你可能會喜歡
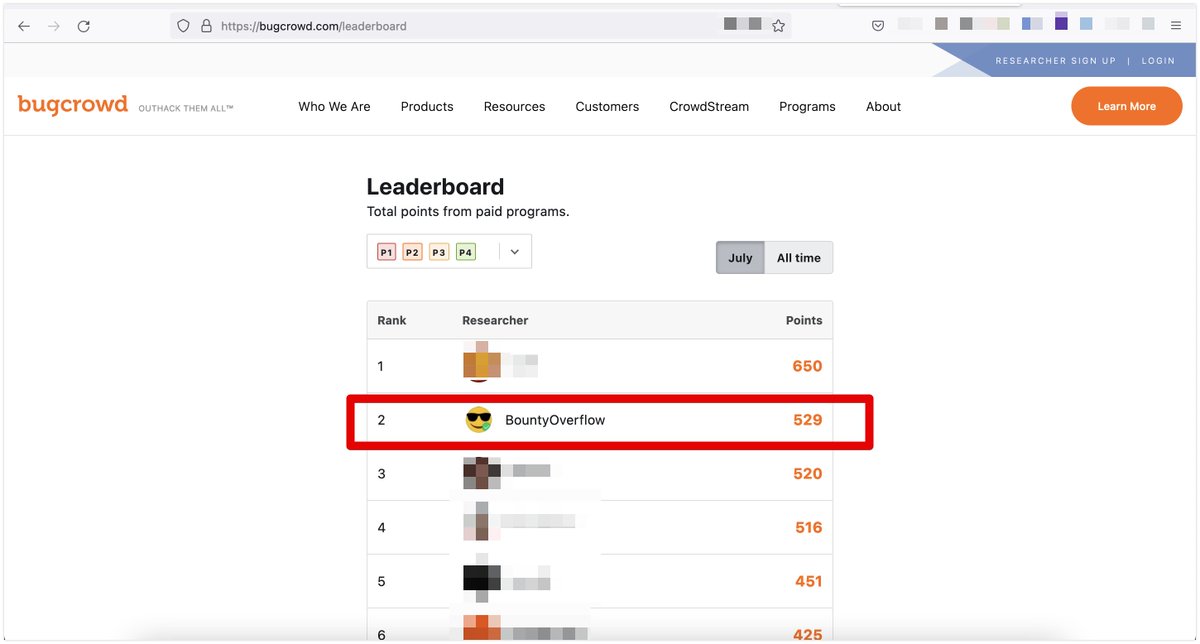
What a great month it was July 2022! I have ranked #2 world wide on @Bugcrowd bugcrowd.com/leaderboard
Why to use a simple #XSS vector like this 🤔 <img src=x onerror=alert(1)> when you can use a much better one? 🤩 1'//"</Script><Img/Src%0AOnError=alert(1)// The vector above pops in HTML and JS scenarios for single and double quotes! 🤯 Try it here: x55.is/brutelogic/xss…
New Rhino Blog Post: CVE-2025-0693: AWS IAM User Enumeration bit.ly/3QcEpnx
blog.cloudflare.com/resolving-a-mu… I don’t work there anymore but it’s truly so sick seeing this level of weird bug being patched so fast Hell yeah
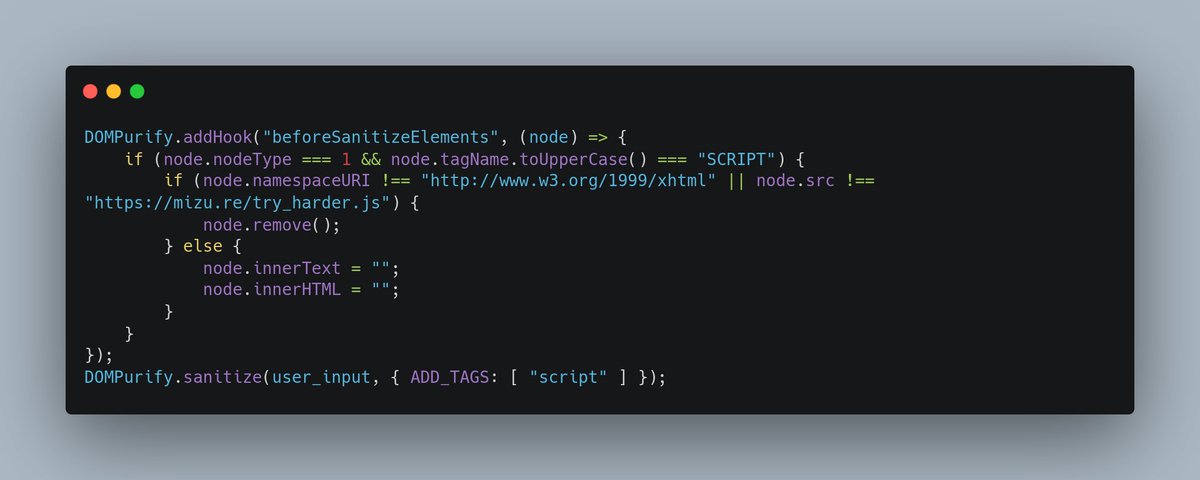
Thanks to the recent @PortSwigger top 10, I finally found the motivation to finish writing the 2nd article about DOMPurify security! 😁 Before releasing it, I would like to share a small challenge 🚩 Challenge link 👇 challenges.mizu.re/xss_04.html 1/2
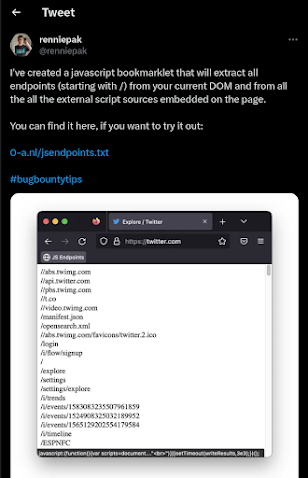
Unleashing The Power of a JavaScript Bookmarklet for Endpoint Discovery in Bug Bounty and… execure.medium.com/unleashing-the…
Seems rennie deleted his twitter so original post is gone :/ but someone made a post about it here with the code: execure.medium.com/unleashing-the…
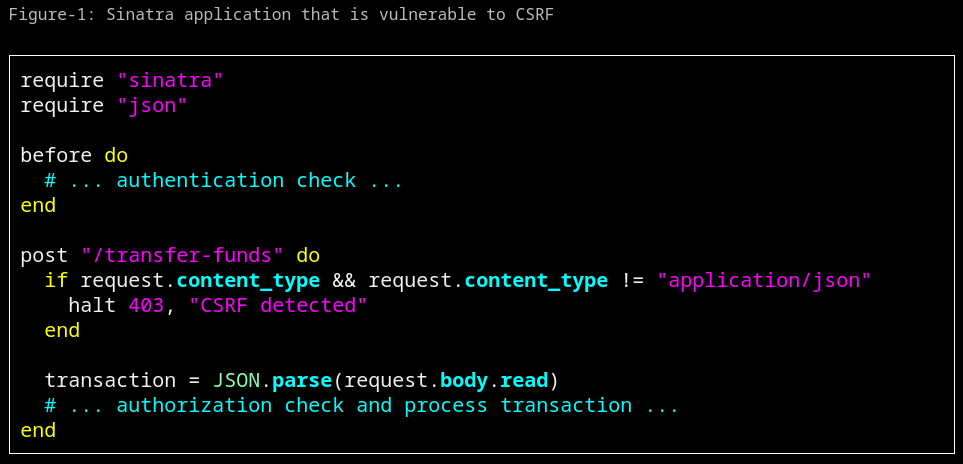
Got a CSRF attack being blocked by Content-Type validation? You might be able to bypass it with this quality technique. x.com/lukejahnke/sta…
