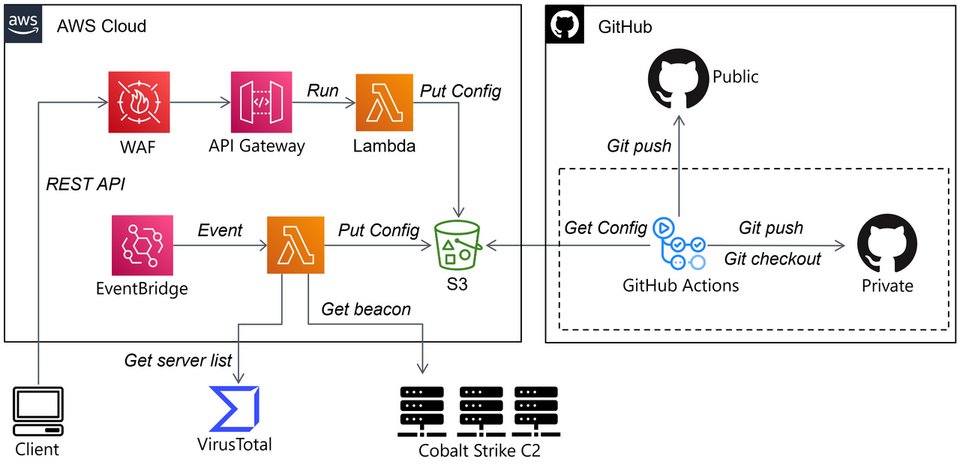
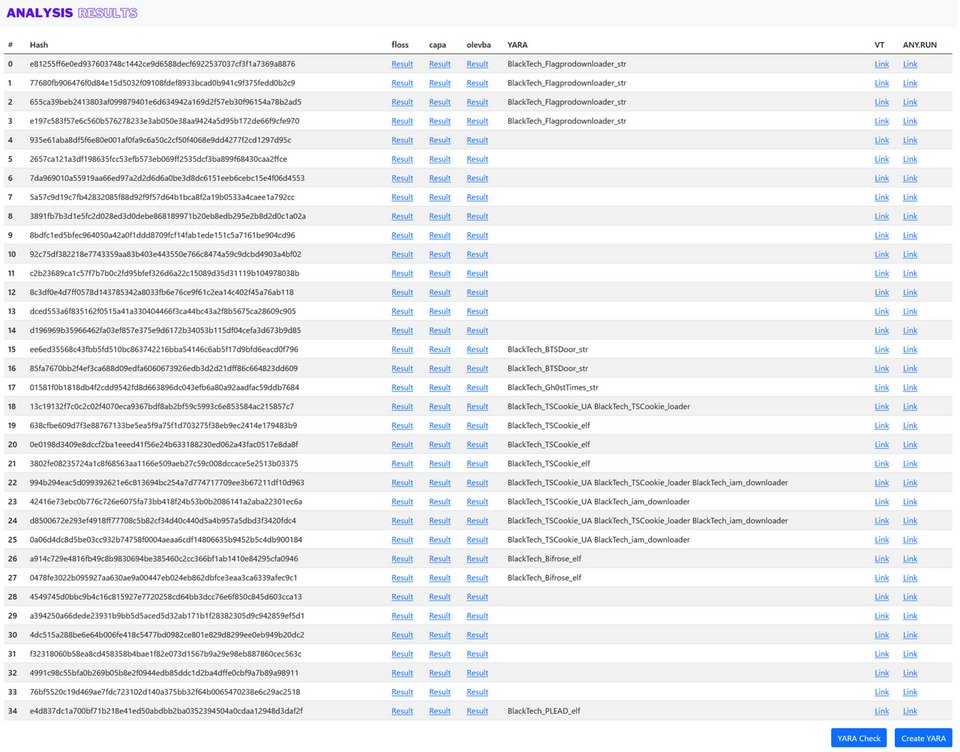
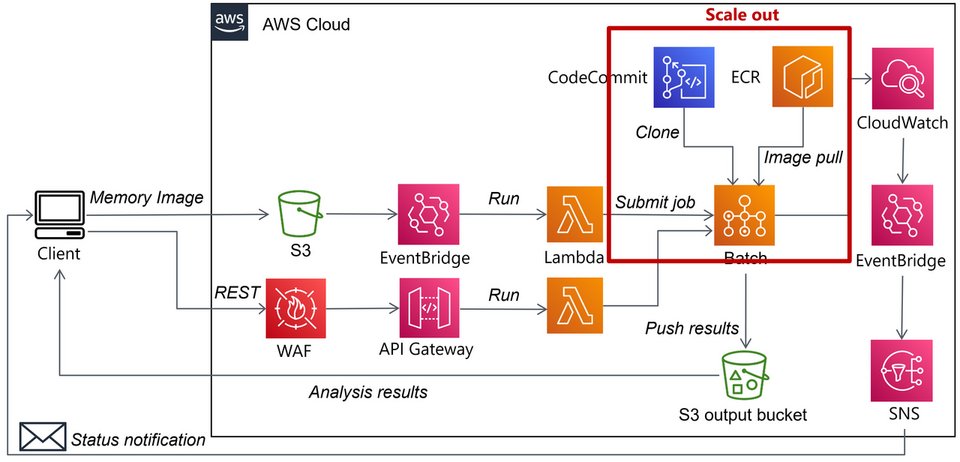
#malwareanalysis search results
🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 github.com/ShadowOpCode/S… #LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence


