#securesoftwaredevelopment 搜尋結果
buff.ly/1RDfOjO #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZlF1 #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Secure software development: Bad Software Development #securesoftwaredevelopment #FreeDownload #Free #Giveaway buff.ly/2ndrntw

SAVE THE DATE, 5 February 2026, for the next @GirlCodeNL at @WerkenBijCGI about #SecureSoftwareDevelopment We'll open the event for RSVP's next week. Tip your friends who might be interested. For more info on the program, speakers and location: meetup.com/girlcode/event…

Secure software development: Secure Software Development #securesoftwaredevelopment #FreeDownload #Free #Giveaway buff.ly/2sMP0Zu

Zapraszamy na nasze stoisko podczas @WTHConf Wstai II dowiedz się czym jest Cyberkomponent WOT. Dołącz do nas! #Terytorialsi #secureSoftwareDevelopment #sysOpsDevOps #cyberCrime


Sub-group discussion on #SecureSoftwareDevelopment #SecuringTheHuman by #InfoSecEvangelist(s) #OperationMFU Mae Fah Luang University

buff.ly/1RDfNMX #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZicz #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

buff.ly/1RDfNMV #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZicp #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

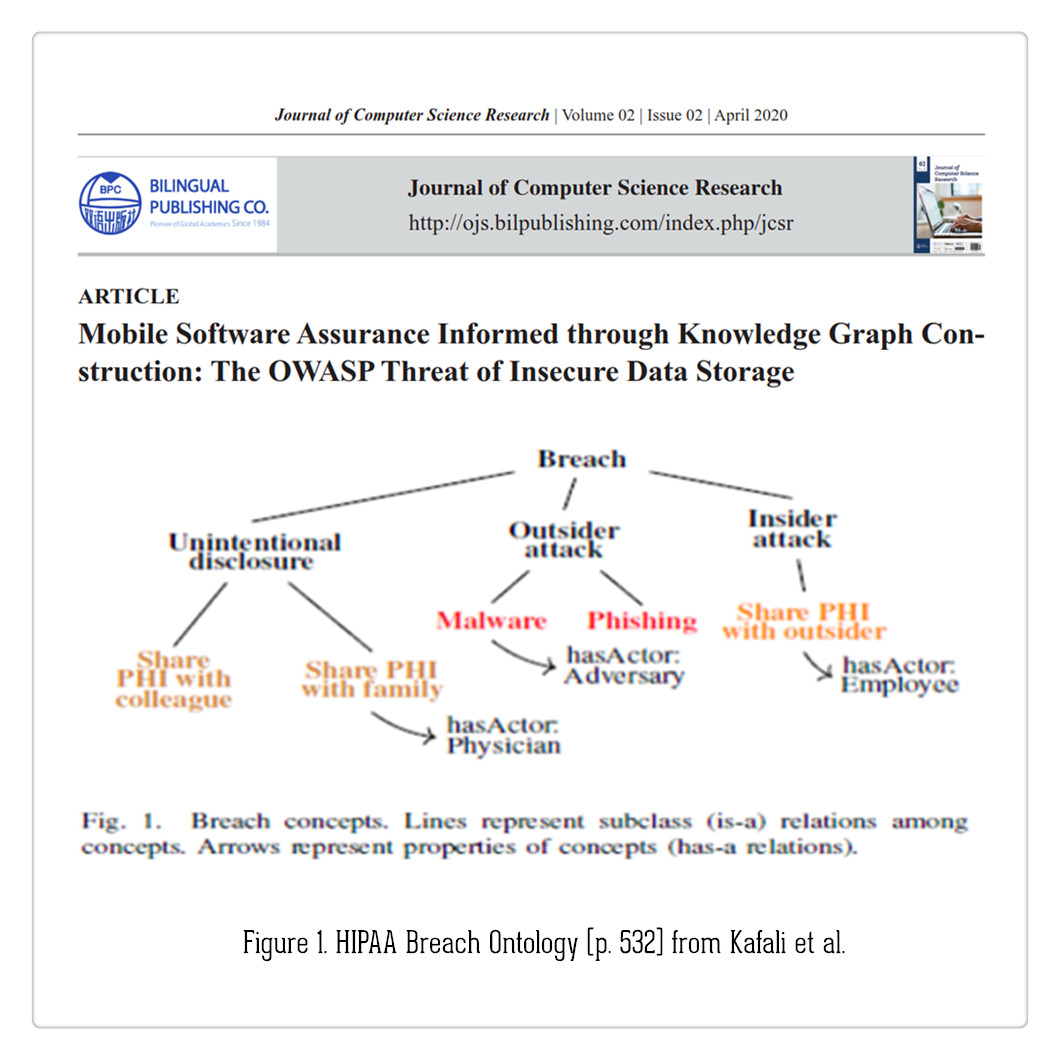
Mobile Software Assurance Informed through Knowledge Graph Construction: The OWASP Threat of Insecure Data Storage #Cybersecurity #Securesoftwaredevelopment #Penetrationtesting #Riskassessment DOI: doi.org/10.30564/jcsr.…
Is the #software you rely on daily developed securely? What does #securesoftwaredevelopment look like? Our CTO Brian Nadzan shares his insights Click here for access: hubs.la/Q01NxlFp0 #alternativeassets #privatemarkets #capitalmarkets #SaaS

