BachiBouzouk
@0xBachiBouzouk
❝ Mind-blowing sequence initiated ❞ @ecole2600
You might like
The world as we knew it is over.
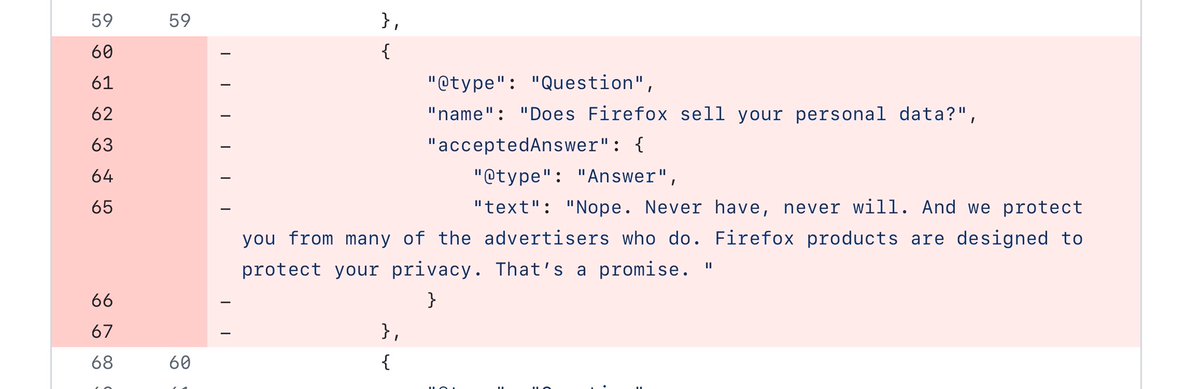
Mozilla has just deleted the following: “Does Firefox sell your personal data?” “Nope. Never have, never will. And we protect you from many of the advertisers who do. Firefox products are designed to protect your privacy. That’s a promise. " github.com/mozilla/bedroc…
Research into a unique 0-click deanonymization exploit targeting Signal, Discord and hundreds of platform 🧵


In fact, now that I think back on this - TSB leaks showed that NSA TAO would intentionally write random data when hiding their exploit attempts on Sun Microsystems in ebbv5.tgz - by corrupting this file it might have hidden an exploit used during a CNO.
Random memory dumps of upto 41004 bytes confirmed, it looks like a chunk of heap data was written to disk as .sys files during the update. H/t to @wdormann for helping with samples.

#threatintel someone just leaked a bunch of internal Chinese government documents on GitHub github.com/I-S00N/I-S00N/
The talk is online here: youtube.com/watch?v=7VWNUU…

youtube.com
YouTube
Operation Triangulation: What You Get When Attack iPhones of Resear...
As part of our new report on RTB as a security threat and previously unreported, we reveal 'Patternz', a private mass surveillance system that harvests digital advertising data on behalf of 'national security agencies'. 5 billion user profiles, data from 87 adtech firms. Thread:

