#secureapplicationdevelopment 搜尋結果
Our @SteveTcherchian & @fenglin_Syd discussing #SecureApplicationDevelopment at the #HPE_NonStop #Korea Technology Day in #Seoul xypro.com #infosec

#Cybersecurity #SecureApplicationDevelopment #MicrosoftSecurity The Security Show: Secure application development explained lnkd.in/dCDqT_n
3 Secure Methodologies to Create a Secure Application! t.ly/Wo3X #createsecureapp #methodologiestocreatesecureapplication #secureapplicationdevelopment #applicationsecuritytestingmethodologies #cwebconsultants
Modernizing #ContainerSecurity Is Essential to #SecureApplicationDevelopment @nextgov “Securing containers necessitates a ‘shift left’ mentality .. #Security is fully integrated into the entire development process from start to finish.” #SecurityByDesign nextgov.com/ideas/2021/05/…
Discover essential strategies to ensure security in your PHP applications, protecting sensitive data and preventing vulnerabilities anastasionico.uk/blog/ensuring-… #ApplicationSecurityBestPractices #WebApplicationSecurityTips #SecureApplicationDevelopment
We're excited to announce our #FinancialServices Garage Series starting at 9 am EST on July 21st! This hands-on lab session will focus on two use cases - #FraudDetection at scale and #SecureApplicationDevelopment. google.smh.re/1EDm
Find security vulnerabilities from your web app with launchguard.dev before the hackers do, no tech expertise needed.
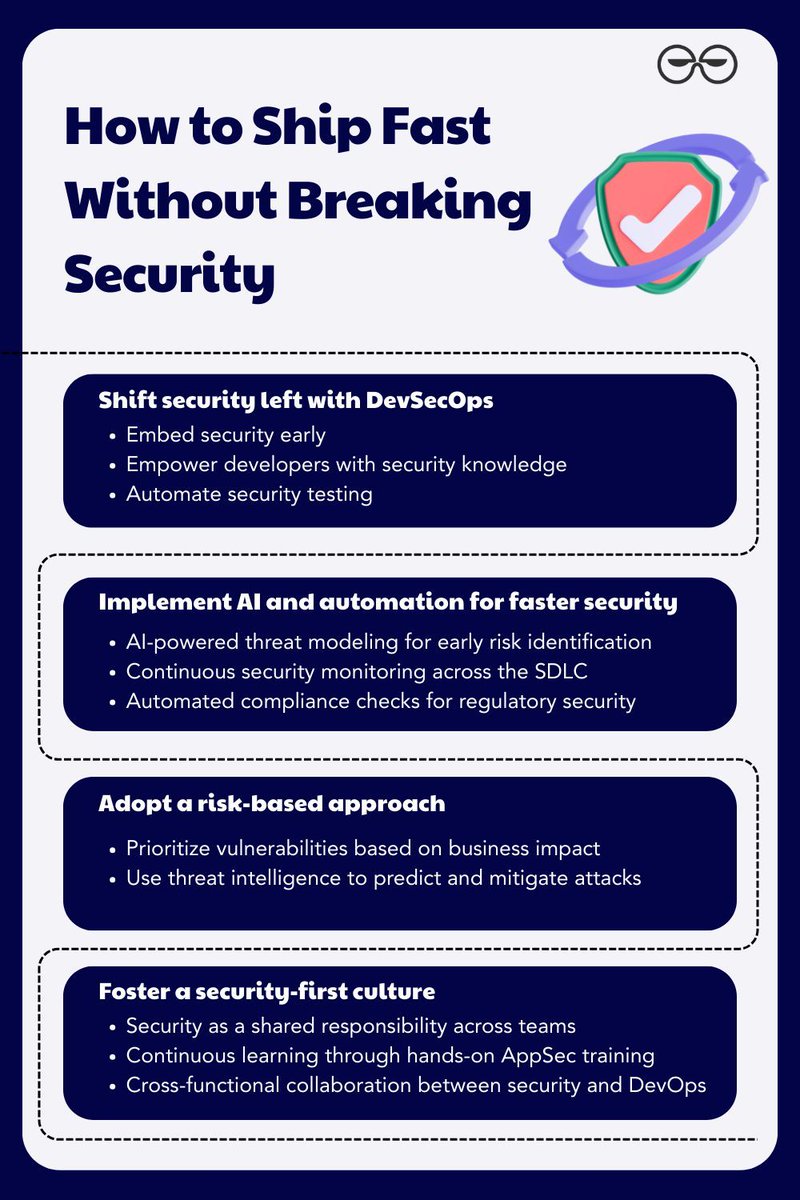
A lot of teams say they do DevSecOps, but the real change happens when security is built into the pipeline — not added at the end. A good DevSecOps process begins by securing your code early and fixing problems before the build stage. Here’s the real approach 🔹 Secure the…
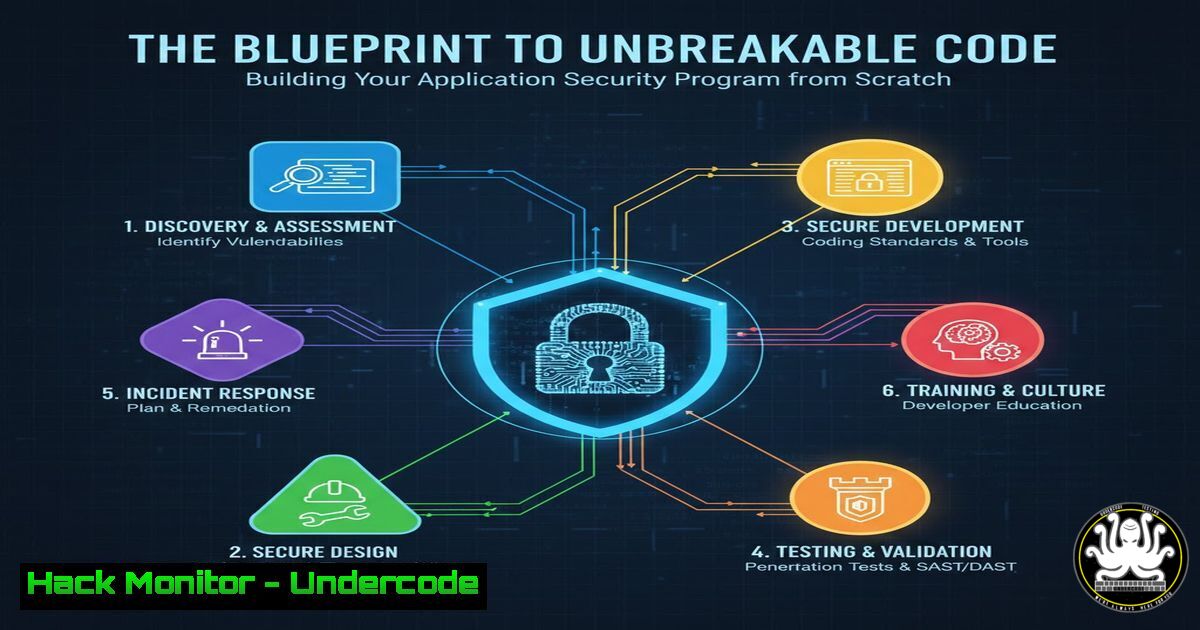
🛡️ The Blueprint to Unbreakable Code: Building Your Application Security Program from Scratch undercodetesting.com/the-blueprint-… Educational Purposes!