Join our SEC Business Webinar on June 23 and register here: r.sec-consult.com/secbusinessweb…. Security Expert Thomas Kerbl will speak about Secure Software Development from the perspective of the Security Requirements Engineer #infosec #securesoftwaredevelopment @Dementophobia

Nasz Cyberkomponent WOT wystawia się na @wthconf.pl. Tutaj znajdziecie więcej info nt Zespołu Działań Cyberprzestrzennych WOT: bit.ly/38C4zcd Dołącz do nas! #Terytorialsi #secureSoftwareDevelopment #sysOpsDevOps #cyberCrime

→ Solutions that enable the hybrid cloud approach will continue to drive this simplification and adoption. This means the hybrid cloud architecture will become the mainstream in larger enterprises. realware.com #DigitalTransformation #securesoftwaredevelopment

Chief Product Officer @BrianRocheBos and CTO & Founder @WeldPond continue their discussion on #AI and #securesoftwaredevelopment. Learn more here: bit.ly/3Hw33ew.
Secure coding produces software that resists cyberattacks from its foundation. Here's how it works to protect you and your data from threats: bit.ly/4oO21xT #coding #onlinesecurity #cybersecurity

An in-depth look at our code hosting security framework that safeguards your code throughout the development workflow. Try it now: tinyurl.com/ykercr7h Learn more: tinyurl.com/y6aadvxh #HuaweiCloud #CodeArts
without safety in execution When we build fast and push features quickly, we must make space for security at the table. During design, during code, during testing, not after deployment. A simple oversight can cost more than money; it can cost trust.
Why a secure software development life cycle is critical for manufacturers bleepingcomputer.com/news/security/… #Security
SAVE THE DATE, 5 February 2026, for the next @GirlCodeNL at @WerkenBijCGI about #SecureSoftwareDevelopment We'll open the event for RSVP's next week. Tip your friends who might be interested. For more info on the program, speakers and location: meetup.com/girlcode/event…

