ClickSafe Community(CSC)
@ClickSafeCSC
Cybersecurity Community
Amazing news here 🥳🥳 As the first half of the year is over, We begin a new Cluster of ClickSafe community. Do you want to transition or upskill in your Cybersecurity journey? This is for you. Join the 2nd Cluster of CSC community. lnkd.in/djrgKpDN
Which of the following is NOT a feature of a cryptographic hash function? A. Reversible B. Deterministic C. Unique D. Useful
Answer: A ✅ Explanation: Wireshark is the world's most widely-used and complete network protocol analyzer that, informally speaking, is the "microscope" of network traffic. John the Ripper is a famous Open Source password security auditing and password recovery tool.…
Which tool is commonly used to sniff network traffic? A. Wireshark B. Burp Suite C. John the Ripper D. Nslookup
The cloud isn’t just someone else’s computer. It’s: • multi-tenant infrastructure • abstracted networking • policy-based access • API-driven operations If you treat it like a normal server, you’ll misconfigure it. 💯
The like button on X changing to the Grok sign when you post about GROK is likely due to X's integration with Grok, an AI chatbot developed by xAI, Elon Musk's AI company. This integration is probably triggered by keyword detection, replacing the like button with the Grok logo…
My question is how did Elon musk put grok logo animation as the like button 😭
To log out on: 1. Android: - Settings > Google > Ads > Opt out of personalized ads - Settings > Privacy > Google activity controls > Web & App Activity > uncheck 2. iPhone: - Settings > Privacy > Tracking > Limit Ad Tracking - Settings > Facebook (app) > Settings > Ads > Limit…
