#sidechannelattacks search results
Semiconductor Engineering's top blogs this week semiengineering.com/blog-review-ma… #semiEDA #AI #SideChannelAttacks #verification

Recap: Day 2 👾Profiling Side-channel Analysis: From Templates to Deep Learning by @StjepanPicek_ 🖥️Machine learning-based SCA with multiple assignments like➡️Extracting the cipher key etc. | 💡Introduction to Deep Learning-based SCA #hw_ioUSA2022 #sidechannelattacks

Letzte Woche diskutierten Wissenschaftler von @BSI_Bund, @cirbw, @ZITiS_de, @CybAgBund über neue Gefahren und Möglichkeiten für #SideChannelAttacks und die künftigen Entwicklungen der #Quantensensorik und den notwendigen Schutz. #Cybersicherheit #Cybersecurity #Quantentechnologie

🖥️Learn how to profile a device using templates & advanced #machinelearning techniques⚙️ 💡In this training by Stjepan @StjepanPicek_ discover, how to write your own code to mount profiling SCA ✅Early bird ends soon➡️bit.ly/3sRDiPD #hw_ioUSA2022 #sidechannelattacks

💻Perform #sidechannelattacks🔌 using fault injection⚡#EMFI on real-world datasets on real hardware aiming at the secret key extraction from this training by Lejla @lejla_batina & Łukasz 🎟️Get your training ticket here➡️ bit.ly/3QWzx4Z #hw_ioNL2022 #embedded

At my RBTC Defense Against the Dark Arts demo, we explored timing side-channel attacks. With the help of an audience volunteer, we cracked a keypad safe. A huge thank you to everyone who attended, helped setup, and asked great questions! #HardwareHacking #SideChannelAttacks

Montag ist bei uns Podcast-Tag! Neu im Security-Podcast, sogar mit nachgereichtem Anhang wegen #PACMAN: #SidechannelAttacks. Hört rein, denn noch ist nicht alles verloren: innoq.com/de/podcast/021…

🔒 Join us for Eliot's Talk on Side Channel Attacks! Exciting things ahead this Wednesday in C27 with a great talk from Eliot on Side Channel Attacks planned! #ENUSEC #Cybersecurity #SideChannelAttacks #TechTalk #PilgrimsEdinburgh #StudentSocials #SaveTheDate

#mdpientropy Information Theoretic Security for Broadcasting of Two Encrypted Sources under Side-Channel Attacks mdpi.com/1099-4300/21/8… #informationtheoreticsecurity #sidechannelattacks #Shannon #ciphersystem #strong #conversetheorem

Check out this latest blog as we define #SideChannelAttacks, what they are not and where they could impact your #ActiveDirectory #security. ow.ly/uAnx30mH0F9 #threatdetection #cybersecurity

Google engineer: Devs must adopt new methods in a post-Spectre world go.tz.nl/RvHKPy #Security #malware #sidechannelattacks #Spectre @techzineeu

#mdpientropy Information Theoretic Security for Shannon Cipher System under Side-Channel Attacks mdpi.com/1099-4300/21/5… #informationtheoreticsecurity; #sidechannelattacks; Shannon cipher system; one helper source coding problem; strong converse theorem

Researchers discover new side-channel attack that works against #Intel CPUs.Affects Core i7-6700, Core i7-7700 & Core i9-10980XE.techspot.com/news/98436-res… #Sidechannelattacks #Vulnerabilities #Meltdown, #Spectre, Fallout and Zombieload.