🧵Can you work out how to bypass this vulnerable CSRF protection? Read all about this gotcha in my latest blog post
After a 4-month break, I’m backon @Bugcrowd ! Life kept me busy with something truly special—welcoming my adorable daughter into the world. 🍼💕 Feeling so blessed! 🥰

There is a public website with the following folder path: txyz.com/wp-content/upl…<filename> Does anyone know of any tricks for WordPress websites that would allow me to list all files and folders in the 'uploads' directory? #thanks-in-adv
I was facing a very strict WAF while trying to exploit a XSS : no gt/lt signs, no parentheses, no double quotes, no backticks. I was injecting inside an html tag. Turns out the solution was very simple (and not well documented): <img src=x onerror=alert(document.domain)>

🚨Alert🚨CVE-2024-30103: Microsoft Outlook Remote Code Execution Vulnerability ⚠This Microsoft Outlook vulnerability can be circulated from user to user and doesn’t require a click to execute. Rather, execution initiates when an affected email is opened.This is notably dangerous…

INTRODUCING: Agentic Security - LLM Security Scanner! 🔍 🛠️ Customizable Rule Sets: Tackle agent-based attacks with precision! 🧪 Comprehensive Fuzzing: Dive deep into any LLM's vulnerabilities! 🔄 LLM API Integration & Stress Testing: Ensure robust performance!
Indeed, for me aswell ! Thanks @Bugcrowd from my bottom of the heart ❤️!
I <3 @Bugcrowd and everyone that worked to make it so good. Definitely improved my life overall.
