Casper
@ChainCasper
I'm a senior web3 security engineer focusing on EVM and Rust smart contracts.
Not just another NFT project; it’s a whole new brand and ecosystem. From now, at any MOMENT, we'll launch our airdrop farming, even before minting. You’re still early. RT+Like+Follow to be eligible for the Airdrop Farming System.
A different interpretation: making so much money from bug bounties is no longer easy.
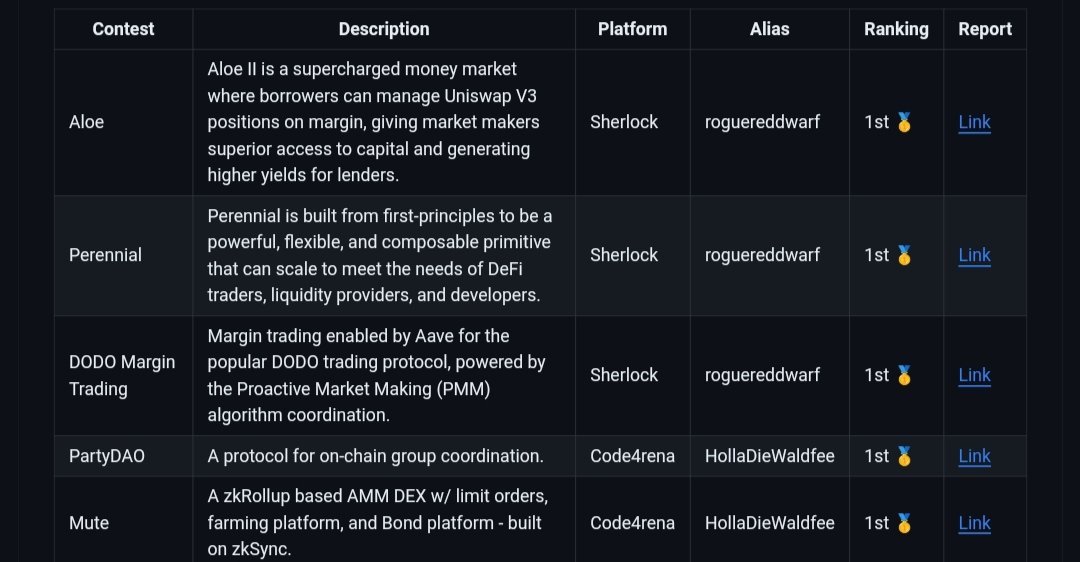
Still top250 even though I haven't done a code4rena contest in 15 months now, and I made only like $10-15k This just shows that not too much people are successfully joining the web3 security space. We need more great talent joining.
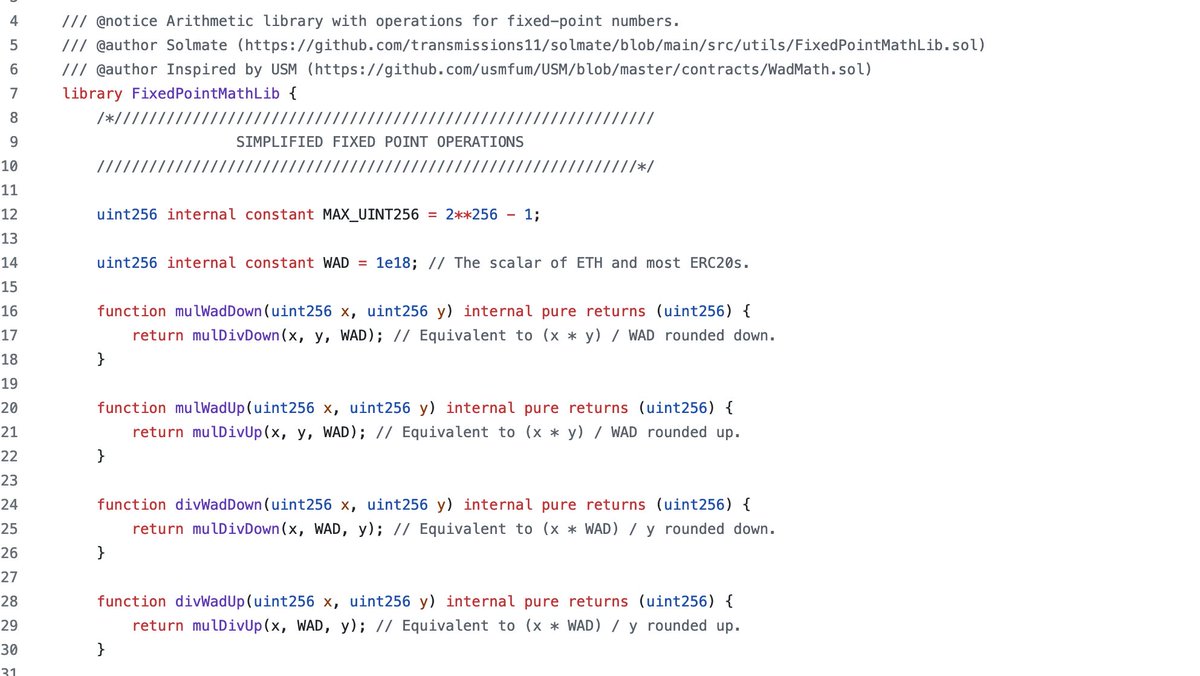
Complex Contracts Simple Explained: Solmate FixedPointMathLib Let’s take a look at the following library from Solmate: This might look scary for a new junior auditor. The good news is - it isn’t scary for much longer! Lets dive into it: First you can see the library name:…
I think the methodology is one thing. But to succeed, you need to understand how your project should work and know the best practices and patterns that can be applied to it. And this, indeed, requires a lot of web3 experience.