Your app's biggest risk is the code you inherit. Criminals are targeting the #SoftwareSupplyChain with typosquatting & dependency confusion. Don't let a third-party package be your next breach. Get the 4-step framework for supply chain risk management. sprou.tt/1yvL2Jn8pZX
Think of security as just another test in your dev suite. 🧪🔒 It's not just about finding bugs, it's about securing them before they escalate. ➡️ anchore.com/blog/modeling-… #DevSecOps #VulnerabilityScanning #SoftwareSupplyChainSecurity
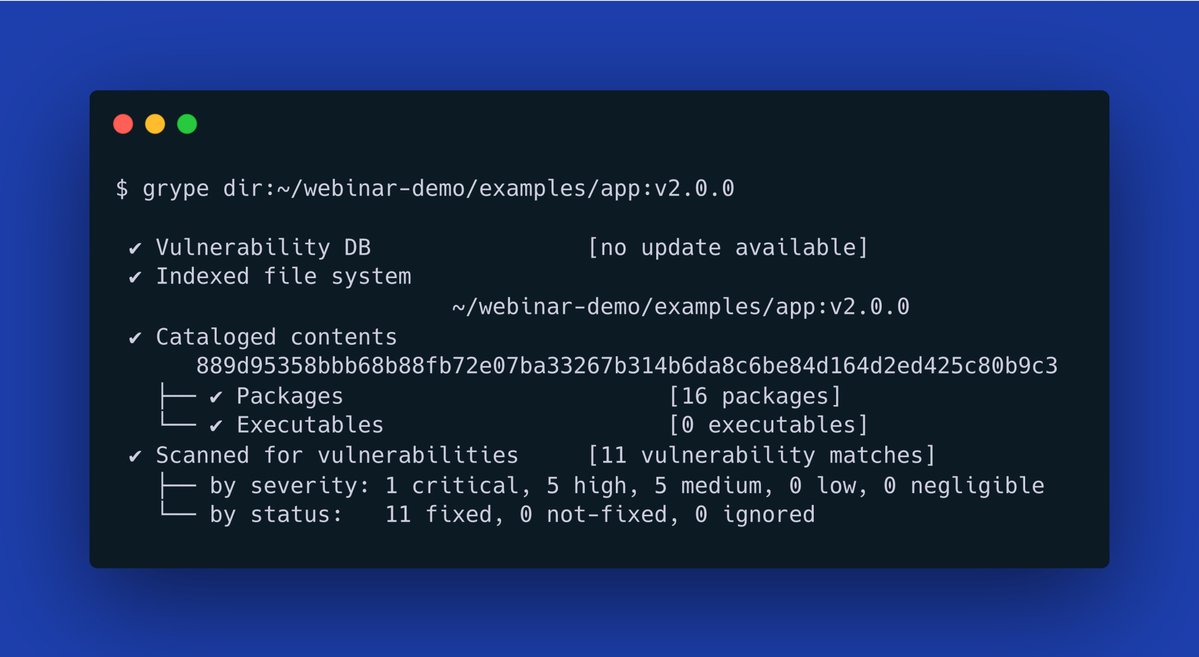
- Pre-launch code audits & formal verification - Post-deployment monitoring with live alerts - AI-powered vulnerability detection (Solidity Shield) - Emergency incident response plans Don't let security be an afterthought. Let us help you build trust from day one.