Securing smart infrastructure 5th @CENSIS121 Tech Summit case study. #OwenLo @EdinburghNapier presents a project with @Keysight_UK to target better security for IoT devices, 8 Nov, Glasgow #CyberSecurity #SideChannelAttacks #CENSIS18 ow.ly/hcZj30lZFYv

Think air-gapped = safe? Meet AirHopper, BitWhisper & GSMem — side-channel attacks that breach "offline" systems using light, heat, sound & EM waves. Isolation ≠ Immunity. #CyberSecurity #HackingMyths #SideChannelAttacks

Intel, ARM, IBM, AMD Processors Vulnerable to New Side-Channel Attacks thehackernews.com/2020/08/foresh… #infosec #cybersec #sidechannelattacks

For all those researchers working in open hardware and/or security/safety evaluation of hardware, there is an open position in our institute for Senior Researcher: boe.es/boe/dias/2024/… See "Tribunal 12" #RISCV #SideChannelAttacks Spread the word!!!
Researchers explore the effectiveness of Intel's SGX update mechanisms in preventing side-channel attacks on real-world deployments, finding severe security compromises in SGX-backed blockchain and DRM software. #SGXFail #SideChannelAttacks
🔒 New research in Cryptography analyzes Correlation Power Analysis (CPA) attacks on the latest Cortex M4 Kyber implementation using Plantard arithmetic. 🔗 Read more: mdpi.com/2410-387X/9/1/… @ComSciMath_Mdpi #PostQuantum #Kyber #SideChannelAttacks

5 strategies to mitigate side channel attacks on cryptocurrency hardware wallets #cryptocurrencyhardwarewallets #sidechannelattacks dlvr.it/Sty3S3
Starting development on RAM Anomaly Detector, a lightweight Python tool to monitor memory patterns and detect potential RAMBO attack indicators on air-gapped systems. Early focus: Baseline profiling and threshold alerts. #CyberSecurity #SideChannelAttacks
Third in the session was Zhang et al.'s "Demystifying ML-Assisted Side-Channel Analysis Framework: A Case of Image Reconstruction" which analyzes cache activities using an autoencoder to reveal image reconstruction limits. (acsac.org/2024/program/f…) 4/6 #SideChannelAttacks #ML

Then followed Lindemann's "Faking deduplication to prevent timing side-channel attacks on memory deduplication," showcasing a novel approach to secure #MemoryDeduplication without sacrificing efficiency. (acsac.org/2024/program/f…) 3/6 #SideChannelAttacks #CyberSecurity

📢 New Article Published in Cryptography Multi-Line Prefetch Covert Channel with Huge Pages 📖 Read more: mdpi.com/2410-387X/9/3/… #SideChannelAttacks #CovertChannels #Microarchitecture

Think air-gapped = safe? Meet AirHopper, BitWhisper & GSMem — side-channel attacks that breach "offline" systems using light, heat, sound & EM waves. Isolation ≠ Immunity. #CyberSecurity #HackingMyths #SideChannelAttacks

Cyber Daily Report Blog Post! Title: Emerging Trends and Key Challenges in Side-Channel Attacks Author: Amir Hassanpour Zarghani Editor: Windhya Rankothge Link: cyberdailyreport.com/blog/98 #CyberSecurity #SideChannelAttacks #AIinSecurity #PostQuantumCryptography #IoTSecurity
⏪ The past 5 years have shown how side channels have become central to security research. 🎥 A recap of #hw_ioNL2024 where @DanielGenkin discussed emerging threats and the future of speculative execution attacks. 👉 youtu.be/uXWZB-EM6wI?si… #sidechannelattacks #GoFetchattack

youtube.com
YouTube
Hardwear.io NL 2024: Side Channel Attacks: Lessons Learned Or...
Great to see so much interest in the @AgileAnalog security related #analogIP solutions. Why not have a look again at our post which gives examples of how our customizable #voltageglitchdetector can help protect against #sidechannelattacks. agileanalog.com/blog-posts/lev…
agileanalog.com
Leveraging analog IP for protection from side-channel attacks
Examples of applications that could be impacted by voltage side-channel attacks and explains how agileVGLITCH, our voltage glitch detection solution, can help offer protection.
🔒 New research in Cryptography analyzes Correlation Power Analysis (CPA) attacks on the latest Cortex M4 Kyber implementation using Plantard arithmetic. 🔗 Read more: mdpi.com/2410-387X/9/1/… @ComSciMath_Mdpi #PostQuantum #Kyber #SideChannelAttacks