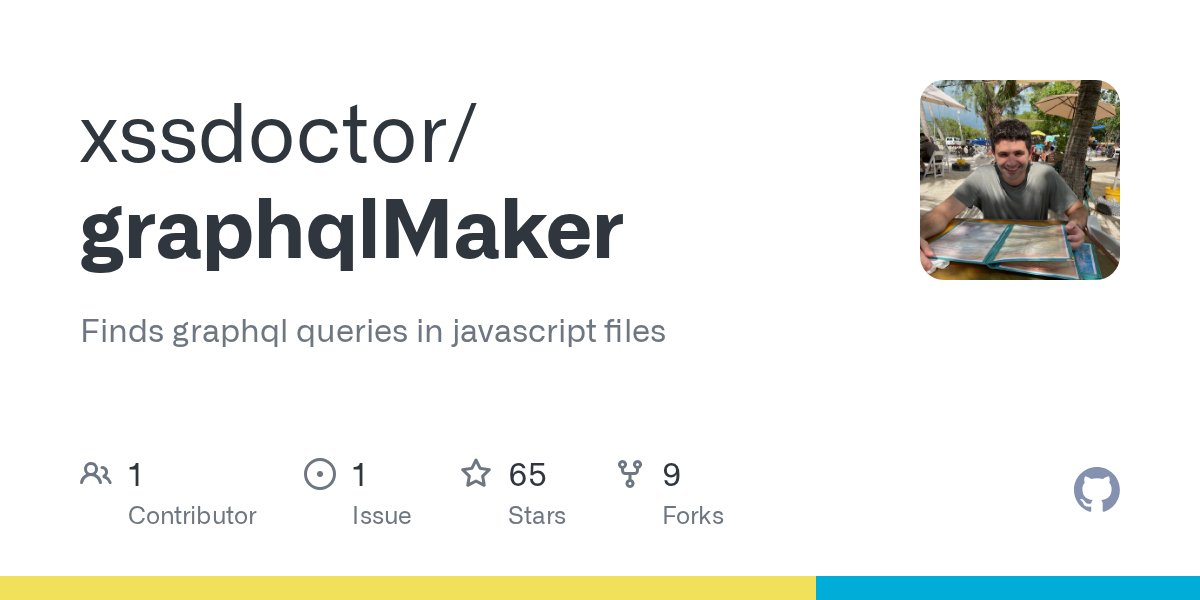
When it comes to GraphQL recon, JavaScript is the next best thing to introspection. I made a tool (in go) which finds all graphql queries in js files (or folders) and uses ChatGPT to build the queries for you! github.com/xssdoctor/grap…
A Day in the Life of an Unemployed Bug Hunter
United States 趨勢
- 1. Pat Spencer 2,364 posts
- 2. Kerr 5,054 posts
- 3. Jimmy Butler 2,470 posts
- 4. Podz 3,034 posts
- 5. Seth Curry 3,905 posts
- 6. Hield 1,497 posts
- 7. Mark Pope 1,855 posts
- 8. #DubNation 1,378 posts
- 9. Carter Hart 3,770 posts
- 10. Derek Dixon 1,205 posts
- 11. Connor Bedard 2,188 posts
- 12. Brunson 7,255 posts
- 13. #ThunderUp N/A
- 14. Caleb Wilson 1,121 posts
- 15. Jaylen Brown 8,987 posts
- 16. Notre Dame 38.5K posts
- 17. Knicks 14.4K posts
- 18. Kuminga 1,314 posts
- 19. Kentucky 29.4K posts
- 20. Celtics 16.4K posts
你可能會喜歡
-
 Bug Bounty Reports Explained
Bug Bounty Reports Explained
@gregxsunday -
 𝐑𝐀𝐢𝐡𝐚𝐧 ✪
𝐑𝐀𝐢𝐡𝐚𝐧 ✪
@zapstiko -
 Hussein Daher
Hussein Daher
@HusseiN98D -
 payloadartist
payloadartist
@payloadartist -
 MorningStar
MorningStar
@0xMstar -
 Julien | MrTuxracer 🇪🇺
Julien | MrTuxracer 🇪🇺
@MrTuxracer -
 Lu3ky13 ⚡️⚡️
Lu3ky13 ⚡️⚡️
@lu3ky13 -
 todayisnew
todayisnew
@codecancare -
 🇸🇦 Murtada Bin Abdullah (Rood)
🇸🇦 Murtada Bin Abdullah (Rood)
@0x_rood -
 Nagli
Nagli
@galnagli -
 Hazem
Hazem
@_bughunter -
 Ali Tütüncü
Ali Tütüncü
@alicanact60 -
 N0t0d4y
N0t0d4y
@0xJin -
 Kanhaiya Sharma 🇮🇳
Kanhaiya Sharma 🇮🇳
@krishnsec -
 Muhammad Fauzan 🇵🇰
Muhammad Fauzan 🇵🇰
@Fozisimi143
Something went wrong.
Something went wrong.