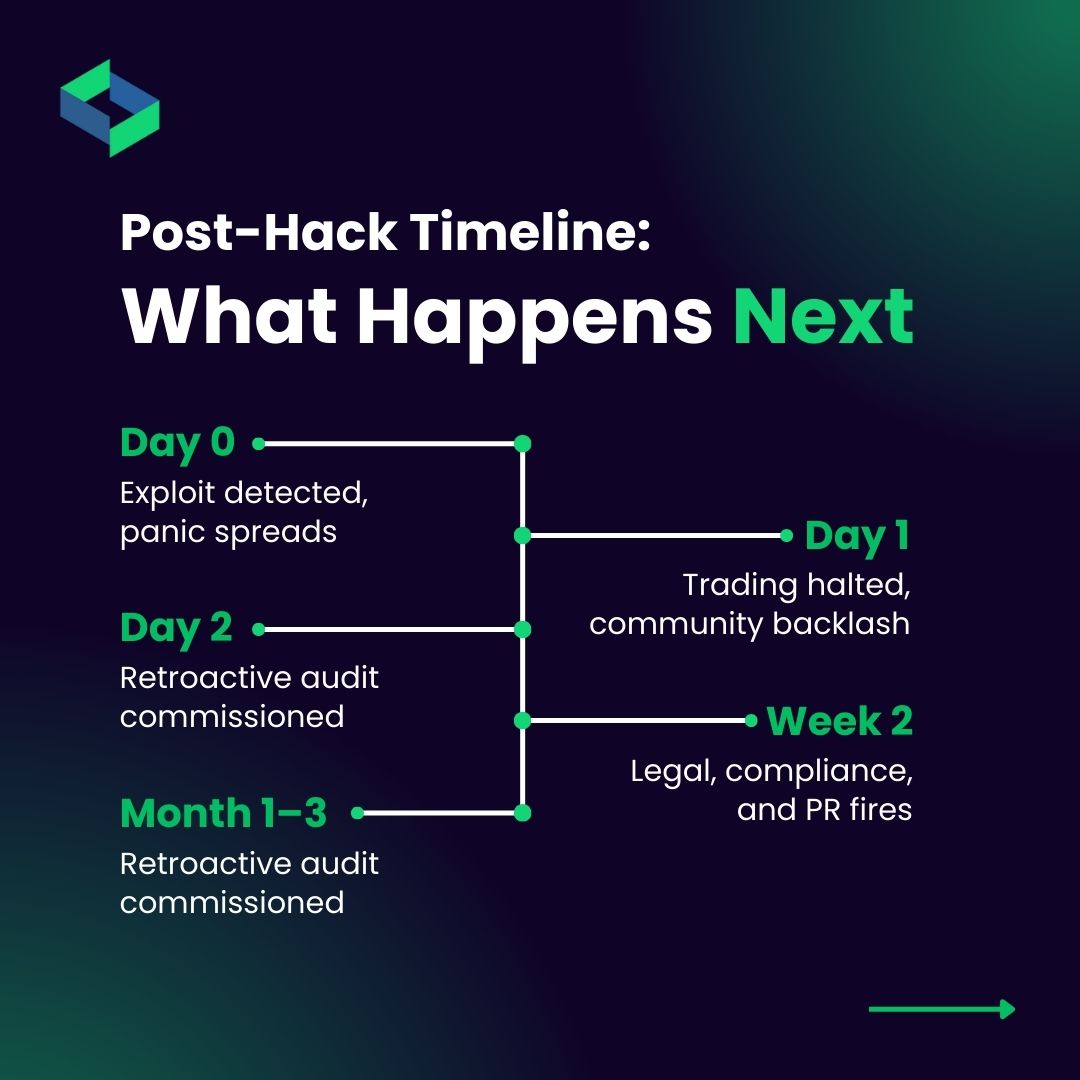
That's not just a bug. That's a business-ending breach. SecuredApp's Hack Prevention Framework helps #Web3 projects protect what truly matters before launch and beyond:




Security can’t be an afterthought — it has to live inside your dev workflow. New blog by Geetha Sharanya Bolla on using GitHub Advanced Security to: ✅ Shift security left ✅ Automate scans & secret checks ✅ Strengthen DevSecOps Read: apexon.com/blog/building-… #DevSecOps…

This vulnerability highlight is critical for framework adoption. Security-first development prevents widespread exploitation of popular frameworks in production.
1/ In software development, also outside Web3, the goal is to make security built-in - make such good frameworks that it's very difficult for any developer to create security issues. If end users and developers can tell themselves if something is secure or not, and this is not…
So I think the issue with developers being skeptical or not following secure coding often starts from the requirements stage. If a feature is needed, it must be clearly defined as a user story with explicit security requirements included. And this starts with scrum masters etc
Why an Application Development Environment Should Be As Secure As Possible #sme #businesstips - businesspartnermagazine.com/application-de…
Im building safecodehq.com and I'm im convinced it will be responsible for the security of thousands developers codebase
Open source. AI-generated code. Third-party components. Software supply chain attacks are up. Are you ready? runsafe.ly/4rqI9Dt