It’s finally here! 📦 Just received my own printed copies of MAoS – Malware Analysis on Steroids 🔥 There’s nothing like holding your work after months of writing, research, and late-night debugging. Get your copy here👉amazon.com/dp/B0FQDGZGZW #CyberSecurity #MalwareAnalysis…


The PolySwarm ecosystem runs on a diverse set of independent engines, each with its own approach to detecting and classifying threats. Different perspectives. Shared intelligence. Better protection. #CyberSecurity #ThreatIntelligence #MalwareAnalysis #PolySwarm
Example: IDA + DIE — Decode XOR data directly in DIE’s data convertor. A fast workflow for efficient malware analysis. #MalwareAnalysis #XOR #ReverseEngineering #DIE #IDA
PolySwarm empowers security teams with private, scalable malware analysis and real-time intelligence, designed for today’s threat landscape. #CyberSecurity #ThreatIntelligence #MalwareAnalysis

Revisited my malware analysis project using FLARE VM and upgraded it with a custom YARA rule to hunt AgentTesla variants. Proud of how it turned out. Shoutout to @ireteeh and @Cyblackorg for this opportunity 🙂 #MalwareAnalysis #YARARules #Cybersecurity #ThreatHunting #FLAREVM

BAT & PowerShell: powerful admin tools — but attackers can abuse them. Follow for Part 2: how to detect & defend. Drop of the week youtu.be/j5PTyL9TFZA?si… #MalwareAnalysis #Cybersecurity #HackDef #script #training
Malware hides behind layers of obfuscation. Most analysts slow down there. We don’t. 👊⚡️ #NeZa reveals runtime behavior, API activity, and memory artifacts fast — and you learn to do it hands-on. Train like a real defender, not a spectator. #MalwareAnalysis #DFIR #BlueTeam
A new approach to static analysis with AI that turns days of research into hours. No MCP or live IDA required. Using GPT-5, we completely cracked XLoader v8, one of the most challenging malware families to analyze. #XLoader #MalwareAnalysis #AI research.checkpoint.com/2025/generativ…
It just warms my heart ❤️ #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware
Fixing an APT sample so it can work on Modern Windows versions - An Exercise in Reverse Engineering gist.github.com/ahm3dgg/b2041f… #malware #malwareanalysis #reverseengineering
We’re excited to welcome Anmol Maurya, Staff Malware Reverse Engineer @ Palo Alto Networks, as he reveals how attackers leverage Go’s portability to target Mac & Linux—and why multi-OS defenses matter. #CyberSecurity #MalwareAnalysis #Infosec #ThreatResearch

RL ❤️ #YARArules! We've been writing them for years. Watch below to see how RL Spectra Analyze makes YARA seamless & powerful for the #SOC. #MalwareAnalysis
Hello! I just dropped a new article about an old but very up-to-date subject. Please let me know if you find anything incorrect or not well-explained. moval0x1.github.io/posts/the-peb-… #malwareanalysis #reverseengineering #malcat #x64dbg #pebwalk #shellcode
moval0x1.github.io
The PEB Walk Anatomy
Practical Techniques for Shellcode & Reversing
🔥 A week after release and thank God, MAoS – Malware Analysis on Steroids is officially a #1 Best Seller on Amazon! Get your copy today: amazon.com/gp/aw/d/B0FQDL… #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware


