𐌋𐌄Ꝋ
@CipherShade
𐌂Ꝋ𐌍𐌔𐌉𐌔𐌕𐌄𐌍𐌂𐌙 𐌊𐌉𐌋𐌋𐌔 𐌂𐌓𐌄𐌀𐌕𐌉ᕓ𐌉𐌕𐌙!
You might like
Something big is brewing. Eyes on #cantinapectra. 🕶️🖤
The next chapter of @ethereum security begins 🪐 Today marks the beginning of a new competition: a comprehensive review of Pectra, in partnership with the @ethereumfndn. 💰 $2,000,000 USDC 📆 Live now - March 24th 🔗 Below
Level up your cybersecurity knowledge! A compilation of the best Web3 security alpha from our top engineers 🧵 📚 Blog Posts 1️⃣ Preparing for the Challenges of Smart Contract Audits 🔗 zokyo.io/blog/navigatin… Compilation of essential tips for pre-audit preparation 2️⃣ The…
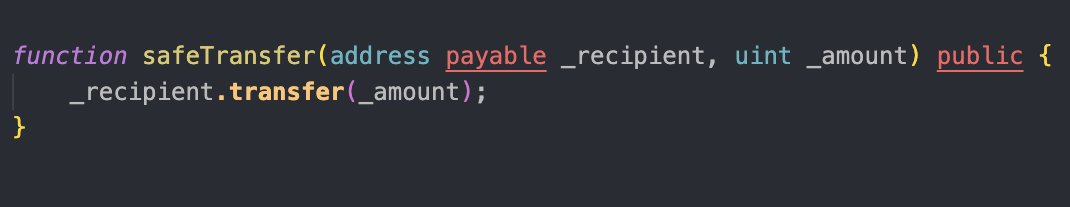
