#secureprotocols 검색 결과
secure shell protocol over HTTP/3 with faster session setup and modern authentication

We built the internet to connect. Somewhere along the way, we made it a place to collect. @idOS_network is rebuilding that trust, starting with data itself. In idOS, security is not about locking information away. It’s about designing a world where exposure is impossible by…
小玉博士签到!今天依旧是深夜局!周末依然是白天做实验晚上学rust和了解项目,我要做到科研和web3两开花! 昨天我谈了 @SolvProtocol 是如何解决“沉睡BTC”的机会成本。今天,我想从我一个(即将)技术转行博士的视角,聊聊一个更深层的问题:信任。 昨天我说到 @SolvProtocol 帮纳斯达克公司管理…

Walrus is now the first decentralized data platform with onchain access control. With Seal live on Sui Mainnet, developers can store, encrypt, and control access to data - all onchain, all decentralized. Programmable privacy is finally here.
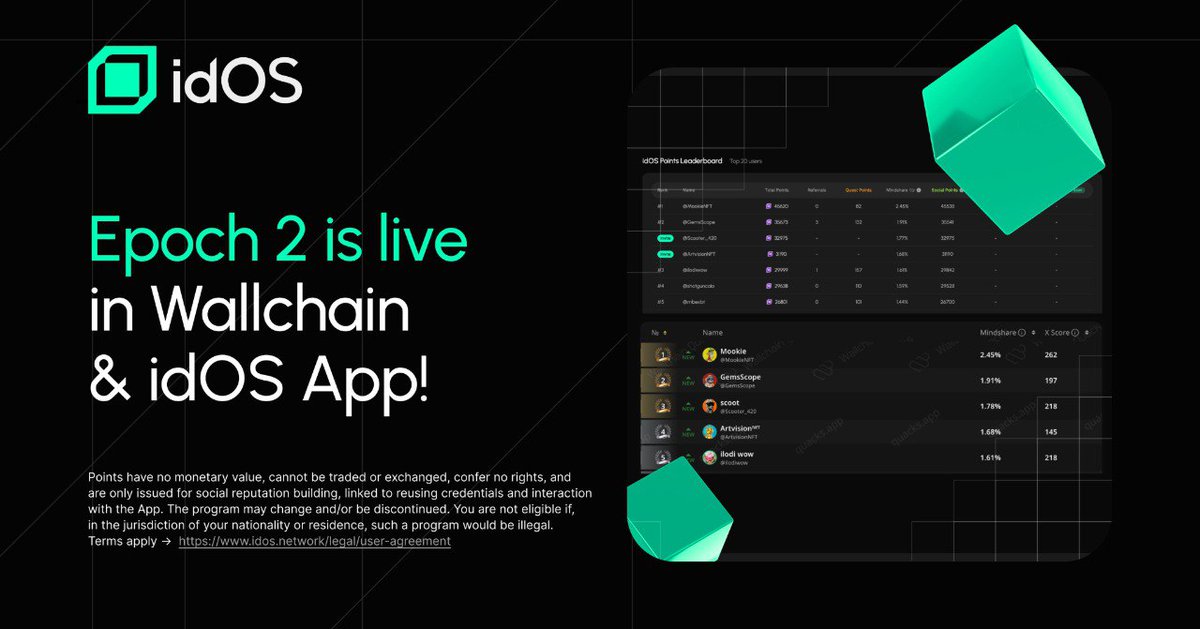
The truth is, KYC sucks But that's because the implementation sucks Which is why @idOS_network built a new KYC framework for a Web3 and Stablecoin powered world -> KYC once -> Store in self custody -> Instantly and securely use it across any application It's really that…

Seal just launched on Sui Mainnet, and builders are already putting it to work. From token-gated content to confidential AI data, here’s how top teams are using Seal to add programmable privacy and access control to their apps 👇
GOOD NIGHT 🌌 if you GN As we move toward a quantum-powered world, security can’t be an afterthought. That’s why @quranium_or built QSafe, the wallet designed to stay ahead of every threat. It’s not just another Web3 wallet, it’s a quantum-secure vault for your digital assets.…

Confidence doesn’t need attention; it generates it Quiet builders don’t compete for spotlight they compete for longevity Invisible winners, patient founders, boring innovators they all share one edge: they trust their process more than public approval That’s the @SCORProtocol…

gidOS KYC isn’t fun. It’s friction. But it’s also what keeps the stablecoin economy alive. Every dollar-backed coin, every on/off-ramp, every DeFi protocol that wants to connect to the real world needs some form of verified identity. The problem? KYC was built for the 90s, not…

🦭 What's the real use of Seal? 🦭 Today, the Seal protocol was finally launched. It's a security layer that will reinforce the Walrus and Sui infrastructure. But how will this happen? Have you ever considered this and how it might impact your @WalrusProtocol and @SuiNetwork…