To log out on: 1. Android: - Settings > Google > Ads > Opt out of personalized ads - Settings > Privacy > Google activity controls > Web & App Activity > uncheck 2. iPhone: - Settings > Privacy > Tracking > Limit Ad Tracking - Settings > Facebook (app) > Settings > Ads > Limit…
Your phone isn't "accidentally" listening to you. It's a feature, not a bug. I talked about a specific dog food brand once 10 minutes later, I had an ad. It’s called "Shadow-Logging," and it’s happening through 5 settings you’ve never touched. Here is how to kill the…
The African in me reading these comments 😭😂🤣. Y’all have fun up there
Discord's age verification aims to protect teens, but raises questions: - Might reduce harm, but won't stop determined users - Teens outside US might struggle with verification especially with the ID part - Possibility of getting bypassed But Does it balance safety and…
If this is true, then it’s a big shift from Microsoft! They're closing physical libraries and embracing an AI-powered Skilling Hub for employee learning. As a cloud expert, I see this as a bold move towards personalized, scalable learning experiences. The future of work is…
Discord's age verification aims to protect teens, but raises questions: - Might reduce harm, but won't stop determined users - Teens outside US might struggle with verification especially with the ID part - Possibility of getting bypassed But Does it balance safety and…
DNI = National Identity Document 🤝
Chrome's RAM usage can be attributed to its design and features: - Multiple processes: Chrome runs each tab, extension, and plugin in a separate process, which increases RAM usage but improves stability and security. - Preloading and caching: Chrome preloads pages and…