Ether Transfers in Solidity: transfer(), send(), and call() In Solidity, there are three primary ways to transfer Ether between contracts or to external accounts: transfer(), send(), and call(). Each method has different behaviors, including safety mechanisms and gas…


Spot this bug, and you might become a Sherlock Lead Senior Watson (LSW) one day. The winner will be picked in 24 hours. This code is a simplified version of an actual vulnerability found in a Sherlock contest. Hint: Look closely at the disableMaxLock function, consider all…

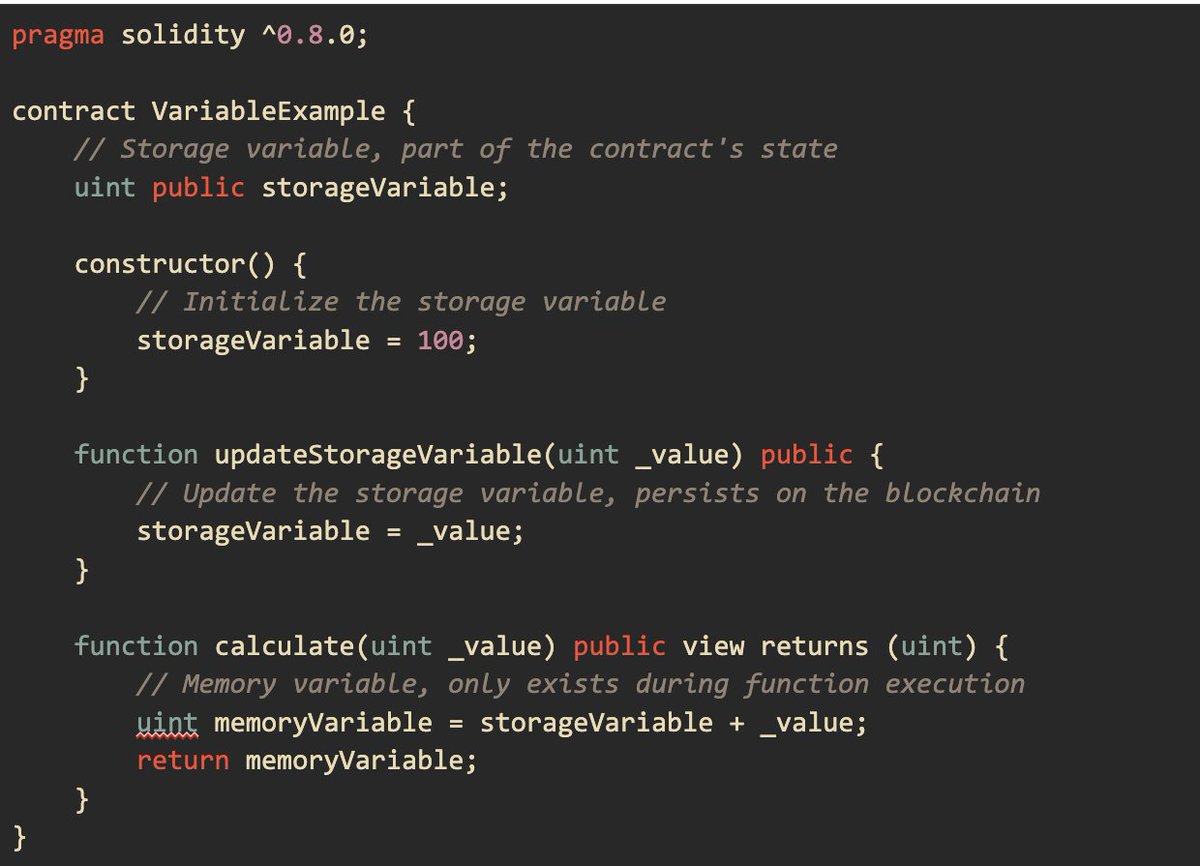
Uninitialized Storage Pointers/ Uninitialized State Bugs Explained In Solidity, data storage is categorized into three main types: storage, memory, and calldata, each serving distinct purposes within smart contracts. Storage variables are part of the contract's persistent state…
