H2Tech
@H2Tech
#itsupport #itsupportsydney #ITConsultancy #techsupport #Microsoftpartner #Macsupport #backups #servers #cloudhosting #virtualization
You might like
Your data is important, so let #H2Tech keep it safe and secure. Contact us today for the best #ITSolutions for you business! #Technology #MSP #Cloud #IaaS #SaaS #ITServices #ITSupport buff.ly/2qS4Eo2

Keep your #tech up and running smoothly with #H2Tech #itsolutions. Contact us today! #techsupport #itsupport #itservices #msp #cloud #cloudcomputing #iaas #saas buff.ly/2qS4Eo2
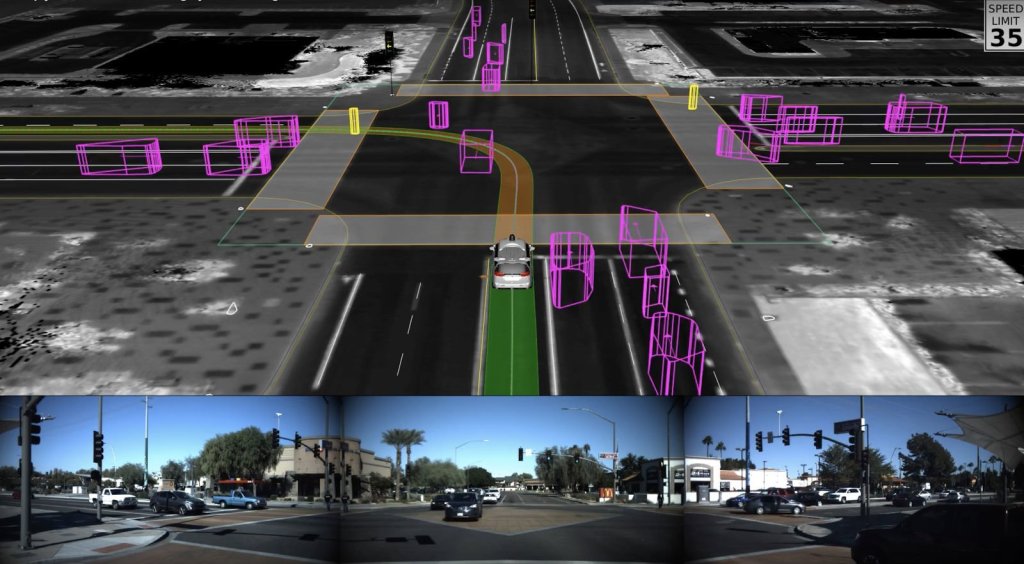
Waymo has now driven 10 billion autonomous miles in simulation tcrn.ch/2XJPP4I by @etherington
Shine a spotlight on your #tech with #H2tech business #itsolutions. Contact us today to find out more! #tech #techsupport #itsupport #itservices #msp #cloud #cloudcomputing #iaas #saas buff.ly/2Q9OlS6

The new Raspberry Pi is basically a $35 desktop computer gizmo.do/UA098jf

This sad robot made from random twigs has to teach itself to get around gizmo.do/QryOfjo
Let #H2Tech work our magic and make your IT issues disappear. Why not give us a call to find out how! #tech #techsupport #itsupport #itsolutions #itservices #msp #cloud #cloudcomputing #iaas #saas buff.ly/2qS4Eo2
Randomness is crucial for almost everything we do with our computational and communications infrastructure. But genuine, verifiable randomness is hard to come by. That could change once quantum computers demonstrate their superiority. wired.trib.al/iYuOykD
All these high-profile database breaches have finally started to make companies aware of what solid encryption is worth. And now researchers may have a radically simple way of actually preventing them. wired.trib.al/kjUROgY
Meet the man who's made mirrors from wooden tiles, trash, fans, even pom-poms. Bonus: They echo your movements. trib.al/k9Pdc9i
Keep your #tech singing the right tune! Contact #H2Tech today and let us find the right key for your #business. #technology #itsupport #techsupport #itsolutions #cloud #cloudcomputing #itservices #msp #iaas #saas buff.ly/2qS4Eo2
Pushing a 28-core CPU to its limits: 6GHz and beyond engadget.com/2019/05/31/ove…
Look upon what Amazon hath designed, for it soon will blanket the sky gizmo.do/CWmDbEh
Your options are endless when it comes to #cloud #technology. Contact #H2Tech and unravel your tech issues today! #ITSupport #tech #ITSolutions #TechSupport #MSP #IaaS #SaaS #CloudComputing #ITServices buff.ly/2qS4Eo2

Thousands of TP-Link routers are vulnerable to a bug that can be used to remotely take control the device, but it took over a year for the company to publish the patches on its website. techcrunch.com/2019/05/22/tp-…
Nectar’s sonar bottle caps could save $50B in stolen booze tcrn.ch/2WXyVj7 by @joshconstine

Let us be your first line of defence when it comes to your #tech, #itsupport with a bang! #H2Tech #technology #techsupport #itsolutions #business #msp #iaas #saas #cloud #cloudcomputing #itservices buff.ly/2qS4Eo2
Intel and security researchers announced a new, serious form of hackable vulnerability in Intel's chips. It's four distinct attacks and all are capable of siphoning a stream of potentially sensitive data from a computer's CPU to an attacker. wired.trib.al/sRtlA4k
United States Trends
- 1. $ENLV 4,175 posts
- 2. Jimmy Cliff 12.5K posts
- 3. Good Monday 41.7K posts
- 4. #MondayMotivation 10.5K posts
- 5. #IDontWantToOverreactBUT N/A
- 6. Victory Monday 2,484 posts
- 7. TOP CALL 4,178 posts
- 8. Happy Thanksgiving 11.2K posts
- 9. AI Alert 2,135 posts
- 10. The Harder They Come 1,525 posts
- 11. DC Shane Bowen N/A
- 12. #MondayVibes 2,804 posts
- 13. DOGE 205K posts
- 14. #MondayMood 1,412 posts
- 15. Market Focus 2,955 posts
- 16. Monad 141K posts
- 17. Check Analyze N/A
- 18. Token Signal 2,566 posts
- 19. $OSCR 2,499 posts
- 20. $NVO 2,646 posts
Something went wrong.
Something went wrong.