What a journey! A huge thank you to my co-authors and collaborators for their invaluable contributions! #ComputerSecurity #SideChannelAttacks #ECC #NeuralNetworks #LSTM #arXiv #UniMi
🔒 Removing Code Clues to Secure Hardware Components 🔗 tinyurl.com/28cesx6o #hardwaresecurity #microarchitecturehacks #sidechannelattacks #securebydesign 💬 A new approach to prevent hackers from exploiting microarchitectural side attacks. [...]
somuchinfo.com
Removing Code Clues to Secure Hardware Components
Enhance hardware security with the 'Oreo' method, a new approach that removes code clues to prevent hackers from exploiting microarchitectural side attacks. By adding a masked address space between...
I never understood how grapheneOS wasn't an oxymoron. Secure, private OS on Google hardware 🙄 #sidechannelattacks
How Side Channel Attacks Work - A technical deep dive. youtu.be/TdjXs4HReHM?si… Equip yourself with the knowledge to identify and respond to potential threats effectively. #CyberSecurity #SideChannelAttacks #DataProtection #CyberDefense #SecurityAwareness
youtube.com
YouTube
How Side Channel Attacks Work - A technical deep dive.
5/13 New threats like TPUXtract show how AI models can be stolen with high accuracy, posing risks to AI intellectual property. #AISecurity #SideChannelAttacks 🚨
At my RBTC Defense Against the Dark Arts demo, we explored timing side-channel attacks. With the help of an audience volunteer, we cracked a keypad safe. A huge thank you to everyone who attended, helped setup, and asked great questions! #HardwareHacking #SideChannelAttacks

At #hw_ioNL2024, @DanielGenkin spoke about iLeakage, revealing how speculative execution attacks still threaten browser isolation primitives despite ongoing mitigations. YouTube Link: youtu.be/uXWZB-EM6wI?si… #sidechannelattacks #hardware #software

youtube.com
YouTube
Hardwear.io NL 2024: Side Channel Attacks: Lessons Learned Or...
📣 Call for reading: "Locating Side Channel Leakage in Time through Matched Filters" by Alessandro Barenghi, Gioele Falcetti and Gerardo Pelosi 👉 Find more at the following link: mdpi.com/2410-387X/6/2/… #ComputerSecurity #SideChannelAttacks

Our @AgileAnalog October blog post is based around the threat of voltage #sidechannelattacks and explains how our agileVGLITCH voltage glitch detector solution can help. agileanalog.com/blog-posts/lev… #analogIP
agileanalog.com
Leveraging analog IP for protection from side-channel attacks
Examples of applications that could be impacted by voltage side-channel attacks and explains how agileVGLITCH, our voltage glitch detection solution, can help offer protection.
Breaking News: New Side Channel Attack called Spectre Bypass Hits CPUs 🛡️💻 youtu.be/E7RICnk3gSg?si… #CyberSecurity #SideChannelAttacks #DataProtection #CyberDefense #SecurityAwarenes
youtube.com
YouTube
Breaking News: New Side Channel Attack called Spectre Bypass Hits...
Bare Metal Forensics overview @billatnapier @TheCyberAcademy @_enusec_ #sidechannelattacks @owenatnapier @Keysight

#SideChannelAttacks #CPUVulnerabilities #CybersecurityThreats #ModernCPUs #SecurityBreach #DataLeaks #VulnerabilityAlert #TechSecurity #CPUHacks #CyberThreats #TechSafety #DigitalSecurity #DigitalPrivacy #SecureComputing #kartheekchanda #ersegmentsolutionspvtltd #ersegment

Interesting Approach to combine ML with SCA #CHES2018 #MachineLearning #sidechannelattacks #deeplearning