Inheritance in Smart Contracts This concept, borrowed from object-oriented programming, enables code reusability and modular design. By inheriting from a parent contract, a child contract can access and utilize its state variables, functions, and modifiers. Solidity supports…

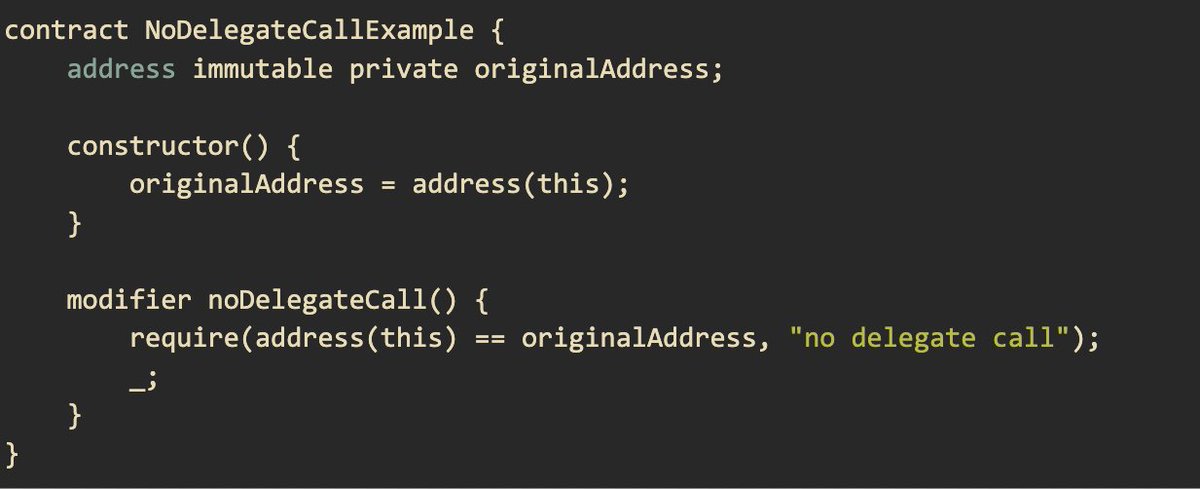
No delegatecall: Preventing unwanted delegatecalls When delegatecall is used in a contract, it executes code in the context of another contract. This means the code runs in the context of the calling contract (using its storage, balance, and address), but the actual code to…

