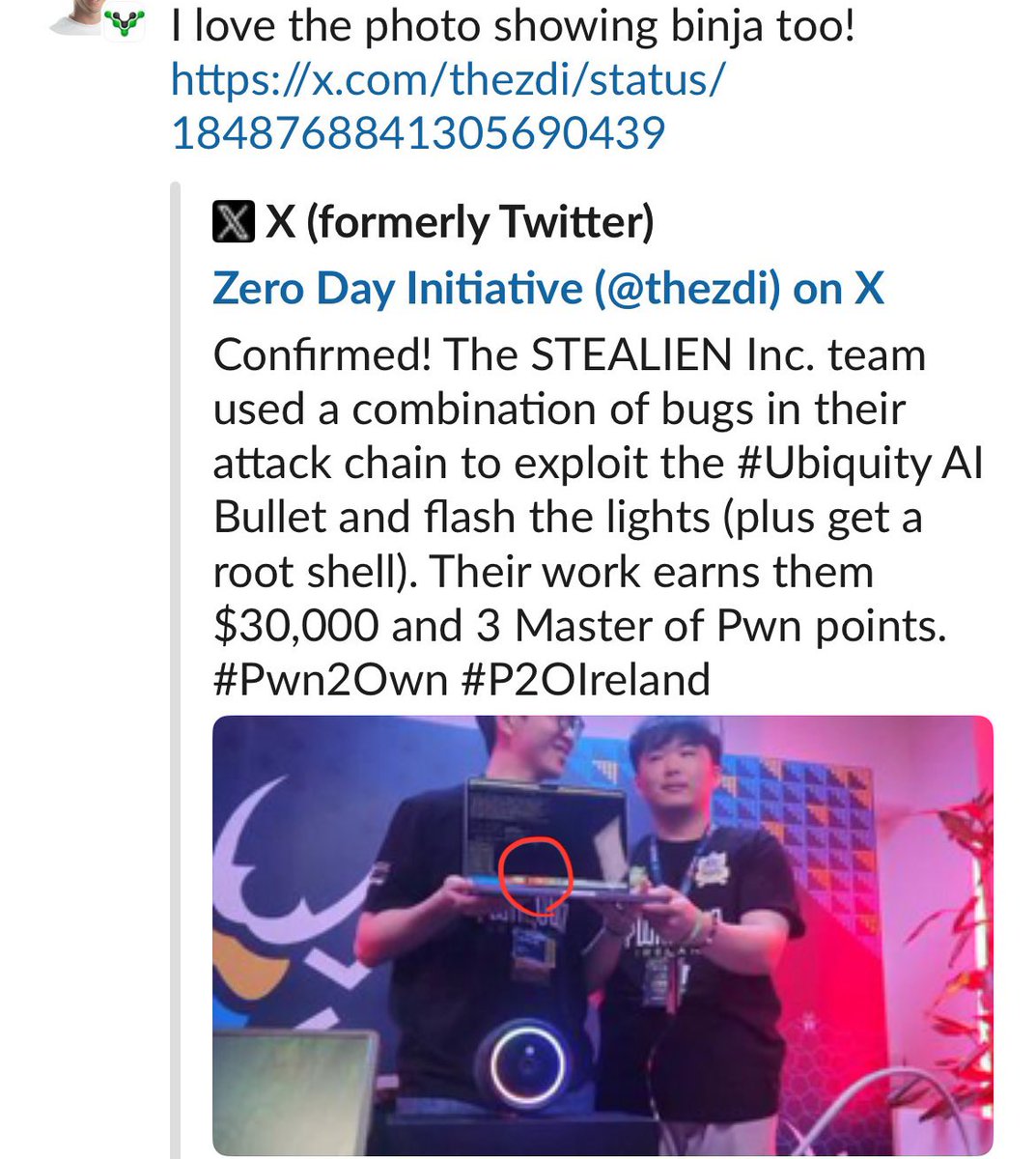
The recording of our @defcon talk is now available. We shared our approach to reversing IoT and OT malware written in Go using a hybrid toolkit that blends AI with traditional analysis methods using #Radare2 , #Ghidra, and #BinaryNinja. youtu.be/TtPicirB6G4?si… #IoT #Reversing #AI
youtube.com
YouTube
DEF CON 33 - Go Malware Meets IoT - Challenges, Blind Spots, and...
The new version of my #BinaryNinja plugin Obfuscation Analysis (v1.2) adds recursive function inlining in the decompiler. It collapses call-heavy code into a single function; analysis, constant propagation, DCE and other analyses work across boundaries. github.com/mrphrazer/obfu…
Exciting! @vector35's excellent #BinaryNinja ships with built-in BinExport in the latest dev version! Here's how to use it with #BinDiff: dev-docs.binary.ninja/guide/binexpor…

