serial-coder (Phuwanai Thummavet)
@0x_serial_coder
Smart Contract Auditor | 🚨 DM for Private Audits 🚨
คุณอาจชื่นชอบ
Thanks to @agfviggiano and @SizeCredit You created an amazing project with a solid codebase!
That’s a wrap on our @cantinaxyz comp 🤝 A special thanks to… @mt030d @0x_serial_coder @0xEkkoo @kalogerone @0xKorok @pep7siup_ @rokinot @talfao1 @radcipher + everyone else that got involved!
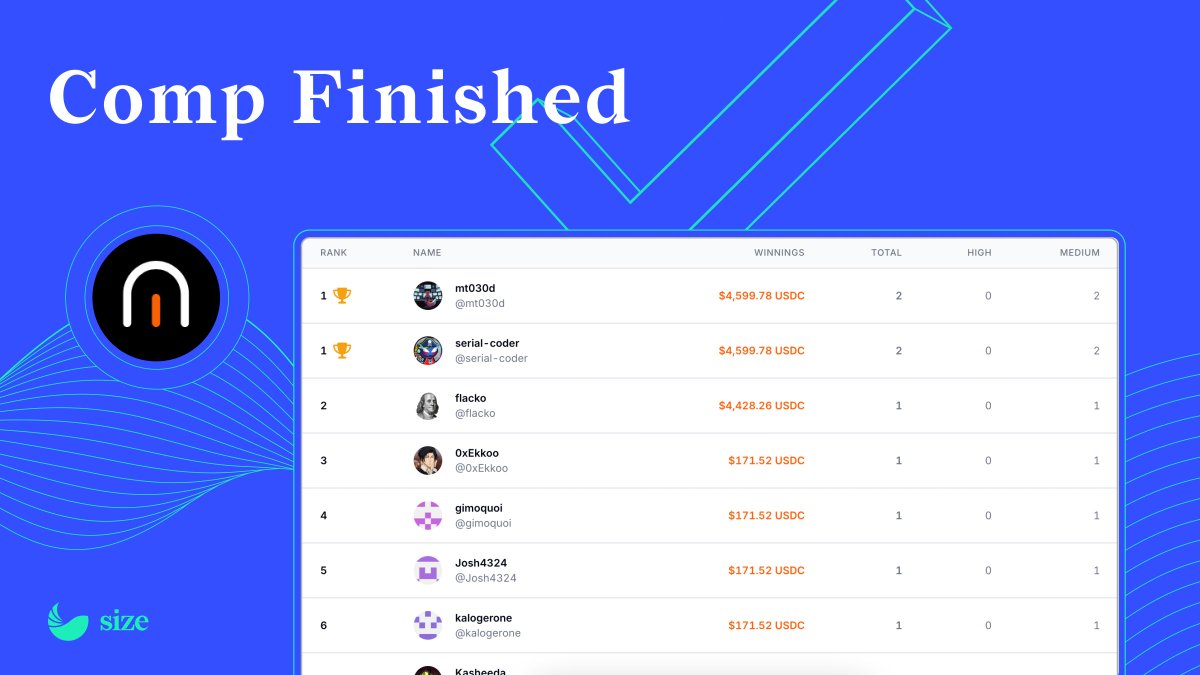
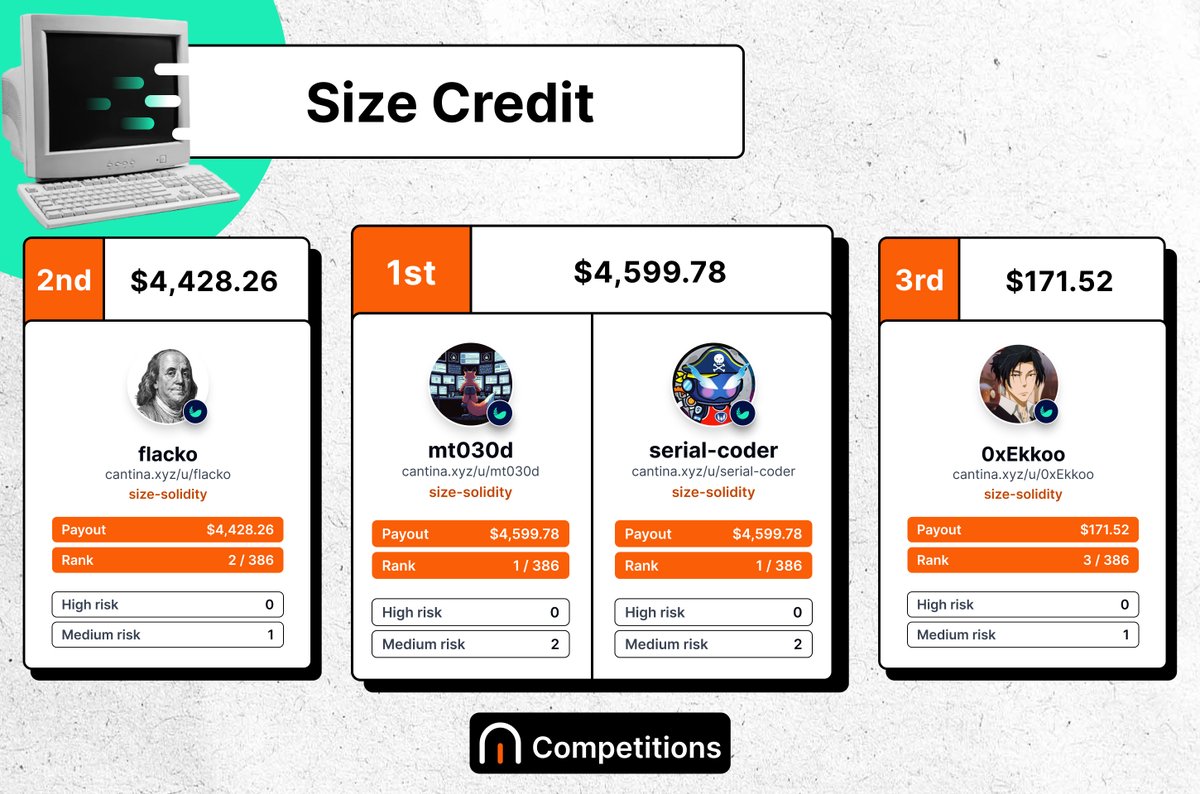
Wow! My first auditing competition on @cantinaxyz, and I won 🥇 (alongside @mt030d). Thank you 🙏 to @SizeCredit, @agfviggiano, and @cantinaxyz!
We love a leaderboard. The @SizeCredit results are in! 🪐 Your top 3 ranked researchers are: 🥇 mt030d : $4,599.78 🥇 @0x_serial_coder : $4,599.78 🥈 @flack00n : $4,428.26 🥉 @0xEkkoo: $171.52 Thank you to everyone that participated! Full leaderboard below.