The cloud isn’t just someone else’s computer. It’s: • multi-tenant infrastructure • abstracted networking • policy-based access • API-driven operations If you treat it like a normal server, you’ll misconfigure it. 💯
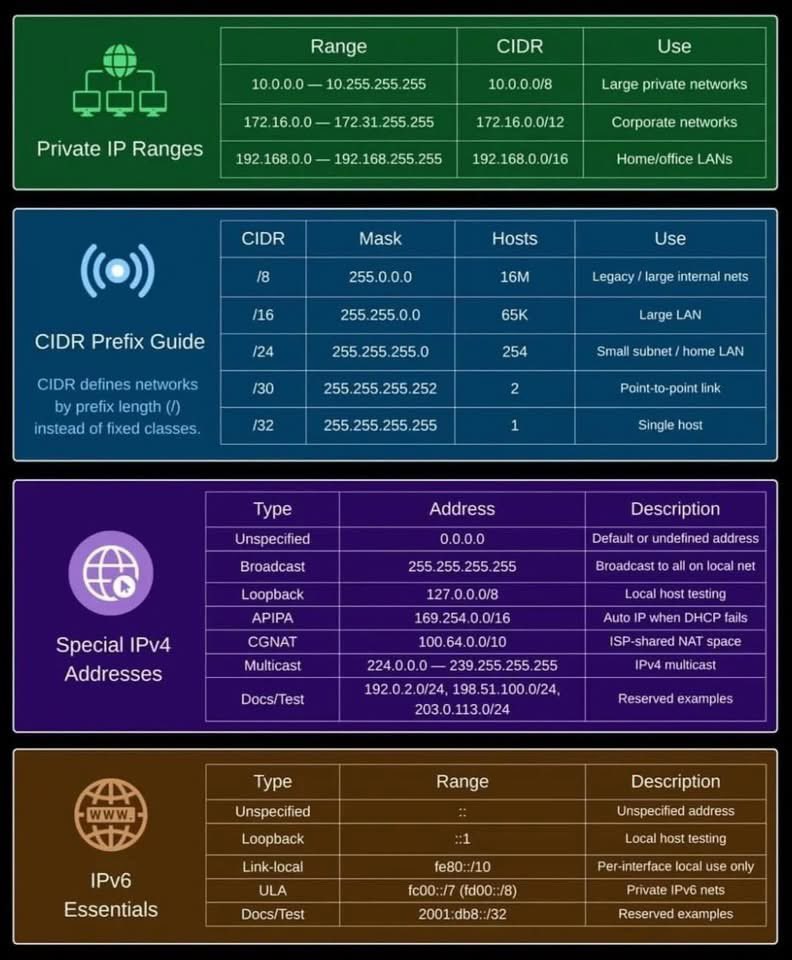
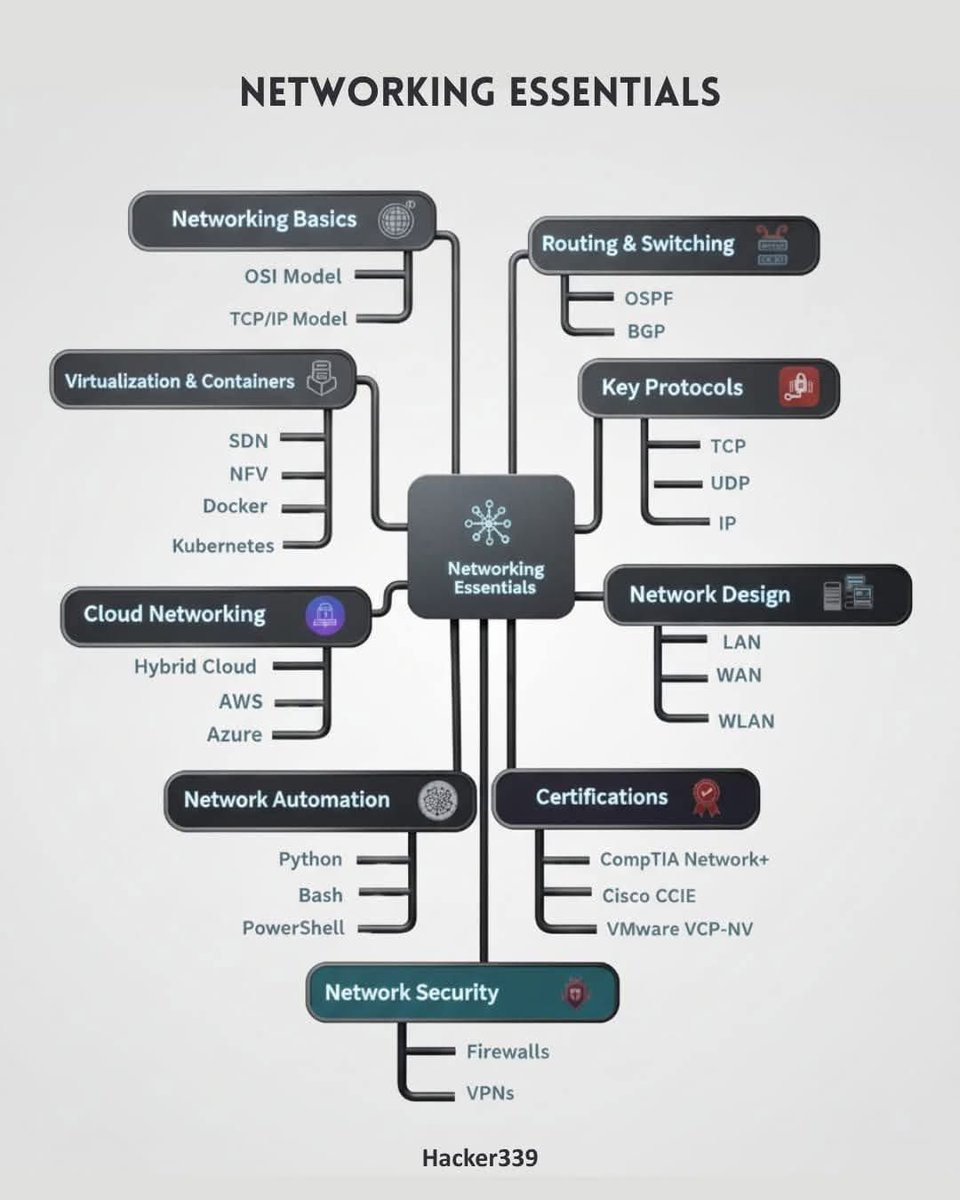
Networking essentials
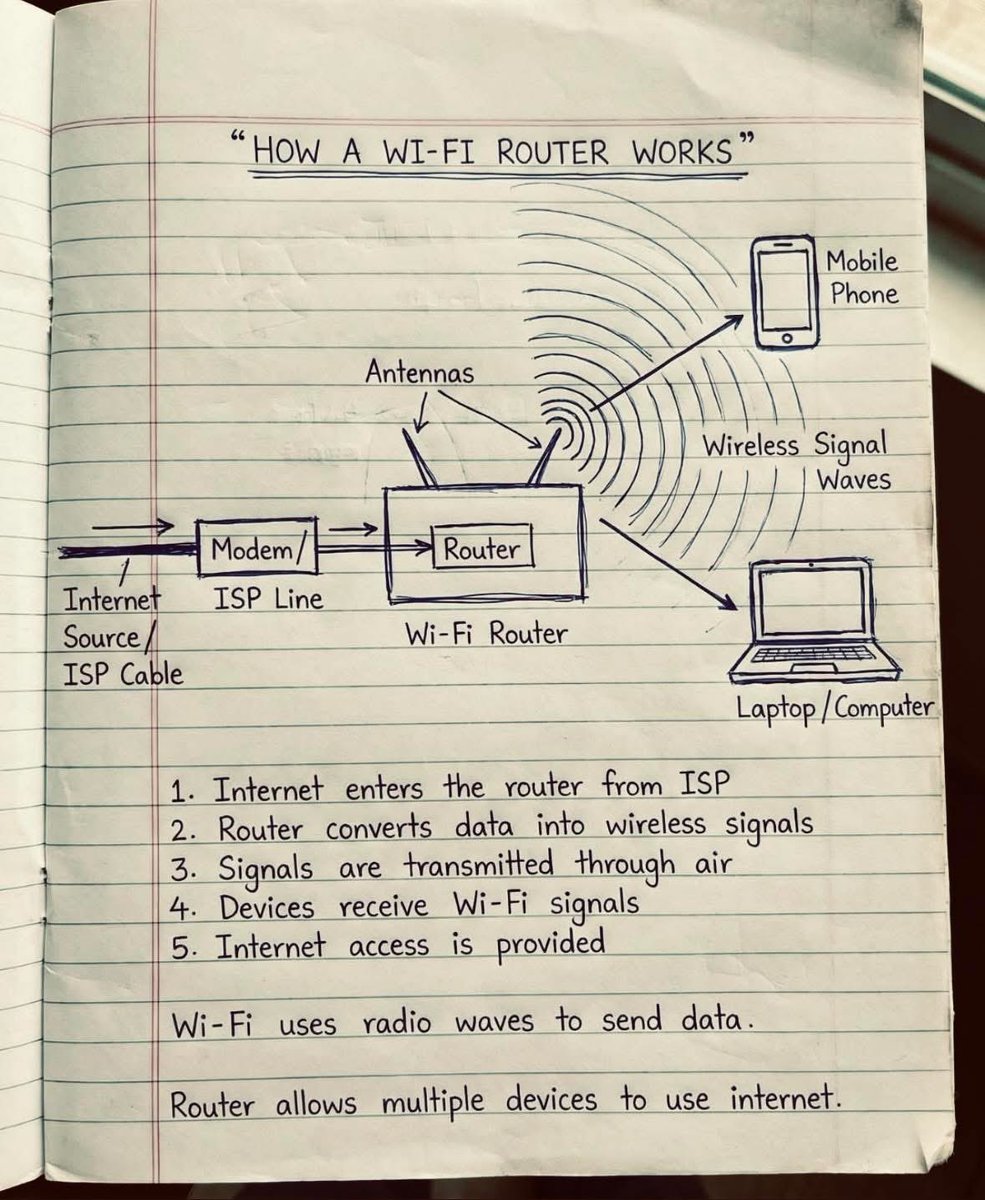
How WiFi Router Works
Stop planning a “cybersecurity roadmap” that spans 4 years. You haven’t even opened Wireshark yet. Start small. Clarity comes from doing, not mapping.
You’re doing well in tech Keep going linkedin.com/posts/racheal-…
Which should you choose? •Choose Brave if: You want a faster, ad-free experience without manual setup and prioritize keeping your data away from Big Tech organizations.. •Choose Chrome if: You are deeply integrated into the Google ecosystem (Gmail, Drive) and value solid…
Before you choose to write a particular cybersecurity certificate, make sure they will be relevant to you and the field you work in. You’re looking for an entry level role, You have no business writing a certificate like CISM, CCSP. You’ll be doing yourself a disservice.
United States Trends
- 1. Kansas N/A
- 2. #WWERaw N/A
- 3. Isaiah Stewart N/A
- 4. Reaves N/A
- 5. #tellmelies N/A
- 6. Pistons N/A
- 7. Arizona N/A
- 8. Duren N/A
- 9. Bridges N/A
- 10. Allen Fieldhouse N/A
- 11. Hornets N/A
- 12. Peterson N/A
- 13. Laravia N/A
- 14. Bill Self N/A
- 15. Rock Chalk N/A
- 16. Caruso N/A
- 17. #kubball N/A
- 18. $Giraffes N/A
- 19. Ayton N/A
- 20. #TheRookie N/A
Something went wrong.
Something went wrong.