New #BinaryNinja plugin: Obfuscation Analysis Simplifies arithmetic obfuscation (MBA) directly in the decompiler (see demo below). Also identifies functions with corrupted disassembly. Co-authored by @nicolodev; available in the plugin manager. github.com/mrphrazer/obfu…
Jordan Wiens (@psifertex) is one of the co-founders of @vector35, and developers of #BinaryNinja. Jordan shares the techniques he uses to break decompilers, and a framework to evaluate existing techniques according to various properties. More info: linkedin.com/posts/off-by-o…

More details: @nicolodev and I discuss the current state of MBA (de)obfuscation and their applications @reconmtl We’ll also introduce a new #BinaryNinja plugin for simplifying MBAs in the decompiler. Details: cfp.recon.cx/recon-2025/fea…

Happy to announce that @nicolodev and I will be giving a talk titled "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" at @reconmtl More information will follow in the coming days.
مهمان قسمت هفتم پادکست Behind the Binary آقای @psifertex ، یکی از هم بنیانگذاران Vector 35 و سازندگان #BinaryNinja هستش و در خصوص چشم انداز آینده #امنیت_سایبری، تاثیر #هوش_مصنوعی، توسعه ی Binary Ninja و شرکت در #CTF صحبت میکنن. اسپاتیفای : open.spotify.com/episode/6tMYu7…
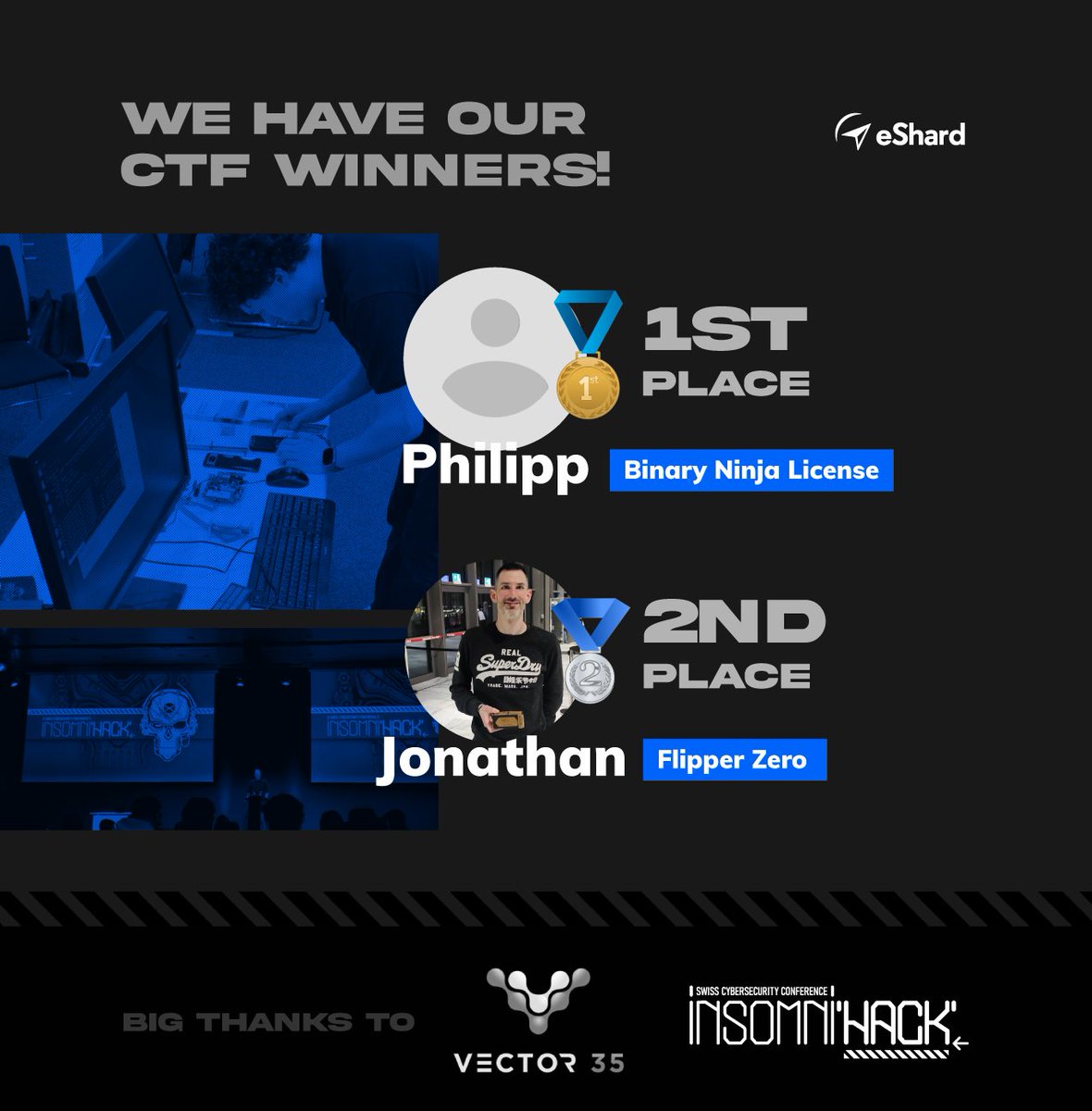
Huge thanks to @vector35 for supporting the challenge and offering a #BinaryNinja license to the first-place winner. 🏅
ابزار #BinaryNinja یک ابزار #مهندسی_معکوس و آنالیز باینری هستش که امکان اسکریپت نویسی با #پایتون برای خودکارسازی فرایندهارو فراهم میکنه. اگه فرصت نکردید، برنامه ضبط میشه و بعدا هم از همون لینکها قابل دسترسه.
New heuristic in my #BinaryNinja plugin obfuscation_detection: Duplicate Subgraphs uses iterative context hashing to spot repeated multi-block code. We merge each block’s signature with its successors over multiple rounds for efficiency. Link: github.com/mrphrazer/obfu…

