A hacker clicked a Google ad. They thought they were grabbing a tool to help their ops. Instead, they installed Huntress on their own machine. 👀 And just like that—we got a front-row seat.

We have a chat service that works over DNS so you can LLM on a flight without paying " dig @ch.at "what is golang" TXT +short"
Okta chained with Azure with auto MFA subscription for Okta and frame-buster bypass to perform Bitb ! Evilginx is really nice to setup custom phishing campaign whatever the environment is... Phishlet available here : github.com/OtterHacker/Ok…
An excellent, in-depth malware analysis article. Refreshing depth and clarity from @cyb3rjerry c-b.io/2025-06-29+-+S… Demonstrably understands Yara's strengths and weaknesses. Take note @cyb3rops.
oh no 🟥 CVE-2025-32463, CVSS: 9.3 (#Critical) #Sudo version 1.9.14 to 1.9.17 #Vulnerability allows local users to gain root access via the --chroot option due to improper handling of /etc/nsswitch.conf. #CyberSecurity #CVE #PrivilegeEscalation openwall.com/lists/oss-secu…

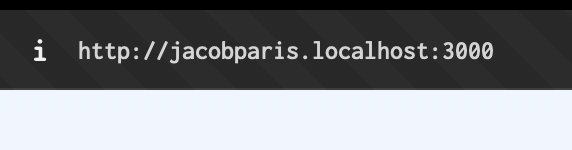
TIL localhost can have subdomains
We've uploaded our beginner .NET malware analysis stream where we analyzed DCRat with dnSpy. Enjoy!

DLL injection fundamental Part 1 systemweakness.com/dll-injection-… Part 2 systemweakness.com/dll-injection-… Part 3 systemweakness.com/dll-injection-…
BREAKING: MIT just completed the first brain scan study of ChatGPT users & the results are terrifying. Turns out, AI isn't making us more productive. It's making us cognitively bankrupt. Here's what 4 months of data revealed: (hint: we've been measuring productivity all wrong)
I'm starting another series - Buffer Overflows in the Modern Era. I'll go over the basics of using a debugger all the way to successfully achieving a buffer overflow exploit on Windows 11 24H2, using ROP gadgets and bypassing ASLR, etc. Here's part 1! g3tsyst3m.github.io/binary%20explo…
I like to bypass XSS filters and sanitizers, so I keep forgetting to test for CSS exfiltration when I have HTML injection. This reminded me of the sic tool by @d0nutptr from a Singapore LHE, but there's also a cool list from @PortSwigger 👇 github.com/PortSwigger/cs…
Learning Active Directory Certificate Service hacking-- with @Shikata! Starting with ESC8 using unauthenticated PetitPotam & Responder, we relay hashes to CA to get a certificate as the domain controller. This is the first video in an ADCS mini-series 😜 youtu.be/tYxJMr8jAgo

null pointer was the culprit that took down google 😭

👀 We have also released a paper which really goes into the nitty-gritty for those who are interested 🕵️♀️: redteam-pentesting.de/publications/2… For those that only need a short overview, here's our advisory 🚨: redteam-pentesting.de/advisories/rt-…
Technical analysis of CVE-2025-31201 blog.epsilon-sec.com/cve-2025-31201…
Rumour has it that Jonas Lykkegaard's self-delete technique doesn't work on Windows 11 anymore. Well, the original proof of concept (PoC) does not, but slight modifications bring this technique back to Win11!😎 With #RustPack, you can easily generate self-deleting executables or…
🚀 We just released my research on BadSuccessor - a new unpatched Active Directory privilege escalation vulnerability It allows compromising any user in AD, it works with the default config, and.. Microsoft currently won't fix it 🤷♂️ Read Here - akamai.com/blog/security-…

What if you skipped VirtualAlloc, skipped WriteProcessMemory and still got code execution? We explored process injection using nothing but thread context. Full write-up + PoCs: blog.fndsec.net/2025/05/16/the…
Yearly blog post just dropped: Control Flow Hijacking via Data Pointers 🐸 Showcasing how to find your own in Binary Ninja, how to weaponize and write a shellcode stub etc. Hopefully people find it useful :) legacyy.xyz/defenseevasion…
United States Trends
- 1. #DWTS 22.7K posts
- 2. Carrie Ann 2,694 posts
- 3. Alix 7,070 posts
- 4. Anthony Black 1,437 posts
- 5. Dylan 31K posts
- 6. Elaine 31K posts
- 7. Robert 92.9K posts
- 8. Jalen Johnson 3,443 posts
- 9. #WWENXT 4,788 posts
- 10. Daniella 2,385 posts
- 11. Wizards 7,694 posts
- 12. Godzilla 29.5K posts
- 13. Brown 160K posts
- 14. Hazel 9,944 posts
- 15. Kingston Flemings N/A
- 16. #DancingWithTheStars N/A
- 17. CJ McCollum N/A
- 18. Bruce Pearl N/A
- 19. #NXTGoldRush 4,164 posts
- 20. Joey Galloway 1,557 posts
Something went wrong.
Something went wrong.