Deep dive into CyberGate RAT! 🔬 We unpack this notorious Delphi malware, detail its process injection, persistence, and C2 communication Don't miss the full technical breakdown! Read the analysis: blog.cyber5w.com/cybergate-malw… #C5W #MalwareAnalysis #CyberGate #RAT #DFIR #InfoSec…

🚨 New variant spotted: Matanbuchus 3.0 — a rebuilt malware loader advertised on underground forums. Features DNS/HTTPS C2, in-memory execution, reverse shell, morphing builds & multitenant panel. Price: $10K–$15K/month. Active threat. #CyberThreat #Infosec #MalwareAnalysis

🔍 A DLL isn’t a standalone file — it has no main function like an EXE. That’s why we need tools like WinDbg + SOS to uncover where execution really begins. In this week’s drop, we show you how. youtu.be/MsijfXAu3rA?si… #ReverseEngineering #dotnet #MalwareAnalysis #HackDef #dll
RL recently introduced significant updates to its #MalwareAnalysis & #ThreatHunting portfolio, adding new AI-driven & Kubernetes-ready capabilities. Join us this Friday to learn more: bit.ly/47pe4ff

رشتو: معرفی تکنیک #ControlFlowFlattening: این تکنیک مبهم سازی، ساختار منطقی و طبیعی یک تابع یا برنامه رو از بین میبره و اون رو به مجموعهای از بلوکهای کد تبدیل میکنه که توسط یک Dispatcher مرکزی و یک متغیر وضعیت (State Variable) کنترل میشن. #آنالیز_بدافزار #MalwareAnalysis 1/6
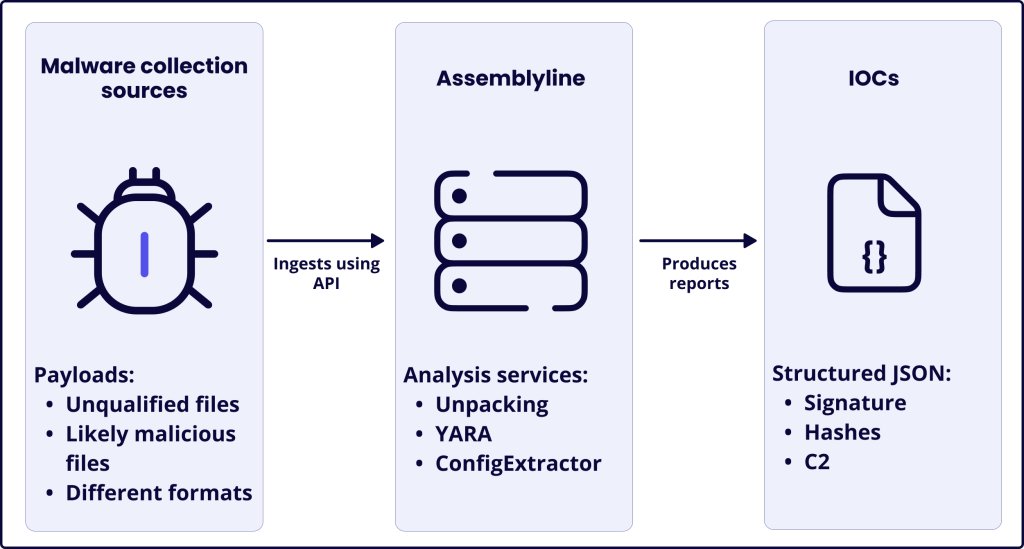
Sekoia TDR leverages Assemblyline's staged pipeline and ConfigExtractor to automate malware config extraction, demonstrated on Kaiji IoT botnet. Uses YARA detection and Python decoding for C2:Port data. #IoTSecurity #MalwareAnalysis #Canada ift.tt/FXU0K2W
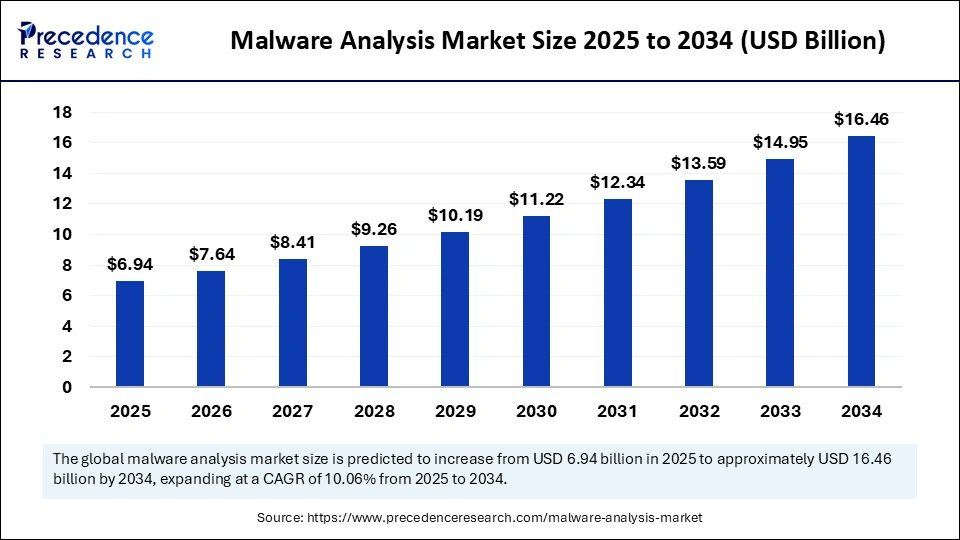
The #malwareanalysis market is rising fast—valued at $6.94B in 2025 and projected to reach $16.46B by 2034 (CAGR 10.06%). With cyberattacks growing more sophisticated, demand for automated threat detection and real-time security intelligence is surging. precedenceresearch.com/malware-analys…
WithSecure's STINGR Group has released a detailed analysis of TangleCrypt, a sophisticated yet buggy Windows malware packer, found in a ransomware attack, outlining its unpacking process and implementation flaws. #CyberSecurity #MalwareAnalysis labs.withsecure.com/publications/t…
Malware Analysis Report 🔥🫡 medium.com/@nanaaisha1030… @ireteeh @judeosamor @TemitopeSobulo @segoslavia #CyberSecurity #MalwareAnalysis