buff.ly/1RDfOjO #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZlF1 #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Zapraszamy na nasze stoisko podczas @WTHConf Wstai II dowiedz się czym jest Cyberkomponent WOT. Dołącz do nas! #Terytorialsi #secureSoftwareDevelopment #sysOpsDevOps #cyberCrime


buff.ly/1MuAxqg #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZlVM #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Mobile Software Assurance Informed through Knowledge Graph Construction: The OWASP Threat of Insecure Data Storage #Cybersecurity #Securesoftwaredevelopment #Penetrationtesting #Riskassessment DOI: doi.org/10.30564/jcsr.…

Nasz Cyberkomponent WOT wystawia się na @wthconf.pl. Tutaj znajdziecie więcej info nt Zespołu Działań Cyberprzestrzennych WOT: bit.ly/38C4zcd Dołącz do nas! #Terytorialsi #secureSoftwareDevelopment #sysOpsDevOps #cyberCrime

SAVE THE DATE, 5 February 2026, for the next @GirlCodeNL at @WerkenBijCGI about #SecureSoftwareDevelopment We'll open the event for RSVP's next week. Tip your friends who might be interested. For more info on the program, speakers and location: meetup.com/girlcode/event…

Is the #software you rely on daily developed securely? What does #securesoftwaredevelopment look like? Our CTO Brian Nadzan shares his insights Click here for access: hubs.la/Q01NxlFp0 #alternativeassets #privatemarkets #capitalmarkets #SaaS

buff.ly/1RDfNMX #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZicz #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Secure software development: Bad Software Development #securesoftwaredevelopment #FreeDownload #Free #Giveaway buff.ly/2ndrntw

Secure software development: Secure Software Development #securesoftwaredevelopment #FreeDownload #Free #Giveaway buff.ly/2sMP0Zu

Developing Secure and Robust Software Solutions bit.ly/459PSKs #SecureSoftwareDevelopment #SecureSoftwareFrameworks #cisin #SoftwareDevelopment #SoftwareDevelopmentTeam

#Veterans, need some upskilling to land that tech job? We have you covered. #CyberSecurityTraining #SecureSoftwareDevelopment

buff.ly/1RDfQs8 #Securesoftwaredevelopment #Quick #Perks #retweet #Strong #library #Dream #Stepbystep #Unpa…

buff.ly/1UtZmsJ #Securesoftwaredevelopment #tellus #Surefire #toolkitTHEWRITER #Selected #Power #Sturdy #wr…

Designing and Developing Secure Software cisin.com/coffee-break/t… #SecureSoftwareDevelopment #SoftwareDevelopment #cisin #HireSoftwareDeveloper #SoftwareDevelopmentSecurity #Cyberattacks #softwaredevelopers

Something went wrong.
Something went wrong.
United States Trends
- 1. The Plasma 27.1K posts
- 2. FINALLY DID IT 500K posts
- 3. #TSTheEndOfAnEra 3,425 posts
- 4. #FanCashDropPromotion N/A
- 5. Good Friday 58.4K posts
- 6. The WET 96.1K posts
- 7. The HYPE 310K posts
- 8. #FridayVibes 4,351 posts
- 9. Smear the Queer 1,938 posts
- 10. Our Lady of Guadalupe 14K posts
- 11. Happy Friyay 1,208 posts
- 12. Lanterns 9,748 posts
- 13. #FridayMotivation 4,170 posts
- 14. #FursuitFriday 12.7K posts
- 15. Chainers N/A
- 16. Pooh 16.6K posts
- 17. RED Friday 2,862 posts
- 18. Tina Peters 95.7K posts
- 19. Premo 1,122 posts
- 20. 21 Savage 25.6K posts








