Hey everyone 🙋♂️, I want to share my career journey (as a smart contract auditor 🕵️♂️) interviewed by DittoETH, @dittoproj. . If you are a smart contract auditor or want to become one, this interview might be worth reading. medium.com/@serial_coder/…
I am happy to have the opportunity to be interviewed by you @dittoproj. Thank you! 🙏
🚀 Featured auditor this week: Phuwanai Thummavet (@0x_serial_coder), ranked #46 in 2024 & #173 all-time on @code4rena! Read here as he discusses the future of Ethereum with Account Abstraction, new oracle models, and the crypto scene from his country of Thailand!

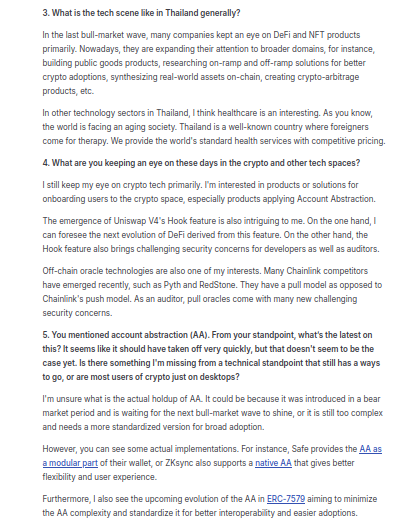


Article dittoeth.com/interviews/5_p… Phuwanai took part in the exclusive Code4rena audit invitational for DittoETH this July, showcasing his expertise in the field. You can continue to follow his contributions on X @0x_serial_coder or read his writings at: serial-coder.com.