2/8 Instant Risk Scoring: Get 0-100 security scores in seconds! The tool automatically detects: Packed malware (UPX unpacking built-in) Suspicious imports & API patterns Future timestamps & fake signatures 186+ embedded URLs & IP addresses #MalwareAnalysis #ThreatDetection
#JSAC2026 registration is now open. #DFIR #MalwareAnalysis jsac.jpcert.or.jp/en/registratio…
Attackers are getting smarter, using signed Microsoft binaries to hide their tracks. Our latest analysis reveals how a hidden Python fragment injects into cvtres.exe to evade detection. Get the full technical breakdown here labs.k7computing.com/index.php/mask… #CyberSecurity #MalwareAnalysis
Ofuscar = ganar tiempo. Mientras vos peleás con el rompecabezas, el malware se instala. #MalwareAnalysis #CyberDefense #IngenieriaInversa
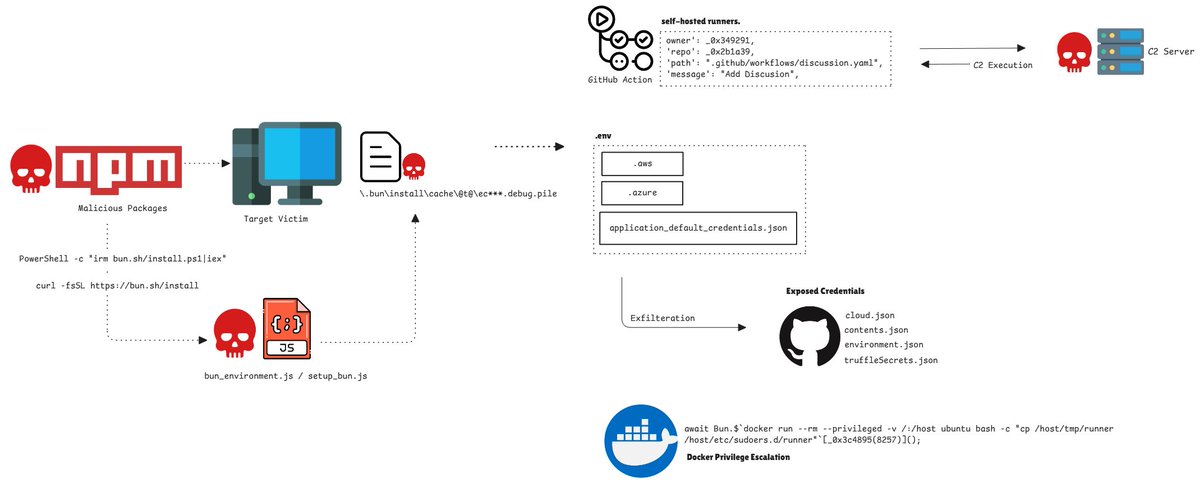
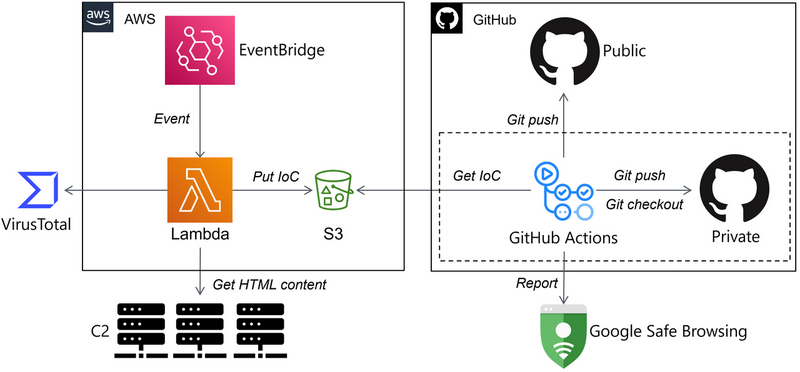
Silent Exfilteration : Sha1-Hulud: The Second Coming. The rise of modern software supply chains has accelerated rapidly—and with it, a new wave of highly sophisticated, often invisible cyberattacks. #SupplyChainAttack #MalwareAnalysis #Sha1Hulud CC: @malwarehuntslab
🚀 MAoS just hit 1,000 reads on ResearchGate! Grateful to see researchers and security professionals diving into the book and using it in real-world work. More research and deep-dive content coming soon. 📖 amazon.com/dp/B0FQDGZGZW #CyberSecurity #MalwareAnalysis…