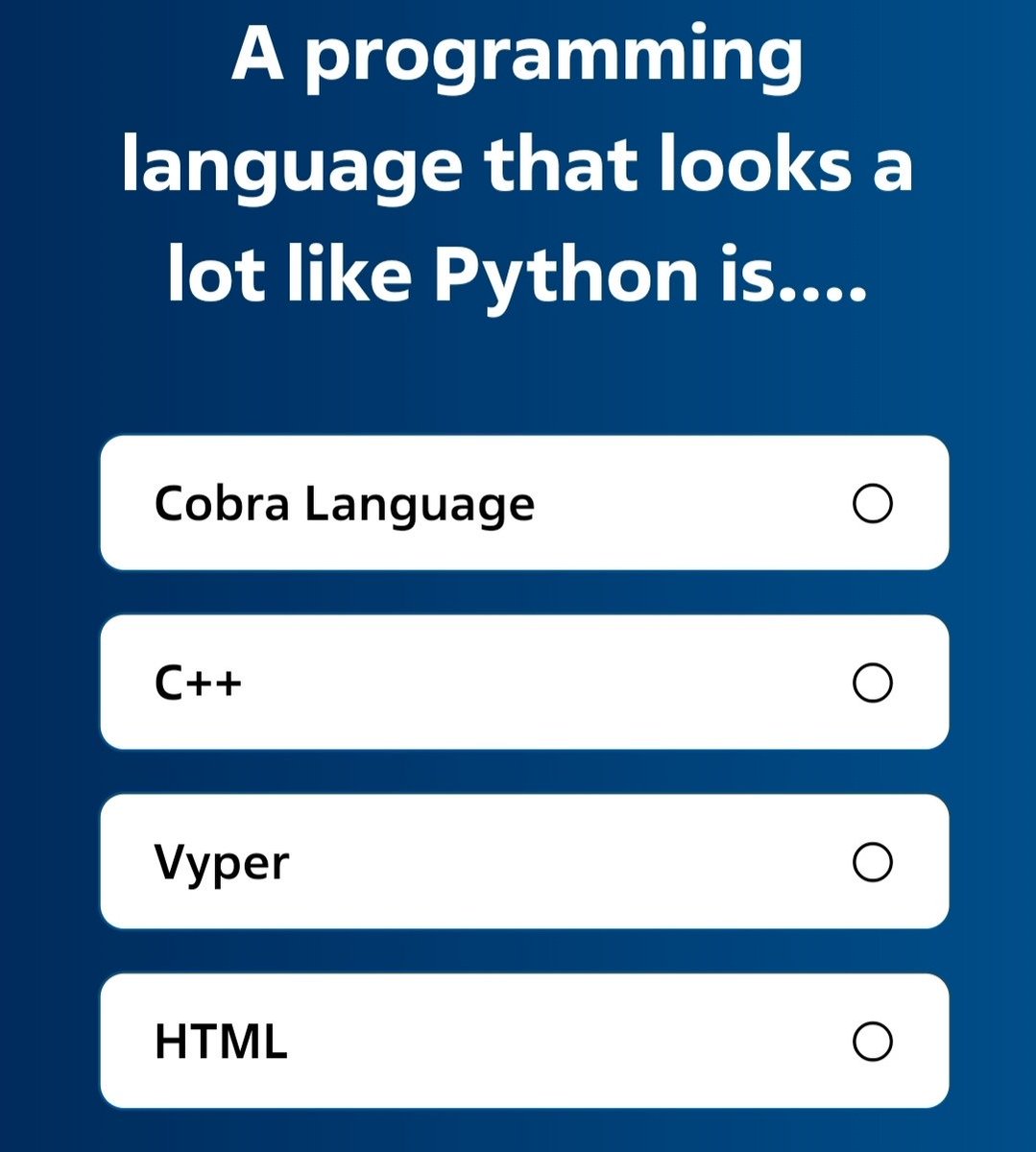
💡 Need a clue on today's quiz? This is a resource limited but yet growing programing language, it's suitable for building secure DeFi protocols such as stable coins and lending platforms.
GOODNIGHT EVERYONE Forget the follower count. The future is about your digital tribe. A tribe that co-creates, governs, and shares in the value they help build. @SCORProtocol is bridging the gap between social influence and on-chain value, creating a new class of programmable…

Sign Protocol's smart contracts are independently audited by leading security firms—ensuring every verification, SBT claim, and on-chain proof is backed by battle-tested infrastructure 🛡️.