Learn how to record a Time Travel Debug (TTD) trace using Binary Ninja! Discover key steps to capture emulation and execution instructions in this insightful video. 🌐 #Debugging #BinaryNinja #USA link: ift.tt/q6dMNZA

Sneak peek preview at new #BinaryNinja visualization tool utilizing #KaitaiStruct declarative power to explore inner structures of intricate binary formats. Hurray to more vis tools and integrations!
Closing out the #Pwn2Own 2018 blog series with with the details behind our sandbox-to-root privilege escalation (CVE-2018-4193). Write a less-shady exploit, and we'll give you a free #BinaryNinja Commercial License! blog.ret2.io/2018/08/28/pwn…
New #BinaryNinja plugin: ReverserAI. It uses local large language models (LLMs) to derive semantically meaningful function names from decompiler output, demonstrating the potential of local LLMs to support reverse engineering on consumer hardware. Link: github.com/mrphrazer/reve…

New #BinaryNinja vis tool based on #KaitaiStruct looks better and better ;) It supports all 129 formats available at formats.kaitai.io
ripr is a #BinaryNinja plugin that makes rapid code reuse easy, this week it got a few new features: blog.ret2.io/2017/11/01/rip…
Just built a prototype for #BinaryNinja to deobfuscate MBAs within the decompiler. Simplified expressions are attached as comments. It will be released soon, stay tuned!

Closed source @Solana programs used to be safe. We’ve changed that. Learn how to hack Solana programs with our open-source #BinaryNinja plugin 👇 osec.io/blog/tutorials…

Why would we use genetic algorithms to construct an assembler??? Check out the latest #BinaryNinja blog post! binary.ninja/2018/06/19/fas…

New major release of my #BinaryNinja plugin obfuscation_detection: Additional to code detection heuristics to explore unknown binaries, it now also includes analysis helpers such as entropy computation to detect packed/encrypted code & data. Code: github.com/mrphrazer/obfu…

New blog post and updated #binaryninja plugin: "Statistical Analysis to Detect Uncommon Code" We use statistics to identify obfuscation in an #Anticheat, a mobile DRM, a #Windows kernel module & malware. Link: synthesis.to/2023/01/26/unc… Code: github.com/mrphrazer/obfu…

Continuing with #BinaryNinja posters. This time - function. SSA form will be covered in different poster. Enjoy.

#BinaryNinja team spotted their icon in my laptop dock - nothing escapes your eyes: my daily RE companion 🥷


Something went wrong.
Something went wrong.
United States Trends
- 1. Dodgers 683K posts
- 2. World Series 360K posts
- 3. Yamamoto 212K posts
- 4. Blue Jays 119K posts
- 5. Will Smith 49.1K posts
- 6. Miguel Rojas 42K posts
- 7. Yankees 15.6K posts
- 8. Kershaw 34.2K posts
- 9. Baseball 162K posts
- 10. Kendrick 17.2K posts
- 11. Dave Roberts 13.4K posts
- 12. Vladdy 22.1K posts
- 13. Ohtani 86.9K posts
- 14. #Worlds2025 27.8K posts
- 15. Jeff Hoffman 3,735 posts
- 16. Cubs 7,616 posts
- 17. Auburn 14.3K posts
- 18. Nike 36.3K posts
- 19. Mets 11.5K posts
- 20. Carlos Manzo 255K posts






