🚀 Featured auditor this week: Phuwanai Thummavet (@0x_serial_coder), ranked #46 in 2024 & #173 all-time on @code4rena! Read here as he discusses the future of Ethereum with Account Abstraction, new oracle models, and the crypto scene from his country of Thailand!




ty to @codehawks and @code4rena for all the help with audits and big shoutout to d3e4, @0x_serial_coder, @NonseOdion, @0xbepresent for that finishing audit
The results of the Ditto invitational audit are in! Thank you to d3e4, @0x_serial_coder, @NonseOdion, and @0xbepresent for helping secure the Ditto codebase! Much respect to @dittoproj for their unwavering commitment to the highest security outcomes 🫡

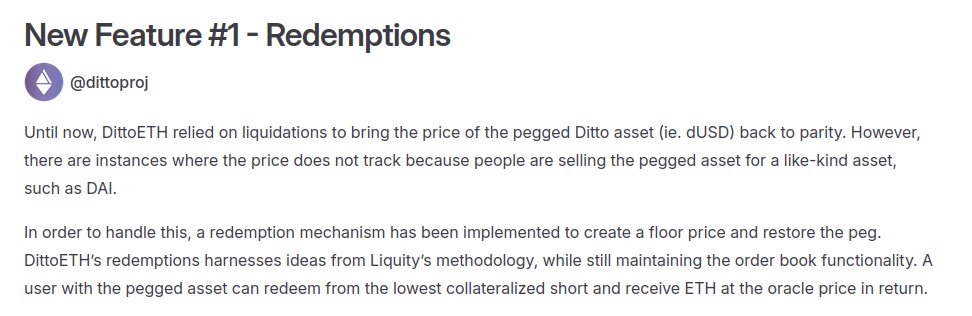
the $13,100 invitational audit with @code4rena has finished! audited a host of new features. one of which is redemption mechanism, read about it in this latest released blog post thank you @NonseOdion, @0x_serial_coder, @0xbepresent and d3e4 for participating in this sec. audit!
@ValixConsulting proudly presents an article series: “Solidity Security By Example.” . Here is the 13th episode of the series. We explain the attack: “Double Spending #2” in the Solidity smart contract. . medium.com/valixconsultin…
Thanks for mentioning @HackenProof
Smart contract security Cross-Function Reentrancy Cross-function reentrancy is another level of reentrancy in terms of complexity. Author by @br1gh7n4ry #bugbounty #offensivesecurity
Smart contract security Cross-Function Reentrancy Cross-function reentrancy is another level of reentrancy in terms of complexity. Author by @br1gh7n4ry #bugbounty #offensivesecurity
@ValixConsulting proudly presents an article series: “Solidity Security By Example.” . Here is the 12th episode of the series. We explain the attack: “Amplification Attack (Double Spending #1)” in the Solidity smart contract. . medium.com/valixconsultin…
Valix Consulting proudly presents an article series: “Solidity Security By Example.” . Here is the 11th episode of the series. We explain the attack: “Denial of Service With Induction Variable Overflow” in the Solidity smart contract. . medium.com/valixconsultin…
💥 Hey, I’ve published my new article, “ 𝐄𝐑𝐂-𝟒𝟑𝟑𝟕 — 𝐖𝐡𝐲 𝐖𝐨𝐮𝐥𝐝 𝐓𝐡𝐢𝐬 𝐂𝐡𝐚𝐧𝐠𝐞 𝐄𝐭𝐡𝐞𝐫𝐞𝐮𝐦 𝐓𝐨 𝐌𝐚𝐬𝐬 𝐀𝐝𝐨𝐩𝐭𝐢𝐨𝐧? ”. 🌛 . 𝐀𝐫𝐭𝐢𝐜𝐥𝐞 𝐥𝐢𝐧𝐤 👉 medium.com/coinmonks/erc-… . Enjoy reading ☃️
@ValixConsulting proudly presents an article series: "Solidity Security By Example." . Here is the 10th episode of the series. We explain the attack: "Denial of Service With Gas Limit" in the Solidity smart contract. . Link: medium.com/valixconsultin… .