🖥️Learn how to profile a device using templates & advanced #machinelearning techniques⚙️ 💡In this training by Stjepan @StjepanPicek_ discover, how to write your own code to mount profiling SCA ✅Early bird ends soon➡️bit.ly/3sRDiPD #hw_ioUSA2022 #sidechannelattacks

New #cryptographic method, 'rekeying,' developed to counter #sidechannelattacks, enhancing #cybersecurity at <1/10th the cost. Check it👉sj.jst.go.jp/news/202403/n0…

💻Perform #sidechannelattacks🔌 using fault injection⚡#EMFI on real-world datasets on real hardware aiming at the secret key extraction from this training by Lejla @lejla_batina & Łukasz 🎟️Get your training ticket here➡️ bit.ly/3QWzx4Z #hw_ioNL2022 #embedded

Recap: Day 2 👾Profiling Side-channel Analysis: From Templates to Deep Learning by @StjepanPicek_ 🖥️Machine learning-based SCA with multiple assignments like➡️Extracting the cipher key etc. | 💡Introduction to Deep Learning-based SCA #hw_ioUSA2022 #sidechannelattacks

Hack-proof RFID chips are here #RFIDchip #impossibletohack #sidechannelattacks innovationtoronto.com/2016/02/hack-p…

Semiconductor Engineering's Top Blogs Of The Week semiengineering.com/blog-review-ja… #quantumcompouting #10nm @intel #sidechannelattacks #semiEDA

Growing IoT security risks semiengineering.com/iot-security-r… #sidechannelattacks #botnets #IoTsecurity #ransomware

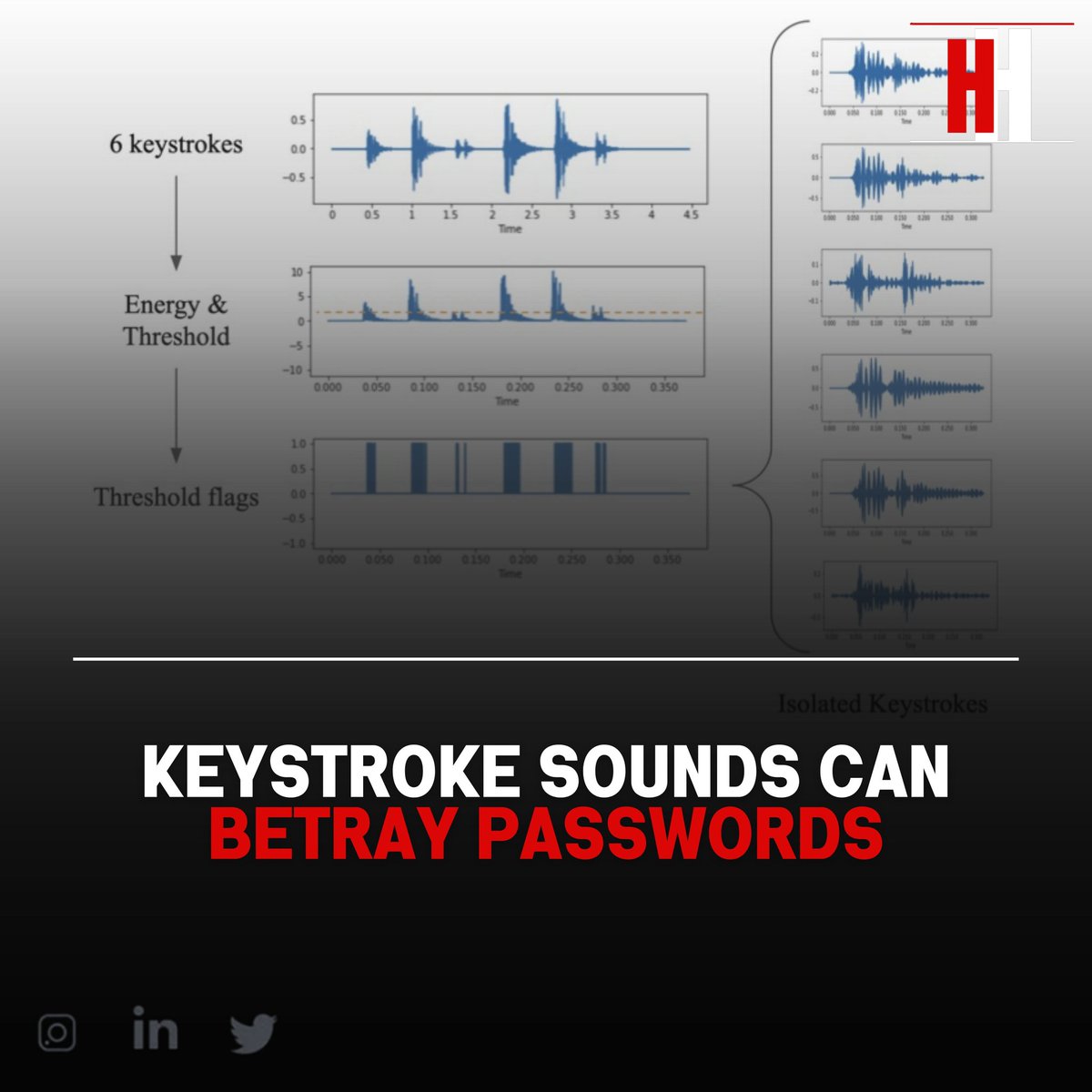
Researchers from UK universities demonstrate that laptop keystroke sounds can be used to accurately obtain sensitive user data, including passwords, through side-channel attacks. These attacks exploit the acoustic emanations of keyboards. #KeystrokeSounds #SideChannelAttacks
Check out this latest blog as we define #SideChannelAttacks, what they are not and where they could impact your #ActiveDirectory #security. ow.ly/uAnx30mH0F9 #threatdetection #cybersecurity