50,000 Total #SpurProtocol token Pool Up For Grab 🎉 5 Lucky Users will receive 10k each To participate > Follow @Defipriest_ton & @Spurprotocol > Retweet > Like Selecting winners in 48 hours

🌍 Welcome to Surreal World Assets — where imagination becomes value. @StoryProtocol We’re building a bridge between reality and digital creation, turning virtual ideas into real-world assets powered by #AI, #Blockchain, and #StoryProtocol.
Happy Halloween CT 🎃 While others chase tricks, @SolvProtocol keeps delivering real treats, yield, utility, and blue-chip consistency in BTCFi. 🍬 No costumes here, just real value on-chain. ⚡️

Seal is now live on Mainnet, completing the most powerful stack in Web3. We're now ready to win!
Everyone talks about data privacy in Web3. Our partners? They're shipping it. Here’s how teams are using Walrus for storage + Seal for access control to power encrypted games, AI agents, token-gated content, and more. Let’s dive in 👇

Emerging protocols aim to reduce the trusted setup footprint or eliminate it entirely, boosting security and trustworthiness. #Trustless #SecureProtocols
7 featured participants in 7 days. Day 7. This is our last partner drop but we’re not done yet. Something fun is on the way. @eulerfinance 🧵
Day 7🚀 Secure your connections! When accessing any site, use Hypertext Transfer Protocol Secure (HTTPS) & Virtual Private Networks (VPNs) for encrypted protection. Keep your data safe & prevent cyber attacks. #Cybersecurity #SecureProtocols
Day 6🚀 Use a password manager! Generate & store complex passwords securely. Avoid using your name, birthday or common words as your password. Ensure it comprises uppercase & lowercase letters, numbers and special characters (X@vi3rP@ss!) #CyberSecurityAwareness
Giverep’s blockchain uses secure protocols—no vulnerabilities. #SecureProtocols @Giverep
Wrapped up: Networking Secure Protocols! This is built on all the previous rooms and now includes encryption, tunneling, and secure communications. #CyberSecurity #Networking #SecureProtocols tryhackme.com/room/networkin… #tryhackme via @realtryhackme
Using secure access protocols ensures that data transmitted over the network is encrypted, protecting it from interception or tampering. #SecureProtocols #DataSecurity #AccessControl

Let's ensure we create a document that sets a new standard for clarity, practicality, and impact within the cross-chain space. #CrossChainCollaboration #Web3Whitepaper #SecureProtocols
YouTube video walk through for TryHackMe room Networking Secure Protocols Learn how TLS, SSH, and VPN can secure your network traffic. Part of the new path: Cyber Security 101 youtube.com/watch?v=HJnoFo… #THMCyberSecurity101 #CyberSecurity101 #SecureProtocols #TLS #SSH #VPN…

youtube.com
YouTube
Networking Secure Protocols: TLS, SSH, and VPN in Cyber Security 101...
6/7 🔗 Technological Approach - Shido: Shido integrates advanced encryption techniques and secure protocols to maintain the integrity and confidentiality of data. It focuses on providing a robust security framework for blockchain applications. #Encryption #SecureProtocols
🟧Call for Papers🟧 Deadline: Jun. 14, 2024❄️ “Special Section on the Architectures, Protocols, and Applications for the Future Internet”🍷 IEICE Transactions on Information and Systems, Jun. 2025🍵 ieice.org/eng/s_issue/cf… #CallforPapers #Sensornetworking #secureprotocols

⚔️ Dive into the realm of secure protocols like a knight of the digital round table! Essential for CompTIA Security+ (SY0-601) exam success! 🛡️ #CyberSecurity #CompTIA #SecureProtocols blog.alphaprep.net/the-art-of-arm…
🔒 TLC's ascendancy on Coindcx! Protect your digital assets with Trillioner Wallet's secure protocols! 💳🛡️ #TLC #SecureProtocols
#TeleGuard is setting a new standard in data privacy. With continuous monitoring and updating of secure protocols, we address emerging vulnerabilities to keep your data safe. Download TeleGuard today and experience a new standard in data privacy. #DataPrivacy #SecureProtocols

Unlock the strength of secure protocols with #TeleGuard! We ensure your messages are encrypted and only decipherable by the rightful recipient. Say goodbye to unwelcome access and hello to secure communication. Download now! #SecureProtocols #EndToEndEncryption

Need to share confidential documents with clients? Want to receive files from your remote team? Thru’s secure file transfer ensures that your files remain protected every step of the way. Visit buff.ly/47fVHaO to learn more. #datasecurity #secureprotocols #filetransfer

6/10: ⚙️ Trusted Setup: Zcash, like its predecessors, requires a trusted setup phase for generating zk-SNARKs. Careful execution and secure destruction of parameters are crucial to prevent potential vulnerabilities. #SecureProtocols
Something went wrong.
Something went wrong.
United States Trends
- 1. Dodgers 440K posts
- 2. #WorldSeries 224K posts
- 3. Yamamoto 94.3K posts
- 4. Blue Jays 94.3K posts
- 5. Will Smith 35.1K posts
- 6. Rojas 49.2K posts
- 7. BACK TO BACK 758K posts
- 8. Kershaw 9,926 posts
- 9. Vlad 12.5K posts
- 10. Ohtani 70K posts
- 11. Dave Roberts 8,390 posts
- 12. #Worlds2025 26.7K posts
- 13. Baseball 130K posts
- 14. Jeff Hoffman 2,964 posts
- 15. Auburn 13.3K posts
- 16. Ernie Clement 11.4K posts
- 17. Nike 25.1K posts
- 18. Miggy 7,774 posts
- 19. Andy Pages 3,607 posts
- 20. Dominguez 4,553 posts


