مستوى متقدم من التخفي البرمجية لا تُكتب على القرص الصلب، بل تعمل من الذاكرة فقط — ما يجعل اكتشافها عبر برامج الحماية التقليدية صعبًا للغاية. كما تستخدم خوارزميات XOR لتشفير الأوامر وإخفاء أنشطتها عن أدوات المراقبة الأمنية. #InfoSec #MalwareAnalysis
🚨 New Python-based WhatsApp worm spreading via malicious links. Visit @TheHackersNews for more details #MalwareAnalysis #Python #WhatsApp
Malicious apps use advanced evasion like packing, obfuscation, and multi-stage payloads to bypass detection. Fake screens mimic official stores while native code and encrypted files hide threats. #AppSecurity #MalwareAnalysis #Japan ift.tt/gLvaFPl
hendryadrian.com
Analysis Report on Malicious Apps Using Advanced Detection and Evasion Techniques – ASEC
Malware developers are employing advanced evasion techniques such as packing, obfuscation, and multi-stage payloads to bypass detection. The malicious app manipulates native code and encrypted files,...
Malware Classification on @TryHackMe taught me to identify and categorize threats, from adware and spyware to ransomware, wipers, and keyloggers. Understanding malware families and attack patterns sharpens threat detection skills. #SOC #BlueTeam #MalwareAnalysis
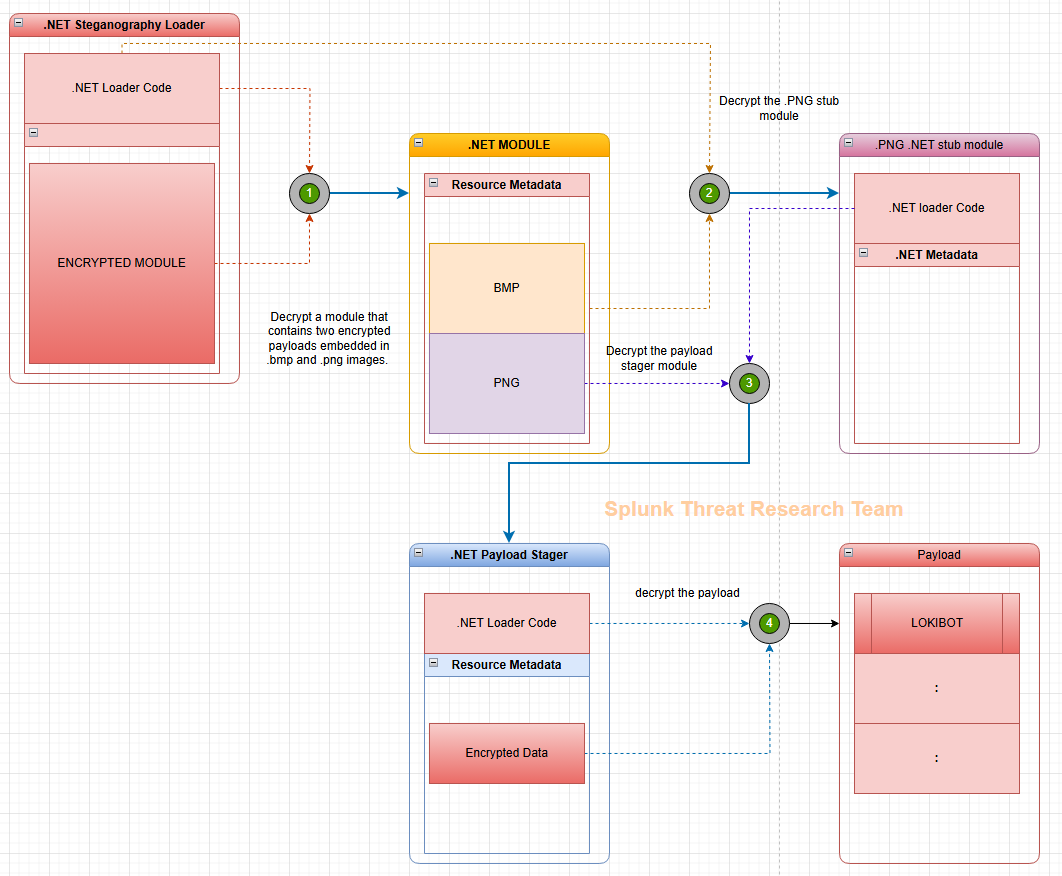
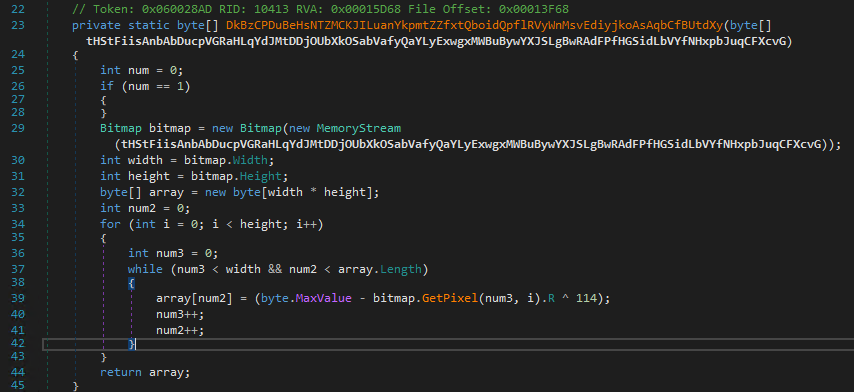
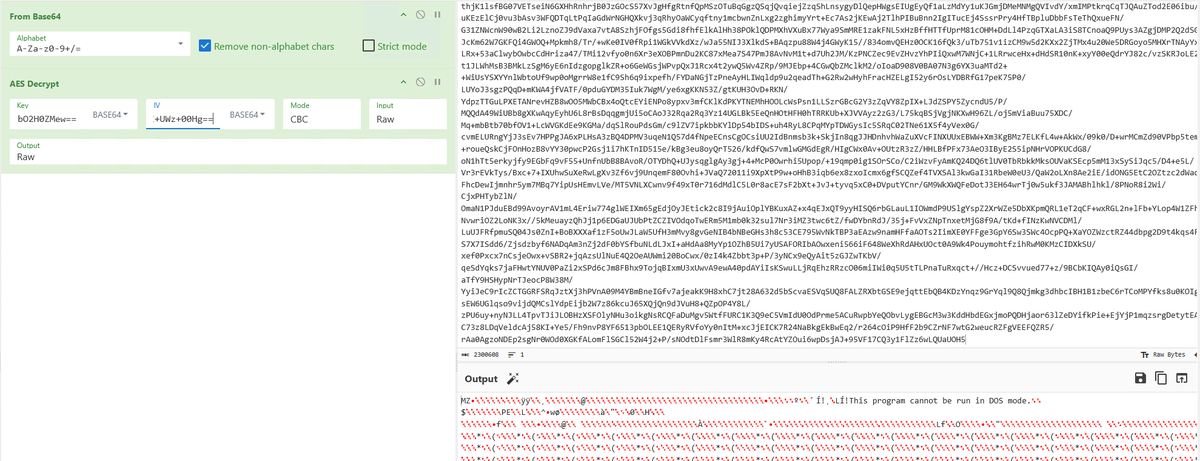
A new .NET steganographic loader disguises as a business document, hiding Lokibot payloads in images, enabling credential theft, code injection, and persistence via scheduled tasks. #Lokibot #Steganography #MalwareAnalysis ift.tt/VT0U1XO
Real-world adoption drives ecosystem strength. PolySwarm’s malware intelligence platform is now powering threat detection across enterprise and ISAC networks. #CyberSecurity #ThreatIntelligence #MalwareAnalysis #InfoSec #EnterpriseSecurity