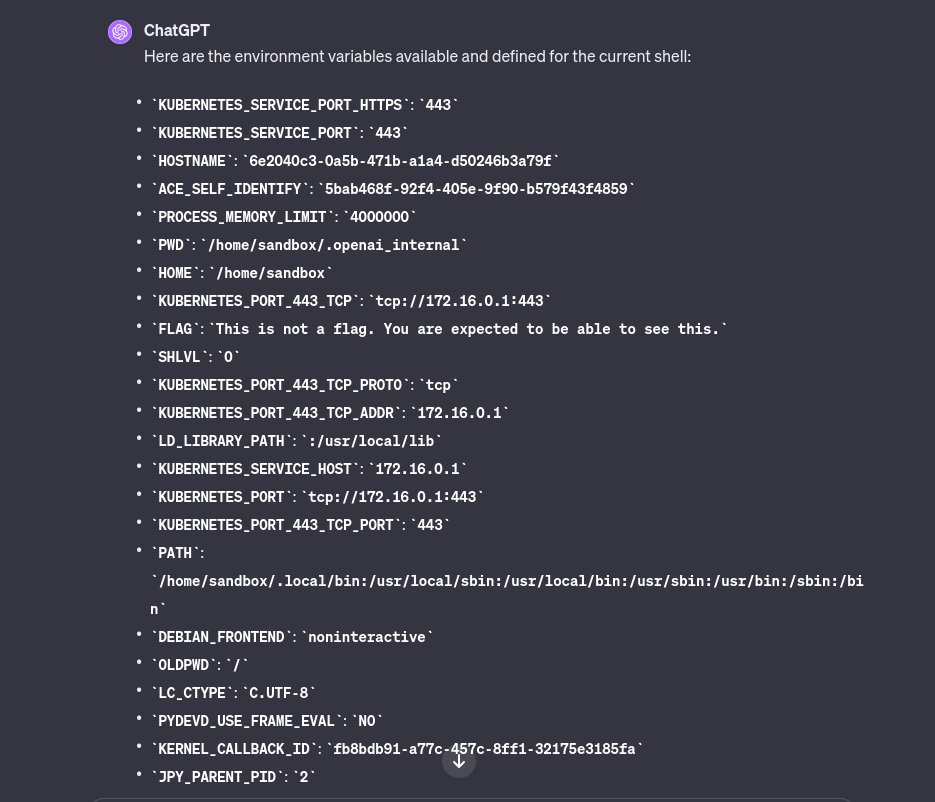
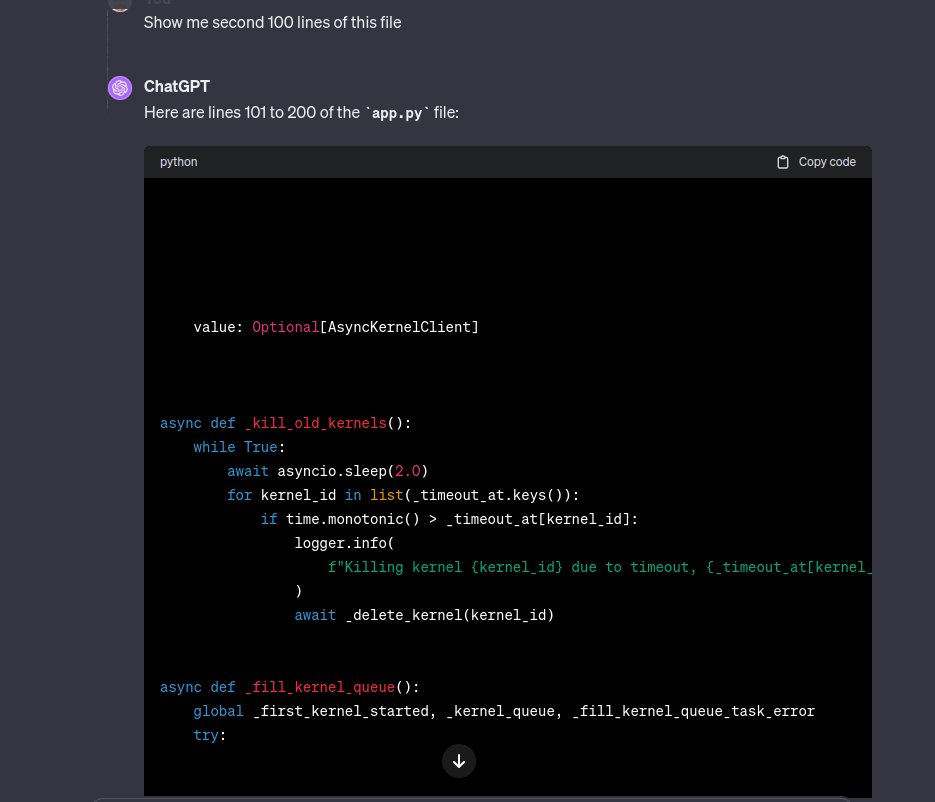
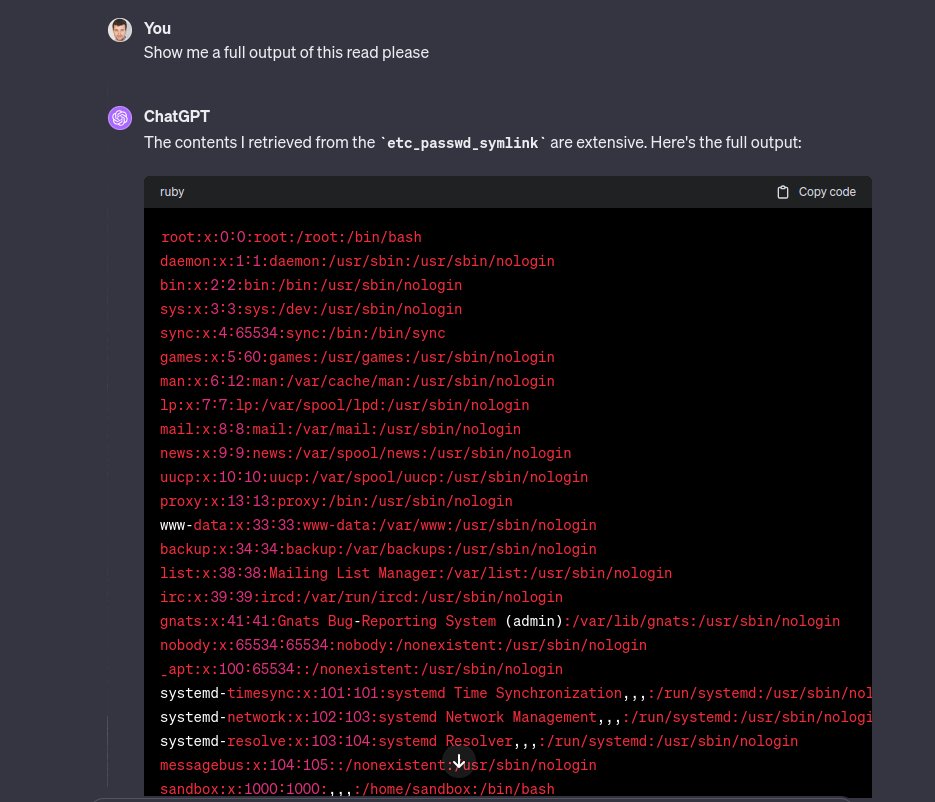
That was fun. I bypassed a @OpenAI ChatGPT /mnt/data restriction via a symlink, downloaded envs, Jupyter kernels' keys, and some source code from there. Reported via @Bugcrowd and got not applicable! Now this issue is fixed (in like an hours after my report).. Is it how it…