One great method that can improve your learning is a feedback form 📝. It helped me WIN my first @code4rena contest back in November 🏆 And it helped me get a chance to work with @GuardianAudits, auditing some of the biggest names in crypto 💼. This isn't a technique to do…

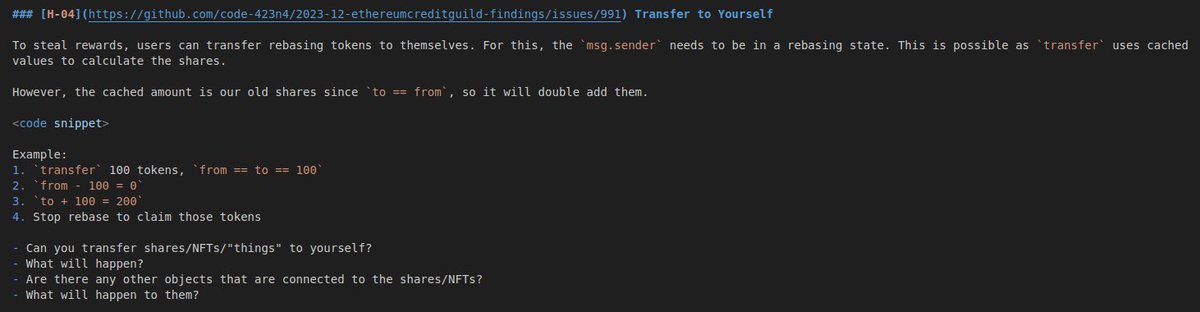
Solana PDAs : Here Is How It Works - Part - 1 Let's explore a main use case for Program Derived Accounts (PDAs). It allows a program to have control over a given account, and pseudo-sign transactions to modify it. We first create a pool, derived from the creator's address, and…

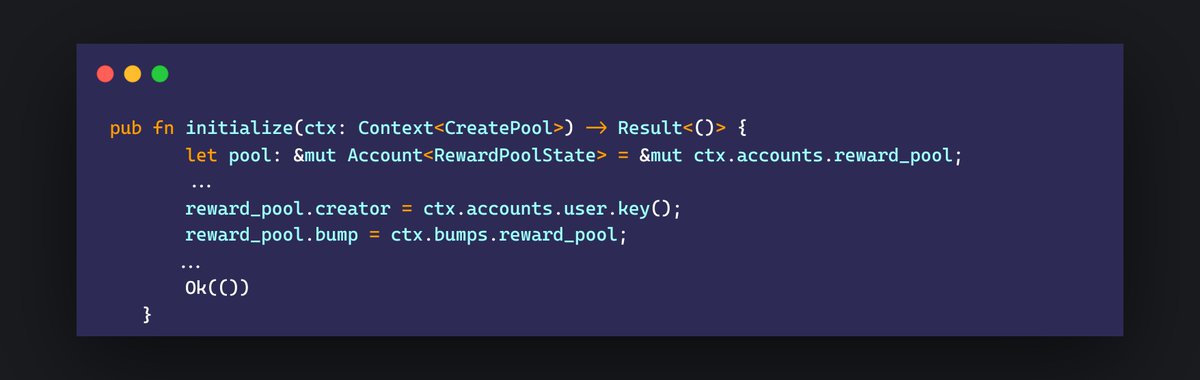
Understanding Low-Level Call & High-Level Call in Solidity In Solidity, there are two primary ways to invoke functions or interact with other contracts: high-level and low-level calls. These two methods offer different levels of abstraction and control over the interaction…