✅ Completed the REMnux: Getting Started lab on @TryHackMe! Learned the fundamentals of malware analysis & reverse engineering using REMnux 🔍#CyberSecurity #TryHackMe #MalwareAnalysis #BlueTeam @anand114bug @CyberMindSpace @rikki59845
🧵New: "From Pixels to Payloads" — We reverse-engineered a multi-stage .NET loader hiding Lumma Stealer in BMPs via stego trick: (255-R)^0x72. Donut Loader → C# Injector → Lumma in memory. 🧠👇 github.com/ShadowOpCode/S… #LummaStealer #Infosec #MalwareAnalysis #ThreatIntelligence




It just warms my heart ❤️ #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware

🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥 Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg. We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses. [1/24] 🖊️ #Malwareanalysis #Ghidra
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gG0vaUAAkrE4.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gOFMbIAA2_rv.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0gVA0bMAAeWzo.jpg)
![embee_research's tweet image. 🔥Lumma Stealer - Manually Unpacking and Extracting C2's 🔥
Let's analyse a Lumma malware sample and manually unpack it with Dnspy and x32dbg.
We'll then leverage Ghidra and x32dbg to locate and decrypt four C2 addresses.
[1/24] 🖊️
#Malwareanalysis #Ghidra](https://pbs.twimg.com/media/GC0hjgObwAAyIRM.png)
Revisited my malware analysis project using FLARE VM and upgraded it with a custom YARA rule to hunt AgentTesla variants. Proud of how it turned out. Shoutout to @ireteeh and @Cyblackorg for this opportunity 🙂 #MalwareAnalysis #YARARules #Cybersecurity #ThreatHunting #FLAREVM

CyberChef Tips - Creating and Accessing Variables #CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis. [1/2] #malware #malwareanalysis
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTCaMAECV1x.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTabwAAd1RG.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQTNa4AAkCq3.jpg)
![embee_research's tweet image. CyberChef Tips - Creating and Accessing Variables
#CyberChef has a little known "registers" operation that allows you to create and reference values later on in your analysis.
[1/2]
#malware #malwareanalysis](https://pbs.twimg.com/media/GPpGQR2bEAAPiZM.png)
It’s finally here! 📦 Just received my own printed copies of MAoS – Malware Analysis on Steroids 🔥 There’s nothing like holding your work after months of writing, research, and late-night debugging. Get your copy here👉amazon.com/dp/B0FQDGZGZW #CyberSecurity #MalwareAnalysis…


In one of the #MalwareAnalysis communities I’m in, we were talking about Go malware. Someone mentioned CAPA as a good tool. I have to say, it’s really helpful for finding the 50kb of interesting code buried inside a 5mb Go binary 😎What other tools do you use?