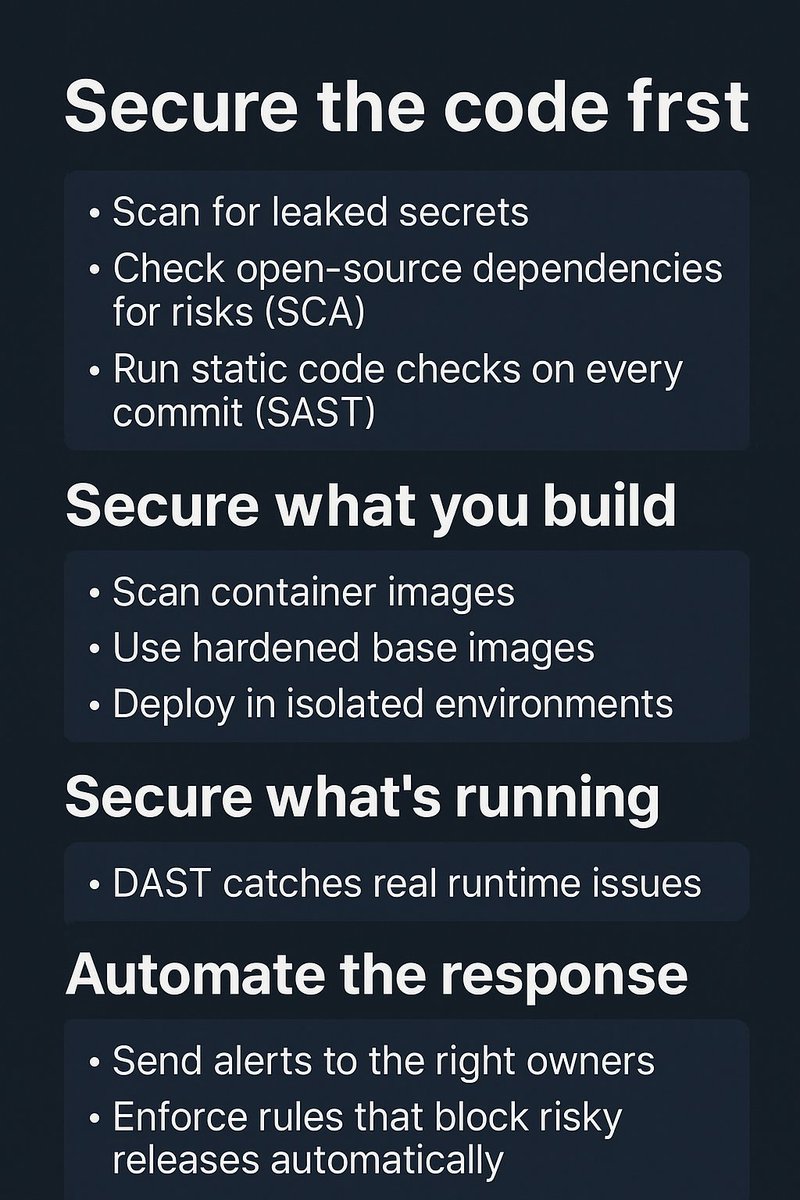
There’s no excuse to not prioritize security from Day 1 of the SDLC. If you’re serious about moving fast and staying secure, you need a process where security isn’t an afterthought, it’s built into every commit, every pipeline, every sprint. So how do you build that in without…
The winning security posture doesn't eliminate app sources—it segments them by risk classification. Banking apps on Play Store with SLA-backed security teams. Development tools on F-Droid with community audit. Critical infrastructure apps built in-house. This prevents any single…
Secure coding isn’t a checklist; it’s a mindset. ✅🧠 Strong teams master the fundamentals that make secure development the default. 👉 Read more: ow.ly/9LCP50Xyj6j #securecode #appsec #devsecops
Hard-coded secrets = hidden risk. 🕵️♂️ BigID finds them fast, flags the risk, and helps you fix it before it spreads. 🔐 Keep your secrets safe & your code clean: bit.ly/3RZup1N #BigID #AppSec #SecretsManagement #DataSecurity

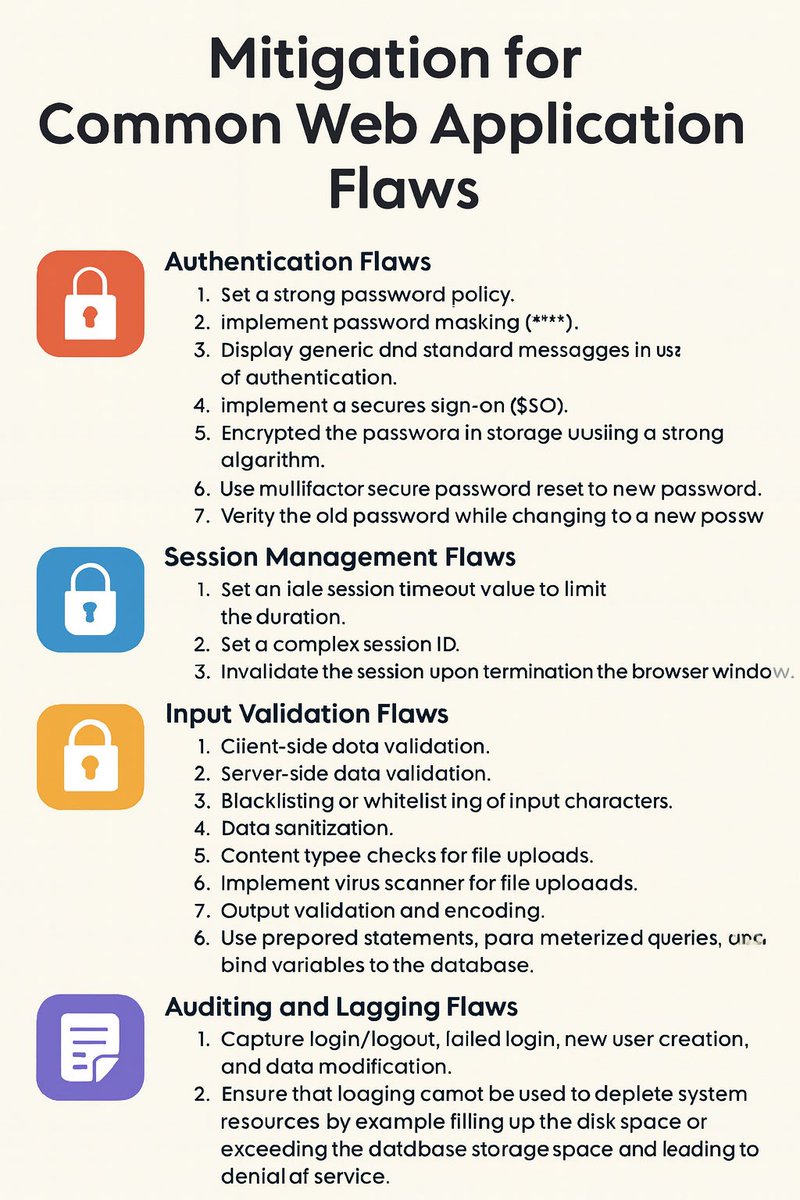
mitigations for common web app security flaws 🔐 From authentication and authorization to session management, input validation, and logging. Infographic below 👇 #Cybersecurity #AppSec #InfoSec #WebSecurity #Blue