Cross-Contract Reentrancy explained The root cause of cross-contract reentrancy attack is typically caused by having multiple contracts mutually sharing the same state variable, and some of them update that variable insecurely. 1) The Vulnerability 2) The Attack 3) The Solution

@ValixConsulting proudly presents an article series: "Solidity Security By Example." . Here is the 9th episode of the series. We explain the attack: "Denial of Service With Revert" in the Solidity smart contract. . Link: medium.com/valixconsultin…
ฝากบทความ ERC-4337 (ที่ลงเฟสไปเมื่อวาน) ฉบับ Medium ครับ น่าจะอ่านง่ายขึ้น และเก็บไว้อ่านย้อนหลังได้ครับ 😀 . นี่จะเป็น Medium แรกของผมที่ลงภาษาไทยเลยนะ 🎃 medium.com/@serial_coder/…
🧵𝗩𝘂𝗹𝗻 𝗼𝗳 𝘁𝗵𝗲 𝗗𝗮𝘆 | 𝗖𝗿𝗼𝘀𝘀-𝗰𝗼𝗻𝘁𝗿𝗮𝗰𝘁 𝗥𝗲𝗲𝗻𝘁𝗿𝗮𝗻𝗰𝘆 6⃣ of 100 | Solidity Vulnerability Rolodex 💡𝗪𝗵𝗮𝘁? Explain a unique vuln every day for 100 days 🎯𝗪𝗵𝘆? The ultimate reference for solidity auditors medium.com/valixconsultin…
United States เทรนด์
- 1. #Worlds2025 49K posts
- 2. #100T N/A
- 3. Yamamoto 49.9K posts
- 4. #DWTS 45.4K posts
- 5. Young Republicans 81.1K posts
- 6. halsey 9,656 posts
- 7. #MOST_WANTED_IN_CHICAGO 1,582 posts
- 8. #FlyTogether 3,048 posts
- 9. Kreider 1,378 posts
- 10. Jared Butler N/A
- 11. Ohtani 14.4K posts
- 12. Cuffem 3,295 posts
- 13. Tami 4,648 posts
- 14. Lucia 61.6K posts
- 15. George Floyd 35.6K posts
- 16. Vishnu 9,056 posts
- 17. Vivian 30K posts
- 18. Will Richard 2,589 posts
- 19. The Dodgers 50K posts
- 20. Politico 318K posts
คุณอาจชื่นชอบ
-
 HickupHH3
HickupHH3
@HickupH -
 Workpod Audits🛡
Workpod Audits🛡
@WorkpodAudits -
 reentrant
reentrant
@0xreentrant -
 DeGatchi
DeGatchi
@DeGatchi -
 Kankodu
Kankodu
@kankodu -
 Jonatascm 🪐
Jonatascm 🪐
@jonataspvt -
 another anon
another anon
@eugenioclrc -
 hake (independent arc)
hake (independent arc)
@hake_stake -
 StErMi
StErMi
@StErMi -
 AlexOnCrypto
AlexOnCrypto
@mis4nthr0pic -
 Daniel | Guardian Audits ◻⛓
Daniel | Guardian Audits ◻⛓
@dannygfromnyc -
 0xDjango
0xDjango
@0xDjangoOnChain -
 zzykxx
zzykxx
@zzykxx -
 P.M
P.M
@p_misirov -
 ggballas 🚀📦 e-commerce 🇮🇱
ggballas 🚀📦 e-commerce 🇮🇱
@ggballas
Something went wrong.
Something went wrong.