PolySwarm empowers security teams with private, scalable malware analysis and real-time intelligence, designed for today’s threat landscape. #CyberSecurity #ThreatIntelligence #MalwareAnalysis

🚨 New variant spotted: Matanbuchus 3.0 — a rebuilt malware loader advertised on underground forums. Features DNS/HTTPS C2, in-memory execution, reverse shell, morphing builds & multitenant panel. Price: $10K–$15K/month. Active threat. #CyberThreat #Infosec #MalwareAnalysis

Automating Malware Analysis Operations (MAOps) blogs.jpcert.or.jp/en/2023/01/clo… #Pentesting #MalwareAnalysis #CyberSecurity #Infosec
🦠💻Explore Part 2 of our Windows Malware blog series on process injections: 8ksec.io/dissecting-win… 📈Ready to sharpen your skills? Browse our courses here: academy.8ksec.io/course/practic… #MalwareAnalysis #Windows #ReverseEngineering

🔍 #Opendir Alert! 📂 Target: ⚠️ hxxps://m[.]bureaux[.]fr/ 📄 Sample Files: Advanced IP Scanner.exe AnyDesk.exe AnyDesk.apk ⚡ Repository contains .apk & .exe files. Handle with caution! 🛡️ 🎯 Potential resource for malware analysts. #CyberSecurity #MalwareAnalysis…
![cyberfeeddigest's tweet image. 🔍 #Opendir Alert!
📂 Target:
⚠️ hxxps://m[.]bureaux[.]fr/
📄 Sample Files:
Advanced IP Scanner.exe
AnyDesk.exe
AnyDesk.apk
⚡ Repository contains .apk & .exe files. Handle with caution! 🛡️
🎯 Potential resource for malware analysts.
#CyberSecurity #MalwareAnalysis…](https://pbs.twimg.com/media/GhhcEuqWoAAUj9f.jpg)
Happened to analyze a suspicious macOS file. A developer downloaded Git from a git lookalike domain. Turns out to be #AMOS :) Thanks to @obje tool Lulu @patrickwardle Check out for more in the thread #macos #malwareanalysis #malware #infostealer

Silent Exfilteration : Sha1-Hulud: The Second Coming. The rise of modern software supply chains has accelerated rapidly—and with it, a new wave of highly sophisticated, often invisible cyberattacks. #SupplyChainAttack #MalwareAnalysis #Sha1Hulud CC: @malwarehuntslab

FLARE floss applied to all unpacked+dumped samples in Malpedia Nice project by Daniel Plohmann (@push_pnx) Blog post: danielplohmann.github.io/blog/2024/03/0… Github repo: github.com/malpedia/malpe… #malwareanalysis #infosec


🔥 A week after release and thank God, MAoS – Malware Analysis on Steroids is officially a #1 Best Seller on Amazon! Get your copy today: amazon.com/gp/aw/d/B0FQDL… #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware


Faculty Updation Program on #CyberSecurity and #MalwareAnalysis at @iitropar (IIT Ropar) as part of @InfoSecAwa of @GoI_MeitY is scheduled from 24th to 28th Feb 2025. @mygovindia @_DigitalIndia @SecretaryMEITY @abhish18 @cdacindia @IndianCERT @NICMeity @PIB_MeitY


Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 49.5K posts
- 2. Dillon Brooks 6,822 posts
- 3. Bron 24.4K posts
- 4. Giants 85.1K posts
- 5. #WWERaw 70.5K posts
- 6. Patriots 130K posts
- 7. Dart 36K posts
- 8. Suns 18.9K posts
- 9. Drake Maye 24.2K posts
- 10. Collin Gillespie 2,018 posts
- 11. #AvatarFireAndAsh 2,886 posts
- 12. Diaz 33.7K posts
- 13. Ryan Nembhard 4,118 posts
- 14. Devin Williams 7,708 posts
- 15. STEAK 10.4K posts
- 16. Gunther 15.1K posts
- 17. Pats 16.2K posts
- 18. James Cameron 4,435 posts
- 19. Devin Booker 2,615 posts
- 20. Joe Schoen 3,438 posts
























![K7CyberSecurity's tweet card. During a routine analysis at K7 Labs, we encountered a Python-based malware sample that uses multi-stage obfuscation. The de-obfuscated result […]](https://pbs.twimg.com/card_img/1993803281370427392/2fY_A7lc?format=jpg&name=orig)