👨💻 Secure code is the foundation of everything. This November, we’re thankful for dev teams who build with security in mind from day one. ➡️ Contact us for SDLC security support: standardusercyber.com #SDLC #AppSec #CyberGratitude #SecureDevelopment
Boost your web app's defenses by implementing Security Headers, such as Content Security Policy (CSP) and Strict-Transport Security (STS). Set a default CSP policy to block malicious scripts & prev... #bugbounty #pentesting #vulnerability
Security headers can reveal sensitive info about your app's infrastructure & dependencies. Review HTTP Response Headers & Content Security Policy to prevent XSS & other attacks. #OWASP #appsec #bugcrowd
Custom Salesforce Apex code is powerful, but can also create insecurities. That’s where our new #Apex labs come in! 🧪 Jump into realistic coding scenarios, spot vulnerabilities & implement practical fixes. 🔗 Build skills to secure your Salesforce apps blog.secureflag.com/2025/11/25/enh…
Security should always be front and center, instead of a retrofitting nightmare – and your Apex code is no different. Aidan explains why architecting secure Apex is essential and how to go about it. bit.ly/49CONQw
salesforceben.com
How to Architect Secure Apex in Salesforce | Salesforce Ben
From permissions and User Mode to defending against SOQL injection, learn the best practices for writing secure Apex code.