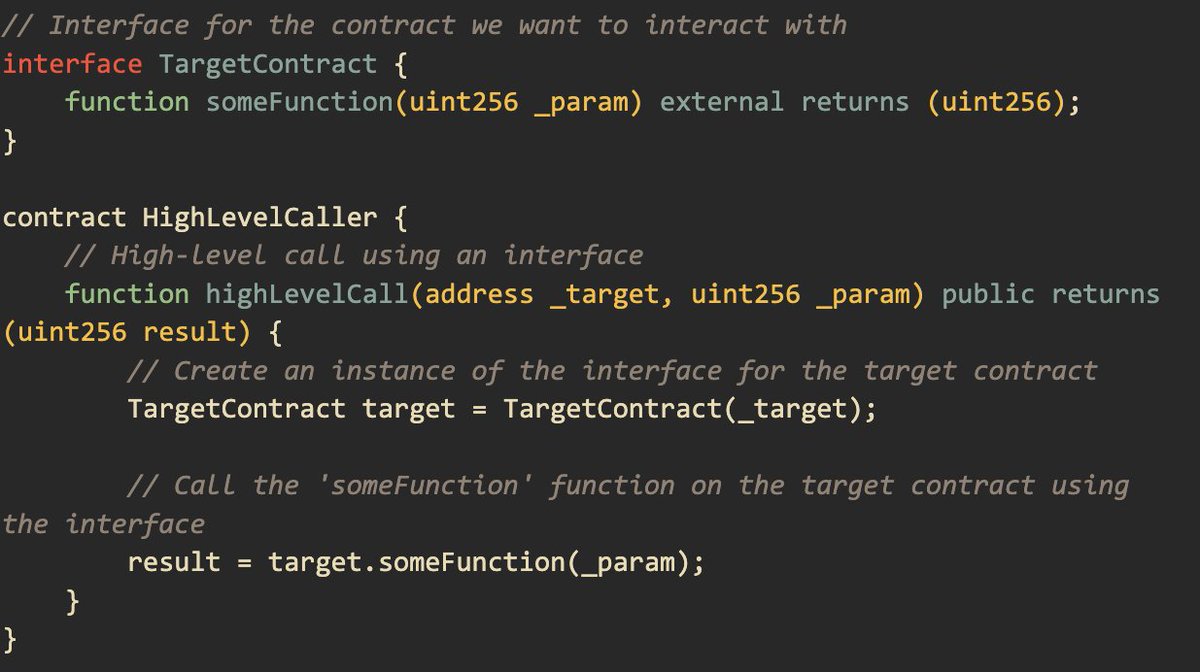
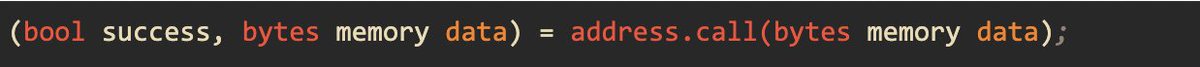
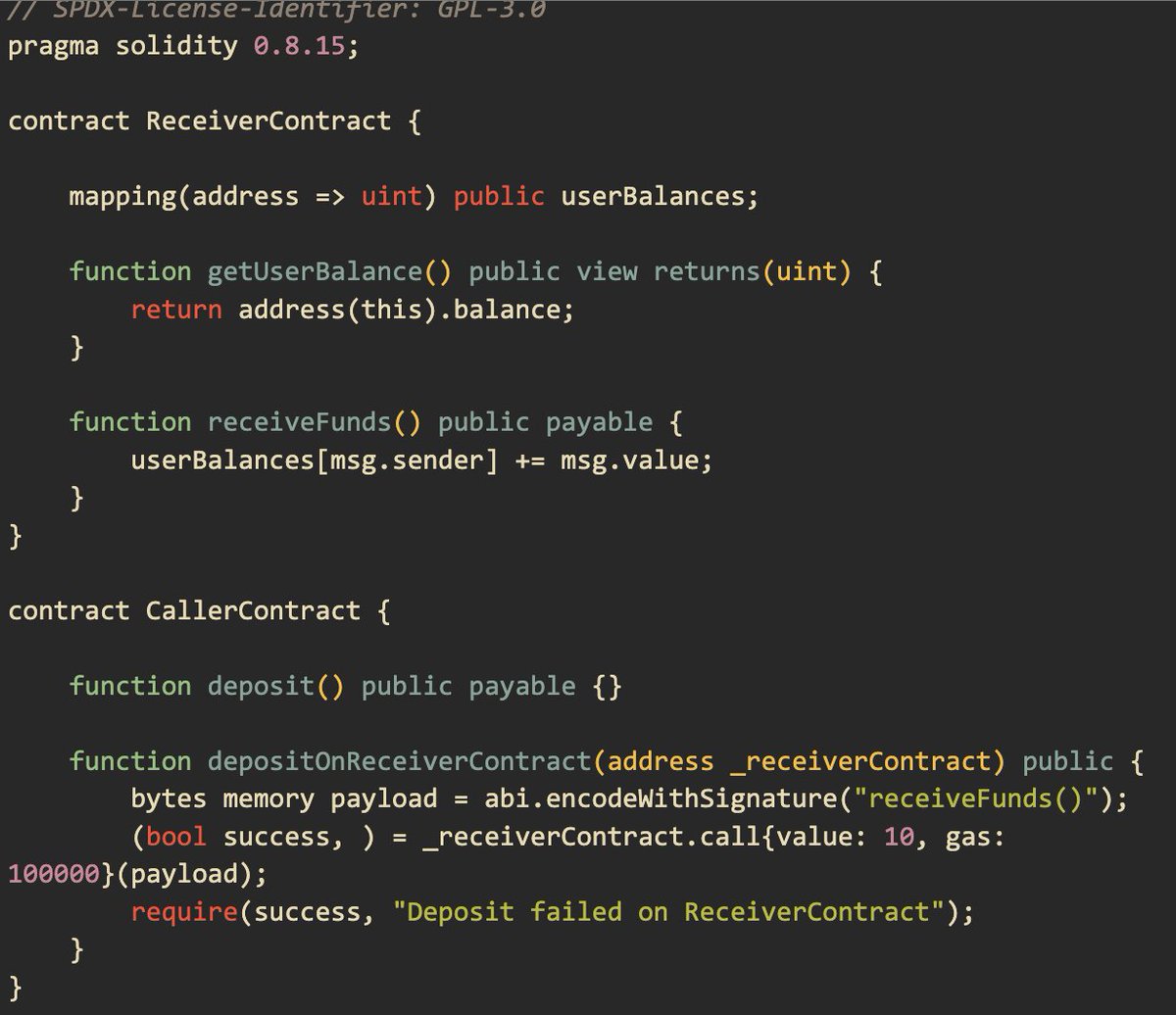
Insecure randomness Explained Generating random numbers has found various applications in the Web3 space. For example, a gaming, gambling/bet DApp finds this useful in determining pool winners. However, doing this can create an in-way for attacks. Insecure randomness refers to…

~2 years ago I got into web3 security, ~6 months later I went all-in on it - best decision ever. Ever since I jumped in that rabbit hole, it's been 24/7/365 non-stop researching, auditing, organising reviews. If I was starting today from scratch I'd 100% do it all over again.