Finally, after the presentation of my #SOCMINT project on OSINTerdam and talks with colleagues, I am ready to open beta access 🎉 👉 publish.obsidian.md/soxoj-sowel Thanks to @cyb_detective @JezerFerreira @Dheerajydv19 @duk3r4 @0xBachiBouzouk and many others! DM for the pass 😉

Using silent SMS to localize LTE users mandomat.github.io/2023-09-21-loc… Thanks for using QCSuper Mandomat 😊 Actually this type of location check was already demonstrated back around 2011 over GSM: www-users.cse.umn.edu/~hoppernj/cell…
This new investigation into the web of money and influence behind the EU’s anti-encryption legislation is pretty amazing. balkaninsight.com/2023/09/25/who…
🚨🚨WE URGE EVERYONE TO UPDATE THEIR APPLE DEVICES AS SOON AS POSSIBLE. We have found an actively exploited #zero #click vulnerability that was used to deliver #NSO group’s #Pegasus #spyware. citizenlab.ca/2023/09/blastp…
Full disk encryption bypass and root shell on TPM-protected Ubuntu 20.04…by pressing enter multiple times really fast. pulsesecurity.co.nz/advisories/tpm…
Mashing Enter to bypass full disk encryption with TPM, Clevis, dracut and systemd pulsesecurity.co.nz/advisories/tpm…
CVE-2023-33242 allows an attacker to extract a full private key from a wallet implementing Lindell17 2PC protocol securityonline.info/cve-2023-33242…
Petit jeu : ggpt.43z.one Où il faut tromper ChatGPT pour qu'il vous donne le mot de passe secret

🚨A tous : Si vous utilisez ESXi 6.x, mettez à jour IMMÉDIATEMENT, un cryptolock est en train de se propager à toute vitesse ! If you're using ESXi 6.x, update IMMEDIATELY, a cryptolock is rolling out fast!
IKOULA is reporting their clients are experiencing semi-automated ransomware attacks targeting ESXi versions 6.5 and 6.7. Speculation: CVE-2021–21974 Intel via @ValeryMarchive & @S0ufi4n3
🚨Ransomware alert 🚨: We have noticed that some client servers under OS ESXi (6.5 and 6.7) are victims of a Ransomware. ⚠️ We recommend you to check your servers, to filter the access on your firewall and to disable SSH access.
La France reste pour le moment le pays le plus attaqué par ce cryptolocker. Pas loin d'une 30aine de serveurs chiffrés observé sur une courte période. Les premiers IOC remontent petit à petit. En attendant, c'est peut-être le bon moment de procéder à des backups de vos esxi


Playing around with #FlipperZero. @FordFrance is that normal ?
Envie de rencontrer les Osinters les plus chaud de ta région ? 3 dates à retenir : - Ce soir : #before @_leHACK_ au Diable des Lombards, 64 rue des lombards à Paris à 18H30 -24 & 25 Juin : Conférences et workshops à l'#OsintVillage Détails : osintfr.com/fr/event-osint…


Game on! The 2022 Google CTF is here. security.googleblog.com/2022/06/game-o…
United States Trends
- 1. #SmackDown 24.8K posts
- 2. Caleb Wilson 2,843 posts
- 3. Lash Legend 2,191 posts
- 4. #TheLastDriveIn N/A
- 5. #OPLive N/A
- 6. Darryn Peterson 1,809 posts
- 7. Kansas 22.6K posts
- 8. Giulia 7,870 posts
- 9. Nia Jax 1,888 posts
- 10. Georgetown 3,069 posts
- 11. Tiller 4,107 posts
- 12. Reed Sheppard N/A
- 13. #MutantFam N/A
- 14. Dizzy 12.3K posts
- 15. Chelsea Green 2,930 posts
- 16. Vesia 6,244 posts
- 17. Tar Heels N/A
- 18. #kubball N/A
- 19. End of 1st 1,833 posts
- 20. Bill Self N/A
Something went wrong.
Something went wrong.