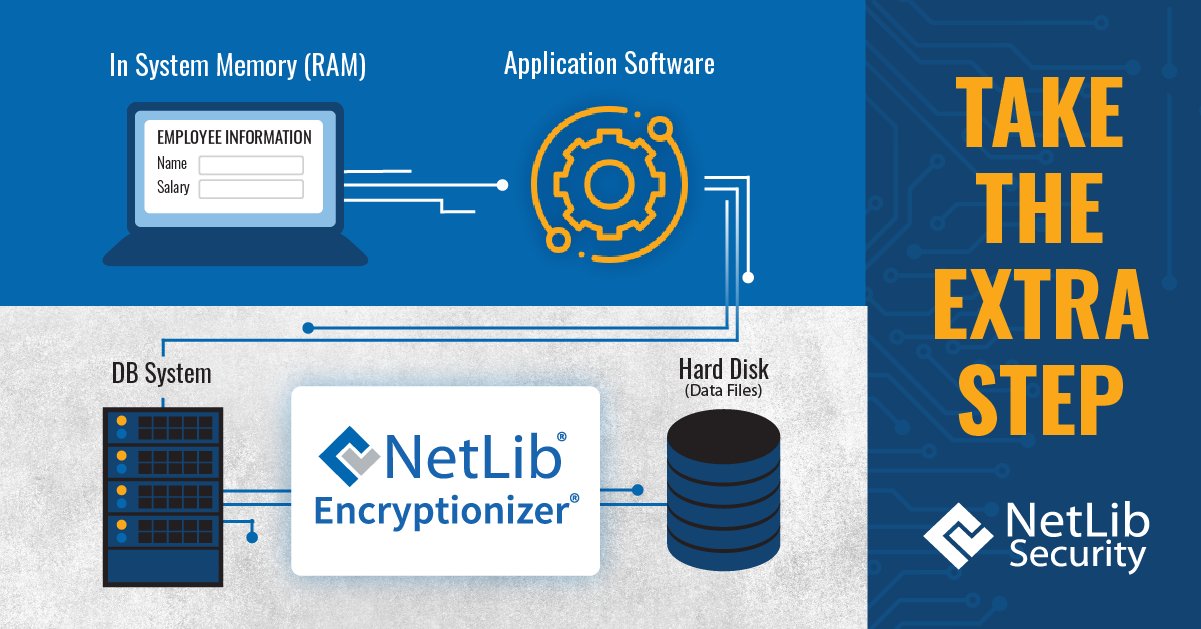
The stakes for application security have never been higher. Our latest article breaks down why application encryption must be the backbone of every modern security strategy. If your apps aren’t encrypted, your data isn’t protected. Learn more 👇 netlibsecurity.com/white-papers/a… #infosec
Our @SteveTcherchian & @fenglin_Syd discussing #SecureApplicationDevelopment at the #HPE_NonStop #Korea Technology Day in #Seoul xypro.com #infosec

Something went wrong.
Something went wrong.
United States Trends
- 1. #WWERaw 55.7K posts
- 2. Giants 67.7K posts
- 3. Giants 67.7K posts
- 4. Patriots 98.1K posts
- 5. Drake Maye 17.2K posts
- 6. Dart 28.8K posts
- 7. Diaz 33.4K posts
- 8. Gunther 11.8K posts
- 9. Devin Williams 5,971 posts
- 10. Younghoe Koo 4,446 posts
- 11. Abdul Carter 8,160 posts
- 12. Mets 16.6K posts
- 13. Marcus Jones 5,534 posts
- 14. LA Knight 11.9K posts
- 15. Theo Johnson 1,873 posts
- 16. #RawOnNetflix 1,806 posts
- 17. Kyle Williams 3,858 posts
- 18. Joe Schoen 1,911 posts
- 19. #NYGvsNE 1,799 posts
- 20. Kafka 6,893 posts