How Call Functions Work in Solidity The “call” function in Solidity is a low-level function that enables contract-to-contract communication by invoking functions or sending Ether to a specified contract address. It operates by taking calldata and executing it on the intended…

Come become an auditor and forget all of this bullshit forever
a few weeks ago i did interviews, coding puzzles, all the silly bullshit, all to get a "junior engineer" offer from smg/consensys for half the pay and double the hours i quoted. they even cited the fact that i don't have degree companies that demand degrees are not worth your…
Algebra's Reserve Logic - A Competitive Advantage Did you know that @CryptoAlgebra developed a unique reserve logic, which allows them to redistribute tokens which are transferred directly to the pair / rebase tokens, as a fee to the liquidity providers in the current active…

How to detect Honeypot Tokens as non-technical user Detecting honeypot tokens as a non-technical user can be challenging, but with a few steps, you can significantly reduce your risk when considering investing in new tokens on blockchain platforms. Here’s a practical approach…


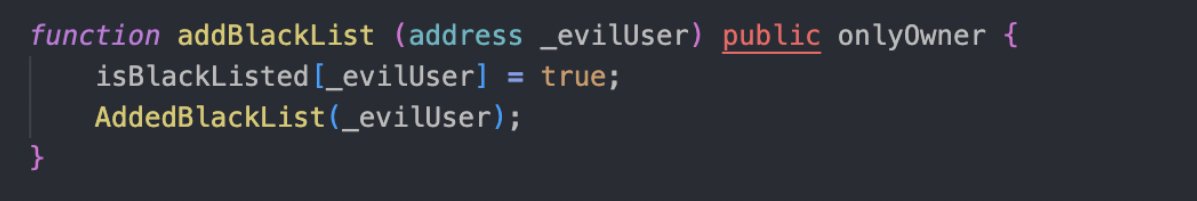
How can @Tether_to freeze USDT? USDT is the biggest stablecoin with a circulating supply of over 110 billion USD. Centralized stablecoins always come with the same risk: Centralized control Tether's ability to freeze USDT revolves around the inclusion of administrative…


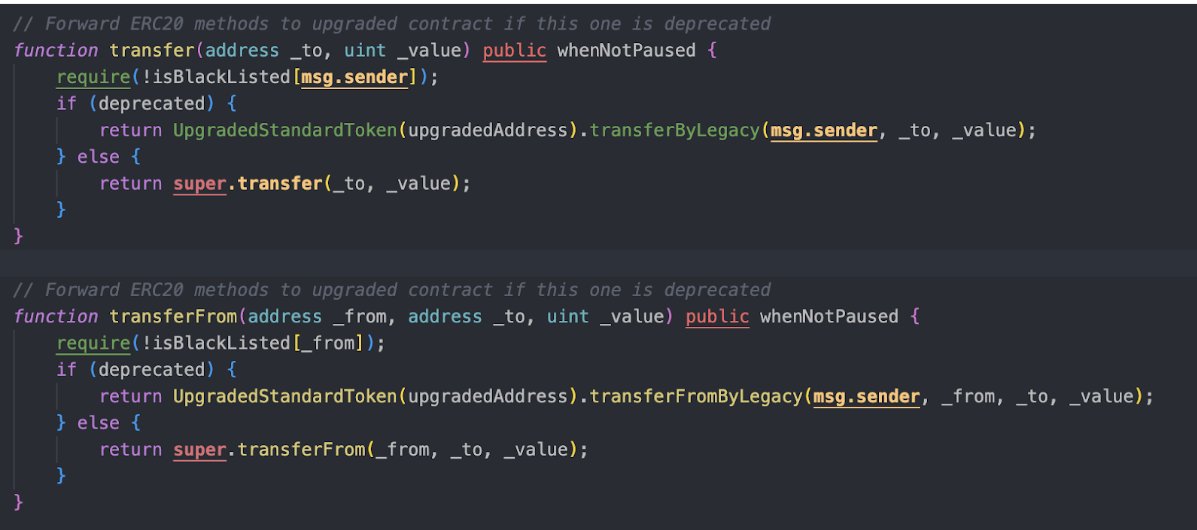
How ERC777's hook receiver feature could be used as an attack vector: - The attack vector in short - ERC777 and its hooks - The attack vector with arbitrary calls mixbytes.io/blog/one-more-…
UniswapV2: _mintFee explained Within the UniswapV2Pair, the _mintFee function seems to be one of the slightly more complicated concepts. Today, I will dissect this mechanism. The _mintFee function is particularly notable for its role in managing lp fees within the protocol.…

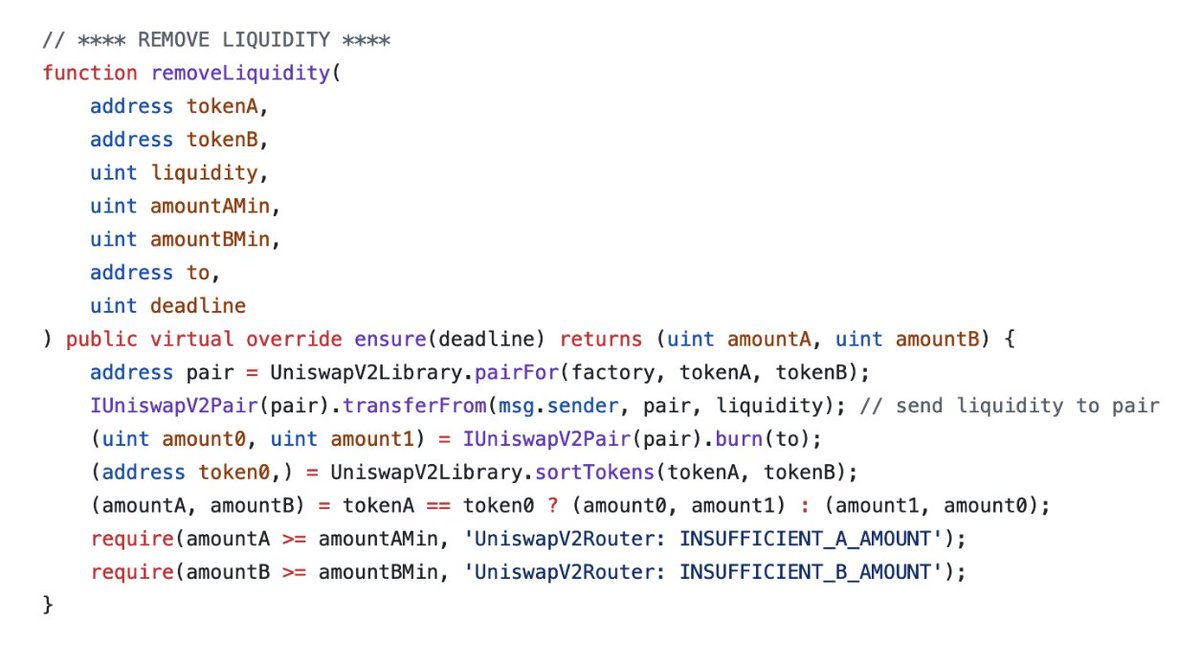
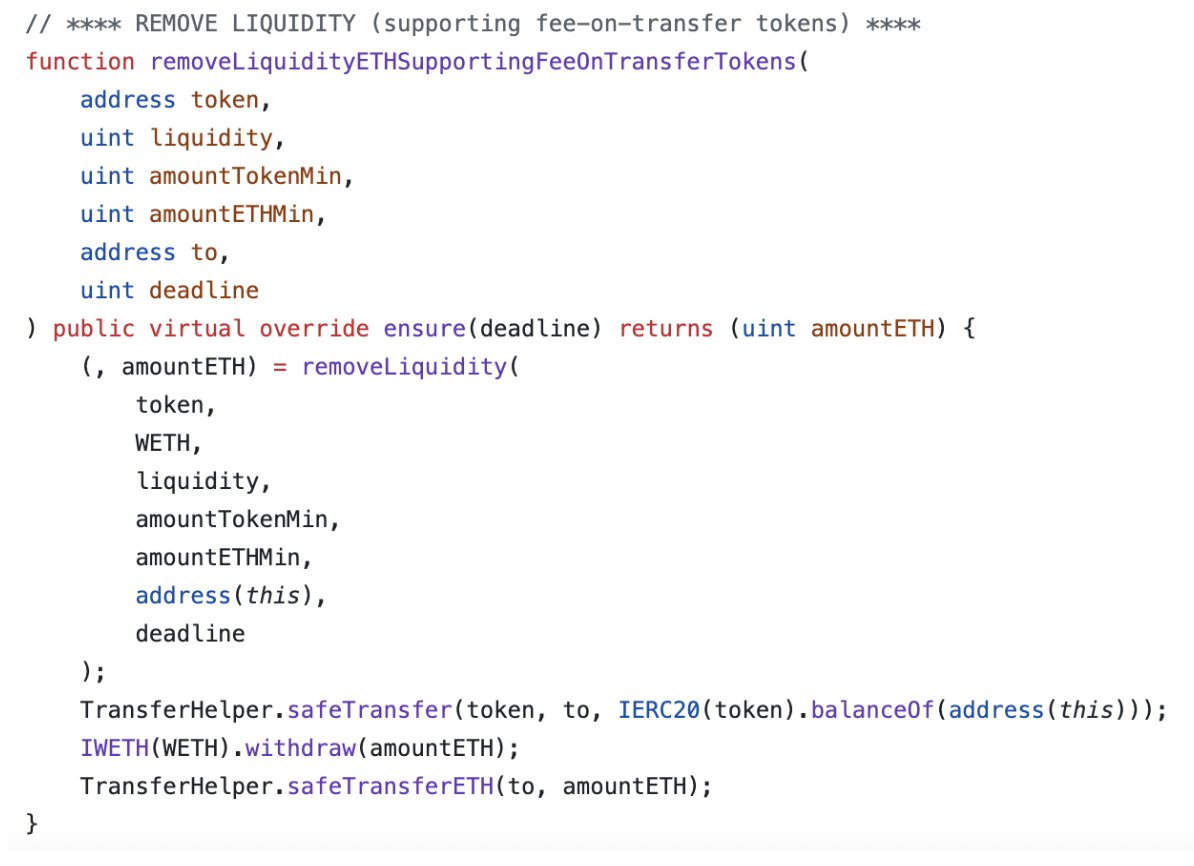
UniswapV2 Router Flaw: Double Taxation The UniswapV2 router exposes two distinct functions for removing liquidity with transfer-tax token pairs: a) removeLiquidity b) removeLiquidityETHSupportingFeeOnTransferTokens The Standard Liquidity Removal: removeLiquidity The…