Semiconductor Engineering's top blogs this week semiengineering.com/blog-review-ma… #semiEDA #AI #SideChannelAttacks #verification

Securing smart infrastructure 5th @CENSIS121 Tech Summit case study. #OwenLo @EdinburghNapier presents a project with @Keysight_UK to target better security for IoT devices, 8 Nov, Glasgow #CyberSecurity #SideChannelAttacks #CENSIS18 ow.ly/hcZj30lZFYv

💡If you wish to learn in-depth about deep-learning based side-channel analysis then grab your ticket for the training by Stjepan to upskill➡️bit.ly/3sRDiPD #hw_ioUSA2022 #hardwaresecurity #sidechannelattacks #deeplearning

A device is only as secure as its weakest component semiengineering.com/side-channel-a… #SideChannelAttacks #Hacking #IoT #DPA #DFA #security

Read full paper here ➡️tches.iacr.org/index.php/TCHE… #sidechannelattacks #cybersecurity #microarchitecture @IACR_News

Google engineer: Devs must adopt new methods in a post-Spectre world go.tz.nl/RvHKPy #Security #malware #sidechannelattacks #Spectre @techzineeu

Something went wrong.
Something went wrong.
United States Trends
- 1. Justin Fields 9,454 posts
- 2. #FinallyOverIt 2,004 posts
- 3. Jets 67.8K posts
- 4. Patriots 146K posts
- 5. Drake Maye 19.6K posts
- 6. Jalen Johnson 6,217 posts
- 7. Henderson 21.6K posts
- 8. Summer Walker 10.7K posts
- 9. 5sos 18.4K posts
- 10. Judge 190K posts
- 11. AD Mitchell 2,315 posts
- 12. Pats 14.3K posts
- 13. #criticalrolespoilers 2,564 posts
- 14. 1-800 Heartbreak N/A
- 15. Diggs 10.5K posts
- 16. Cal Raleigh 7,635 posts
- 17. Santana 13.8K posts
- 18. #GreysAnatomy 2,107 posts
- 19. #zzzSpecialProgram 1,158 posts
- 20. #TNFonPrime 3,429 posts





