The reason I say audit methodologies are overrated is that I've used the same methodology for over a year, yet with drastically different results. The difference between making $10 and making $10000 is NOT the methodology.
It's good to see that there are so many web3 competitions. On the other hand, in such an abundance, the smaller ones may receive less attention.
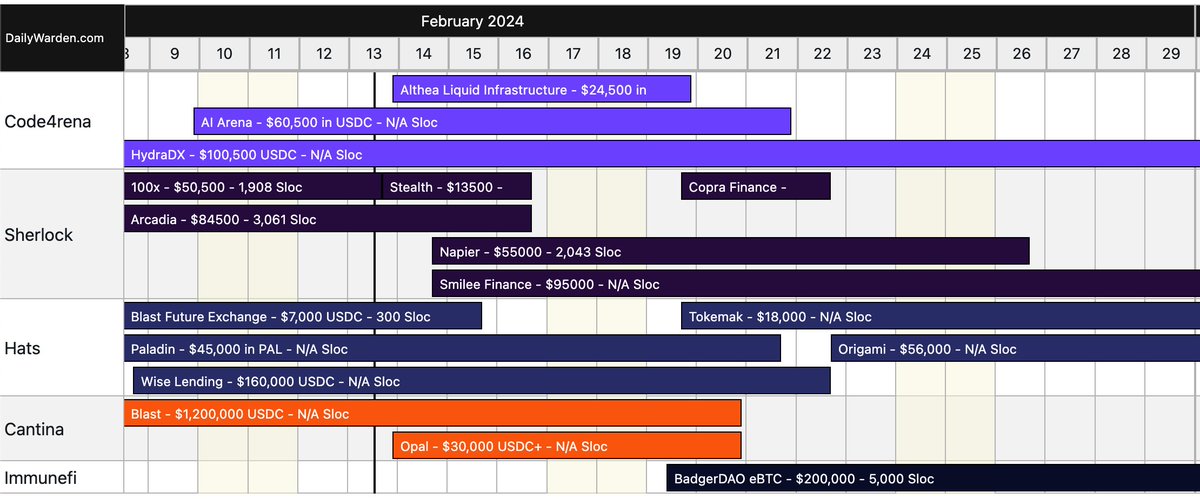
February is another uptrend month when it comes to web3 security audits demand So much money to be made by smart security researchers
3 mandatory checklists to go through before doing a smart contract security audit on your codebase: 1. The Solcurity Standard - github.com/transmissions1… 2. Weird ERC20 tokens list - github.com/d-xo/weird-erc… 3. Solodit aggregated checklists - solodit.xyz/checklist
I think this is an important take. Overoptimization or significant innovations often complicate protocols, increasing the chances of hidden vulnerabilities.
I'm going to take issue with this. Bugs will _almost always_ exist in codebases of sufficient complexity. This is mistake for "bugs will always exist" But there are programs out there, tiny ones, that are perfect in every way, provably so. If we want correct smart contracts…
Q: How can I write more secure Smart Contracts? A: By understanding this key principle: Smart Contracts are NOT SOFTWARE. Smart Contracts are HARDWARE. “Alex, WTF are you talking about?”… hear me out… For the past 20 years, writing software has meant iterating quickly:…
I have always appreciated transparency instead of throwing out bogus numbers.
Unfortunately, the more complex and revolutionary a protocol is, the more likely it is to have unnoticed bugs.
Sherlock is extremely disappointed to see the @KyberNetwork exploit and is engaged fully in assisting Kyber. The hack is one of the most complex exploits ever seen in DeFi but this does not absolve Sherlock from responsibility.[1] For background, the Kyber team stands out as a…
![sherlockdefi's tweet image. Sherlock is extremely disappointed to see the @KyberNetwork exploit and is engaged fully in assisting Kyber.
The hack is one of the most complex exploits ever seen in DeFi but this does not absolve Sherlock from responsibility.[1]
For background, the Kyber team stands out as a…](https://pbs.twimg.com/media/F_zPoXsW0AAd1Mw.jpg)
Thanks Doug. I've been grinding all day on this. I found the root cause after 8 hours and just minutes before you posted. But I have to hand it to the @KyberNetwork devs for getting there first. I knew they'd already found the root cause but decided to hold off on receiving…
1/ Finished a preliminary deep dive into the Kyber exploit, and think I now have a pretty good understanding of what happened. This is easily the most complex and carefully engineered smart contract exploit I've ever seen...
United States Trends
- 1. Caleb N/A
- 2. Rams N/A
- 3. Don Lemon N/A
- 4. DJ Moore N/A
- 5. Ben Johnson N/A
- 6. Stafford N/A
- 7. McVay N/A
- 8. Adams N/A
- 9. #RHOP N/A
- 10. #AKnightOfTheSevenKingdoms N/A
- 11. #LARvsCHI N/A
- 12. Kmet N/A
- 13. FACE Act N/A
- 14. #BaddiesUSA N/A
- 15. Patriots N/A
- 16. #Married2Med N/A
- 17. Puka N/A
- 18. Gizelle N/A
- 19. Kam Curl N/A
- 20. Harrison Mevis N/A
Something went wrong.
Something went wrong.