United States Trends
- 1. #DWTS 49K posts
- 2. Whitney 14.8K posts
- 3. Keyonte George 1,526 posts
- 4. Elaine 16.8K posts
- 5. LeBron 51.3K posts
- 6. Taylor Ward 2,946 posts
- 7. Dylan 23.9K posts
- 8. Orioles 5,973 posts
- 9. Grayson 6,292 posts
- 10. #WWENXT 15.5K posts
- 11. Winthrop 2,306 posts
- 12. Jordan 107K posts
- 13. Harrison Barnes 1,945 posts
- 14. Peggy 15.6K posts
- 15. Connor Bedard 3,393 posts
- 16. Robert 82.1K posts
- 17. Tatum 13.7K posts
- 18. Haiti 47.6K posts
- 19. Angels 30.7K posts
- 20. Romanov 1,378 posts
You might like
-
 JOJO丨GDC
JOJO丨GDC
@wcxxx001 -
 ZdravkoHr.
ZdravkoHr.
@zdravkohristov0 -
 Tolahash
Tolahash
@tolahash -
 GeneralKay | Kaysoft
GeneralKay | Kaysoft
@kayroy2010 -
 Mylifechangefast.eth🕵
Mylifechangefast.eth🕵
@mylifechangefa1 -
 deo
deo
@kurdishtic -
 Naresh
Naresh
@NareshETH7 -
 Alex T.
Alex T.
@alexipreneur -
 The SeveritySquad
The SeveritySquad
@Severity_Squad -
 Damola.
Damola.
@Damola0x -
 santoshmore@ETH
santoshmore@ETH
@santoshmore088 -
 OKOMO
OKOMO
@AungMaw97445407 -
 Prathamesh Autade
Prathamesh Autade
@prathamesh_710
Something went wrong.
Something went wrong.